- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Cloud Integration: AMQP Adapter, Client Certificat...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
SAP Cloud Integration (aka CPI) allows to send messages from an iFlow to an Event Broker via AMQP.
The AMQP adapter can be configured with Basic Authentication or with Client Certificate.
This blog post shows how to configure client certificate authentication in iFlow for sending messages to Solace PubSub+ Event Broker.
Overview
Part 1: Introduction
Part 2 : Create Client Certificate Chain
Part 3 : Configure Solace (this blog post)
3.0. Check Authentication Options
3.1. Upload Root Certificate
3.2. Authorization for Client
3.3. Create Queue
3.4. Connection Details
Part 4: Configure CPI, create iFlow, run
Part 3: Solace
At Solace side, we have 3 tasks to do:
1. upload the new root CA certificate
2. configure authorization for the new client
3. create a queue
0. There’s a prerequisite:
Certificate-based authentication must be enabled.
We check this in a step zero.
4. Furthermore, we need to get a hold of the connection details, to be used by CPI.
We need an additional step 4.
I assume you know better than myself how to work with Solace and use the Event Broker, so keeping it short.
To start with configuration, we logon to the PubSub+ Cloud console at
https://console.solace.cloud/login
3.0. Check Certificate-Based Authentication
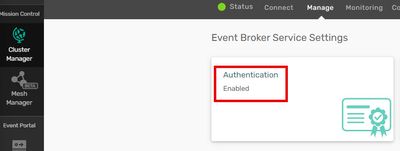
We go to “Cluster Manager” and select our Event Broker service instance.
Then choose “Manage” tab above.
Then “Authentication” tile on top left.
Make sure that it is “Enabled”.
Otherwise, click on the tile and enable “Client Certificate Authentication”.
In addition, if desired, enable the date-validation.
Don’t forget to “Save”.
3.1. Upload Root certificate
This section could also be called “Establish Trust”, between Solace server and CPI.
After uploading our root certificate, the Solace server will be able to trust the client certificates that are signed by this root (via chain).
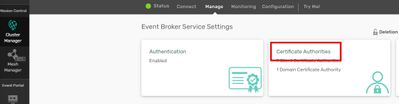
We go to “Cluster Manager”, select our Event Broker service instance and choose the “Manage” tab.
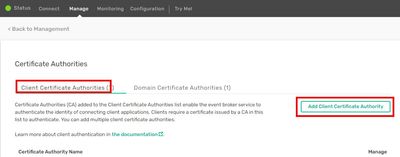
Then click “Certificate Authorities”:
We’re ready to upload our root.cert by pressing “Add Client Certificate Authority”:
We browse to our c:\solace\root.cert
and enter any name of our choice.
Save.
It may take some time to upload.
3.2. Authorization for Client
This section could also be called “Mapping between Client Cert and User”.
Remember that usually the Event Broker is accessed by users.
In our case, we don’t send a username, but a certificate.
But still, a user is required at the Broker-side.
As such, we create a new username.
This user must correspond to the client certificate.
This is done by an implicit mapping:
The new user gets a name that is identical to the “Common Name” (CN) of the client certificate.
OK.
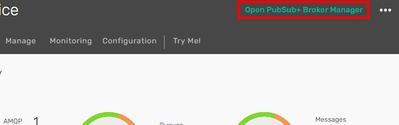
We have to go to the broker manager.
“Cluster Manager” -> Event Broker service instance
On top of the page we can jump to the “PubSub+ Broker Manager”
There, we click on “Access Control” on the left pane.
Then “Client Usernames” tab on top.
Then we click on “➕Client Username” button on the top right corner.
Now we enter the value of “CN” in our client certificate.
To save us from headache, we should copy&paste the name from our certificate.
We need the readable (decoded) certificate.
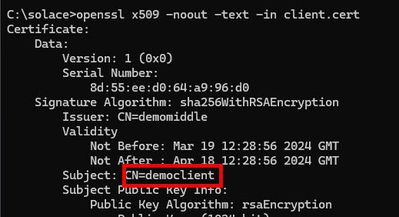
Remember the useful command?
openssl x509 -noout -text -in client.cert
The find the "Subject"
In our example, we copy "democlient" and paste it into the new username dialog.
Press “Create”.
This new user has to be enabled in the subsequent screen:
Don’t forget to save by pressing “Apply”.
3.3. Create Queue
This section could also be called “create topic”.
We just need some target to send messages to.
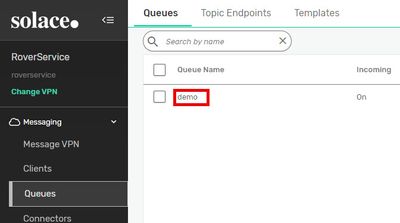
We go again to “Open PubSub+ Broker Manager” and choose “Queues” at left navigation pane.
There, we press “➕ Queue” and enter a name of our choice, e.g. “demo”:
Nice queue – but empty.
3.4. Connection Details
All certificates and configurations at Solace are useless – if we don’t connect to the broker and send messages to the (nice but empty) queue.
So we need to gather the connection details.
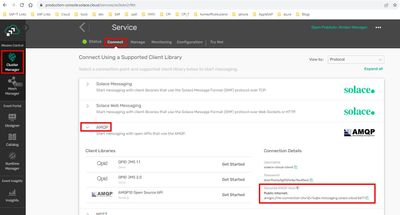
We go to “Cluster Manager” -> Event Broker service instance.
Click on “Connect” tab.
Expand AMQP section.
Copy the AMQP Host value:
The username and password can be used for Basic Auth testing.
But that's not part of our tutorial.
Next Steps
Part 4: Configure CPI, create iFlow, run scenario
Links
Solace
Solace home
Solace Event Broker Cloud Trial
The Solace dashboard entry
Docu for Solace PubSub+ Cloud
✨✨✨✨✨
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
93 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
67 -
Expert
1 -
Expert Insights
177 -
Expert Insights
301 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
346 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
430 -
Workload Fluctuations
1
- Update Public/Private Key in SFTP adapter in Technology Q&A
- General Splitter in CI - Namespace Prefix Problem in Technology Blogs by Members
- External System Integration in DMC in Technology Blogs by Members
- SAP Integration Suite - IDOC to flat file conversion in Technology Q&A
- Consuming SAP with SAP Build Apps - Mobile Apps for iOS and Android in Technology Blogs by SAP
| User | Count |
|---|---|
| 30 | |
| 17 | |
| 15 | |
| 13 | |
| 11 | |
| 9 | |
| 8 | |
| 8 | |
| 8 | |
| 7 |