- SAP Community
- Products and Technology
- CRM and Customer Experience
- CRM and CX Blogs by SAP
- SAP Sales Cloud and SAP Service Cloud version 2 - ...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Steps:
- You have a client certificate signed by one of the CAs supported by the load balancer. More information on the supported CAs: Load Balancer Root Certificates Supported by SAP.
- Upload the key pair to communication system in SAP Sales Cloud and Service Cloud Version 2.
- Configure Client Certificate-Based Authentication in the Service Instance in SAP Cloud Platform Cockpit.
Let's cover the steps in more detail
Step 1 : Prepare Key-Pair in PKCS#12 (.p12) File format
Note: SAP Sales Cloud and Service Cloud Version 2 only supports .p12 not .pfx for now.
For this post I am using openssl to generate the key pair and the PKCS#12 file.
This is optional and you are free to use any other tool as preferred
First let's generate a key and certificate signing request
openssl genrsa -out an150224.key 2048
openssl req -new -key an150224.key -out an150224.csr
Next step is to get the certificate signed by one of the CAs supported by the SAP load balancer
Once you have the CA signed certificate, export the certificate and private key to .p12 (PKCS12) file format. Note : The certificate file should have whole certificate chain (including Intermediate certificate authorities in order)
openssl pkcs12 -export -out an150224.p12 -inkey an150224.key -in an150224certchain.cer
If needed, verify the content of .p12
openssl pkcs12 -info -nodes -in an150224.p12
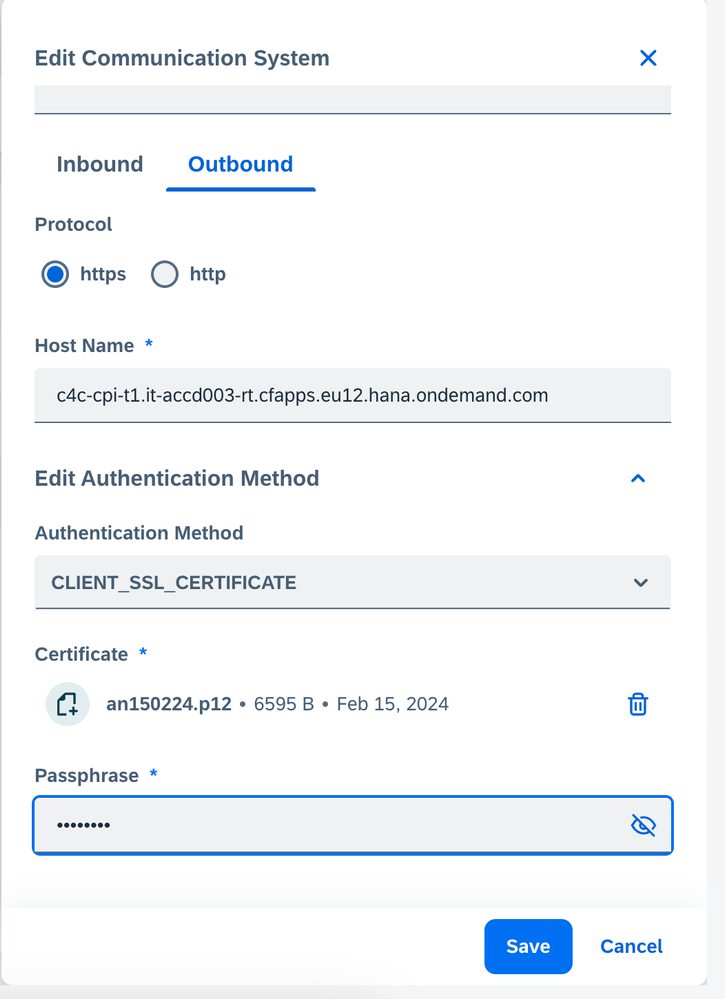
Step 2: Upload the key pair to communication system inSAP Sales Cloud and Service Cloud Version 2
Upload the .p12 file to the communcation system under Outbound as shown below
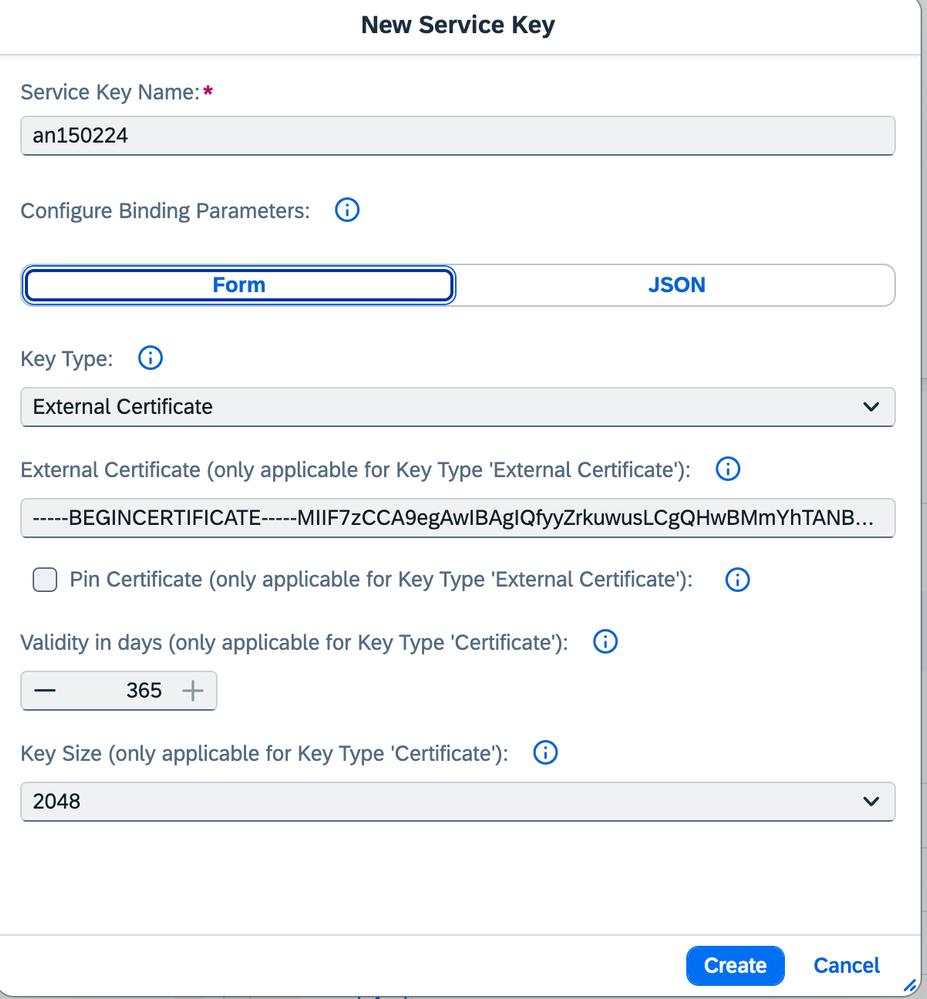
Step 3 - Configure Client Certificate-Based Authentication in the Service Instance in SAP Cloud Platform Cockpit
Create a service key under Process Integration Runtime service for plan integration-flow. Use key type as external certificate.
Note : Only client certificate in PEM format should be maintained under the External Certificate. CA certificates are not needed. More details on defining service keys in the Cloud Foundry environment can be found in the SAP online documentation at Creating Service Instance and Service Key for Inbound Authentication.
You are all set. Now messages coming from SAP Sales Cloud and Service Cloud V2 using the connector service will use mTLS (Client Cert) for authentication with SAP Cloud Integration.
You can also test it from curl if needed using the key and certificate chain.
curl -v --key an150224.key https://<CPI Runtime URL>/http/test/helloworld --cert an150224certchain.cer
Hint:
If you are getting 401 error, make sure the .p12 file has whole certificate chain including the private key.
That's all for this post. Happy Learning!!!
- SAP Managed Tags:
- SAP Sales Cloud,
- SAP Service Cloud
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
Business Trends
270 -
Business Trends
10 -
chitchat
1 -
customerexperience
1 -
Event Information
256 -
Event Information
18 -
Expert Insights
30 -
Expert Insights
49 -
Life at SAP
133 -
Life at SAP
1 -
Product Updates
666 -
Product Updates
25 -
SAP HANA Service
1 -
SAPHANACloud
1 -
SAPHANAService
1 -
Technology Updates
453 -
Technology Updates
15
- Create Custom Key Metrics with Kyma Serverless Functions in Sales and Service Cloud Version 2 in CRM and CX Blogs by Members
- Release Announcement: SAP Customer Data Cloud Implementation Training in CRM and CX Blogs by SAP
- Advanced Development Best Practices for SAP Commerce Cloud in CRM and CX Blogs by SAP
- SAP Commerce Cloud Updates in 2023: A Not-So-Brief Summary for Technical Users in CRM and CX Blogs by SAP
| User | Count |
|---|---|
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |