- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- SAP NetWeaver PI\PO SFTP Fingerprint Scenarios wit...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
SFTP Adapter is being used in the business scenario for message processing. While message processing with finger print following error has been observed in the channel logs :
Exception received: java.lang.UnsupportedOperationException: promptYesNo(String str) is not implemented yet!
The issue occurs after upgrading the component SAP_XIAF to 7.50 SP028 patch level 0.
The issue has been resolved by code changes in Note : 3397655 - SFTP Adapter fails with java.lang.UnsupportedOperationException: promptYesNo(String str) i...
After implementation of above Note , Below steps will help to solve the issue and follow steps to setup SFTP Finger Print Scenarios with Global Parameter.
Note: Below steps explain creating scenarios from end to end, In your case If you already have a setup, you can directly follow steps from Setting Parameter.
Prerequisites:
- Create SFTP Sender channel
- Create SFTP Receiver Channel
- Create ICO
- SSH Keys for SFTP Adapters ( Ref:
Generating SSH Keys for SFTP Adapters - Type 1 | SAP Help Portal
Generating SSH Keys for SFTP Adapters - Type 2 | SAP Help Portal
With this fix, two new parameters 'preferredKeyType' and 'fingerprintHash' are introduced and the default value for these parameters are as follows:
preferredKeyType = ssh-rsa
fingerprintHash = SHA256
Setting Parameter:
Options available to configure fingerprintHash and preferredKeyType:
- Channel level only via advanced mode parameters
- Application level only via global parameters
- Both Channel level and Application level (priority will be given to corresponding channel level value)
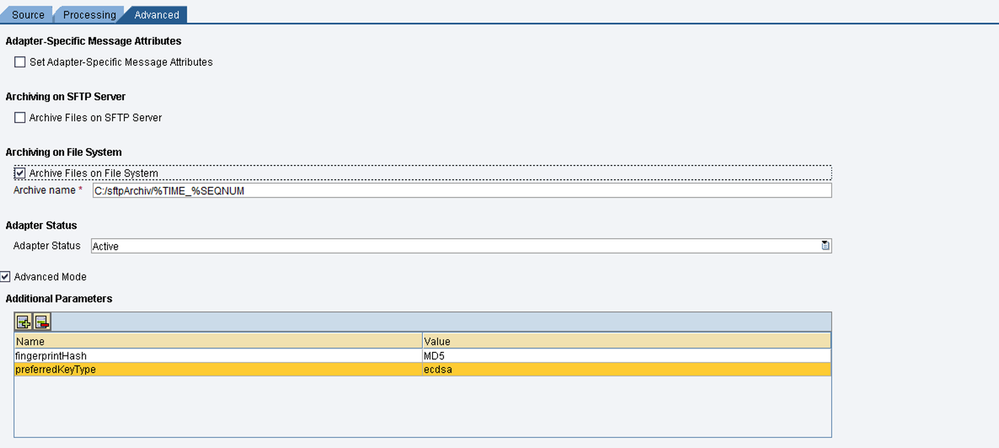
1)Channel level only via advanced mode parameters
In the SFTP Adapter channel configuration, the Server fingerprint has to be set to SHA-256 fingerprint hash value. MD5 hash value is disabled in SP28 by default as it is outdated and insecure for cryptographic purposes, while SHA-256 is a more secure and widely used cryptographic hash function with a longer hash length. MD5 generates a 128-bit (16-byte) hash value whereas SHA-256 generates a 256-bit (32-byte) hash value.
Fingerprint format before SP28 (MD5 hash value) : b0:67:bb:26:aa:65:0f:32:a1:0d:35:ae:26:85:a2:98
Fingerprint format SP28 onwards (SHA-256 hash value): 88:7a:ce:65:b4:a1:3f:c5:f6:38:ce:a5:70:32:ee:38:b6:9d:50:4f:ae:01:0d:ed:e7:26:52:b3:b6:81:10:1f
The channels with old fingerprint setting (MD5 hash value) will fail and the correct/sha-256 fingerprint value will be suggested in the channel logs.
NOTE: If needed, the old behaviour (i.e., old fingerprint -MD5 hash value) can be enabled again by setting advanced mode parameter fingerprintHash = MD5
The following points has to be followed:
The correct fingerprint can be verified/collected from the channel log.
The fingerprint can also be taken from the xpi inspector traces. For this, xpi traces can be collected for Example 100 by selecting the location: com.sap.aii.adapter.sftp. From the logs, the value for fingerprint can be copied by searching the text 'Server Fingerprint'.
The collected fingerprint should be set in the SFTP channel to resolve the issue.
To enable the old behaviour (i.e., old fingerprint -MD5 hash value), the following advanced mode channel parameter should be set in each channel: fingerprintHash = MD5
To prioritise ECDSA key usage over RSA key, the following advanced mode channel parameter should be set in each channel: preferredKeyType = sha2 or ecdsa or ecdsa-sha2 or ecdsa-sha2-nistp256
It is possible to retrieve in advance of the system update the new SHA256 server fingerprint for internal SFTP servers with the command below (for remote servers, request this to their administrators to ensure authenticity):
For ECDSA key type:
# ssh-keyscan -t ecdsa -p <myport> <myhost> 2>/dev/null | sed "s/^[^ ]* //" | awk '{print $2}' | base64 -d | sha256sum | awk '{print $1}' | fold -w2 | paste -sd':' -
88:7a:ce:65:b4:a1:3f:c5:f6:38:ce:a5:70:32:ee:38:b6:9d:50:4f:ae:01:0d:ed:e7:26:52:b3:b6:81:10:1f
For SSH-RSA key type:
# ssh-keyscan -t rsa -p <myport> <myhost> 2>/dev/null | sed "s/^[^ ]* //" | awk '{print $2}' | base64 -d | sha256sum | awk '{print $1}' | fold -w2 | paste -sd':' -
This command is only valid for Linux based systems. For other OS we have currently no similar command.
If multiple SFTP channels are connecting to same SFTP server, then the fingerprint for all those SFTP channels can be updated together using Migration Tool. To run the Integration Directory Migration Tool, please use the following link in target system:
Open a browser and go to http://[host]:[port]/pimon to access the Process Integration tools.
Then choose Start of the navigation path 'Configuration and Administration' and from there, open 'Migration Tool.
Set the correct fingerprint by replacing the value/*.
Example:
2) Introduction of global parameters for fingerprintHash and preferredKeyType:
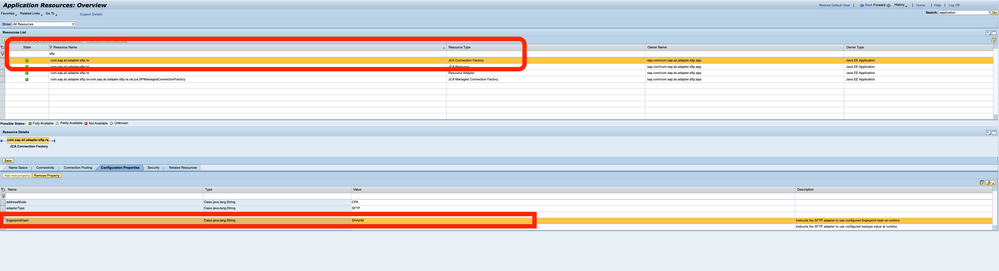
It is now possible to configure the properties fingerprintHash and preferredKeyType at the application level. The values of these global parameters will then reflect in ALL sftp channels (other than those channels where this value is overridden by corresponding advanced mode parameter)
To do so please navigate to NWA -> Configuration ->Infrastructure> Application Resources. Search for com.sap.aii.adapter.sftp.ra under "Resource Name", from the search results click on the row where "Resource Type" is JCA Connection Factory and click on Configuration Properties below. Here you can see the rows fingerprintHash and preferredKeyType - to edit them click on the value column and edit the cell and click on "Save" once you are done editing. (Kindly refer the attachments in this note for a snippet of the same)
Please note that the default values and the set of values which can be configured for these parameters are the same as the respective channel level advanced parameters mentioned earlier in this note.
In the case that a channel has the same parameter configured in the advanced mode, this value will take precedence over the value configured for the parameter at the application level. For example, if fingerprintHash is set to SHA256 in application level, but configured as MD5 in a particular channel (via advanced mode params), then this particular channel will use MD5 as it's fingerprintHash.
3).Both Channel level and Application level (priority will be given to corresponding channel level value)
You can set Parameter according to your requirement in global\channel level as mentioned above.
With the above detailed steps you can setup SFTP Finger Print Scenarios with Global Parameter.
- SAP Managed Tags:
- SAP Community
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
95 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
67 -
Expert
1 -
Expert Insights
177 -
Expert Insights
310 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,576 -
Product Updates
353 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
441 -
Workload Fluctuations
1
- Certificate file content disappeared from the ICM trace level 3 in ABAP 7.58 in Technology Q&A
- SAP BW/4 - revamp and true to the line 2024 in Technology Blogs by Members
- Quick & Easy Datasphere - When to use Data Flow, Transformation Flow, SQL View? in Technology Blogs by Members
- SAP Enable Now setup in Technology Blogs by Members
- How to test a Windows Failover cluster? in Technology Blogs by SAP
| User | Count |
|---|---|
| 20 | |
| 14 | |
| 12 | |
| 11 | |
| 10 | |
| 10 | |
| 9 | |
| 9 | |
| 8 | |
| 8 |