
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by Members
- Privileged Access Management in SAP S/4HANA Cloud:...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Understanding the Basics:
Privileged Access Management (PAM) in the context of SAP S/4HANA Cloud is a critical aspect of cybersecurity and compliance. It serves as the cornerstone of secure cloud operations. But what exactly is PAM, and why is it so vital in the SAP ecosystem? At its core, PAM is a security solution designed to monitor and control elevated ('privileged') access within an IT environment. Privileged accounts are those that have administrative or specialized access to critical systems. In SAP S/4HANA Cloud, these accounts could include system administrators, superusers, or any account with access to sensitive data and controls.
Privileged or Emergency Access Management in SAP refers to the process of securely granting and monitoring temporary, high-level access to critical systems and data in exceptional situations while ensuring strict controls, auditability, and accountability. This access is typically granted to authorized personnel for urgent tasks and it is closely managed to minimize security risks.
The figure below explains some of the scenarios where PAM can be potentially used.

PAM Usage Scenarios
The figure below explains the PAM process for SAP S/4HANA Cloud.
- Users can create self-service requests for emergency access to systems and applications.
- Approvers, reviewers and security can review requests for emergency access and grant access.
- Compliance persons can perform periodic audit and monitoring based on usage logs.

PAM Process
The benefits of PAM are:
- Enhanced Security: PAM ensures that only authorized personnel have access to critical systems, reducing the risk of security breaches.
- Audit and Compliance: It provides detailed logging and tracking of privileged activities, which is crucial for audits and regulatory compliance.
- Least Privilege Principle: PAM enforces the principle of least privilege, where users are granted only the access necessary for their role, minimizing the potential for unauthorized access or actions.
The various terminologies used within PAM process in SAP are:
- PAM User: The IT Support User who requires the elevated access.
- PAM ID: The PAM User Id with elevated privileges.
- PAM Approver: The person(s) who approvers the PAM ID assignment to a PAM User.
- PAM Reviewer: The person(s) who reviews the log request and investigates any differences between intended and actual usage.
The PAM ID is a generic ID created in SAP IAG and backend SAP S/4HANA Cloud system.

What is a PAM ID?
Implementation Steps:
- Client Authentication Setup: This step involves creating a client ID and secret for the S/4HANA application in Identity Authentication (IAS). It is crucial for establishing a secure connection.
- Destination Creation in BTP: We then proceed to create a destination in the BTP for PAM in the IAG Subaccount.
- Privileged Access IDs Creation: This is a critical step where privileged access IDs are set up in PAM on IAG.
- Provisioning Job Execution: Finally, running the provisioning job on IAG is essential to ensure that all configurations take effect.
Prerequisites:
Before diving into the implementation of Privileged Access Management (PAM) in SAP S/4HANA Cloud, certain foundational steps must be completed. Here's what needs to be in place:
- IPS_PROXY destination has been set as per SAP documentation
- S/4HANA Cloud application setup has been completed as per SAP documentation
- Worker IDs have been created for the PAM IDs using the Manage Workforce app in S/4HANA Cloud.
- Business roles have been defined for PAM in IAG
- PAM access has been provided using BTP role collections for PAM to the administrators, approvers, reviewers, and the PAM end users. (Pre-delivered role collection CIAG_Privileged_Access)
- Access Request workflow has been set up for PAM as per SAP documentation. (Request Type: PAM and PAMREVIEW)

Request Type Rule for PAM Access Request Process
- The following communication scenarios have been added to the communication user in S/4HANA:
| SAP_COM_0193 | Identity Provisioning Integration |
| SAP_COM_0066 | SAP Cloud Identity Access Governance Integration |
| SAP_COM_0093 | Identity Management Integration |
| SAP_COM_0327 | Business User Change Document Integration |
| SAP_COM_0366 | Business Role Change Document Integration |
| SAP_COM_0750 | Security Audit Log Integration |
We started implementing PAM after we completed the implementation of the Access Request Service. So, some of these prerequisites were already in place.
Configuration Steps
Let's walk through the key configuration steps.
- Client Authentication Setup for S/4HANA Application in Identity Authentication (IAS)
To integrate with IAG, we will create a Client ID and Secret on the S/4HANA application in IAS. This is because IAG currently only supports basic authentication. You will need to use this client and secret as your user and password when setting up the BTP destination for PAM.
- Navigate to Applications and Resources Applications.
- Select the SAP S/4HANA Cloud Tenant and navigate to Trust Application APIs Client Authentication.
- Go to the Secrets section and click on Add. Enter a description and click Save.

Add a Secret in S/4HANA API Authentication on IAS
- Copy and securely store the Client and Secret values. They will be required to create the BTP destination for PAM.

Copy Client ID and Secret
- Create a destination in BTP for PAM in the IAG Subaccount
- Login to the IAG Subaccount on BTP and navigate to Connectivity Destinations.
- Create a new destination with these values:
- Name: (e.g., S4C-IAG-PAM)
- Description: PAM Destination for S/4HANA
- Type: HTTP
- Accept: */*
- Authentication: BasicAuthentication
- ProxyType: Internet
- URL: [Your IAS URL, e.g.,https://<yourtenant>.accounts.ondemand.com]
- User: [Client ID from IAS]
- Password: [Secret from IAS]
- USERSURL: /service/users

Destination for PAM in the IAG Subaccount on SAP BTP
- Update the S/4HANA destination with PAM parameters in the IAG Subaccount
Add these additional properties to the S/4HANA destination in BTP in the IAG subaccount.
- IASApplicationName: Application name of Identity Authentication system in IAG
- IASDestinationName: Name of the PAM destination created in the previous step
- IASSubjectNameIdentifier: The Subject Name Identifier used for user authentication to S/4HANA in the IAS application configuration. E.g. UserID or Email
- S4HCHomePageURL: URL to the S/4HANA system. If you have set up a corporate identity provider and if you are using IAS as a proxy then you will need the URL to bypass the corporate identity provider. This can be found under the conditional authentication of the S/4HANA application configuration in IAS.

Destination for S/4HANA Cloud in IAG Subaccount on SAP BTP
- Create Privileged Access Ids in PAM on IAG
You can now start creating the PAM Ids using the “Maintain Privileged Access” app on IAG.
- Login to IAG and navigate to Privilege Access Management tab.
- Open the app “Maintain Privileged Access”
Maintain Privileged Access App on IAG
- Click on “+” button on the right.
- In the attributes section enter all the mandatory fields.
- Name: Same as Worker ID
- Description: Provide a suitable description for the PAM ID
- Business Role: Role defined for the PAM ID in IAG
- PS: Upon selecting the business role, the Employee ID and Email fields are displayed. These fields are not displayed initially.
- Employee ID: Same as Worker ID
- Email: Same as the email provided for the Worker ID
- Criticality: Can be CRITICAL, HIGH, MEDIUM or LOW
- Duration in Days: Max number of days for which the PAM can be requested.

Attributes Section of a PAM ID on IAG
- In the allowed activities, you will be provided with a list of catalogs based on the business role assigned. Here you can select the activities for which the PAM ID is designed to be used. This is not an authorization restriction for the PAM ID. It is just for documentation purposes only.

Catalogs allowed for the PAM ID based on the assigned business role

Allowed activities section of the PAM ID on IAG
- In the Approvers / Reviewers section you will assign the users who should approve the PAM ID in the access request workflow in the “ROLE OWNER” stage and the person who will review the log access review request after the PAM ID has been used by a user. PS: All IAS users are listed for selection. There is no dependency upon any group to be assigned for users to be listed here.

Approvers and Reviewers section of the PAM ID on IAG
- Click on Save and Activate to save the PAM ID.
- Run the provisioning job on IAG
- Navigate to Administration Job Scheduler
- Provide a suitable job description and job category as Provisioning

Schedule Job for PAM ID Provisioning on IAG
- Click on Schedule Job
- Navigate to the Job History App to confirm that the PAM ID has been provisioned in the S/4HANA Cloud backend system.

Log of Provisioned PAM ID in the Job History app on IAG
- Login to the backend S/4HANA Cloud to ensure the account has been created.

PAM ID displayed in Maintain Business Users app on S/4HANA Cloud
PAM Access Request Process
The Access Request app now allows you to request the PAM ID. Simply search for the PAM ID you need using the search field, or filter by “Access Type = Privilege Access”.

Search for PAM ID in Access Request on IAG
Once the PAM end user submits the request, the access request workflow for the "PAM" request type will be triggered. Note, the PAM end user is any IT support user who requires elevated access to perform a critical task in Production.
The defined workflow will send the request to the appropriate approver. In the case below, the approver is the PAM Owner defined in the Maintain Privileged Access app on the PAM ID. You can define your own workflow stages and have multiple stage approval as well as multiple approvers for a stage (except the Manager stage).
Note that the access request inbox for approving PAM requests is under the Privileged Access Management tab and the app is called "Privileged Access Request – Inbox”. This can cause confusion for approvers because the normal tendency would be to check the "Access Request - Inbox". I hope that in future releases SAP would consolidate the different inboxes of the services that have workflow capabilities on IAG.

Approval work item in Privileged Access Request – Inbox app on IAG

PAM Request Details for Approval on IAG
Once the request is approved, the user who made the request is assigned an ID.
PAM Execution
The PAM end user can now log in to IAG and execute the PAM ID session using the "PAM Execute Session" application.

Assigned PAM ID displayed in PAM Execute Session app on IAG
Upon clicking “Execute Session”, the user is presented with a popup with a link to activate the PAM ID.

Access Link to activate PAM ID for the session
Click the link to open a new tab. The message displayed states that you are required to sign out from the current application to activate the new account. Click on Sign out and continue.

Sign Out page for activating the PAM ID
On the next page, enter a password for the account and click on continue.

IAS Password entry page for activating PAM ID
You will now be logged in to the target S/4HANA Cloud system with the PAM ID.

S/4HANA Account to confirm the logged in PAM ID
If you go to your IAS Tenant and navigate to the User Management section, you will see that the PAM ID is created after this step. Once the PAM session is terminated, the ID will be removed from IAS. This process will be repeated each time the user logs in and terminates the PAM session.

IAS User Management displaying the activated PAM ID
Once you have completed the PAM tasks, sign out of the PAM ID from S/4HANA.

PAM Sign Out after completion of the session tasks
Navigate back to the IAG tab. If you have been logged out of IAG then close the browser and log back into IAG using a new browser window. Navigate back to the “PAM Execute Session” app.

PAM Execute Session app on IAG after Signing Out of PAM from S/4HANA
Click on “Terminate Session”. A pop up message confirms that the session has been terminated.
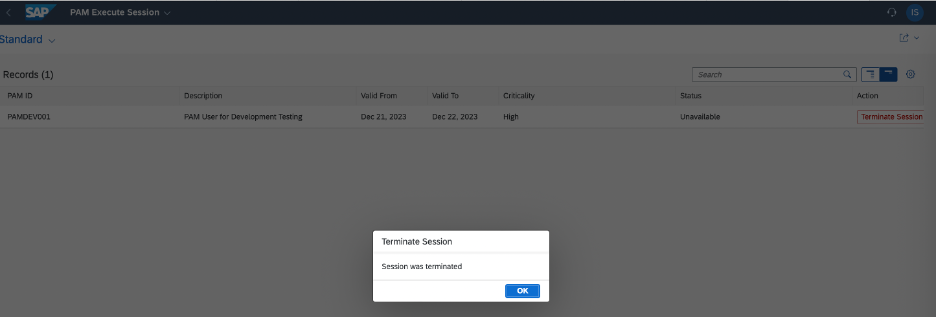
Termination Confirmation
The “Execute Session” button is displayed once again.

PAM Execute Session app on IAG after session is terminated
If you check the user in IAS you will find that the user has been deleted.

PAM ID is deleted from IAS after session is terminated
PAM Log generation and review
To proceed, we need to schedule the Log Sync and Access Request Review jobs. It's recommended to schedule these jobs to run regularly, particularly in a production scenario.
Using the Job Scheduler application on IAG, you can schedule the "Privileged Access Log Sync" job. This job syncs the logs from the S/4HANA backend system to IAG.

Scheduling the Privileged Access Log Sync Job on IAG
Check the Job History to confirm the job is completed. Next use the Job scheduler app on IAG, to schedule the “Privileged Access Review Request” Job.

Scheduling the Privileged Access Review Request job on IAG
The second job creates a log review request and sends it to the PAM ID reviewer for approval. The PAM reviewer can access the PAM Logs review request in the app “Privileged Access Monitoring – Inbox”.

Log review work item in Privileged Access Monitoring – Inbox app on IAG
The log review request has three files as attachment.
- Business Role Changes: An excel file with changes made to the business role using the PAM ID during that PAM session.
- Business User Changes: An excel file with changes made to any business users using the PAM ID during that PAM session.
- Security Audit Log: An excel file with the details of the login session and the apps used during the PAM session.

Log attachments for the PAM session in the review work item
Important Note on PAM Log File Generation
As of the writing of this content, there is a known challenge with the consistent generation of log files in the Privileged Access Management (PAM) system. This issue primarily arises from a timing discrepancy between the PAM log generation process on SAP Cloud Identity Access Governance (IAG) and the synchronization with the SAP S/4HANA backend system. SAP is actively aware of this issue and is diligently working towards a resolution.
In the interim, SAP has proposed a manual workaround for this issue. It involves the use of the "Click to upload attachment" feature to manually add log files from the SAP backend system. This method ensures that crucial log files are not missed and maintains a comprehensive audit trail for privileged access activities.
To aid in the prioritization and rapid resolution of this issue, I have initiated a customer influence request. If you, like many others, are keen on seeing a more streamlined and automated solution to this log file generation challenge, your support would be invaluable. By voting on this customer influence request, you can significantly contribute to highlighting the importance of this issue to SAP, thereby potentially accelerating its resolution.
https://influence.sap.com/sap/ino/#/idea/314189
Completing the Privileged Access Management Cycle
The final step in the Privileged Access Management (PAM) process within SAP S/4HANA Cloud is crucial and signifies the completion of a comprehensive cycle of secure access management. Once a PAM ID has been used, it undergoes a thorough review process. This review is essential to ensure that the privileged access was utilized appropriately and by the established guidelines and policies.
The PAM reviewer, a designated authority within the system, plays a pivotal role at this juncture. After the PAM ID usage, the reviewer meticulously examines the access logs and activities performed. This step is not just a formality but a critical component of maintaining the integrity and security of the system. It helps in identifying any discrepancies, unauthorized activities, or potential security risks.
Upon a detailed review, when the PAM reviewer approves the review request, it marks the successful conclusion of the PAM process. This approval indicates that the privileged access was managed, executed, and reviewed in line with the stringent security standards set by the organization.
- SAP Managed Tags:
- SAP Cloud Identity Access Governance,
- SAP S/4HANA Public Cloud
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
"automatische backups"
1 -
"regelmäßige sicherung"
1 -
"TypeScript" "Development" "FeedBack"
1 -
505 Technology Updates 53
1 -
ABAP
14 -
ABAP API
1 -
ABAP CDS Views
2 -
ABAP CDS Views - BW Extraction
1 -
ABAP CDS Views - CDC (Change Data Capture)
1 -
ABAP class
2 -
ABAP Cloud
3 -
ABAP Development
5 -
ABAP in Eclipse
1 -
ABAP Platform Trial
1 -
ABAP Programming
2 -
abap technical
1 -
abapGit
1 -
absl
2 -
access data from SAP Datasphere directly from Snowflake
1 -
Access data from SAP datasphere to Qliksense
1 -
Accrual
1 -
action
1 -
adapter modules
1 -
Addon
1 -
Adobe Document Services
1 -
ADS
1 -
ADS Config
1 -
ADS with ABAP
1 -
ADS with Java
1 -
ADT
2 -
Advance Shipping and Receiving
1 -
Advanced Event Mesh
3 -
AEM
1 -
AI
7 -
AI Launchpad
1 -
AI Projects
1 -
AIML
9 -
Alert in Sap analytical cloud
1 -
Amazon S3
1 -
Analytical Dataset
1 -
Analytical Model
1 -
Analytics
1 -
Analyze Workload Data
1 -
annotations
1 -
API
1 -
API and Integration
3 -
API Call
2 -
API security
1 -
Application Architecture
1 -
Application Development
5 -
Application Development for SAP HANA Cloud
3 -
Applications and Business Processes (AP)
1 -
Artificial Intelligence
1 -
Artificial Intelligence (AI)
5 -
Artificial Intelligence (AI) 1 Business Trends 363 Business Trends 8 Digital Transformation with Cloud ERP (DT) 1 Event Information 462 Event Information 15 Expert Insights 114 Expert Insights 76 Life at SAP 418 Life at SAP 1 Product Updates 4
1 -
Artificial Intelligence (AI) blockchain Data & Analytics
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise Oil Gas IoT Exploration Production
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise sustainability responsibility esg social compliance cybersecurity risk
1 -
ASE
1 -
ASR
2 -
ASUG
1 -
Attachments
1 -
Authorisations
1 -
Automating Processes
1 -
Automation
2 -
aws
2 -
Azure
1 -
Azure AI Studio
1 -
Azure API Center
1 -
Azure API Management
1 -
B2B Integration
1 -
Backorder Processing
1 -
Backup
1 -
Backup and Recovery
1 -
Backup schedule
1 -
BADI_MATERIAL_CHECK error message
1 -
Bank
1 -
BAS
1 -
basis
2 -
Basis Monitoring & Tcodes with Key notes
2 -
Batch Management
1 -
BDC
1 -
Best Practice
1 -
bitcoin
1 -
Blockchain
3 -
bodl
1 -
BOP in aATP
1 -
BOP Segments
1 -
BOP Strategies
1 -
BOP Variant
1 -
BPC
1 -
BPC LIVE
1 -
BTP
13 -
BTP Destination
2 -
Business AI
1 -
Business and IT Integration
1 -
Business application stu
1 -
Business Application Studio
1 -
Business Architecture
1 -
Business Communication Services
1 -
Business Continuity
1 -
Business Data Fabric
3 -
Business Fabric
1 -
Business Partner
12 -
Business Partner Master Data
10 -
Business Technology Platform
2 -
Business Trends
4 -
BW4HANA
1 -
CA
1 -
calculation view
1 -
CAP
4 -
Capgemini
1 -
CAPM
1 -
Catalyst for Efficiency: Revolutionizing SAP Integration Suite with Artificial Intelligence (AI) and
1 -
CCMS
2 -
CDQ
12 -
CDS
2 -
Cental Finance
1 -
Certificates
1 -
CFL
1 -
Change Management
1 -
chatbot
1 -
chatgpt
3 -
CL_SALV_TABLE
2 -
Class Runner
1 -
Classrunner
1 -
Cloud ALM Monitoring
1 -
Cloud ALM Operations
1 -
cloud connector
1 -
Cloud Extensibility
1 -
Cloud Foundry
4 -
Cloud Integration
6 -
Cloud Platform Integration
2 -
cloudalm
1 -
communication
1 -
Compensation Information Management
1 -
Compensation Management
1 -
Compliance
1 -
Compound Employee API
1 -
Configuration
1 -
Connectors
1 -
Consolidation Extension for SAP Analytics Cloud
2 -
Control Indicators.
1 -
Controller-Service-Repository pattern
1 -
Conversion
1 -
Cosine similarity
1 -
cryptocurrency
1 -
CSI
1 -
ctms
1 -
Custom chatbot
3 -
Custom Destination Service
1 -
custom fields
1 -
Customer Experience
1 -
Customer Journey
1 -
Customizing
1 -
cyber security
3 -
cybersecurity
1 -
Data
1 -
Data & Analytics
1 -
Data Aging
1 -
Data Analytics
2 -
Data and Analytics (DA)
1 -
Data Archiving
1 -
Data Back-up
1 -
Data Flow
1 -
Data Governance
5 -
Data Integration
2 -
Data Quality
12 -
Data Quality Management
12 -
Data Synchronization
1 -
data transfer
1 -
Data Unleashed
1 -
Data Value
8 -
database tables
1 -
Datasphere
3 -
datenbanksicherung
1 -
dba cockpit
1 -
dbacockpit
1 -
Debugging
2 -
Defender
1 -
Delimiting Pay Components
1 -
Delta Integrations
1 -
Destination
3 -
Destination Service
1 -
Developer extensibility
1 -
Developing with SAP Integration Suite
1 -
Devops
1 -
digital transformation
1 -
Documentation
1 -
Dot Product
1 -
DQM
1 -
dump database
1 -
dump transaction
1 -
e-Invoice
1 -
E4H Conversion
1 -
Eclipse ADT ABAP Development Tools
2 -
edoc
1 -
edocument
1 -
ELA
1 -
Embedded Consolidation
1 -
Embedding
1 -
Embeddings
1 -
Employee Central
1 -
Employee Central Payroll
1 -
Employee Central Time Off
1 -
Employee Information
1 -
Employee Rehires
1 -
Enable Now
1 -
Enable now manager
1 -
endpoint
1 -
Enhancement Request
1 -
Enterprise Architecture
1 -
ESLint
1 -
ETL Business Analytics with SAP Signavio
1 -
Euclidean distance
1 -
Event Dates
1 -
Event Driven Architecture
1 -
Event Mesh
2 -
Event Reason
1 -
EventBasedIntegration
1 -
EWM
1 -
EWM Outbound configuration
1 -
EWM-TM-Integration
1 -
Existing Event Changes
1 -
Expand
1 -
Expert
2 -
Expert Insights
2 -
Exploits
1 -
Fiori
14 -
Fiori Elements
2 -
Fiori SAPUI5
12 -
first-guidance
1 -
Flask
1 -
FTC
1 -
Full Stack
8 -
Funds Management
1 -
gCTS
1 -
General
1 -
Generative AI
1 -
Getting Started
1 -
GitHub
9 -
Grants Management
1 -
groovy
1 -
GTP
1 -
HANA
6 -
HANA Cloud
2 -
Hana Cloud Database Integration
2 -
HANA DB
2 -
HANA XS Advanced
1 -
Historical Events
1 -
home labs
1 -
HowTo
1 -
HR Data Management
1 -
html5
8 -
HTML5 Application
1 -
Identity cards validation
1 -
idm
1 -
Implementation
1 -
input parameter
1 -
instant payments
1 -
Integration
3 -
Integration Advisor
1 -
Integration Architecture
1 -
Integration Center
1 -
Integration Suite
1 -
intelligent enterprise
1 -
iot
1 -
Java
1 -
job
1 -
Job Information Changes
1 -
Job-Related Events
1 -
Job_Event_Information
1 -
joule
4 -
Journal Entries
1 -
Just Ask
1 -
Kerberos for ABAP
8 -
Kerberos for JAVA
8 -
KNN
1 -
Launch Wizard
1 -
Learning Content
2 -
Life at SAP
5 -
lightning
1 -
Linear Regression SAP HANA Cloud
1 -
Loading Indicator
1 -
local tax regulations
1 -
LP
1 -
Machine Learning
2 -
Marketing
1 -
Master Data
3 -
Master Data Management
14 -
Maxdb
2 -
MDG
1 -
MDGM
1 -
MDM
1 -
Message box.
1 -
Messages on RF Device
1 -
Microservices Architecture
1 -
Microsoft Universal Print
1 -
Middleware Solutions
1 -
Migration
5 -
ML Model Development
1 -
Modeling in SAP HANA Cloud
8 -
Monitoring
3 -
MTA
1 -
Multi-Record Scenarios
1 -
Multiple Event Triggers
1 -
Myself Transformation
1 -
Neo
1 -
New Event Creation
1 -
New Feature
1 -
Newcomer
1 -
NodeJS
3 -
ODATA
2 -
OData APIs
1 -
odatav2
1 -
ODATAV4
1 -
ODBC
1 -
ODBC Connection
1 -
Onpremise
1 -
open source
2 -
OpenAI API
1 -
Oracle
1 -
PaPM
1 -
PaPM Dynamic Data Copy through Writer function
1 -
PaPM Remote Call
1 -
PAS-C01
1 -
Pay Component Management
1 -
PGP
1 -
Pickle
1 -
PLANNING ARCHITECTURE
1 -
Popup in Sap analytical cloud
1 -
PostgrSQL
1 -
POSTMAN
1 -
Prettier
1 -
Process Automation
2 -
Product Updates
5 -
PSM
1 -
Public Cloud
1 -
Python
4 -
python library - Document information extraction service
1 -
Qlik
1 -
Qualtrics
1 -
RAP
3 -
RAP BO
2 -
Record Deletion
1 -
Recovery
1 -
recurring payments
1 -
redeply
1 -
Release
1 -
Remote Consumption Model
1 -
Replication Flows
1 -
research
1 -
Resilience
1 -
REST
1 -
REST API
1 -
Retagging Required
1 -
Risk
1 -
Rolling Kernel Switch
1 -
route
1 -
rules
1 -
S4 HANA
1 -
S4 HANA Cloud
1 -
S4 HANA On-Premise
1 -
S4HANA
3 -
S4HANA_OP_2023
2 -
SAC
10 -
SAC PLANNING
9 -
SAP
4 -
SAP ABAP
1 -
SAP Advanced Event Mesh
1 -
SAP AI Core
8 -
SAP AI Launchpad
8 -
SAP Analytic Cloud Compass
1 -
Sap Analytical Cloud
1 -
SAP Analytics Cloud
4 -
SAP Analytics Cloud for Consolidation
3 -
SAP Analytics Cloud Story
1 -
SAP analytics clouds
1 -
SAP API Management
1 -
SAP BAS
1 -
SAP Basis
6 -
SAP BODS
1 -
SAP BODS certification.
1 -
SAP BTP
21 -
SAP BTP Build Work Zone
2 -
SAP BTP Cloud Foundry
6 -
SAP BTP Costing
1 -
SAP BTP CTMS
1 -
SAP BTP Innovation
1 -
SAP BTP Migration Tool
1 -
SAP BTP SDK IOS
1 -
SAP BTPEA
1 -
SAP Build
11 -
SAP Build App
1 -
SAP Build apps
1 -
SAP Build CodeJam
1 -
SAP Build Process Automation
3 -
SAP Build work zone
10 -
SAP Business Objects Platform
1 -
SAP Business Technology
2 -
SAP Business Technology Platform (XP)
1 -
sap bw
1 -
SAP CAP
2 -
SAP CDC
1 -
SAP CDP
1 -
SAP CDS VIEW
1 -
SAP Certification
1 -
SAP Cloud ALM
4 -
SAP Cloud Application Programming Model
1 -
SAP Cloud Integration for Data Services
1 -
SAP cloud platform
8 -
SAP Companion
1 -
SAP CPI
3 -
SAP CPI (Cloud Platform Integration)
2 -
SAP CPI Discover tab
1 -
sap credential store
1 -
SAP Customer Data Cloud
1 -
SAP Customer Data Platform
1 -
SAP Data Intelligence
1 -
SAP Data Migration in Retail Industry
1 -
SAP Data Services
1 -
SAP DATABASE
1 -
SAP Dataspher to Non SAP BI tools
1 -
SAP Datasphere
9 -
SAP DRC
1 -
SAP EWM
1 -
SAP Fiori
3 -
SAP Fiori App Embedding
1 -
Sap Fiori Extension Project Using BAS
1 -
SAP GRC
1 -
SAP HANA
1 -
SAP HCM (Human Capital Management)
1 -
SAP HR Solutions
1 -
SAP IDM
1 -
SAP Integration Suite
9 -
SAP Integrations
4 -
SAP iRPA
2 -
SAP LAGGING AND SLOW
1 -
SAP Learning Class
1 -
SAP Learning Hub
1 -
SAP Master Data
1 -
SAP Odata
2 -
SAP on Azure
2 -
SAP PartnerEdge
1 -
sap partners
1 -
SAP Password Reset
1 -
SAP PO Migration
1 -
SAP Prepackaged Content
1 -
SAP Process Automation
2 -
SAP Process Integration
2 -
SAP Process Orchestration
1 -
SAP S4HANA
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Cloud for Finance
1 -
SAP S4HANA Cloud private edition
1 -
SAP Sandbox
1 -
SAP STMS
1 -
SAP successfactors
3 -
SAP SuccessFactors HXM Core
1 -
SAP Time
1 -
SAP TM
2 -
SAP Trading Partner Management
1 -
SAP UI5
1 -
SAP Upgrade
1 -
SAP Utilities
1 -
SAP-GUI
8 -
SAP_COM_0276
1 -
SAPBTP
1 -
SAPCPI
1 -
SAPEWM
1 -
sapfirstguidance
1 -
SAPHANAService
1 -
SAPIQ
1 -
sapmentors
1 -
saponaws
2 -
SAPS4HANA
1 -
SAPUI5
5 -
schedule
1 -
Script Operator
1 -
Secure Login Client Setup
8 -
security
9 -
Selenium Testing
1 -
Self Transformation
1 -
Self-Transformation
1 -
SEN
1 -
SEN Manager
1 -
service
1 -
SET_CELL_TYPE
1 -
SET_CELL_TYPE_COLUMN
1 -
SFTP scenario
2 -
Simplex
1 -
Single Sign On
8 -
Singlesource
1 -
SKLearn
1 -
Slow loading
1 -
soap
1 -
Software Development
1 -
SOLMAN
1 -
solman 7.2
2 -
Solution Manager
3 -
sp_dumpdb
1 -
sp_dumptrans
1 -
SQL
1 -
sql script
1 -
SSL
8 -
SSO
8 -
Substring function
1 -
SuccessFactors
1 -
SuccessFactors Platform
1 -
SuccessFactors Time Tracking
1 -
Sybase
1 -
system copy method
1 -
System owner
1 -
Table splitting
1 -
Tax Integration
1 -
Technical article
1 -
Technical articles
1 -
Technology Updates
15 -
Technology Updates
1 -
Technology_Updates
1 -
terraform
1 -
Threats
2 -
Time Collectors
1 -
Time Off
2 -
Time Sheet
1 -
Time Sheet SAP SuccessFactors Time Tracking
1 -
Tips and tricks
2 -
toggle button
1 -
Tools
1 -
Trainings & Certifications
1 -
Transformation Flow
1 -
Transport in SAP BODS
1 -
Transport Management
1 -
TypeScript
3 -
ui designer
1 -
unbind
1 -
Unified Customer Profile
1 -
UPB
1 -
Use of Parameters for Data Copy in PaPM
1 -
User Unlock
1 -
VA02
1 -
Validations
1 -
Vector Database
2 -
Vector Engine
1 -
Visual Studio Code
1 -
VSCode
2 -
VSCode extenions
1 -
Vulnerabilities
1 -
Web SDK
1 -
work zone
1 -
workload
1 -
xsa
1 -
XSA Refresh
1
- « Previous
- Next »
- Sapphire 2024 user experience and application development sessions in Technology Blogs by SAP
- Enhance your SAP Datasphere Experience with API Access in Technology Blogs by SAP
- Consuming SAP with SAP Build Apps - Mobile Apps for iOS and Android in Technology Blogs by SAP
- Streamlining Time Sheet Approvals in SuccessFactors: Time Sheet Approval Center in Technology Blogs by Members
- Introducing Blog Series of SAP Signavio Process Insights, discovery edition – An in-depth exploratio in Technology Blogs by SAP
| User | Count |
|---|---|
| 8 | |
| 7 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 | |
| 4 | |
| 3 | |
| 3 |