
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Enable Kerberos-based SSO for accessing your appli...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Associate
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
07-15-2019
9:23 AM
Intro into SCP and security.
I had the pleasure of touring with Martin Raepple across Australia to meet all our key customers presenting security session workshops. We discussed the option to put some of the common things asked by some of the SAP cloud subscribers into some blogs to help assist the journey.
When using SAP Cloud Platform Identity Authentication (IAS) many of our customers using Microsoft AD are interested in the configuration of Kerberos and IAS.
Scenario Overview
SAP Cloud Platform Identity Authentication Service (IAS) allows to configure single sign-on (SSO) for Browser-based access to any application trusted by the IAS tenant based on the SPNEGO protocol, which is also referred to as “Integrated Windows Authentication” by Microsoft. SPNEGO uses the Kerberos ticket issued by the user’s corporate Active Directory to authenticate the user at the IAS tenant.
Figure 1. Shows the major steps in this SSO scenario:
 Figure 1.
Figure 1.
- In the first step, the user with login name “jdoe” authenticates against the corporate Active Directory domain. This happens usually at initial windows login in the corporate network (Intranet). After successful login, the user obtains a Kerberos ticket from Active Directory (AD).
- When accessing the IAS tenant administration console, jdoe’s Web browser identifies this application as a trusted web site, and requests a new Kerberos ticket for it from the corporate AD, using the existing ticket obtained in the first step. This happens without asking the user again for her username and password. Based on an established trust relationship to the IAS tenant, the new ticket is accepted by the IAS tenant and the user is single-signed on to the administration console.
Prerequisites
The following settings should be checked before configuring the SPNEGO settings in Active Directory and IAS.
Steps Description
1) A user account for the IAS administrator exists in IAS tenant with login name equal to Windows logon name (here “P000000”)

2) A user account for the IAS Administrator exists in Active Directory (AD) with logon name equal to user in IAS tenant (here “P000000”)

3) In the business user’s browser settings, ensure that your IAS tenant’s hostname is either listed in the sites under “Trusted Sites”, or in the sites of the “Local intranet” zone (see screenshot for IE settings)

3.1) Optional: If IAS hostname is added under “Trusted Sites” zone, also set “Automatic logon with current user name and password” in “User Authentication” à “Logon” Security Settings of the “Trusted Sites” zone.

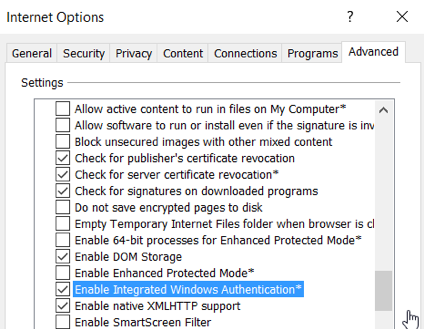
4) In the business user’s browser settings, ensure that “Integrated Windows Authentication” (aka SPNEGO) is enabled under Advanced options.
Scenario Configuration
5) Create a (service) user iastenant in AD. Mark in account options that “the account supports Kerberos AES 128 Bit encryption”.

6) Open command line and register a service principal name (SPN) associated with the service user for the host name used to access Identity Authentication:
setspn -A HTTP/<tenantid>.accounts.ondemand.com iastenant

7) Register the root host name of IAS per your region as an additional SPN for your service user, which is accounts.ondemand.com.cloud.sap.akadns.net for tenants in EU, or
us-east.accounts.ondemand.com for tenants in US:
setspn -A HTTP/accounts.ondemand.com.cloud.sap.akadns.net iastenant

8) Verify that the two SPNs are registered with the following command: setspn -T <Realm> -F -Q http/*

9) Change to your JAVA runtime bin folder (e.g. cd c:\Program Files\Java\jre1.8.0_131\bin)
10) Create new keytab file for the service user with command .\ktab -a iastenant@BESTRUN.CORP -k c:\tmp\newkeytab.ktab

11) Extract the keys from the keytab file with klist command from JAVA runtime environment:
cd c:\Program Files\Java\jre1.8.0_131\bin
.\klist -e -f -k -K c:\tmp\newkeytab.ktab
Copy the hex value for Key type 17 (all characters including ‘0x…’) into the clipboard.

12) Login to the IAS admin console with your IAS administrator username and password.
Go to SPNEGO Configuration under Tenant Settings.
Paste the key from the clipboard and select “AES128-CTS…” from the key type.
Enter the correct Realm name for your domain and save the settings.

13) Go to the Administration Console under Applications and enable SPNEGO

Testing the Scenario
14) Login to a host which belongs to the AD domain
15) Open the URL of the admin console in a Web browser (https://<tenantid>.accounts.ondemand.com/admin)
You're user should be single-singed-on to the admin console now.
See video
- SAP Managed Tags:
- SAP BTP Security,
- SAP Connectivity service,
- Security
Labels:
3 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
100 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
68 -
Expert
1 -
Expert Insights
177 -
Expert Insights
317 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,576 -
Product Updates
365 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
450 -
Workload Fluctuations
1
Related Content
- SAP BAS (Can I Deploy multiple times UI5 Application into ABAP Repository using BAS Trail Version) in Technology Q&A
- Third-Party Cookies and SAP Analytics Cloud in Technology Blogs by SAP
- Integration between SAP and One Identity in Technology Blogs by SAP
- SAPRouter Installation on Linux step by step in Technology Blogs by Members
- Cost optimized SAP HANA DR options on Google Cloud in Technology Blogs by Members
Top kudoed authors
| User | Count |
|---|---|
| 21 | |
| 12 | |
| 11 | |
| 9 | |
| 8 | |
| 8 | |
| 7 | |
| 7 | |
| 6 | |
| 6 |