- SAP Community
- Products and Technology
- Technology
- Technology Blogs by Members
- Exploring SAP Secure Login Service for SAP GUI: A ...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
[Last Update 2024.03.01]
Hello fellow SAP security enthusiasts!
I wanted to share some exciting news with you. I've been busy creating a couple of LinkedIn blogs that delve into the fascinating world of the SAP Secure Login Service for SAP GUI. As I was exploring this topic, I thought, why not bring all this valuable knowledge together into one comprehensive blog post?
I hope you enjoy reading it as much as I enjoyed writing it!
TOC
Introduction
Multiple Factors Propel SAP's Move Towards New Solution for Enhanced Authentication
Brief Overview of the SAP Secure Login Service for SAP GUI
Background
Embracing Change: Switching from Active Directory to Native Azure AD Environments
Ramifications on SAP Authentication Landscape
The Migration to Azure AD
The Exodus of Kerberos
Introducing Azure Active Directory Domain Services
The Implications for SAP GUI
HTTP-Driven SAP Applications and SAML 2.0
Exploring the SAP Secure Login Service for SAP GUI: An In-Depth Review
Basic Setup of the Service (SAP BTP & IAS)
Customization Options for X.509 DN in Issued Certificates
Certificate Chain of the SAP-Managed PKI
Aspects and Some Nice Features of SNC User Mapping
What's Still Missing and What Could Come Nex
Compilation of frequently asked questions
Introduction
The highly anticipated SAP Secure Login Service for SAP GUI has emerged as a testament to innovation, merging the stalwart functionality of the esteemed SAP Single Sign-On with the expansive capabilities of cloud computing.
On May 4, 2023, SAP introduced the SAP Secure Login Service for SAP GUI, a cloud-centric solution that advances the concept of single sign-on. For comprehensive details, I direct your attention to the Release Blog post available here
By opting to retire the traditional AS Java platform, not only are cost efficiencies achieved but resource optimization is also realized. With a rhythmic alignment with Kerberos and X.509, coupled with seamless integration into cloud-driven identity frameworks, the opportune moment has arrived to engage with the SAP SSO cohort. The SAP Secure Login Service (SLS) builds upon the bedrock of SAP Single Sign-On, elevating the single sign-on experience to the cloud milieu. Embrace a lean cloud service seamlessly harmonizing with your corporate identity provider, as you embark on this transformative journey.

Source: SAP Secure Login Service for SAP GUI - Solution Overview
Multiple Factors Propel SAP's Move Towards New Solution for Enhanced Authentication
Let's begin by examining the key drivers behind SAP's introduction of this new solution. Currently, SAP SSO 3.0 remains in maintenance mode, with no new feature integrations from SAP. Notably, there are no plans for the release of Version 4.0.
Over time, certain scenarios have become obsolete, magnifying the demand to transition specific components (such as the Secure Login Server) to the cloud, a demand that has grown increasingly pronounced in recent years.
With the expansion of IT infrastructures reliant on cloud-native technologies and Azure AD, and in the absence of Active Directory (AD), there exists a pressing requirement for Multi-Factor Authentication (MFA) within the SAP GUI environment. The retirement of SAP AS Java has emerged as a pivotal factor thus far, underscoring the multifaceted motivations driving this shift. Indeed, it appears that a multitude of reasons converge to shape this transition.
Brief Overview of the SAP Secure Login Service for SAP GUI
The SAP Secure Login Service for SAP GUI is a multi-tenant SAP Business Technology Platform (BTP) cloud application designed to facilitate multifactor authentication (MFA) and single sign-on (SSO) when utilizing the SAP GUI interface.
Building upon the achievements of SAP Single Sign-On, the Secure Login Service (SLS) preserves its core functionalities while enhancing them to align with the demands of the cloud era. It seamlessly integrates with cloud-based identity providers, reinforcing authentication and single sign-on for business applications. By establishing connections with central authentication solutions like identity providers, this service streamlines access, enhances user efficiency, and reinforces data security through robust authentication methods.
It's all about keeping things simple and secure for your SAP GUI users. This new solution comes packed with a whole set of enhanced capabilities. One of the coolest things about this cloud-powered gem is the way it handles X.509 certificates. No more fussing around with on-premise servers or SAP NetWeaver Application Server Java. The cloud service takes care of all the certificate enrollment, leaving you with more time to binge-watch your favorite shows. So long, AS Java!
But wait, there's more! You can now flex your existing identity provider solution, like SAP Cloud Identity Services or other popular ones such as Microsoft Azure Active Directory and Okta. These authentication superheroes bring their mighty multi-factor authentication powers to the table, ensuring only the worthy can access your SAP GUI kingdom.
Highlights:
- Secure Login Client can authenticate SAP users based on the SAML standard (SAML & X.509).
- Supports SSO and MFA for SAP GUI without the need for a SAP NetWeaver AS Java instance (SLS).
- Enables previously missing functionalities such as SAP GUI SSO integration with SAML IdPs and MFA for SAP GUI without AS Java (SAP Secure Login Server).
- Provides an alternative to the Kerberos scenario (e.g. in pure Azure AD environments without KDC).
How it works in a nutshell:
- The Secure Login Client communicates with the new cloud service which can authenticate the user through IAS and/or an existing Corporate IdP (Azure|ADFS|Okta...).
- The "SLS in the Cloud" (user certificate service) issues a temporary SSO certificate.
- Technically, (after the SAML flow) this still involves an SNC connection with X.509 CBA (certificate-based authentication) to the AS ABAP or S/4HANA system.

Source: SAP Secure Login Service for SAP GUI - Solution Overview
Key Features:
- Configuration is based on your SAP Cloud Identity Services tenant or corporate Identity Provider (IdP). Various authentication factors such as passwords, Time-Based One-Time Password (TOTP) tokens, local X.509 certificates, and authentication devices like Windows Hello, macOS Touch ID, or FIDO can be configured.
- The Software-as-a-Service (SaaS) application offers a web-based user interface (UI) for administrative purposes. While the current Secure Login Service Web UI has limited settings, it's anticipated that additional features will be added in the future.
- Authentication takes place within an embedded web browser (part of the Secure Login Client in Windows) or the standard web browser (macOS version), contributing to an excellent user experience.
- Successful user authentication yields a short-lived user certificate, usable for Secure Network Communication (SNC), Secure Store and Forward (SSF), or Transport Layer Security (TLS).
- Users can authenticate to an AS ABAP (Advanced Business Application Programming) using X.509 certificates and Kerberos via SNC communication.
- Notably, the migration to the new service can be carried out seamlessly in parallel without disrupting the existing setup.

Source: SAP Secure Login Service for SAP GUI - Solution Overview
For more information, you can refer to the solution overview provided in this link: https://www.sap.com/documents/2023/05/50bf62e4-707e-0010-bca6-c68f7e60039b.html
To delve deeper into the topic of SAP Secure Login Service for SAP GUI, we recommend exploring the following resources for comprehensive information:
- Product overview presentation from SAP
- Documentation on SAP Help
Background
Before delving into the depths, let us initially provide a concise overview of why the current topic of Active Directory / Azure Active Directory holds relevance.
Embracing Change: Switching from Active Directory to Native Azure AD Environments
In the dynamic landscape of technological evolution, change stands as a pivotal determinant. Currently, a significant paradigm shift is underway, marked by the transition from conventional Active Directory (AD) environments to the native constructs of Azure Active Directory (AAD).
Especially prevalent in the initiatives of nascent enterprises commencing from their inception, a pronounced inclination towards a cloud-exclusive approach is often observed. In such scenarios, the conventional notion of a Domain, as commonly understood, may indeed lose its pertinence or operative status.
By harnessing the capabilities of cloud-based services and platforms, many organizations effectively obviate the need for traditional, on-premises domains, allowing them to fully leverage the advantages inherent to a cloud-native milieu. Facilitated by robust identity and access management solutions offered by cloud service providers, these enterprises can orchestrate secure and streamlined operations, thereby concentrating their efforts on fundamental business imperatives.
As these forward-looking entities wholeheartedly embrace the cloud as their principal infrastructure, they reap the rewards of its inherent flexibility, scalability, and cost-efficiency. Concurrently, the prevalence of cloud-native solutions and platforms renders the requirement for on-premises domains progressively obsolete, enabling enterprises to harness the potency of cloud services to fulfill both their IT and business prerequisites.
By committing to a cloud-exclusive methodology, these enterprises fully harness the capabilities proffered by cloud giants such as Microsoft Azure, AWS, or Google Cloud. They architect their infrastructure, applications, and services directly atop these platforms, capitalizing on the innate security, scalability, and availability features inherent in the cloud paradigm.
This transition toward an exclusive cloud-centric approach affords enterprises the luxury of concentrating on core business pursuits, unfettered by the complexities of managing and upkeeping conventional on-premises domains. Instead, they avail themselves of the cloud provider's infrastructure, empowering swift deployment and scalability of applications and services congruent with their burgeoning operations.
Furthermore, by embracing cloud-native offerings such as Azure Active Directory, enterprises can still uphold stringent access management and identity federation protocols without necessitating an on-premises domain. Azure AD extends an all-encompassing spectrum of identity and access management capabilities, encompassing Single Sign-On (SSO), Multi-Factor Authentication (MFA), and Conditional Access policies, seamlessly amalgamating with cloud-centric environments.
Ramifications on SAP Authentication Landscape
Thus, esteemed readers, let us pivot our attention to the trajectory of transition toward Azure's cloud-native approach and the ensuing implications on your SAP SSO landscape, particularly if you have traditionally relied on Kerberos authentication and have not yet traversed the realm of X.509 certificates for SAP GUI authentication.
The Migration to Azure AD
A growing cohort of global enterprises is unequivocally embracing the Azure and Intune ecosystem, bidding adieu to the conventional AD-domain construct. With Azure AD, clients emancipate themselves from the shackles of internal Active Directory systems, signifying the discontinuation of domain controllers and the prevailing of Kerberos Key Distribution Centers (KDCs). A farewell to erstwhile companions, indeed!
The Exodus of Kerberos
In the SAP domain, our endeavors have perennially revolved around realizing a seamless SSO experience via Kerberos authentication. However, in the nascent domain of Azure AD, this approach no longer retains its efficacy. The absence of domain controllers renders our cherished SAP GUI SSO solution, founded on SNC with Kerberos tokens, no longer as efficacious.
Introducing Azure Active Directory Domain Services
At this point, you might ask, "Can we use Kerberos in these new infrastructures?" The answer is found in Azure Active Directory Domain Services, which is like having two Domain Controllers offered as a service – quite a complex setup. When there's a noticeable lack of an LDAP infrastructure, some businesses might consider using these services to meet this need. I haven't had much experience with SAP SSO combined with these services so far. However, I'm keen to learn from anyone who has explored this option.
The Implications for SAP GUI
This technological shift undoubtedly impinges on SAP GUI. Ensuring encryption and SSO mandates continued safeguarding of all SAP proprietary DIAG and RFC communications through Secure Network Communications (SNC). Consequently, the necessity for the SAP SSO 3.0 solution (Secure Login Client) on client-side installations remains relatively unchanged within this novel framework.
HTTP-Driven SAP Applications and SAML 2.0
In recent times, SAML 2.0 has become the central standard in the SAP environment, especially for applications that operate over HTTP. Within the SAP ecosystem, which includes AS ABAP, AS Java, S/4HANA, and HANA DB, these systems act as service providers. They work together seamlessly with either the Azure Identity Provider (IDP) or the Identity Authentication Service (IAS), both of which are aligned with Azure AD. This forms a harmonious collaboration, like a symphony of interconnected champions.
When integrated with Azure AD, a world of opportunities emerges, with SAML 2.0 playing a pivotal role in single sign-on technology. This leads to the implementation of Conditional Access, Multi-Factor Authentication, and Intune policies for device recognition – a collection of security measures that can be likened to having your own team of security superheroes.
In the realm of SAP, whether within the On-Premises milieu or the SAP Cloud continuum (encompassing SaaS/BTP), the ascendancy of SAP Cloud Identity Services and SAP IAS remains unchallenged, serving as the paragons of Identity Providers. The integration with Azure AD not only remains a viable proposition but also avails itself of a multitude of advantages. For an in-depth elucidation, I direct your attention to this blog post.
SAP Cloud Identity Services
- Ideal for browser-based SAP access
- Enables SSO across cloud and on-premises apps
- Simplifies IAM for unified landscapes
- Supports SAML and OpenID Connect
SAP Single Sign-On 3.0
- Crucial for SAP GUI and on-premise systems
- Utilizes X.509 certificates or Kerberos (SNC)
- Ensures end-user SSO in various scenarios
SAP Secure Login Service for SAP GUI
- Official successor to SAP Single Sign-On 3.0 (post-2027)
- Enhances SAP GUI security
- Enables SAML-based authentication with Secure Login Client
- Integrates with existing SAML Identity Providers via SAP IAS
- Offers MFA support for SAP GUI, even without SAP NetWeaver AS Java (SLS)
- Replacement for Kerberos in pure Azure AD (Entra ID) environments
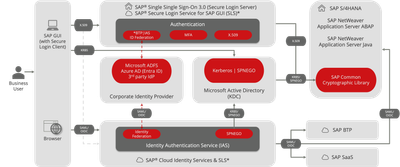
Big Picture: Authentication and SSO in a hybrid SAP system landscape

This graphic combines these three solutions to address your IAM and SSO needs, delivering a secure and user-friendly experience in your SAP landscape
Exploring the SAP Secure Login Service for SAP GUI: An In-Depth Review
In this chapter, you can expect the following:
- Information about the basic setup of the service (SAP BTP & IAS)
- Customization options for the X.509 DN of issued certificates
- Insights and some niceties about SNC User Mapping
- What's still missing and what could potentially be added in the future
Basic Setup of the Service (SAP BTP & IAS)
I was genuinely impressed by how straightforward the setup process is! While a few steps need to be followed, they are quite easy to manage. At a high level, without delving too deeply into the specifics, here are the 10 steps to success:
- License Assignment (Global Account Level): Assign the license to your Global Account (SAP SE).
- Define target BTP Subaccount: Establish a new BTP subaccount dedicated to the Secure Login Service (SLS).
- Trust Establishment: Establish trust between the SLS subaccount and your Identity Authentication Service (IAS) tenant.
- Configure Entitlement: Set up the entitlement and link the service to the SLS subaccount.
- Subscription: Subscribe to the Secure Login Service and generate a service instance.
- Group Setup in IAS: Create groups in IAS to control access to the Secure Login Service web UI.
- SSO Certificate Lifetime Configuration: Configure the lifespan of Single Sign-On (SSO) certificates in the SLS web UI.
- Common Name Attribute Setup: Establish the Common Name attribute for user certificates in IAS.
- Secure Login Client Deployment, Configuration and Policy Loading: Configure the Secure Login Client and provide the policy.
- Customization of SNC Names and CERTRULE: Customize the Secure Network Communication (SNC) names and certificate rules.
For detailed information, you can refer to the SAP Help guide for the SAP Secure Login Service for SAP GUI: https://help.sap.com/docs/SAP%20SECURE%20LOGIN%20SERVICE/c35917ca71e941c5a97a11d2c55dcacd/28d654c445...
In short:
- Licensing is tied to your Global Account and can be allocated to a pre-existing or new subaccount (Service Entitlement). This subaccount then hosts an instance of the SAP Secure Login Service for SAP GUI (Subscription). To establish this, the BTP subaccount must establish an OpenID Trust connection with one of your IAS tenants.
- Interestingly, it's worth noting that an IAS tenant from a different Global Account (with the same customer number) can also be leveraged, which is a beneficial feature.
- In conclusion, within IAS, you'll discover two applications: the Subaccount Trust XSUAA_<subaccount> (associated with your BTP subaccount trust) and the <secure-login-service>_<region> (your instance of the User Certificate Service). For the latter application, you can set up a Conditional Authentication Rule that allows optional redirection to your Corporate Identity Provider, which, in our case, was Azure AD.
- Accessing the web UI necessitates membership in two groups: SecureLoginServiceAdministrator and SecureLoginServiceViewer in IAS. Importantly, the SAP Secure Login Service for SAP GUI doesn't have its own set of BTP cockpit roles or role collections; instead, service access authorizations are administered through the trusted IAS tenant.
- From there, you can obtain the Client Policy Groups Host URL (found as enrollURL0), a crucial element for configuring the Secure Login Client Policy. This configuration ultimately enables the acquisition of certificates from the cloud certificate service operating within your BTP subaccount.
- By the way, the Client Setup process has remained unchanged. The Secure Login Client (SLC) can still be deployed manually or through automated means, and configuration can be automated using Registry Keys (Intune, GPO etc.).
And with that, the essentials have been covered.
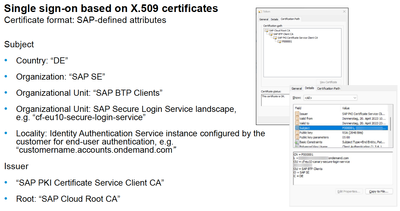
Customization Options for X.509 DN in Issued Certificates
Regarding X.509 DN, well, it's just how it is.
While the common names (CN) of user certificates are unique and dynamic, the static suffix is generated by the Secure Login Service and represents the identifier for the IAS tenant and SLS region. The CN part of the certificate's Distinguished Name is configured within the IAS application, following this procedure: https://help.sap.com/docs/SAP%20SECURE%20LOGIN%20SERVICE/c35917ca71e941c5a97a11d2c55dcacd/81fe0a1211...
In our scenario, we aimed to include the email address from IAS as the CN in the certificate. This email attribute is sourced from the IAS user store (IdDS), which is synchronized with users from our Azure AD tenant. However, you could also retrieve this attribute directly from your chosen Corporate Identity Provider (IdP), especially if you don't have profiles in IAS (no Identity Federation).
The certificate's structure will be formed using the following X.509 DN - Example:
CN=<E-Mail>, L=<ias-tenant>.accounts.ondemand.com, OU=<SLS-region-id>, OU=SAP BTP Clients, O=SAP SE, C=DE
This customization allows for tailoring the certificate to incorporate specific attributes from your chosen identity source, enhancing the certificate's relevance and usefulness within your system.

Source: SAP Secure Login Service for SAP GUI - Solution Overview
Certificate Chain of the SAP-Managed PKI
By the way, the certificate chain of the issued temporary SSO certificates can be traced back to the SAP Cloud Root CA, which has a validity of 20 years. This is the well-known certification authority that also issues SAP Passports (S-User Certificates), among other things.
Beneath this, there is the SAP BTP Client CA with a validity of 10 years, followed by the actual Issuing CA, SAP PKI Certificate Service Client CA, which has a validity of 2 months and is regularly renewed by SAP. Ultimately, in the SAP backend, the trust relationship to the root certificate must be established within the necessary PSE containers.
Here's the complete CA chain:
SAP Cloud Root CA
|- SAP BTP Client CA
|- SAP PKI Certificate Service Client CA
Aspects and Some Nice Features of SNC User Mapping
When implementing the new solution, adjustments to SNC names become necessary. There are various approaches to mass-set SNC names. While using the RSUSR300 report might pose some challenges, a Central User Administration (CUA) or Identity Management (IDM) systems are equally helpful.
Custom reports, as well as tools like our XAMS can also be used. With those you can easily create an Excel sheet with a generic formula, upload the sheet, and voilà, you're good to go.
By the way, it's worth noting that you can shorten parts of the long Distinguished Name (DN) using SAP CCL (CommonCryptoLib) ccl/* profile parameters. However, this requires configuration in the default profile on a per-system basis. Further information can be found here:
https://help.sap.com/docs/SAP_SINGLE_SIGN-ON/df185fd53bb645b1bd99284ee4e4a750/ca4af653ac444b54ba7fbb... and in SAP Note 2338952: https://me.sap.com/notes/2338952/E
Here's an example of how the configuration might look
ccl/snc/namealias/value_1 = L=<iastenant>.accounts.ondemand.com
ccl/snc/namealias/replacement_1 = L=My-IAS
ccl/snc/namealias/value_2 = OU=<region>-secure-login-service
ccl/snc/namealias/replacement_2 = OU=SLS
ccl/snc/namealias/value_3 = OU=SAP BTP Clients
ccl/snc/namealias/replacement_3 = OU=BTP
Original SNC Name:
p:CN=<E-Mail>, L=<iastenant>.accounts.ondemand.com, OU=<region>-secure-login-service, OU=SAP BTP Clients, O=SAP SE, C=DE
After applying the configurations, the modified SNC name would appear as follows:
p:CN=<E-Mail>, L=My-IAS, OU=SLS, OU=BTP, O=SAP SE, C=DE
Additionally, in the transaction CERTRULE, you can create a new rule quite easily. We simply mapped the CN part to the SU01 field "E-Mail" and filtered out all other DN elements like L, OU, O, and C.
What's Still Missing and What Could Come Next
Please bear in mind that I am not part of SAP's Product Management team 😇, and the following points are based on my personal opinion.
Certain aspects from the SAP SSO 3.0 suite are not currently covered by the new solution, and there hasn't been much change in this regard. Nevertheless, we would like to address some current limitations of the service and provide insights into its potential future developments.
Here are some points we'd like to share with you:
Customization of X.509 DN is currently not possible: Currently, adjusting the X.509 DN is not feasible, and it follows a fixed structure. It would be fantastic if the lengthy part after the CN could be customized. Unfortunately, the X.509 DN is even so lengthy that the RSUSR300 report (SNC1) struggles to handle it due to a field length restriction.
UPDATE: As of November 6, 2023, SAP Note 3396732 (SNC1/RSUSR300) has been released, providing support for extended prefix and suffix values. This update addresses the previous limitation, now allowing a field length of up to 200 characters.
According to SAP, the X.509 DN will become configurable once the custom cloud CA (Certificate Authority) support goes live. Integrating a customer-specific cloud CA is on the roadmap. However, it's unlikely that a similar option to the old SLS, using Remote CAs through NDES & Cloud Connector, will be available.
Profiles/Profile Groups Not Currently Supported: Presently, using profiles or profile groups to enforce true Multi-Factor Authentication (MFA) requirements for specific SAP systems isn't feasible. In the previous SLS version, certificates could be removed after a timeout, or there was the option to automatically log off from the profile when the last SNC session was closed. With the new solution, this isn't currently achievable for individual GssTargetNames.
Different profiles can only be represented through separate subscriptions, which is a bit of a drawback. Additionally, some settings familiar from SLS 3.0 are not yet available in the new cloud solution. SAP might observe customer demand before implementing these.
Certificate Lifecycle Management (CLM) Similar to the old SAP SLS 3.0: The management of certificate lifecycles (CLM), akin to the old SLS, is not currently planned. SAP hasn't provided a timeline, but this will be explored more closely once the custom cloud CA support is in place. Currently, customers would need to license both solutions – the minimum bundle for SAP SSO 3.0, and the new solution.
As the solution evolves and more feedback is gathered from users, SAP might address these limitations and introduce new features. The complexities surrounding certificate management and authentication are areas of ongoing development. Let's see how the solution will evolve over time.
We conclude this blog with a collection of FAQs.
Compilation of frequently asked questions
Q: What happens if the cloud service is unavailable due to IaaS provider network issues (SAP/AWS/Microsoft Azure/Google CP)?
A: The certificate service operates on SAP BTP, following platform availability commitments. While cloud service is needed for certificate provisioning, typical validity spans a workday. Users access the service once daily, enabling independent ABAP system use. In case of service unavailability, alternative on-premises solutions like certificates, smart cards, or Kerberos are recommended.
Q: Can users of SAP SSO 3.0 and SAP Secure Login Server transition to the cloud? Are there commercial advantages or parallel product usage?
A: SAP SSO 3.0 and SLS differ in licensing and features. SLS benefits include better cloud identity provider integration and reduced total cost of ownership by eliminating AS Java operation. Technical intricacies of SLS 3.0 might not fully transfer. Commercial transition details can be discussed with your SAP Account Executive.
Q: Can CPEA Global Accounts subscribe to SAP Secure Login Service for SAP GUI?
A: Currently, CPEA is not supported. Minimal subscriptions are available through SAP contacts to facilitate starting. No trial version is offered by SAP SE at present.
Q: Is SAP Secure Login Service the official successor to SAP Single Sign-On 3.0 after 2027 end of maintenance?
A: Yes, SAP Secure Login Service for SAP GUI will replace SAP Single Sign-On 3.0.
Q: What benefits does SAP Secure Login Service offer over SAP Single Sign-On 3.0 for complex on-premise SAP landscapes using Kerberos?
A: Both products offer Kerberos-based single sign-on with no difference. Transition isn't necessary unless supporting multiple ADs/Forests or consolidating authentication via central Azure AD tenant. Migration enhances flexibility and future-proofing.
Q: Does SAP Secure Login Service for SAP GUI support SAP Fiori or SAP GUI HTML?
A: Http-based apps can use SAML 2.0 or X.509 certificates, possibly without this solution. SPNEGO is feasible if SAP Secure Login Service for SAP GUI functions solely as a Kerberos solution.
Q: Is SAP Cloud Identity Authentication Service (IAS) essential for SAP Secure Login Service for SAP GUI?
A: Identity Authentication Service is integral, but can proxy Azure AD. This way, users interact only with Azure AD interfaces.
[Last Update 2024.03.01]
Hello fellow SAP security enthusiasts!
I wanted to share some exciting news with you. I've been busy creating a couple of LinkedIn blogs that delve into the fascinating world of the SAP Secure Login Service for SAP GUI. As I was exploring this topic, I thought, why not bring all this valuable knowledge together into one comprehensive blog post?
I hope you enjoy reading it as much as I enjoyed writing it!
TOC
Introduction
Multiple Factors Propel SAP's Move Towards New Solution for Enhanced Authentication
Brief Overview of the SAP Secure Login Service for SAP GUI
Background
Embracing Change: Switching from Active Directory to Native Azure AD Environments
Ramifications on SAP Authentication Landscape
The Migration to Azure AD
The Exodus of Kerberos
Introducing Azure Active Directory Domain Services
The Implications for SAP GUI
HTTP-Driven SAP Applications and SAML 2.0
Exploring the SAP Secure Login Service for SAP GUI: An In-Depth Review
Basic Setup of the Service (SAP BTP & IAS)
Customization Options for X.509 DN in Issued Certificates
Certificate Chain of the SAP-Managed PKI
Aspects and Some Nice Features of SNC User Mapping
What's Still Missing and What Could Come Nex
Compilation of frequently asked questions
Introduction
The highly anticipated SAP Secure Login Service for SAP GUI has emerged as a testament to innovation, merging the stalwart functionality of the esteemed SAP Single Sign-On with the expansive capabilities of cloud computing.
On May 4, 2023, SAP introduced the SAP Secure Login Service for SAP GUI, a cloud-centric solution that advances the concept of single sign-on. For comprehensive details, I direct your attention to the Release Blog post available here
By opting to retire the traditional AS Java platform, not only are cost efficiencies achieved but resource optimization is also realized. With a rhythmic alignment with Kerberos and X.509, coupled with seamless integration into cloud-driven identity frameworks, the opportune moment has arrived to engage with the SAP SSO cohort. The SAP Secure Login Service (SLS) builds upon the bedrock of SAP Single Sign-On, elevating the single sign-on experience to the cloud milieu. Embrace a lean cloud service seamlessly harmonizing with your corporate identity provider, as you embark on this transformative journey.
Source: SAP Secure Login Service for SAP GUI - Solution Overview
Multiple Factors Propel SAP's Move Towards New Solution for Enhanced Authentication
Let's begin by examining the key drivers behind SAP's introduction of this new solution. Currently, SAP SSO 3.0 remains in maintenance mode, with no new feature integrations from SAP. Notably, there are no plans for the release of Version 4.0.
Over time, certain scenarios have become obsolete, magnifying the demand to transition specific components (such as the Secure Login Server) to the cloud, a demand that has grown increasingly pronounced in recent years.
With the expansion of IT infrastructures reliant on cloud-native technologies and Azure AD, and in the absence of Active Directory (AD), there exists a pressing requirement for Multi-Factor Authentication (MFA) within the SAP GUI environment. The retirement of SAP AS Java has emerged as a pivotal factor thus far, underscoring the multifaceted motivations driving this shift. Indeed, it appears that a multitude of reasons converge to shape this transition.
Brief Overview of the SAP Secure Login Service for SAP GUI
The SAP Secure Login Service for SAP GUI is a multi-tenant SAP Business Technology Platform (BTP) cloud application designed to facilitate multifactor authentication (MFA) and single sign-on (SSO) when utilizing the SAP GUI interface.
Building upon the achievements of SAP Single Sign-On, the Secure Login Service (SLS) preserves its core functionalities while enhancing them to align with the demands of the cloud era. It seamlessly integrates with cloud-based identity providers, reinforcing authentication and single sign-on for business applications. By establishing connections with central authentication solutions like identity providers, this service streamlines access, enhances user efficiency, and reinforces data security through robust authentication methods.
It's all about keeping things simple and secure for your SAP GUI users. This new solution comes packed with a whole set of enhanced capabilities. One of the coolest things about this cloud-powered gem is the way it handles X.509 certificates. No more fussing around with on-premise servers or SAP NetWeaver Application Server Java. The cloud service takes care of all the certificate enrollment, leaving you with more time to binge-watch your favorite shows. So long, AS Java!
But wait, there's more! You can now flex your existing identity provider solution, like SAP Cloud Identity Services or other popular ones such as Microsoft Azure Active Directory and Okta. These authentication superheroes bring their mighty multi-factor authentication powers to the table, ensuring only the worthy can access your SAP GUI kingdom.
Highlights:
- Secure Login Client can authenticate SAP users based on the SAML standard (SAML & X.509).
- Supports SSO and MFA for SAP GUI without the need for a SAP NetWeaver AS Java instance (SLS).
- Enables previously missing functionalities such as SAP GUI SSO integration with SAML IdPs and MFA for SAP GUI without AS Java (SAP Secure Login Server).
- Provides an alternative to the Kerberos scenario (e.g. in pure Azure AD environments without KDC).
How it works in a nutshell:
- The Secure Login Client communicates with the new cloud service which can authenticate the user through IAS and/or an existing Corporate IdP (Azure|ADFS|Okta...).
- The "SLS in the Cloud" (user certificate service) issues a temporary SSO certificate.
- Technically, (after the SAML flow) this still involves an SNC connection with X.509 CBA (certificate-based authentication) to the AS ABAP or S/4HANA system.
Source: SAP Secure Login Service for SAP GUI - Solution Overview
Key Features:
- Configuration is based on your SAP Cloud Identity Services tenant or corporate Identity Provider (IdP). Various authentication factors such as passwords, Time-Based One-Time Password (TOTP) tokens, local X.509 certificates, and authentication devices like Windows Hello, macOS Touch ID, or FIDO can be configured.
- The Software-as-a-Service (SaaS) application offers a web-based user interface (UI) for administrative purposes. While the current Secure Login Service Web UI has limited settings, it's anticipated that additional features will be added in the future.
- Authentication takes place within an embedded web browser (part of the Secure Login Client in Windows) or the standard web browser (macOS version), contributing to an excellent user experience.
- Successful user authentication yields a short-lived user certificate, usable for Secure Network Communication (SNC), Secure Store and Forward (SSF), or Transport Layer Security (TLS).
- Users can authenticate to an AS ABAP (Advanced Business Application Programming) using X.509 certificates and Kerberos via SNC communication.
- Notably, the migration to the new service can be carried out seamlessly in parallel without disrupting the existing setup.
Source: SAP Secure Login Service for SAP GUI - Solution Overview
For more information, you can refer to the solution overview provided in this link: https://www.sap.com/documents/2023/05/50bf62e4-707e-0010-bca6-c68f7e60039b.html
To delve deeper into the topic of SAP Secure Login Service for SAP GUI, we recommend exploring the following resources for comprehensive information:
- Product overview presentation from SAP
- Documentation on SAP Help
Background
Before delving into the depths, let us initially provide a concise overview of why the current topic of Active Directory / Azure Active Directory holds relevance.
Embracing Change: Switching from Active Directory to Native Azure AD Environments
In the dynamic landscape of technological evolution, change stands as a pivotal determinant. Currently, a significant paradigm shift is underway, marked by the transition from conventional Active Directory (AD) environments to the native constructs of Azure Active Directory (AAD).
Especially prevalent in the initiatives of nascent enterprises commencing from their inception, a pronounced inclination towards a cloud-exclusive approach is often observed. In such scenarios, the conventional notion of a Domain, as commonly understood, may indeed lose its pertinence or operative status.
By harnessing the capabilities of cloud-based services and platforms, many organizations effectively obviate the need for traditional, on-premises domains, allowing them to fully leverage the advantages inherent to a cloud-native milieu. Facilitated by robust identity and access management solutions offered by cloud service providers, these enterprises can orchestrate secure and streamlined operations, thereby concentrating their efforts on fundamental business imperatives.
As these forward-looking entities wholeheartedly embrace the cloud as their principal infrastructure, they reap the rewards of its inherent flexibility, scalability, and cost-efficiency. Concurrently, the prevalence of cloud-native solutions and platforms renders the requirement for on-premises domains progressively obsolete, enabling enterprises to harness the potency of cloud services to fulfill both their IT and business prerequisites.
By committing to a cloud-exclusive methodology, these enterprises fully harness the capabilities proffered by cloud giants such as Microsoft Azure, AWS, or Google Cloud. They architect their infrastructure, applications, and services directly atop these platforms, capitalizing on the innate security, scalability, and availability features inherent in the cloud paradigm.
This transition toward an exclusive cloud-centric approach affords enterprises the luxury of concentrating on core business pursuits, unfettered by the complexities of managing and upkeeping conventional on-premises domains. Instead, they avail themselves of the cloud provider's infrastructure, empowering swift deployment and scalability of applications and services congruent with their burgeoning operations.
Furthermore, by embracing cloud-native offerings such as Azure Active Directory, enterprises can still uphold stringent access management and identity federation protocols without necessitating an on-premises domain. Azure AD extends an all-encompassing spectrum of identity and access management capabilities, encompassing Single Sign-On (SSO), Multi-Factor Authentication (MFA), and Conditional Access policies, seamlessly amalgamating with cloud-centric environments.
Ramifications on SAP Authentication Landscape
Thus, esteemed readers, let us pivot our attention to the trajectory of transition toward Azure's cloud-native approach and the ensuing implications on your SAP SSO landscape, particularly if you have traditionally relied on Kerberos authentication and have not yet traversed the realm of X.509 certificates for SAP GUI authentication.
The Migration to Azure AD
A growing cohort of global enterprises is unequivocally embracing the Azure and Intune ecosystem, bidding adieu to the conventional AD-domain construct. With Azure AD, clients emancipate themselves from the shackles of internal Active Directory systems, signifying the discontinuation of domain controllers and the prevailing of Kerberos Key Distribution Centers (KDCs). A farewell to erstwhile companions, indeed!
The Exodus of Kerberos
In the SAP domain, our endeavors have perennially revolved around realizing a seamless SSO experience via Kerberos authentication. However, in the nascent domain of Azure AD, this approach no longer retains its efficacy. The absence of domain controllers renders our cherished SAP GUI SSO solution, founded on SNC with Kerberos tokens, no longer as efficacious.
Introducing Azure Active Directory Domain Services
At this point, you might ask, "Can we use Kerberos in these new infrastructures?" The answer is found in Azure Active Directory Domain Services, which is like having two Domain Controllers offered as a service – quite a complex setup. When there's a noticeable lack of an LDAP infrastructure, some businesses might consider using these services to meet this need. I haven't had much experience with SAP SSO combined with these services so far. However, I'm keen to learn from anyone who has explored this option.
The Implications for SAP GUI
This technological shift undoubtedly impinges on SAP GUI. Ensuring encryption and SSO mandates continued safeguarding of all SAP proprietary DIAG and RFC communications through Secure Network Communications (SNC). Consequently, the necessity for the SAP SSO 3.0 solution (Secure Login Client) on client-side installations remains relatively unchanged within this novel framework.
HTTP-Driven SAP Applications and SAML 2.0
In recent times, SAML 2.0 has become the central standard in the SAP environment, especially for applications that operate over HTTP. Within the SAP ecosystem, which includes AS ABAP, AS Java, S/4HANA, and HANA DB, these systems act as service providers. They work together seamlessly with either the Azure Identity Provider (IDP) or the Identity Authentication Service (IAS), both of which are aligned with Azure AD. This forms a harmonious collaboration, like a symphony of interconnected champions.
When integrated with Azure AD, a world of opportunities emerges, with SAML 2.0 playing a pivotal role in single sign-on technology. This leads to the implementation of Conditional Access, Multi-Factor Authentication, and Intune policies for device recognition – a collection of security measures that can be likened to having your own team of security superheroes.
In the realm of SAP, whether within the On-Premises milieu or the SAP Cloud continuum (encompassing SaaS/BTP), the ascendancy of SAP Cloud Identity Services and SAP IAS remains unchallenged, serving as the paragons of Identity Providers. The integration with Azure AD not only remains a viable proposition but also avails itself of a multitude of advantages. For an in-depth elucidation, I direct your attention to this blog post.
SAP Cloud Identity Services
- Ideal for browser-based SAP access
- Enables SSO across cloud and on-premises apps
- Simplifies IAM for unified landscapes
- Supports SAML and OpenID Connect
SAP Single Sign-On 3.0
- Crucial for SAP GUI and on-premise systems
- Utilizes X.509 certificates or Kerberos (SNC)
- Ensures end-user SSO in various scenarios
SAP Secure Login Service for SAP GUI
- Official successor to SAP Single Sign-On 3.0 (post-2027)
- Enhances SAP GUI security
- Enables SAML-based authentication with Secure Login Client
- Integrates with existing SAML Identity Providers via SAP IAS
- Offers MFA support for SAP GUI, even without SAP NetWeaver AS Java (SLS)
- Replacement for Kerberos in pure Azure AD (Entra ID) environments
Big Picture: Authentication and SSO in a hybrid SAP system landscape
This graphic combines these three solutions to address your IAM and SSO needs, delivering a secure and user-friendly experience in your SAP landscape
Exploring the SAP Secure Login Service for SAP GUI: An In-Depth Review
In this chapter, you can expect the following:
- Information about the basic setup of the service (SAP BTP & IAS)
- Customization options for the X.509 DN of issued certificates
- Insights and some niceties about SNC User Mapping
- What's still missing and what could potentially be added in the future
Basic Setup of the Service (SAP BTP & IAS)
I was genuinely impressed by how straightforward the setup process is! While a few steps need to be followed, they are quite easy to manage. At a high level, without delving too deeply into the specifics, here are the 10 steps to success:
- License Assignment (Global Account Level): Assign the license to your Global Account (SAP SE).
- Define target BTP Subaccount: Establish a new BTP subaccount dedicated to the Secure Login Service (SLS).
- Trust Establishment: Establish trust between the SLS subaccount and your Identity Authentication Service (IAS) tenant.
- Configure Entitlement: Set up the entitlement and link the service to the SLS subaccount.
- Subscription: Subscribe to the Secure Login Service and generate a service instance.
- Group Setup in IAS: Create groups in IAS to control access to the Secure Login Service web UI.
- SSO Certificate Lifetime Configuration: Configure the lifespan of Single Sign-On (SSO) certificates in the SLS web UI.
- Common Name Attribute Setup: Establish the Common Name attribute for user certificates in IAS.
- Secure Login Client Deployment, Configuration and Policy Loading: Configure the Secure Login Client and provide the policy.
- Customization of SNC Names and CERTRULE: Customize the Secure Network Communication (SNC) names and certificate rules.
For detailed information, you can refer to the SAP Help guide for the SAP Secure Login Service for SAP GUI: https://help.sap.com/docs/SAP%20SECURE%20LOGIN%20SERVICE/c35917ca71e941c5a97a11d2c55dcacd/28d654c445...
In short:
- Licensing is tied to your Global Account and can be allocated to a pre-existing or new subaccount (Service Entitlement). This subaccount then hosts an instance of the SAP Secure Login Service for SAP GUI (Subscription). To establish this, the BTP subaccount must establish an OpenID Trust connection with one of your IAS tenants.
- Interestingly, it's worth noting that an IAS tenant from a different Global Account (with the same customer number) can also be leveraged, which is a beneficial feature.
- In conclusion, within IAS, you'll discover two applications: the Subaccount Trust XSUAA_<subaccount> (associated with your BTP subaccount trust) and the <secure-login-service>_<region> (your instance of the User Certificate Service). For the latter application, you can set up a Conditional Authentication Rule that allows optional redirection to your Corporate Identity Provider, which, in our case, was Azure AD.
- Accessing the web UI necessitates membership in two groups: SecureLoginServiceAdministrator and SecureLoginServiceViewer in IAS. Importantly, the SAP Secure Login Service for SAP GUI doesn't have its own set of BTP cockpit roles or role collections; instead, service access authorizations are administered through the trusted IAS tenant.
- From there, you can obtain the Client Policy Groups Host URL (found as enrollURL0), a crucial element for configuring the Secure Login Client Policy. This configuration ultimately enables the acquisition of certificates from the cloud certificate service operating within your BTP subaccount.
- By the way, the Client Setup process has remained unchanged. The Secure Login Client (SLC) can still be deployed manually or through automated means, and configuration can be automated using Registry Keys (Intune, GPO etc.).
And with that, the essentials have been covered.
Customization Options for X.509 DN in Issued Certificates
Regarding X.509 DN, well, it's just how it is.
While the common names (CN) of user certificates are unique and dynamic, the static suffix is generated by the Secure Login Service and represents the identifier for the IAS tenant and SLS region. The CN part of the certificate's Distinguished Name is configured within the IAS application, following this procedure: https://help.sap.com/docs/SAP%20SECURE%20LOGIN%20SERVICE/c35917ca71e941c5a97a11d2c55dcacd/81fe0a1211...
In our scenario, we aimed to include the email address from IAS as the CN in the certificate. This email attribute is sourced from the IAS user store (IdDS), which is synchronized with users from our Azure AD tenant. However, you could also retrieve this attribute directly from your chosen Corporate Identity Provider (IdP), especially if you don't have profiles in IAS (no Identity Federation).
The certificate's structure will be formed using the following X.509 DN - Example:
CN=<E-Mail>, L=<ias-tenant>.accounts.ondemand.com, OU=<SLS-region-id>, OU=SAP BTP Clients, O=SAP SE, C=DE
This customization allows for tailoring the certificate to incorporate specific attributes from your chosen identity source, enhancing the certificate's relevance and usefulness within your system.
Source: SAP Secure Login Service for SAP GUI - Solution Overview
Certificate Chain of the SAP-Managed PKI
By the way, the certificate chain of the issued temporary SSO certificates can be traced back to the SAP Cloud Root CA, which has a validity of 20 years. This is the well-known certification authority that also issues SAP Passports (S-User Certificates), among other things.
Beneath this, there is the SAP BTP Client CA with a validity of 10 years, followed by the actual Issuing CA, SAP PKI Certificate Service Client CA, which has a validity of 2 months and is regularly renewed by SAP. Ultimately, in the SAP backend, the trust relationship to the root certificate must be established within the necessary PSE containers.
Here's the complete CA chain:
SAP Cloud Root CA
|- SAP BTP Client CA
|- SAP PKI Certificate Service Client CA
Aspects and Some Nice Features of SNC User Mapping
When implementing the new solution, adjustments to SNC names become necessary. There are various approaches to mass-set SNC names. While using the RSUSR300 report might pose some challenges, a Central User Administration (CUA) or Identity Management (IDM) systems are equally helpful.
Custom reports, as well as tools like our XAMS can also be used. With those you can easily create an Excel sheet with a generic formula, upload the sheet, and voilà, you're good to go.
By the way, it's worth noting that you can shorten parts of the long Distinguished Name (DN) using SAP CCL (CommonCryptoLib) ccl/* profile parameters. However, this requires configuration in the default profile on a per-system basis. Further information can be found here:
https://help.sap.com/docs/SAP_SINGLE_SIGN-ON/df185fd53bb645b1bd99284ee4e4a750/ca4af653ac444b54ba7fbb... and in SAP Note 2338952: https://me.sap.com/notes/2338952/E
Here's an example of how the configuration might look
ccl/snc/namealias/value_1 = L=<iastenant>.accounts.ondemand.com
ccl/snc/namealias/replacement_1 = L=My-IAS
ccl/snc/namealias/value_2 = OU=<region>-secure-login-service
ccl/snc/namealias/replacement_2 = OU=SLS
ccl/snc/namealias/value_3 = OU=SAP BTP Clients
ccl/snc/namealias/replacement_3 = OU=BTP
Original SNC Name:
p:CN=<E-Mail>, L=<iastenant>.accounts.ondemand.com, OU=<region>-secure-login-service, OU=SAP BTP Clients, O=SAP SE, C=DE
After applying the configurations, the modified SNC name would appear as follows:
p:CN=<E-Mail>, L=My-IAS, OU=SLS, OU=BTP, O=SAP SE, C=DE
Additionally, in the transaction CERTRULE, you can create a new rule quite easily. We simply mapped the CN part to the SU01 field "E-Mail" and filtered out all other DN elements like L, OU, O, and C.
What's Still Missing and What Could Come Next
Please bear in mind that I am not part of SAP's Product Management team 😇, and the following points are based on my personal opinion.
Certain aspects from the SAP SSO 3.0 suite are not currently covered by the new solution, and there hasn't been much change in this regard. Nevertheless, we would like to address some current limitations of the service and provide insights into its potential future developments.
Here are some points we'd like to share with you:
Customization of X.509 DN is currently not possible: Currently, adjusting the X.509 DN is not feasible, and it follows a fixed structure. It would be fantastic if the lengthy part after the CN could be customized. Unfortunately, the X.509 DN is even so lengthy that the RSUSR300 report (SNC1) struggles to handle it due to a field length restriction.
UPDATE: As of November 6, 2023, SAP Note 3396732 (SNC1/RSUSR300) has been released, providing support for extended prefix and suffix values. This update addresses the previous limitation, now allowing a field length of up to 200 characters.
According to SAP, the X.509 DN will become configurable once the custom cloud CA (Certificate Authority) support goes live. Integrating a customer-specific cloud CA is on the roadmap. However, it's unlikely that a similar option to the old SLS, using Remote CAs through NDES & Cloud Connector, will be available.
Profiles/Profile Groups Not Currently Supported: Presently, using profiles or profile groups to enforce true Multi-Factor Authentication (MFA) requirements for specific SAP systems isn't feasible. In the previous SLS version, certificates could be removed after a timeout, or there was the option to automatically log off from the profile when the last SNC session was closed. With the new solution, this isn't currently achievable for individual GssTargetNames.
Different profiles can only be represented through separate subscriptions, which is a bit of a drawback. Additionally, some settings familiar from SLS 3.0 are not yet available in the new cloud solution. SAP might observe customer demand before implementing these.
Certificate Lifecycle Management (CLM) Similar to the old SAP SLS 3.0: The management of certificate lifecycles (CLM), akin to the old SLS, is not currently planned. SAP hasn't provided a timeline, but this will be explored more closely once the custom cloud CA support is in place. Currently, customers would need to license both solutions – the minimum bundle for SAP SSO 3.0, and the new solution.
As the solution evolves and more feedback is gathered from users, SAP might address these limitations and introduce new features. The complexities surrounding certificate management and authentication are areas of ongoing development. Let's see how the solution will evolve over time.
We conclude this blog with a collection of FAQs.
Compilation of frequently asked questions
Q: What happens if the cloud service is unavailable due to IaaS provider network issues (SAP/AWS/Microsoft Azure/Google CP)?
A: The certificate service operates on SAP BTP, following platform availability commitments. While cloud service is needed for certificate provisioning, typical validity spans a workday. Users access the service once daily, enabling independent ABAP system use. In case of service unavailability, alternative on-premises solutions like certificates, smart cards, or Kerberos are recommended.
Q: Can users of SAP SSO 3.0 and SAP Secure Login Server transition to the cloud? Are there commercial advantages or parallel product usage?
A: SAP SSO 3.0 and SLS differ in licensing and features. SLS benefits include better cloud identity provider integration and reduced total cost of ownership by eliminating AS Java operation. Technical intricacies of SLS 3.0 might not fully transfer. Commercial transition details can be discussed with your SAP Account Executive.
Q: Can CPEA Global Accounts subscribe to SAP Secure Login Service for SAP GUI?
A: Currently, CPEA is not supported. Minimal subscriptions are available through SAP contacts to facilitate starting. No trial version is offered by SAP SE at present.
Q: Is SAP Secure Login Service the official successor to SAP Single Sign-On 3.0 after 2027 end of maintenance?
A: Yes, SAP Secure Login Service for SAP GUI will replace SAP Single Sign-On 3.0.
Q: What benefits does SAP Secure Login Service offer over SAP Single Sign-On 3.0 for complex on-premise SAP landscapes using Kerberos?
A: Both products offer Kerberos-based single sign-on with no difference. Transition isn't necessary unless supporting multiple ADs/Forests or consolidating authentication via central Azure AD tenant. Migration enhances flexibility and future-proofing.
Q: Does SAP Secure Login Service for SAP GUI support SAP Fiori or SAP GUI HTML?
A: Http-based apps can use SAML 2.0 or X.509 certificates, possibly without this solution. SPNEGO is feasible if SAP Secure Login Service for SAP GUI functions solely as a Kerberos solution.
Q: Is SAP Cloud Identity Authentication Service (IAS) essential for SAP Secure Login Service for SAP GUI?
A: Identity Authentication Service is integral, but can proxy Azure AD. This way, users interact only with Azure AD interfaces.
Q:Is there a direct correlation between the number of "SAP Secure Login Service for SAP GUI" instances and "SAP Cloud Authentication Service" instances? Specifically, if a customer has three IAS instances due to a one-to-one relationship with SuccessFactors instances (Production, Non-Production 1, and Non-Production 2), each linked to corresponding SuccessFactors and S4HANA environments, is it necessary to have three separate SAP Secure Login Service instances for SSO in S4HANA environments (Prod, Test, Development)? Also, does the pricing for SAP Secure Login Service only apply to production usage?
A: SAP Secure Login Service doesn't have its own user store and always relies on the identity provider, such as IAS, for authentication. To enable SSO for a specific S/4HANA system, an SAP Secure Login Service instance must be integrated with an IAS tenant containing the relevant user accounts. If the productive IAS tenant lacks certain user accounts, additional SAP Secure Login Service instances are required for other IAS tenants. Pricing is determined by the number of users or employees, not by the number of SAP Secure Login Service instances.
Q: Can Azure Idp be used without a BTP tenant for authentication?
A: Secure Login Client relies on BTP's SAP Secure Login Service for certificate provisioning and Identity Authentication Service for authentication. Azure AD integration is enabled through proxy configuration in Identity Authentication Service and Azure AD.
Q: Does "SAP Secure Login Service for SAP GUI" include Certificate Lifecycle Management (CLM)?
A: Current version lacks CLM. SAP considers cloud-based alternatives to on-premise Java stack for future CLM inclusion, with details and timelines pending.
Q: How can we perform tasks such as creating root certificates, intermediates, signing certificates with CSR, and installing them into ABAP/JAVA systems using the new SAP Secure Login Service for SAP GUI?
A: Currently, the new service primarily deals with client certificates for SSO using an SAP-managed CA. Support for customer-managed CAs in the cloud is on the roadmap, but not yet available. Certificate Lifecycle Management is under consideration, but the scope and roadmap haven't been finalized. Thus, the functionality of the on-premise server for creating root certificates, intermediates, signing certificates with CSR etc. is not available in the cloud service at this time.
Q: Does the Secure Login Service for SAP GUI running on SAP Business Technology Platform - will only function within the client's network, as it may not be able to communicate with the corporate on-premises IDP (Identity Provider) from outside the network due to potential connectivity restrictions?
A: In this case, SAP utilize the IAS identity provider proxy mechanism, detailed at https://help.sap.com/docs/identity-authentication/identity-authentication/corporate-identity-provide.... This setup eliminates the need for a network connection between the two identity providers, as all communication occurs through the end user's browser. The only requirement is that both the identity authentication service and your corporate IdP must be accessible from the end user's desktop.
Got more juicy tidbits to add or feeling the itch to sprinkle your magical feedback dust? Don't be a stranger – drop a line, a joke, or even your favorite recipe! Feel free to leave a comment 📣
- SAP Managed Tags:
- SAP Single Sign-On,
- SAP Secure Login Service for SAP GUI
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
"automatische backups"
1 -
"regelmäßige sicherung"
1 -
"TypeScript" "Development" "FeedBack"
1 -
505 Technology Updates 53
1 -
ABAP
22 -
ABAP API
1 -
ABAP CDS Views
4 -
ABAP CDS Views - BW Extraction
2 -
ABAP CDS Views - CDC (Change Data Capture)
1 -
ABAP class
2 -
ABAP Cloud
3 -
ABAP DDIC CDS view
1 -
ABAP Development
5 -
ABAP in Eclipse
3 -
ABAP Platform Trial
1 -
ABAP Programming
3 -
abap technical
1 -
abapGit
1 -
absl
2 -
access data from SAP Datasphere directly from Snowflake
1 -
Access data from SAP datasphere to Qliksense
1 -
Accrual
1 -
action
1 -
adapter modules
1 -
Addon
1 -
Adobe Document Services
1 -
ADS
1 -
ADS Config
1 -
ADS with ABAP
1 -
ADS with Java
1 -
ADT
3 -
Advance Shipping and Receiving
1 -
Advanced Event Mesh
3 -
Advanced formula
1 -
AEM
1 -
AI
9 -
AI Launchpad
2 -
AI Projects
1 -
AIML
11 -
Alert in Sap analytical cloud
1 -
Amazon S3
1 -
Analytic Models
1 -
Analytical Dataset
1 -
Analytical Model
1 -
Analytics
1 -
Analyze Workload Data
1 -
annotations
1 -
API
1 -
API and Integration
5 -
API Call
2 -
API security
1 -
Application Architecture
1 -
Application Development
5 -
Application Development for SAP HANA Cloud
3 -
Applications and Business Processes (AP)
1 -
Architecture
1 -
Artificial Intelligence
1 -
Artificial Intelligence (AI)
8 -
Artificial Intelligence (AI) 1 Business Trends 363 Business Trends 8 Digital Transformation with Cloud ERP (DT) 1 Event Information 462 Event Information 15 Expert Insights 114 Expert Insights 76 Life at SAP 418 Life at SAP 1 Product Updates 4
1 -
Artificial Intelligence (AI) blockchain Data & Analytics
2 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise Oil Gas IoT Exploration Production
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise sustainability responsibility esg social compliance cybersecurity risk
1 -
Artificial Intelligence role in shaping the future of Energy Industry
1 -
AS Java
1 -
ASE
1 -
ASR
2 -
Asset Management
2 -
Associations in CDS Views
1 -
ASUG
1 -
Attachment Handling. Create Attachment
1 -
Attachments
1 -
Authentication
1 -
Authorisations
1 -
Authorizations
1 -
Automate the Interim Account Update rule using Integration Center Job (Time Off)
1 -
Automated Test
1 -
Automating Processes
1 -
Automation
2 -
aws
2 -
Azure
2 -
Azure AI Studio
2 -
Azure API Center
1 -
Azure API Management
1 -
B2B Integration
1 -
Background job
1 -
Backorder Processing
1 -
Backpropagation
1 -
Backup
1 -
Backup and Recovery
1 -
Backup schedule
1 -
BADI_MATERIAL_CHECK error message
1 -
Bank
1 -
Bank Communication Management
1 -
BAS
1 -
basis
2 -
Basis Monitoring & Tcodes with Key notes
2 -
Batch Management
1 -
BDC
1 -
Best Practice
1 -
BI
1 -
bitcoin
1 -
Blockchain
3 -
bodl
1 -
BOP in aATP
1 -
BOP Segments
1 -
BOP Strategies
1 -
BOP Variant
1 -
BPC
1 -
BPC LIVE
1 -
BTP
19 -
BTP AI Launchpad
1 -
BTP Destination
2 -
BTP for Sustainability
1 -
Business AI
1 -
Business and IT Integration
1 -
Business application stu
1 -
Business Application Studio
3 -
Business Architecture
1 -
Business Communication Services
1 -
Business Continuity
2 -
Business Data Fabric
3 -
Business Fabric
1 -
Business Partner
14 -
Business Partner Master Data
13 -
Business Technology Platform
2 -
Business Trends
4 -
Business_catalog
1 -
BW ODP
1 -
BW4 HANA Dev
1 -
BW4HANA
1 -
C4C cloud root certificate
1 -
CA
1 -
calculation view
1 -
CAP
6 -
CAP development
1 -
Capgemini
1 -
CAPM
1 -
Catalyst for Efficiency: Revolutionizing SAP Integration Suite with Artificial Intelligence (AI) and
1 -
CCMS
2 -
CDQ
13 -
CDS
2 -
CDS Views
1 -
Cental Finance
1 -
Certificates
1 -
CFL
1 -
Change Management
1 -
chatbot
1 -
ChatGPT
4 -
CICD
1 -
CL_SALV_TABLE
2 -
Class Runner
1 -
Classrunner
1 -
Cloud ALM Monitoring
1 -
Cloud ALM Operations
1 -
cloud connector
2 -
Cloud Extensibility
1 -
Cloud Foundry
4 -
Cloud Integration
6 -
Cloud Platform Integration
2 -
cloudalm
1 -
Collaboration
1 -
Collaborative Draft
1 -
communication
1 -
Compensation Information Management
1 -
Compensation Management
1 -
compliance
1 -
Compound Employee API
1 -
Configuration
1 -
Connectors
1 -
Consolidation
1 -
Consolidation Extension for SAP Analytics Cloud
4 -
Control Indicators.
1 -
Controller-Service-Repository pattern
1 -
Conversion
1 -
Corrective Maintenance
1 -
Cosine similarity
1 -
CPI
3 -
cryptocurrency
1 -
CSI
1 -
ctms
1 -
Custom chatbot
3 -
Custom Destination Service
1 -
custom fields
1 -
Custom Headers
1 -
Custom Widget
2 -
Customer Experience
1 -
Customer Journey
1 -
Customizing
1 -
cyber security
6 -
cybersecurity
1 -
DAC
1 -
Data
1 -
Data & Analytics
1 -
Data Aging
1 -
Data Analysis
1 -
Data Analytics
2 -
Data and Analytics (DA)
2 -
Data Archiving
1 -
Data Back-up
1 -
Data Flow
1 -
Data Governance
6 -
Data Integration
2 -
Data Quality
13 -
Data Quality Management
13 -
Data Replication
1 -
Data Synchronization
1 -
data transfer
1 -
Data Unleashed
1 -
Data Value
9 -
Database
1 -
Database and Data Management
1 -
database tables
1 -
Databricks
1 -
Dataframe
1 -
Datasphere
5 -
Datasphere Delta
1 -
datenbanksicherung
1 -
dba cockpit
1 -
dbacockpit
1 -
Debug
1 -
Debugging
2 -
Defender
1 -
Delimiting Pay Components
1 -
Delta Integrations
1 -
Destination
3 -
Destination Service
1 -
Developer extensibility
1 -
Developing with SAP Integration Suite
2 -
Devops
1 -
digital transformation
1 -
Disaster Recovery
1 -
Document Information Extraction
1 -
Documentation
1 -
Dot Product
1 -
DOX
1 -
DQM
1 -
dump database
1 -
dump transaction
1 -
e-Invoice
1 -
E4H Conversion
1 -
Eclipse ADT
1 -
Eclipse ADT ABAP Development Tools
3 -
edoc
1 -
edocument
1 -
ELA
1 -
Embedded Consolidation
1 -
Embedding
1 -
Embeddings
1 -
Emergency Maintenance
1 -
Employee Central
1 -
Employee Central Payroll
1 -
Employee Central Time Off
1 -
Employee Information
1 -
Employee Rehires
1 -
Enable Now
1 -
Enable now manager
1 -
endpoint
1 -
Enhancement Request
1 -
Enterprise Architecture
2 -
Enterprise Asset Management
2 -
Entra
1 -
ESLint
1 -
ETL Business Analytics with SAP Signavio
1 -
Euclidean distance
1 -
Event Dates
1 -
Event Driven Architecture
1 -
Event Mesh
2 -
Event Reason
1 -
EventBasedIntegration
1 -
EWM
1 -
EWM Outbound configuration
1 -
EWM-TM-Integration
1 -
Existing Event Changes
1 -
Expand
1 -
Expert
2 -
Expert Insights
2 -
Exploits
1 -
Fiori
17 -
Fiori App Extension
2 -
Fiori Elements
2 -
Fiori Launchpad
2 -
Fiori SAPUI5
15 -
first-guidance
2 -
Flask
2 -
FLP_APP_MANAGER
1 -
FLP_CONTENT_MANAGER
1 -
Fragment Forms
1 -
Fragment Forms using ABA[
1 -
FTC
1 -
Full Stack
9 -
Funds Management
1 -
gCTS
1 -
Gemini
1 -
GenAI hub
1 -
General
3 -
Generative AI
4 -
Getting Started
1 -
GitHub
11 -
Google cloud
1 -
Grants Management
1 -
groovy
2 -
GTP
1 -
HANA
6 -
HANA Cloud
3 -
hana cloud database
2 -
Hana Cloud Database Integration
2 -
HANA DB
2 -
Hana Vector Engine
1 -
HANA XS Advanced
1 -
HanaDB
1 -
Historical Events
1 -
home labs
1 -
HowTo
1 -
HR Data Management
1 -
html5
9 -
HTML5 Application
1 -
ICCX
1 -
ico
1 -
Identity cards validation
1 -
idm
1 -
Impact of AI on Energy Industry's Future
1 -
Implementation
1 -
Improvement Maintenance
1 -
Infuse AI
1 -
input parameter
1 -
instant payments
1 -
Integration
4 -
Integration Advisor
1 -
Integration Architecture
1 -
Integration Center
1 -
Integration Suite
1 -
intelligent enterprise
1 -
Internal Table
1 -
IoT
2 -
Java
1 -
Java Script
1 -
JavaScript
2 -
JMS Receiver channel ping issue
1 -
job
1 -
Job Information Changes
1 -
Job-Related Events
1 -
Job_Event_Information
1 -
joule
4 -
Journal Entries
1 -
Just Ask
1 -
Kafka
1 -
Kerberos for ABAP
10 -
Kerberos for JAVA
9 -
KNN
1 -
Launch Wizard
1 -
Learning Content
3 -
Life at SAP
4 -
lightning
1 -
Linear Regression SAP HANA Cloud
1 -
Live Sessions
1 -
LLM
1 -
Loading Indicator
1 -
local tax regulations
1 -
LP
1 -
Machine Learning
6 -
Machine learning using SAP HANA
1 -
Marketing
1 -
Master Data
3 -
Master Data Governance
1 -
Master Data Management
15 -
Maxdb
2 -
MDG
2 -
MDGM
1 -
MDM
1 -
Message box.
1 -
Messages on RF Device
1 -
Microservices Architecture
1 -
Microsoft
1 -
Microsoft Universal Print
1 -
Middleware Solutions
1 -
Migration
6 -
ML Model Development
1 -
MLFlow
1 -
Modeling in SAP HANA Cloud
9 -
Monitoring
3 -
MPL
1 -
MTA
1 -
Multi-factor-authentication
1 -
Multi-Record Scenarios
1 -
Multilayer Perceptron
1 -
Multiple Event Triggers
1 -
Myself Transformation
1 -
Neo
1 -
NetWeaver
1 -
Neural Networks
1 -
New Event Creation
1 -
New Feature
1 -
Newcomer
1 -
NodeJS
3 -
OCR
1 -
ODATA
3 -
OData APIs
1 -
odatav2
1 -
ODATAV4
1 -
ODBC
1 -
ODBC Connection
1 -
ODP
1 -
ODP connectivity
1 -
ODP to Datasphere
1 -
Onpremise
1 -
open source
2 -
OpenAI
1 -
OpenAI API
1 -
Optimized Story Experience
1 -
Oracle
1 -
Overhead and Operational Maintenance
1 -
PaPM
1 -
PaPM Dynamic Data Copy through Writer function
1 -
PaPM Remote Call
1 -
Partner Built Foundation Model
1 -
PAS-C01
1 -
Pay Component Management
1 -
Personal story
1 -
PGP
1 -
Pickle
1 -
pio
1 -
PLANNING ARCHITECTURE
1 -
Plant Maintenance
2 -
Plugin Attachment
1 -
PO Directory API
1 -
Popup in Sap analytical cloud
1 -
Postgresql
1 -
PostgrSQL
1 -
POSTMAN
1 -
Practice Systems
1 -
Prettier
1 -
Proactive Maintenance
1 -
Process Automation
3 -
Process Management
1 -
Product Updates
6 -
Product Updates
1 -
PSE
1 -
PSM
1 -
Public Cloud
1 -
Python
5 -
python library - Document information extraction service
1 -
Qlik
1 -
Qualtrics
1 -
RAP
3 -
RAP BO
2 -
Rapid Data Governance
2 -
RDG
1 -
React
1 -
Reactive Maintenance
2 -
Record Deletion
1 -
Recovery
1 -
recurring payments
1 -
redeply
1 -
Release
1 -
Remote Consumption Model
1 -
Replication Flows
1 -
Replication using Cloud Connector
1 -
Report Malfunction
1 -
report painter
1 -
research
1 -
Research and Development Custom Widgets in SAP Analytics Cloud
1 -
Resilience
1 -
REST
1 -
REST API
1 -
Retagging Required
1 -
RFID
1 -
Risk
1 -
Robots
1 -
rolandkramer
3 -
Rolling Kernel Switch
1 -
route
1 -
Route determination
1 -
Router Non-XML condition
1 -
rules
1 -
S4 HANA
3 -
S4 HANA ABAP Dev
1 -
S4 HANA Cloud
2 -
S4 HANA On-Premise
3 -
S4HANA
8 -
S4HANA Cloud
1 -
S4HANA_OP_2023
2 -
SAC
12 -
SAC PLANNING
10 -
SAN
1 -
SAP
4 -
SAP ABAP
1 -
SAP Advanced Event Mesh
2 -
SAP AI Core
11 -
SAP AI Launchpad
9 -
SAP Analytic Cloud
1 -
SAP Analytic Cloud Compass
1 -
Sap Analytical Cloud
1 -
SAP Analytics Cloud
9 -
SAP Analytics Cloud for Consolidation
4 -
SAP Analytics cloud planning
1 -
SAP Analytics Cloud Story
1 -
SAP analytics clouds
1 -
SAP API Management
1 -
SAP Application Lifecycle Management
1 -
SAP Application Logging Service
1 -
SAP BAS
1 -
SAP Basis
6 -
SAP BO FC migration
1 -
SAP BODS
1 -
SAP BODS certification.
1 -
SAP BODS migration
1 -
SAP BPC migration
1 -
SAP BTP
28 -
SAP BTP Build Work Zone
3 -
SAP BTP Cloud Foundry
9 -
SAP BTP Costing
1 -
SAP BTP CTMS
1 -
SAP BTP Generative AI
1 -
SAP BTP Innovation
1 -
SAP BTP Migration Tool
1 -
SAP BTP SDK IOS
1 -
SAP BTPEA
1 -
SAP Build
12 -
SAP Build App
1 -
SAP Build apps
1 -
SAP Build CodeJam
1 -
SAP Build Process Automation
5 -
SAP Build work zone
11 -
SAP Business AI
1 -
SAP Business Objects Platform
1 -
SAP Business Technology
2 -
SAP Business Technology Platform (XP)
1 -
sap bw
2 -
SAP CAP
2 -
SAP CDC
1 -
SAP CDP
1 -
SAP CDS VIEW
1 -
SAP Certification
1 -
SAP Cloud ALM
5 -
SAP Cloud Application Programming Model
2 -
SAP Cloud Integration
3 -
SAP Cloud Integration for Data Services
1 -
SAP cloud platform
10 -
SAP Companion
1 -
SAP CPI
3 -
SAP CPI (Cloud Platform Integration)
3 -
SAP CPI Discover tab
1 -
sap credential store
1 -
SAP Customer Data Cloud
1 -
SAP Customer Data Platform
1 -
SAP Data Intelligence
1 -
SAP Data Migration in Retail Industry
1 -
SAP Data Services
1 -
SAP DATABASE
1 -
SAP Dataspher to Non SAP BI tools
1 -
SAP Datasphere
12 -
SAP DRC
1 -
SAP EWM
1 -
SAP Fiori
4 -
SAP Fiori App Embedding
1 -
Sap Fiori Extension Project Using BAS
1 -
SAP GRC
1 -
SAP HANA
1 -
SAP HANA Dev tools
1 -
SAP HANA PAL
1 -
SAP HANA Vector
1 -
SAP HCM (Human Capital Management)
1 -
SAP HR Solutions
1 -
SAP IDM
1 -
SAP Integration Suite
11 -
SAP Integrations
4 -
SAP iRPA
2 -
SAP LAGGING AND SLOW
1 -
SAP learning
1 -
SAP Learning Class
2 -
SAP Learning Hub
1 -
SAP Master Data
1 -
SAP MDG
1 -
SAP Odata
3 -
SAP on Azure
3 -
SAP PAL
1 -
SAP PartnerEdge
1 -
sap partners
1 -
SAP Password Reset
1 -
SAP PO Migration
1 -
SAP PO to CPI Migration
1 -
SAP Prepackaged Content
1 -
sap print
1 -
SAP Process Automation
2 -
SAP Process Integration
3 -
SAP Process Orchestration
2 -
SAP Router
1 -
SAP S4HANA
2 -
SAP S4HANA Cloud
3 -
SAP S4HANA Cloud for Finance
1 -
SAP S4HANA Cloud private edition
1 -
SAP Sandbox
1 -
SAP STMS
1 -
SAP successfactors
3 -
SAP SuccessFactors HXM Core
1 -
SAP Time
1 -
SAP TM
2 -
SAP Trading Partner Management
1 -
SAP UI5
1 -
SAP Upgrade
1 -
SAP Utilities
1 -
SAP-GUI
9 -
SAP-Login-PowerShell
1 -
SAP_COM_0276
1 -
SAPBTP
1 -
SAPCPI
1 -
SAPEWM
1 -
sapfirstguidance
4 -
SAPHANAService
1 -
SAPIQ
2 -
sapmentors
1 -
saponaws
2 -
saprouter
1 -
SAPRouter installation
1 -
SAPS4HANA
1 -
SAPUI5
6 -
SAPUI5 Extensibility
1 -
schedule
1 -
Script Operator
1 -
Secure Login Client Setup
9 -
security
11 -
Selenium Testing
1 -
Self Transformation
1 -
Self-Transformation
1 -
SEN
1 -
SEN Manager
1 -
Sender
1 -
service
2 -
SET_CELL_TYPE
1 -
SET_CELL_TYPE_COLUMN
1 -
SFTP scenario
2 -
Simplex
1 -
Single Sign On
9 -
Singlesource
1 -
SKLearn
1 -
Skybuffer AI
1 -
Slow loading
1 -
SOAP
3 -
SOAP Web Service
1 -
Software Development
1 -
SOLMAN
1 -
solman 7.2
2 -
Solution Manager
3 -
sp_dumpdb
1 -
sp_dumptrans
1 -
SQL
2 -
sql script
1 -
SSL
10 -
SSO
9 -
Story2
1 -
Substring function
1 -
SuccessFactors
1 -
SuccessFactors Platform
1 -
SuccessFactors Time Tracking
1 -
Sybase
1 -
Syniti RDG
1 -
Synthetic User Monitoring
1 -
system copy method
1 -
System owner
1 -
Table splitting
1 -
Tax Integration
1 -
Technical article
1 -
Technical articles
1 -
Technical_catalog
1 -
Technology Updates
15 -
Technology Updates
1 -
Technology_Updates
1 -
terraform
1 -
Testing
1 -
Threats
2 -
Time Collectors
1 -
Time Off
2 -
Time Sheet
1 -
Time Sheet SAP SuccessFactors Time Tracking
1 -
Tips and tricks
2 -
toggle button
1 -
Tools
1 -
Trainings & Certifications
2 -
Transformation Flow
1 -
Transport in SAP BODS
1 -
Transport Management
1 -
TypeScript
3 -
ui designer
1 -
unbind
1 -
Unified Customer Profile
1 -
UPB
1 -
UploadSetTable
1 -
Use of Parameters for Data Copy in PaPM
1 -
User Unlock
1 -
VA02
1 -
Validations
1 -
Vector Database
2 -
Vector Engine
1 -
Vectorization
1 -
Visual Studio Code
1 -
VSCode
2 -
VSCode extenions
1 -
Vulnerabilities
1 -
Web SDK
1 -
Web Service Configuration
1 -
Webhook
1 -
where used
1 -
work zone
1 -
Workflow Management
2 -
workload
1 -
xsa
1 -
XSA Refresh
1
- « Previous
- Next »
- What’s new with SAP Build Work Zone guided experiences in Technology Blogs by SAP
- SAP BTP FAQs - Part 4 (DevOps) in Technology Blogs by SAP
- Experience Instant Translation on SAP Help Portal with our New Feature MT on-the-fly in Technology Blogs by SAP
- AI Launchpad: "Generative AI Hub" menu not displayed in Technology Q&A
- Configuring SAP Cloud ALM for Integration Suite in Technology Blogs by Members
| User | Count |
|---|---|
| 10 | |
| 10 | |
| 7 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |