
- SAP Community
- Products and Technology
- Enterprise Resource Planning
- ERP Blogs by SAP
- SAP S/4HANA Cloud, Public Edition: Cybersecurity F...
Enterprise Resource Planning Blogs by SAP
Get insights and updates about cloud ERP and RISE with SAP, SAP S/4HANA and SAP S/4HANA Cloud, and more enterprise management capabilities with SAP blog posts.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Advisor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
05-16-2023
2:05 AM
(Jana Subramanian serves as APJ Principal Cybersecurity Advisor for Cloud Security and has been recognized as a Fellow of Information Privacy (FIP) by the International Association of Privacy Professionals (IAPP). As part of his responsibilities, Jana helps with strategic customer engagements related to topics such as cybersecurity, data privacy, multi-cloud security integration architecture, contractual assurance, audit, and compliance.)
Introduction
The SAP S/4HANA Cloud, Public Edition provides a comprehensive set of features and capabilities that empower businesses to standardize business processes, propel digital innovation and transformation, enhance security measures, and remain competitive in the digital age. As a core component of the GROW with SAP bundle, SAP S/4HANA cloud, public edition enables a seamless transition to Next-Generation Enterprise Resource Planning (ERP) systems, while protecting customer data and incorporating cybersecurity throughout every layer of the platform.
In this blog, we will address frequently asked questions (FAQ) about the cybersecurity aspects of the SAP S/4HANA Cloud, Public Edition that is easy to read by customers and partners. By exploring these frequently asked questions, one can obtain a better understanding of how SAP S/4HANA Cloud, Public Edition can improve security, protect customer data, and minimize potential risks.
Customer Segregation
Secure Connectivity
Data Protection
High Availability and Disaster Recovery
Malware Protection
Audit Certification and Compliance
Shared Security Responsibility
Backup and Restore
Application Security
Logging and Monitoring
Secure Operations
Additional References
Conclusion
This blog seeks to answer some of the most common cybersecurity questions about RISE with SAP S/4HANA cloud, public edition. This solution offers strong and comprehensive security capabilities to protect customers' business data. By utilizing SAP's secure multi-tenanted architecture, secure operations, and security assurances through contracts and certifications, customers can have greater confidence that their mission critical business data is secure from emerging cyber threats. For more information on cybersecurity protections and contractual assurances, customers are encouraged to refer to the SAP Trust Center or access the resources provided in the references.
Acknowledgement:
The author would like to express deep appreciation for PATRICK BOCH, Product Management S/4HANA Security at SAP for his efforts in reviewing the content and providing valuable feedback. Special thanks to Björn Brencher, Product Security for clarifying few of the questions.
Disclaimer:
© 2023 SAP SE or an SAP affiliate company. All rights reserved. See Legal Notice on www.sap.com/legal-notice for use terms, disclaimers, disclosures, or restrictions related to SAP Materials for general audiences.
Introduction
The SAP S/4HANA Cloud, Public Edition provides a comprehensive set of features and capabilities that empower businesses to standardize business processes, propel digital innovation and transformation, enhance security measures, and remain competitive in the digital age. As a core component of the GROW with SAP bundle, SAP S/4HANA cloud, public edition enables a seamless transition to Next-Generation Enterprise Resource Planning (ERP) systems, while protecting customer data and incorporating cybersecurity throughout every layer of the platform.
In this blog, we will address frequently asked questions (FAQ) about the cybersecurity aspects of the SAP S/4HANA Cloud, Public Edition that is easy to read by customers and partners. By exploring these frequently asked questions, one can obtain a better understanding of how SAP S/4HANA Cloud, Public Edition can improve security, protect customer data, and minimize potential risks.

Figure 1: Multi-Layer Security
Customer Segregation
| S.No | Description of FAQ | FAQ Explained |
| 1 | How does SAP segregate each customer environment in SAP S/4HANA cloud public edition, specifically in Azure and GCP environments? |
|
| 2 | How is segregation established between admin network, backup network and Customer Tenancy Network? |
|
| 3 | What are resources that are shared in the platform? |
|
Secure Connectivity

Figure 2: Access to SAP S/4HANA cloud, public edition
| S.No | Description of FAQ | FAQ Explained |
| 4 | How do customers connect to SAP S/4HANA cloud, public edition? |
|
| 5 | Do you support dedicated network connection bypassing Internet? |
|
| 7 | How do I establish security in case I need to integrate with other cloud services? |
|
| 8 | What is the role of SAP BTP in SAP S/4HANA cloud, public edition? |
|
| 9 | How do I secure the cloud integrations with SAP BTP, SAP S/4HANA cloud, public edition and on-premises SAP systems? | SAP BTP offers numerous services that enable building, extending, and connecting applications throughout the SAP landscape.
|
Data Protection
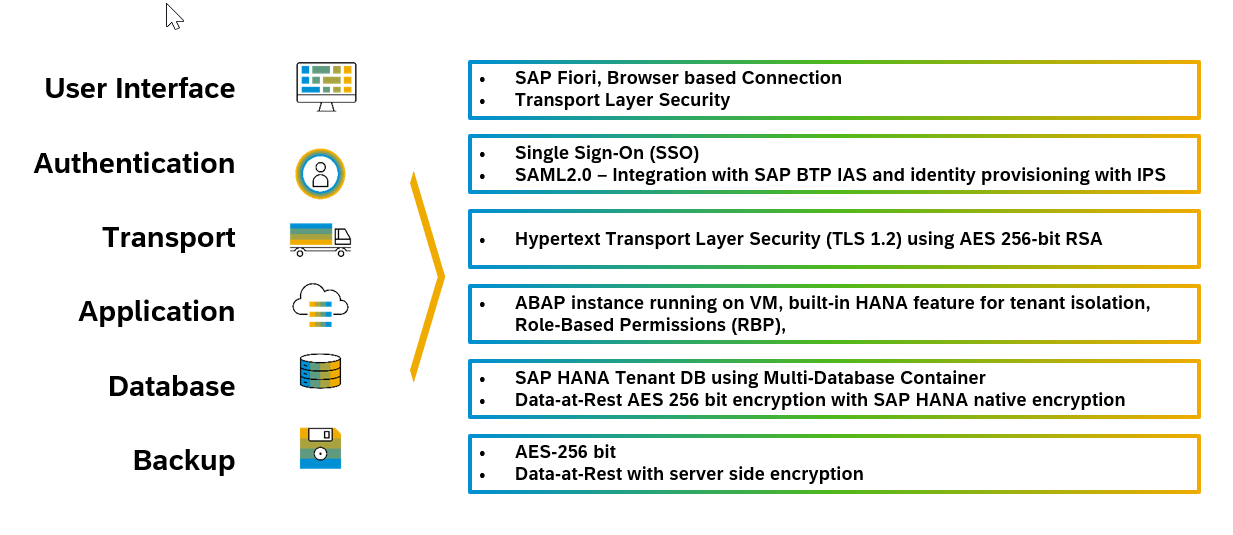
Figure 3: End-to-End Data Protection
| S.No | Description of FAQ | FAQ Explained |
| 10 | How is data encryption supported for data in transit? |
|
| 11 | How is data at rest encryption performed in SAP S/4HANA cloud, public edition? |
|
| 12 | Can SAP S/4HANA cloud, public edition support Bring Your Own Key (BYOK)? |
|
| 13 | What is the other application-level data protection and privacy controls available with SAP S/4HANA cloud, public edition? | SAP S/4HANA cloud, public edition provides following application-level controls:
|
High Availability and Disaster Recovery
| S.No | Description of FAQ | FAQ Explained |
| 14 | Do you support High Availability? |
|
| 15 | Do you support Disaster Recovery and if so, what are the RTO and RPO? |
|
| 16 | How does S/4HANA cloud, public edition manage capacity? |
|
Malware Protection
| S.No | Description of FAQ | FAQ Explained |
| 17 | How do you protect against Malware? | SAP cloud operations employees several security measures to protect against malware which include among others:
|
| 18 | Does SAP S/4HANA cloud, public edition maintain capability virus scan for document uploads? | Yes. SAP S/4HANA Cloud uses virus scanning services to provide real-time protection and prevent the upload of malicious or suspicious content. The capabilities include the following:
|
Audit Certification and Compliance
| S.No | Description of FAQ | FAQ Explained |
| 19 | What security certifications audited via external 3rd party auditors are maintained for SAP S/4HANA cloud, public edition? | SAP S/4HANA cloud, public edition maintains several certifications, among them:
The certifications can be downloaded via https://www.sap.com/sea/about/trust-center/certification-compliance.html and SOC attestation report can be requested via Trust Center subject to NDA. |
Shared Security Responsibility
| S.No | Description of FAQ | FAQ Explained |
| 20 | What are the broad security responsibilities for customers in SAP S/4HANA cloud, public edition? |
|
| 21 | What are the broad security responsibilities of SAP as a Cloud Service Provider? | As the Cloud Service Provider (CSP) for SAP S/4HANA Cloud, public edition, SAP has a range of responsibilities to ensure the service is reliable, secure, and up to date. These responsibilities include:
|
| 22 | What are the other contractual assurances related to cloud services that may be applicable? |
|
Backup and Restore
| S.No | Description of FAQ | FAQ Explained |
| 23 | How does the Backup and Restore process is implemented? |
|
Application Security
| S.No | Description of FAQ | FAQ Explained |
| 24 | How does SAP follow secure coding for application development? |
|
Logging and Monitoring

Figure 4: Security Relevant APIs
| S.No | Description of FAQ | FAQ Explained |
| 25 | What are the security audit logs are available to customer on SAP S/4HANA application? |
|
| 26 | Can customer get access to Infrastructure Logs |
|
| 27 | Can SAP share Cyber SOC Use cases with Customers? |
|
Secure Operations
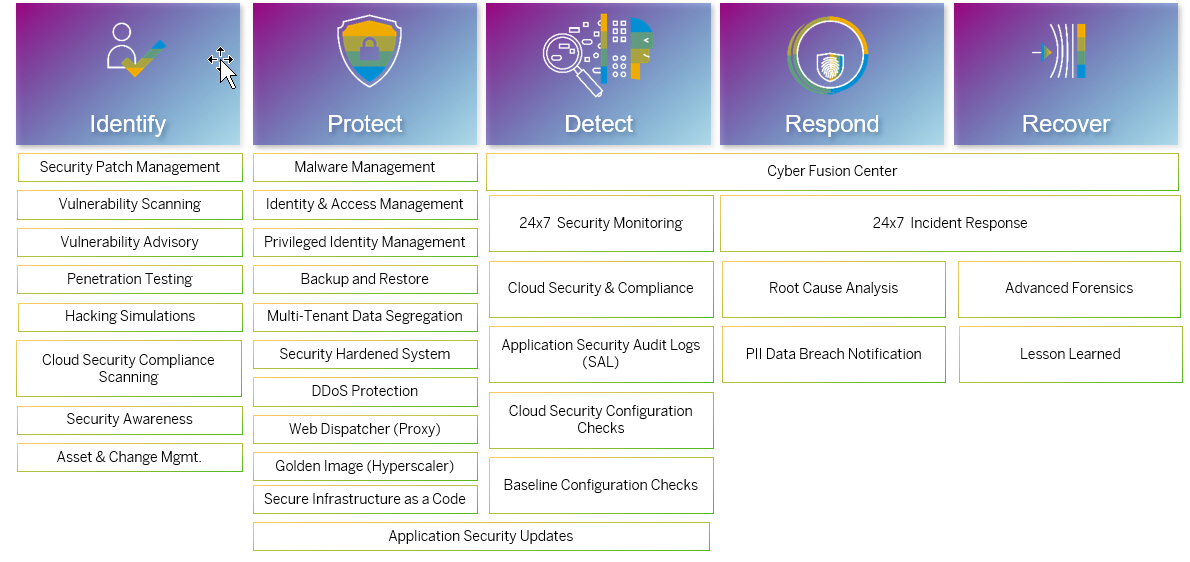
Figure 5: Secure Operations
| S.No | Description of FAQ | FAQ Explained |
| 28 | Is there any support portal that customer can access to view cloud availability, status, and other touch points with SAP? |
|
| 29 | Does SAP maintain Cyber SOC and if so, how the security use cases are being built? |
|
| 30 | How can customer raise a security incident? |
|
| 31 | What is the process for notifying personal data breach notifications to affected customers? |
|
| 32 | When and who decides to escalate an incident? Who is Contact Point for Security related communications? |
|
Additional References
Conclusion
This blog seeks to answer some of the most common cybersecurity questions about RISE with SAP S/4HANA cloud, public edition. This solution offers strong and comprehensive security capabilities to protect customers' business data. By utilizing SAP's secure multi-tenanted architecture, secure operations, and security assurances through contracts and certifications, customers can have greater confidence that their mission critical business data is secure from emerging cyber threats. For more information on cybersecurity protections and contractual assurances, customers are encouraged to refer to the SAP Trust Center or access the resources provided in the references.
Acknowledgement:
The author would like to express deep appreciation for PATRICK BOCH, Product Management S/4HANA Security at SAP for his efforts in reviewing the content and providing valuable feedback. Special thanks to Björn Brencher, Product Security for clarifying few of the questions.
Disclaimer:
© 2023 SAP SE or an SAP affiliate company. All rights reserved. See Legal Notice on www.sap.com/legal-notice for use terms, disclaimers, disclosures, or restrictions related to SAP Materials for general audiences.
Labels:
1 Comment
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
Artificial Intelligence (AI)
1 -
Business Trends
363 -
Business Trends
24 -
Customer COE Basics and Fundamentals
1 -
Digital Transformation with Cloud ERP (DT)
1 -
Event Information
461 -
Event Information
24 -
Expert Insights
114 -
Expert Insights
159 -
General
1 -
Governance and Organization
1 -
Introduction
1 -
Life at SAP
415 -
Life at SAP
2 -
Product Updates
4,684 -
Product Updates
219 -
Roadmap and Strategy
1 -
Technology Updates
1,502 -
Technology Updates
89
Related Content
- Join the Innovation Journey with SAP Enterprise Threat Detection, cloud edition in Enterprise Resource Planning Blogs by SAP
- RISE with SAP: Navigating Vulnerability and Patch Management in SAP Enterprise Cloud Services – Part 1 in Enterprise Resource Planning Blogs by SAP
- What is Everything-as-a-Service and Why Should You Care? in Enterprise Resource Planning Blogs by SAP
- Decoding Data Types and Security in SAP Cloud Services in Enterprise Resource Planning Blogs by SAP
- Secure Data Flow and Connectivity with SAP Cloud Services in Enterprise Resource Planning Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 11 | |
| 10 | |
| 9 | |
| 7 | |
| 7 | |
| 7 | |
| 6 | |
| 5 | |
| 4 | |
| 4 |