- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Unlocking the Power of Encryption
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Understanding Encryption
Encryption is a method of converting data into a coded form to prevent unauthorized access. It is a critical element of data security, ensuring that even if data is intercepted or accessed without permission, it remains unreadable without the decryption key.
Encryption keys are essential tools in the encryption process. They work like complex digital passwords that lock (encrypt) or unlock (decrypt) data. The nature of these keys can be symmetric or asymmetric. Symmetric encryption uses the same key for both the plaintext (unencrypted data) encryption and the ciphertext (encrypted data) decryption. It is fast and efficient, but the challenge lies in securely distributing the key to the intended decrypter. On the other hand, asymmetric encryption, also known as public-key encryption, uses two different keys: a public key for encryption and a private key for decryption. The public key, as the name suggests, is made available to everyone, but the private key is kept secret by the key’s owner. Asymmetric encryption is generally slower than symmetric encryption but offers the advantage of secure key distribution, as the private key never needs to be transmitted or shared. Both symmetric and asymmetric encryption play pivotal roles in maintaining the integrity and privacy of data in the digital world
If you would like a deeper dive into the fundamentals of encryption, be sure to read my other article entitled Encryption for Beginners: A Guide to Protecting Your Data.
Different Types of Encryption Methods
Now that you are familiar with the differences between symmetric and asymmetric encryption, let’s delve into the details of popular encryption algorithms.
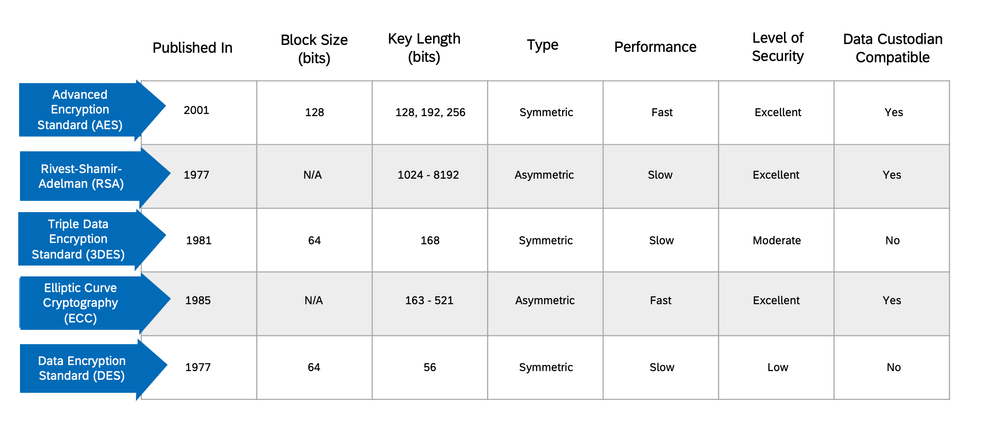
Two examples of symmetric encryption are the algorithms Advanced Encryption Standard (AES) and Data Encryption Standard (DES). Symmetric encryption algorithms are generally fast and efficient, especially for large amounts of data. However they also come with the risk of the keys being intercepted during transmission since the owner of the key must share their key with whomever they wish to converse with. To increase the security of an encryption algorithm one could increase the key length. The key length is the number of bits used in the cryptographic key. A longer key length generally equates to stronger security because it increases the number of potential combinations, making the key harder to guess or crack through brute force methods. AES, for example, can use key lengths of 128, 192, or 256 bits, which provides a very high level of security. AES is currently considered one of the most secure symmetric encryption algorithms and is widely used. DES, on the other hand, uses a 56-bit key and is considered weak in today's standards. It’s also worth noting that as the key size increases, so does the computational effort required for encryption and decryption.
Asymmetric encryption, used by the RSA (Rivest-Shamir-Adleman) algorithm, uses a pair of keys – both a public and private key. RSA key lengths are typically much larger than those of symmetric algorithms often 1024, 2048 or even 4096 bits. This is because the security of RSA is based on the difficulty of factoring large prime numbers, a task that becomes exponentially harder as the numbers get larger. Using large prime numbers makes RSA more secure, but it is also slower and requires more computational resources.
Lastly, you may be familiar with a term in computer security called hashing or perhaps you’ve heard of the popular hashing algorithm SHA (Secure Hash Algorithm). Hashing is not a form of encryption, as encryption provides a method for the data to become decrypted. Hashing is a one-way process, meaning that the original data cannot be retrieved from the hash value. It is a form of cryptographic security that transforms data into a fixed size hash value that cannot be decrypted. Hashing is commonly used for verifying data integrity and storing passwords securely but never for tasks that require the recovery of the data.
Choosing the Right Encryption Type
Selecting the right encryption type for your data necessitates careful consideration of several factors. First, you should identify the sensitivity of the data. Highly confidential and sensitive data, such as personally identifiable information (PII) or financial records, usually warrants stronger encryption algorithms to prevent unauthorized access. Second, regulatory requirements play a significant role in determining the encryption method that you should use. Different industries and countries have varying regulations regarding data protection. For instance, healthcare organizations in the U.S. must adhere to Health Insurance Portability and Accountability Act (HIPAA) that dictates which encryption standards must be used. The availability and cost of computational resources also plays a factor in choosing the right encryption algorithm. It is essential to balance the need for high-level security with the availability of computational resources and costs.
Key Management Service
When choosing and implementing an encryption method, it is imperative to follow your company’s security policies, but there are also some industry-standard best practices that you should keep in mind.
A critical aspect of a properly implemented encryption system is key management, which includes generating, storing, distributing, and retiring encryption keys in a secure manner. Key lifecycle operations such as key creation, distribution, storage, rotation, and deletion are essential processes that need to be managed with the utmost care and precision. For instance, key deletion is used when a key is no longer needed or has been compromised. This operation ensures that the key can no longer be used to access protected information, thus maintaining security. Another important operation is key rotation, which involves replacing a key with a new one at regular intervals or in response to specific events. Regular key rotation mitigates the risk of a key being compromised because even if an attacker gets hold of a key, they will not be able to use it for long before it becomes obsolete.
Let's take an example of an employee who leaves the company. In such a case, it is critical to revoke their access to all systems and delete or rotate any keys they had access to. This prevents the ex-employee from potentially gaining unauthorized access to the company's systems or data. If keys were not properly managed in this scenario, the company could be left vulnerable to security breaches.
There are many possible ways to implement a key management system. One option is to leverage a Hardware Security Module (HSM), a physical device that safeguards and manages digital keys for strong authentication and provides crypto processing. A HSM provides an additional layer of security, protecting against the potential vulnerabilities of software-based systems. Another option is to use a key management service that your data storage provider offers, such as SAP Data Custodian. SAP Data Custodian is a SaaS application, compatible with public hyperscalers and SAP managed clouds, that SAP offers to help users maintain visibility and control over their data in the cloud. SAP Data Custodian offers multiple encryption options for customers, including AES, RSA and Elliptic Curve Cryptography (ECC).
In conclusion, understanding and choosing the right encryption method—whether it's asymmetric or symmetric encryption—is a significant factor in ensuring data security. Both encryption types have their strengths, with symmetric encryption often being faster and less computationally heavy, and asymmetric encryption offering more robust security through its dual key system. Key Management Services (KMS) plays a pivotal role in the secure creation, control, and storage of encryption keys, making the implementation of encryption more seamless and secure. The decision of which encryption algorithm to use should be made based on your unique needs, considering factors like the sensitivity of the data, the time it takes to encrypt and decrypt, and the computing costs. Ultimately, the goal is to strike the right balance between security and efficiency to create a robust data protection strategy.
Learn more about encryption at SAP:
Take Control of Your Encryption Keys with SAP Data Custodian Key Management Service
- SAP Managed Tags:
- Security,
- SAP Data Custodian
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
93 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
67 -
Expert
1 -
Expert Insights
177 -
Expert Insights
301 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
346 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
430 -
Workload Fluctuations
1
- Explore Business Continuity Options for SAP workload using AWS Elastic DisasterRecoveryService (DRS) in Technology Blogs by Members
- Enhancing S/4HANA with SAP HANA Cloud Vector Store and GenAI in Technology Blogs by SAP
- SAP Enterprise Architecture: Positioning Blockchain Database as an Enterprise Technology Standard 🚀 in Technology Blogs by Members
- Unlock the Future of SAP: Don't Miss These Sessions at SAP Sapphire 2024! in Technology Blogs by SAP
- Empowering Process Transformation: Variant Management for Managing Complex Process Landscapes in Technology Blogs by SAP
| User | Count |
|---|---|
| 28 | |
| 17 | |
| 15 | |
| 13 | |
| 11 | |
| 9 | |
| 8 | |
| 8 | |
| 8 | |
| 7 |