
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by Members
- Connecting SAP IAS as a proxy to Azure AD using Op...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
UPDATE: E-Book for this blog is now available for download
It contains all information from this blog as well as the configuration part and deals with the integration of SAP Identity Authentication Service with your Azure Tenant.
Most of the implementations with corporate IDPs we have done so far were based on the SAML 2.0 standard. In the Q2 2022 roadmap, you can find the information that SAP IAS now supports federation with a corporate identity provider using OpenID Connect. As of September 2022, this support is limited to Microsoft Azure Active Directory. In this scenario, IAS uses the Azure OpenID Connect identity provider as an external authenticating authority. IAS thus acts as a proxy to delegate authentication to the external IDP.
This blog is for those of you who struggle with configuring your SAP IAS tenant as a proxy to forward authentication requests to your Azure AD tenant using OpenID Connect.
In our opinion, configuring this scenario currently isn't sufficiently documented in SAP Help as of September 2022, to put it mildly. Sorry SAP, but we only received the necessary information through the OSS and your support, this could go better.
For this reason, we like to share our experience with the community and look forward to further discussions on this topic. I'm happy to exchange views on the benefits of connecting IAS to the corporate IDP via ODIC rather than SAML.

Even if you are familiar with SAML 2.0 you may have noticed, OIDC works differently. It supports different authentication flows and the terminology used for the involved entities is different as well. In short, to really understand and implement OpenID Connect, we recommend trying to first understand the underlying OAuth 2.0 framework. OIDC operates on top of it.
Furthermore, OIDC is considered SAP's preferred standard for the SAP BTP and undoubtedly future SaaS applications. SAP BTP in combination with SAP Cloud Identity Services, automates the creation of OpenID Connect (OIDC) applications with the customers' IAS tenant(s). Therefore, soon more and more SAP organizations will have points of contact with this standard… have fun reading!
TOC
Introduction
Benefits of using IAS in proxy mode
Adjustment of claims (modify, enrich or replace)
Identity Federation
Conclusion
Benefits of OIDC compared with SAML
What is Security Assertion Markup Language (SAML) 2.0
What is OAuth 2.0
What is OpenID Connect (OIDC) 1.0
How are OIDC and SAML connected
Conclusion
Configuration guideline
Obtaining required information from your Azure tenant
Setup the OpenID Connect IDP in IAS
Register IAS as an application in your Azure tenant
Finish and validate the OpenID Connect IDP configuration in IAS
Obtaining an ID token from your Azure tenant using Postman
Introduction
In a standard setup, your IAS tenant will act as the default identity provider (IDP) for your applications. IAS itself can serve the function of both, SAML 2.0 and OpenID Connect IDP. Furthermore, the SAP IAS supports protocol conversion, which is often used in proxy scenarios:

To simplify access, organizations typically want to reuse their existing IDP. Often these are Azure AD, ADFS, Nevis Identity Suite, Okta, Ping Identity, and other SAML and/or OIDC-compliant IDPs that one may like to integrate with.
IAS delegates authentication to the external IDP and functions as a proxy for another IDP. An IDP proxy allows the creation of trust relationships that simplify the management of the many SAP applications (cloud and on-premises). The reason for this is simple: this IDP often is connected with your corporate user base, knows all identities, handles their login credentials, and offers additional SSO and security capabilities such as MFA.
With the FIDO2 support, we observe tendencies indicating increased use of passwordless authentication. IAS allows integration with third-party solutions in flexible ways. Those may be used to guarantee the highest level of privacy and security including features like identity verification. Such solutions like the Nevis authentication cloud can cover different B2C, B2B, and B2G use cases with significantly higher security and a broader range of capabilities. Think about scenarios geared towards customers and external partners, developers, and others.
The well-known combination of SAP IAS and MSFT Azure AD unites conditional authentication and MDM policies like restricting access to company-managed devices only with additional security features from SAP IAS or third parties.
Benefits of using IAS in proxy mode
SAP Cloud Identity Authentication (IAS) acting as a proxy, can use a SAML 2.0 or an OpenID Connect identity provider as an external authenticating authority for the application. The choice depends on your scenario and needs. For SAP BTP and mobile applications, the recommended protocol is OpenID Connect. On the other hand, if in your scenario IAS acts as a proxy to multiple identity providers, and you allow the partner users to log in via their corporate identity providers, the choice could be SAML 2.0.

In one of our older blogs, we already wrote about using IAS acting as a proxy to delegate authentication requests to existing (and even multiple) corporate identity providers. To obtain some basic understanding of the proxy scenario we recommend reading this blog first.
From an authentication perspective, in short here is what happens:
- A user tries to access the target application and is redirected to the IDP configured in the SAP application (IAS).
- Based on conditional authentication rules (mostly email domain) or static configuration, IAS delegates the authentication to the corporate IDP (Azure).
- At this stage, user authentication is required for the first time, based on the windows credentials. In most cases, the users benefit from SSO combined with MFA.
- Using the SAML assertion (or ID token) issued from Azure AD, the user is propagated to IAS and the correct identity is determined in the IdDS (Identity Directory Service) used by IAS.
- As the IAS knows about the user's attributes and applies the configuration of the target application (SP) it issues the final SAML assertion (or ID token).
- It will contain the required identifiers like an e-mail address, an employee ID or login name, and even certain claims and groups or other custom attributes, which the target application can evaluate and use for AuthN and AuthZ.
- This configuration can be done individually for each application in IAS, including protocol conversion and enrichment or modification of claims.
It is important to understand that from the perspective of the corporate IDP, the IAS is just another service provider (SP). In typical customer scenarios, a large number of service providers continue to be connected directly with the corporate IDP, while the IAS is used as a central hub and proxy system for the connected SAP applications.
Adjustment of claims (modify, enrich or replace)
Every cloud application has its characteristics concerning user management and the requested Name Identifier formats and attributes. This affects the user mapping that you need to take care of after the successful authentication process. After exchanging the metadata on both sides, it was determined, for example, that Azure passes the email address as a SAML NameID with the format urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress and a few other desired claims (possibly group memberships or UIDs).
The corporate IDP is activated for the respective application(s) in IAS, which always is the issuer of the SAML assertion for the respective (SAP) target application. However, depending on the configuration, it can either pass on the claims defined by the corporate IDP or additional ones from the IAS user store.
Furthermore, IAS supports RegEx filters and various modifications and transformations for the assertion attributes received from the corporate identity provider before they are sent to the application. IAS can override the assertion attributes from the corporate IDP and instead provide attributes, claims, and group assignments that are maintained in the IAS console or provisioned by an IDM system using SCIM.
Identity Federation
ID-Federation by definition provides the means to share identity information across company boundaries. A User must be unambiguous and clearly identifiable, even though different user identifiers may exist across the landscape. The name identifier (name ID) is the means to establish a common identifier and once established, the user is said to have a federated identity.
The administrator of the IAS tenant can determine whether the attributes from the SAML assertion of the corporate IdP or the IAS user store should be used. Access to every single application can be restricted based on the user profile, or additional risk-based authentication policies which can be applied and enforced in addition.
You may also want to check if the users authenticated by the corporate identity provider exist in the SAP IAS. For users that exist, data from the IAS user store is taken and the NameID, assertion and default attributes according to the application configuration are sent. For users with no profile in SAP IAS, the application receives the NameID attribute from the corporate IdP assertion, and the attributes according to the application configuration.
To make use of the Identity Federation features, additional configurations at the SAP IAS tenant must be made so that the changed attributes are taken into account. Furthermore, companies need to implement automated user provisioning. This way, the profiles can be generated automatically in SAP IAS. The use of other SAP solutions such as SAP IDM 8.0 in conjunction with the SAP Cloud Identity Provisioning is helpful to manage the user lifecycle.
Example: The assertion attributes received from the corporate IDP should be changed before they are sent to the application. Prefixes or suffixes can be added or special attributes (Application Custom Attributes) can be used. This works for both SAML 2.0 and OpenID Connect (id_token) applications. So instead of the email address of the Azure user (for example), the IAS Login Name can be sent as NameID with the format unspecified to the SAP cloud application.
Thanks to these features, the proxy scenario can be expanded to authenticate employees who have also been provisioned in the SAP IAS to the target application with different or enriched SAML claims. Also to authenticate external users, such as partners and customers, directly at the IAS without being known in Azure (IDP-initiated authentication via a special URL; this way, the Azure login can be bypassed for certain users despite the corporate IdP being activated).
Finally, this proxy integration allows using Identity Federation/Propagation between the corporate identity provider and the IAS. To support this, IdDS provides an extendable user store with a set of SCIM APIs that aim to simplify user management and persistence. With this, the concept of the universally unique identifier (UUID) has been introduced at the end of 2020 where IAS is the instance that generates and owns it.
This is what makes IAS so powerful and flexible and why SAP recommends persisting users to IAS. To obtain further information about the IdDS you can read this nice blog from Sonia Petrescu.
Conclusion
It became clear that SAP Cloud Identity Services with its capabilities of secure authentication, identity federation, SSO, and SCIM-based identity provisioning are a core element in SAP BTP. Consequently, many customers are connecting the Identity Services as a proxy to their corporate IDP to reuse existing processes for authentication, SSO, or MFA. This way they decide if the user identifiers and claims are just forwarded as received from the corporate IDP or managed through the IAS utilizing its user persistence and group management interfaces. This way, customers control the authorization independently allowing for separation of Azure and SAP security administration teams. Lastly, there are interfaces allowing to automate everything using APIs through an existing IAM solution.
Benefits of OIDC compared with SAML
Two of the main authentication protocols in the cloud world nowadays are:
- OpenID Connect (OIDC 1.0)
- Security Access Markup Language (SAML 2.0)
Key aspects of both are asserting a user's identity, providing standardized mechanisms and protocols, different authentication flows, and finally trust. Both provide a cross-domain and cross-vendor single sign-on (SSO) standard.
What is Security Assertion Markup Language (SAML) 2.0?
SAML is the most flexible and adopted SSO technology supporting both on-premises and cloud applications. It is an XML-based authentication framework that is specified primarily for browser-based access. It uses a dynamic token model that works based on assertions. Here both the authenticating instance and the application server can be operated externally, supporting more flexible user federation scenarios beyond the B2E use case.
SAML-enabled web applications delegate user authentication to a central instance. The identity provider proves that a subject (user) has identified himself. Users authenticate to the IDP by different means, which may involve various supported SSO methods or additional authentication factors. A successful authentication triggers the creation of a SAML assertion that certifies a user's identity against the target application, termed the SAML service provider (SP). IDP and SP must establish a mutual relationship of trust beforehand. That involves the exchange of so-called SAML metadata on both sides containing the Entity IDs, protocol endpoints, supported bindings and attribute formats, and required cryptographic keys.
A SAML assertion enables SSO during the lifetime of the browser session. It is accepted as proof of identity by web applications. The assertion definition is very flexible and enables an easy mapping of attributes between systems for loosely coupled integration across organizations. Browser applications on desktop and mobile devices support the SAML authentication flow.
SAML 2.0 is a very secure and powerful framework based on X(AC)ML, X.509, and digital signatures and albeit older, still a good choice for various authentication and authorization scenarios. No surprise SAML is not designed for the requirements of modern mobile apps, after all this standard existed even before I held the first iPhone 2g in my hands 🙂
The simple fact that SAML is older compared to OIDC, doesn't necessarily mean it's no longer valid or insecure. Recently a former security colleague and namesake of mine impressively reminded me of the good old client-certificate-based TLS authentication (CBA). Many are dealing with phishing-resistant MFA right now, while CBA has been resistant to monster-in-the-middle attacks since a time when no one paid attention to gender neutrality and you could call it man-in-the-middle - it was 1999. Pay attention to rfc2246 "CertificateVerify": The client must sign the previous session including the server certificate. This ensures security even if the client trusts an incorrect CA certificate. (Thanks Carsten)
To learn more about secure authentication for SAP and SAML, you can read the OASIS SAML 2.0 technical overview and one of our previous blogs
Plenty of other blogs about SSO and SAP cloud security can be found here
What is OAuth 2.0?
OAuth 2.0 (RFC 6749) is seen as a complete redesign and not compatible with the deprecated OAuth 1.0 standard. OAuth still is an authorization framework that solves the problem of delegated access without credential sharing, is a protocol for delegating authorizations, and is not suitable for authentication.
It aims to simplify authorization for developers as it offers specific authorization processes - called flows - suitable for different application use cases and so-called Authorization Grant types. To request access to an OAuth-protected resource (API), the OAuth client obtains authorization from the resource owner - with this permission, the client then requests an access token.

OAuth doesn’t share password data but instead uses authorization tokens to prove an identity between consumers and service providers. SAML uses XML to pass messages while OAuth uses JSON. As OAuth works with RESTful API endpoints it is the best choice for mobile and modern web (cloud) applications, (I)IoT devices. SAML 2.0 using XML and session cookies, for example, would still be fine for SAP portals, your SAP Fiori Launchpad, and other ICF applications.
OAuth 2.0 has established itself as the standard for securing API access. Since the OAuth process (obtaining access token) is usually required in combination with user authentication, it made sense to use OAuth for the login as well - this is where OpenID Connect comes into play.
Check out this great blog from rajaprasad.gupta for more details about OAuth and JWT.
What is OpenID Connect (OIDC) 1.0?
OpenID Connect 1.0 was adopted as a standard in February 2014 and should not be confused with the outdated OpenID 2.0 standard.
Put simply, OAuth 2.0 is a protocol and - with OpenID Connect 1.0 as an extension - a login method that confirms user identities based on an existing, verified authentication (ID token) and authorizes them by using access tokens.
An OAuth client can request the OpenID extension by adding the scope "openid" to an authorization request. Information about the identity of the user and the authentication performed is returned to the client in an additional (OpenID-specific) token, the so-called ID token. The standard defines the ID token must be in the JWT format and is restricted to a specific client. Additionally, the UserInfo endpoint was introduced, seen as another OAuth-protected API for accessing user data.
Any OAuth 2.0 authorization server that supports OIDC is also known as an OpenID Provider (OP). Accordingly, every OAuth 2.0 client that uses OpenID Connect is called a Relying Party (RP).
“OpenID Connect 1.0 is a simple identity layer on top of the OAuth 2.0 protocol. It allows Clients to verify the identity of the End-User based on the authentication performed by an Authorization Server, as well as to obtain basic profile information about the End-User in an interoperable and REST-like manner.” (https://openid.net/connect/)
How are OIDC and SAML connected?
“The Security Assertion Markup Language (SAML) is an XML-based federation technology used in many enterprises and academic use cases. OpenID Connect can satisfy these same use cases but with a simpler, JSON/REST-based protocol. OpenID Connect was designed to also support native apps and mobile applications, whereas SAML was designed only for Web-based applications.” (https://openid.net/connect/faq/)
Conclusion
The three aspects of login, authentication and authorization can be realized using OAuth, JWT and OpenID Connect. As an extension to OAuth 2.0 it represents a functional and secure authentication system.
The main driver for a protocol is the client usage and with SAP cloud (BTP & SaaS) and especially with mobile applications the use of OAuth 2.0 and OIDC has gained stronger importance. IAS supports a mix of both standards. However, mixing always makes the configuration more complicated. Therefore if a corporate IDP supports OIDC and the client uses it, the complete authentication flow is much leaner compared to SAML2/OIDC in combination.
Configuration guideline
You can follow this documentation on help.sap.com. However, the v1 endpoint is still being used there. According to SAP they experienced unexpected behavior and suggested using the v2 endpoint. This information is currently not included in the documentation, for this reason, we suggest following the steps outlined here.
In this example, we use our demo environment with some sandbox systems (nothing secret, so we won’t obfuscate those values here)
Azure Tenant ID: bbffd6ff-54e5-498a-8632-2b05586ee6f9
IAS Tenant: ias.carstenolt.de
Obtaining required information from your Azure tenant
First, obtain the metadata from your Azure AD tenant. OpenID Connect describes a metadata document that contains most of the information required for an app to perform a login. For this, the OP typically publishes its metadata at a well-known URL. To query your discovery or well-known endpoint - use this URL: https://login.microsoftonline.com/<azure-tenant>/v2.0/.well-known/openid-configuration
Result:
{"token_endpoint":"https://login.microsoftonline.com/<azure-tenant>/oauth2/v2.0/token","token_endpoint_auth_methods_supported":["client_secret_post","private_key_jwt","client_secret_basic"],"jwks_uri":"https://login.microsoftonline.com/<azure-tenant>/discovery/v2.0/keys","response_modes_supported":["query","fragment","form_post"],"subject_types_supported":["pairwise"],"id_token_signing_alg_values_supported":["RS256"],"response_types_supported":["code","id_token","code id_token","id_token token"],"scopes_supported":["openid","profile","email","offline_access"],"issuer":"https://login.microsoftonline.com/<azure-tenant>/v2.0","request_uri_parameter_supported":false,"userinfo_endpoint":"https://graph.microsoft.com/oidc/userinfo","authorization_endpoint":"https://login.microsoftonline.com/<azure-tenant>/oauth2/v2.0/authorize","device_authorization_endpoint":"https://login.microsoftonline.com/<azure-tenant>/oauth2/v2.0/devicecode","http_logout_supported":true,"frontchannel_logout_supported":true,"end_session_endpoint":"https://login.microsoftonline.com/<azure-tenant>/oauth2/v2.0/logout","claims_supported":["sub","iss","cloud_instance_name","cloud_instance_host_name","cloud_graph_host_name","msgraph_host","aud","exp","iat","auth_time","acr","nonce","preferred_username","name","tid","ver","at_hash","c_hash","email"],"kerberos_endpoint":"https://login.microsoftonline.com/<azure-tenant>/kerberos","tenant_region_scope":"EU","cloud_instance_name":"microsoftonline.com","cloud_graph_host_name":"graph.windows.net","msgraph_host":"graph.microsoft.com","rbac_url":"https://pas.windows.net"}Setup the OpenID Connect IDP in IAS
On your IAS tenant switch to Identity Providers → Corporate identity providers
and create a new entry - for example: OIDC_IDP

Switch Identity Provider Type to OpenID Connect Compliant:

Now Switch to OpenID Connect configuration and enter the URL: https://login.microsoftonline.com/<azure-tenant>/v2.0/.well-known/openid-configuration
in the field Discovery URL. Press Load, and IAS will populate the Issuer URL from the metadata.
The issuer in this case is: https://login.microsoftonline.com/<azure-tenant>/v2.0

Now we see that we need to enter a Client ID and secret to authorize and validate our OIDC client connection. For this reason, now it’s time to switch to your Azure tenant as we first need to perform some steps there.
We will proceed here later on!
Register IAS as an application in your Azure tenant
In your Azure Portal switch to Azure Active Directory → App registrations.
Add a new registration. Enter a name representing your IAS tenant and choose the supported account types according to your needs. In our scenario, we will just use a single tenant:

After a user successfully authorizes an application, the authorization server will redirect the user back to the application. Hence, we need to add a Redirect URI from type Web with the value: https://<ias-tenant>/oauth2/callback

Azure already created the OAuth 2.0 Client ID for you, in this case 0b35d68a-8420-4b92-952e-67bf1b429978…which is one of the values you will require to finish the configuration on the IAS side:

In the next step add a secret to your Azure app via Add a certificate or secret → New client secret and configure the lifetime according to your policy (ask your Azure experts for advice):

The next screen will show you the new client secret, you need to copy the value of the client secret in your password safe. Please note those values cannot be viewed again, except for immediately after creation. You don't need the Secret ID.
In this case the value is: ~4y8Q*****************************ql which is the second information you will require to finish the configuration on the IAS side.
Summary
Client ID: 0b35d68a-8420-4b92-952e-67bf1b429978
Client Secret: ~4y8Q*****************************ql
Before you finish the configuration on your IAS tenant set up some additional stuff. In the next step, we want to provide the email address of the Azure user to the ID token (JWT) issued from Azure. In addition, we want to provide the groups claim to forward the sAMAccountName of all groups the user is assigned to.
Switch to Token configuration and add email as an optional claim to your ID token (While adding this claim your API permissions may be updated).
In the same way, add the groups claim, and the final result will look like this:

Please note: Your configuration and required claims may vary depending on your environment and requirements, this is just a sample configuration (!)
Finish the OpenID Connect IDP configuration in IAS
Since the app registration, the creation of client credentials, and custom settings have been done on the Azure side, we are ready to finish our configuration on the IAS side.
Back in your ODIC IDP configuration, enter Client ID and Client Secret and Validate the configuration. This will execute a client credential token request to your Azure IDP to verify the credentials:

You can have up to 20 scopes. The openid scope is added by default. Each scope can have a length of up to 99 characters.
For the client credentials flow to work, Azure requires some specific scopes. In our scenario we need to add the scope <azure-client-id></.default> to our configuration:

Update 09-11-22: adding the scope "<azure client id>/.default" in section "Finish the OpenID Connect IDP configuration in IAS" is not required any more for the validate feature (thanks Torsten)
Once added, let’s try again:

Information from SAP support: “Please keep in mind if you provide some further scopes it might lead to some issues for other flows which may require to remove this "/.default" scope again (which will make the client credentials flow fail) but the Corporate IdP configuration will be still valid if the save works. These scenarios depend a lot on the Third-Party Corporate IdP, in that case, Azure”
In our scenario, the user identifier should be obtained from the claim email contained in the received ID token. We defined not to use the sub but instead the email claim that should be used as the subject name identifier for this Corporate Identity Provider:

Technically you can send any attribute, here we just added the email scope, so Azure puts the email address into the “email" claim. In IAS we ensure the "Subject Name Identifier" for the Corporate IdP is "E-Mail" as well, so the user is successfully federated with the user object in the IAS IdDS.
Keep in mind your configuration may vary.
As a prerequisite, you must have enabled the Use Identity Authentication user store for this to work. Of course, we enabled Identity Federation in order to make use of the entire spectrum and flexibility of the IAS:

In addition, we recommend configuring your OpenID Connect IDP name similar to your custom domain from the very beginning (in case you have one in use):

Heureka! Time to test your setup
Obtaining an ID token from your Azure tenant using Postman
In fact, the federation between IAS and Azure uses the OAuth grant-type authorization code. This means that no ID token can be found in your browser by using common tracer tools.
If you are as curious as I am, you can get an ID token directly from your Azure tenant, to see what information is contained there and whether the claims are delivered correctly. There are many ways, here is a simple one using a POST request to the OAuth 2.0 token endpoint (v2) of your Azure tenant via Postman:

As a result, you will receive your “id_token” and you can decode it using jwt.io
Example ID Token:
eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsImtpZCI6IjJaUXBKM1VwYmpBWVhZR2FYRUpsOGxWMFRPSSJ9.eyJhdWQiOiIwYjM1ZDY4YS04NDIwLTRiOTItOTUyZS02N2JmMWI0Mjk5NzgiLCJpc3MiOiJodHRwczovL2xvZ2luLm1pY3Jvc29mdG9ubGluZS5jb20vYmJmZmQ2ZmYtNTRlNS00OThhLTg2MzItMmIwNTU4NmVlNmY5L3YyLjAiLCJpYXQiOjE2NjUwNTY1MDQsIm5iZiI6MTY2NTA1NjUwNCwiZXhwIjoxNjY1MDYwNDA0LCJlbWFpbCI6ImMub2x0QG5vZW1haWwuY29tIiwiZ3JvdXBzIjpbIlhJVF9BRF9HUk9VUF9TVVBQT1JUIiwiWElUX0FEX0dST1VQX0NPTlNVTFRJTkciLCJYSVRfQURfR1JPVVBfU0NQX1dFQklERSIsIlhJVF9BRF9HUk9VUF9FRFVDQVRJT04iLCJBUklCQV9Hcm91cF9GdW5rdGlvbjEiLCJYSVRfQURfR1JPVVBfQ0NBRE1JTlMiLCJTRlNGX0dyb3VwX0Z1bmN0aW9uMSJdLCJuYW1lIjoiQ2Fyc3RlbiBPbHQiLCJvaWQiOiI0ODAzNTE4My0xNDY4LTQ2ZDQtYjMzYy1mMzRhMDJjMzg0ZjIiLCJwcmVmZXJyZWRfdXNlcm5hbWUiOiJjLm9sdEBjYXJzdGVub2x0LmRlIiwicmgiOiIwLkFURUFfOWJfdS1WVWlrbUdNaXNGV0c3bS1ZcldOUXNnaEpKTGxTNW52eHRDbVhneEFJdy4iLCJzdWIiOiJBbkNpUFZFVU1UUXpSTWtRSFBWUU1qQ2p3el9wSFJRRms0VTl0S0J6Mi13IiwidGlkIjoiYmJmZmQ2ZmYtNTRlNS00OThhLTg2MzItMmIwNTU4NmVlNmY5IiwidXRpIjoiV3V5M01wd3R1a0sxX2NyNmZLazlBQSIsInZlciI6IjIuMCJ9.K6v2-8UnfA2rG8eXBIUSX6CaLGvAzFsIIDmQDTXV1XqCuX9VZSweHy33Q3TU2KwRpCmiXxYo4ccBr8euuIkUZyMgGDlM82GO1uQWZw6WzVIgsj7AXeT-DYD09mKwNTzu11I2_Js3rVdWQGWROXiSCXtF4LfiEarp2t6Sq5bI42t9cdmQYRT9BR9I8b6wVuNu2JJ5RXmXVO5o9Ln59m4NGkK4ZMqR2xCGxkmmUz42hMIdAIpj9vEDIj_01ziUJKftm9LUry4HcBWn4YHKoXtlq0NyukCwI5QFXZ7adMfcjFeqCVXTzGPTm6OOkDFvgEWlQllPR7T-pcpwhid6HA3jlQThe payload contains some important information like the issuer, the intended audience (aud) which is the IAS client ID as well as the claims email and groups.
{
"aud": "0b35d68a-8420-4b92-952e-67bf1b429978",
"iss": "https://login.microsoftonline.com/bbffd6ff-54e5-498a-8632-2b05586ee6f9/v2.0",
"...,
"email": "c.olt@noemail.com",
"groups": [
"XIT_AD_GROUP_CONSULTING",
…"
],
"name": "Carsten Olt",
…"
}Fine, this way you can use the E-Mail claim (email) as subject name identifier for authentication and the groups for authorization purposes.
In a recent project, we had the requirement to mix some groups from the corporate IDP with group claims from IAS. Even with OIDC, this is possible using the Default Attributes.
For example, to enrich the final SAML assertion that will be sent to the application with Azure groups that start with XIT_:
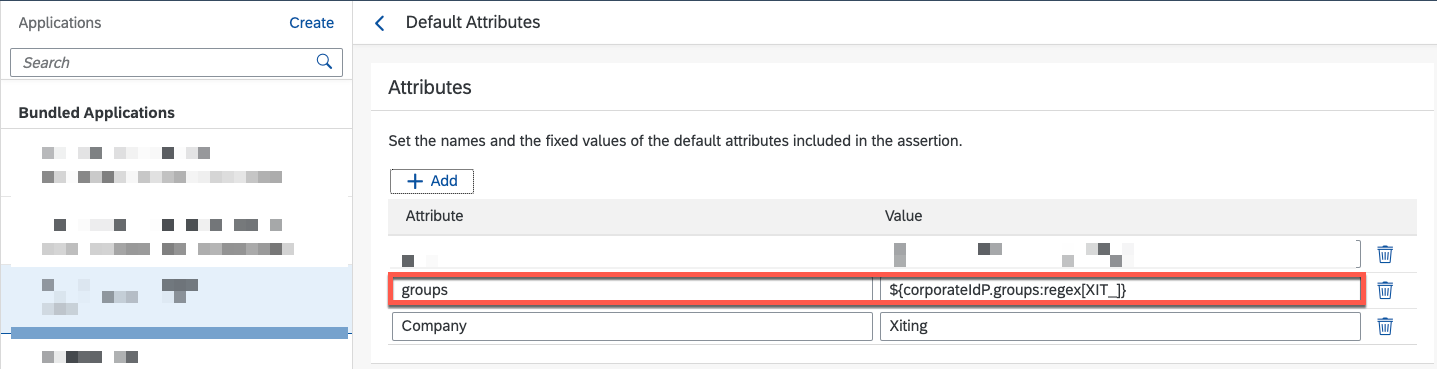
Finally, configure your new OIDC Corporate Identity Provider for your IAS applications (Conditional Authentication)
This article only deals with IAS using OIDC for the Corporate IDP. Depending on your scenario, IAS supports various flows and capabilities, you can read more about them here
We hope this blog was helpful!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
"automatische backups"
1 -
"regelmäßige sicherung"
1 -
505 Technology Updates 53
1 -
ABAP
14 -
ABAP API
1 -
ABAP CDS Views
2 -
ABAP CDS Views - BW Extraction
1 -
ABAP CDS Views - CDC (Change Data Capture)
1 -
ABAP class
2 -
ABAP Cloud
2 -
ABAP Development
5 -
ABAP in Eclipse
1 -
ABAP Platform Trial
1 -
ABAP Programming
2 -
abap technical
1 -
absl
1 -
access data from SAP Datasphere directly from Snowflake
1 -
Access data from SAP datasphere to Qliksense
1 -
Accrual
1 -
action
1 -
adapter modules
1 -
Addon
1 -
Adobe Document Services
1 -
ADS
1 -
ADS Config
1 -
ADS with ABAP
1 -
ADS with Java
1 -
ADT
2 -
Advance Shipping and Receiving
1 -
Advanced Event Mesh
3 -
AEM
1 -
AI
7 -
AI Launchpad
1 -
AI Projects
1 -
AIML
9 -
Alert in Sap analytical cloud
1 -
Amazon S3
1 -
Analytical Dataset
1 -
Analytical Model
1 -
Analytics
1 -
Analyze Workload Data
1 -
annotations
1 -
API
1 -
API and Integration
3 -
API Call
2 -
Application Architecture
1 -
Application Development
5 -
Application Development for SAP HANA Cloud
3 -
Applications and Business Processes (AP)
1 -
Artificial Intelligence
1 -
Artificial Intelligence (AI)
4 -
Artificial Intelligence (AI) 1 Business Trends 363 Business Trends 8 Digital Transformation with Cloud ERP (DT) 1 Event Information 462 Event Information 15 Expert Insights 114 Expert Insights 76 Life at SAP 418 Life at SAP 1 Product Updates 4
1 -
Artificial Intelligence (AI) blockchain Data & Analytics
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise Oil Gas IoT Exploration Production
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise sustainability responsibility esg social compliance cybersecurity risk
1 -
ASE
1 -
ASR
2 -
ASUG
1 -
Attachments
1 -
Authorisations
1 -
Automating Processes
1 -
Automation
1 -
aws
2 -
Azure
1 -
Azure AI Studio
1 -
B2B Integration
1 -
Backorder Processing
1 -
Backup
1 -
Backup and Recovery
1 -
Backup schedule
1 -
BADI_MATERIAL_CHECK error message
1 -
Bank
1 -
BAS
1 -
basis
2 -
Basis Monitoring & Tcodes with Key notes
2 -
Batch Management
1 -
BDC
1 -
Best Practice
1 -
bitcoin
1 -
Blockchain
3 -
BOP in aATP
1 -
BOP Segments
1 -
BOP Strategies
1 -
BOP Variant
1 -
BPC
1 -
BPC LIVE
1 -
BTP
11 -
BTP Destination
2 -
Business AI
1 -
Business and IT Integration
1 -
Business application stu
1 -
Business Architecture
1 -
Business Communication Services
1 -
Business Continuity
1 -
Business Data Fabric
3 -
Business Partner
12 -
Business Partner Master Data
10 -
Business Technology Platform
2 -
Business Trends
1 -
CA
1 -
calculation view
1 -
CAP
3 -
Capgemini
1 -
CAPM
1 -
Catalyst for Efficiency: Revolutionizing SAP Integration Suite with Artificial Intelligence (AI) and
1 -
CCMS
2 -
CDQ
12 -
CDS
2 -
Cental Finance
1 -
Certificates
1 -
CFL
1 -
Change Management
1 -
chatbot
1 -
chatgpt
3 -
CL_SALV_TABLE
2 -
Class Runner
1 -
Classrunner
1 -
Cloud ALM Monitoring
1 -
Cloud ALM Operations
1 -
cloud connector
1 -
Cloud Extensibility
1 -
Cloud Foundry
3 -
Cloud Integration
6 -
Cloud Platform Integration
2 -
cloudalm
1 -
communication
1 -
Compensation Information Management
1 -
Compensation Management
1 -
Compliance
1 -
Compound Employee API
1 -
Configuration
1 -
Connectors
1 -
Consolidation Extension for SAP Analytics Cloud
1 -
Controller-Service-Repository pattern
1 -
Conversion
1 -
Cosine similarity
1 -
cryptocurrency
1 -
CSI
1 -
ctms
1 -
Custom chatbot
3 -
Custom Destination Service
1 -
custom fields
1 -
Customer Experience
1 -
Customer Journey
1 -
Customizing
1 -
Cyber Security
2 -
Data
1 -
Data & Analytics
1 -
Data Aging
1 -
Data Analytics
2 -
Data and Analytics (DA)
1 -
Data Archiving
1 -
Data Back-up
1 -
Data Governance
5 -
Data Integration
2 -
Data Quality
12 -
Data Quality Management
12 -
Data Synchronization
1 -
data transfer
1 -
Data Unleashed
1 -
Data Value
8 -
database tables
1 -
Datasphere
2 -
datenbanksicherung
1 -
dba cockpit
1 -
dbacockpit
1 -
Debugging
2 -
Delimiting Pay Components
1 -
Delta Integrations
1 -
Destination
3 -
Destination Service
1 -
Developer extensibility
1 -
Developing with SAP Integration Suite
1 -
Devops
1 -
digital transformation
1 -
Documentation
1 -
Dot Product
1 -
DQM
1 -
dump database
1 -
dump transaction
1 -
e-Invoice
1 -
E4H Conversion
1 -
Eclipse ADT ABAP Development Tools
2 -
edoc
1 -
edocument
1 -
ELA
1 -
Embedded Consolidation
1 -
Embedding
1 -
Embeddings
1 -
Employee Central
1 -
Employee Central Payroll
1 -
Employee Central Time Off
1 -
Employee Information
1 -
Employee Rehires
1 -
Enable Now
1 -
Enable now manager
1 -
endpoint
1 -
Enhancement Request
1 -
Enterprise Architecture
1 -
ETL Business Analytics with SAP Signavio
1 -
Euclidean distance
1 -
Event Dates
1 -
Event Driven Architecture
1 -
Event Mesh
2 -
Event Reason
1 -
EventBasedIntegration
1 -
EWM
1 -
EWM Outbound configuration
1 -
EWM-TM-Integration
1 -
Existing Event Changes
1 -
Expand
1 -
Expert
2 -
Expert Insights
1 -
Fiori
14 -
Fiori Elements
2 -
Fiori SAPUI5
12 -
Flask
1 -
Full Stack
8 -
Funds Management
1 -
General
1 -
Generative AI
1 -
Getting Started
1 -
GitHub
8 -
Grants Management
1 -
groovy
1 -
GTP
1 -
HANA
5 -
HANA Cloud
2 -
Hana Cloud Database Integration
2 -
HANA DB
1 -
HANA XS Advanced
1 -
Historical Events
1 -
home labs
1 -
HowTo
1 -
HR Data Management
1 -
html5
8 -
Identity cards validation
1 -
idm
1 -
Implementation
1 -
input parameter
1 -
instant payments
1 -
Integration
3 -
Integration Advisor
1 -
Integration Architecture
1 -
Integration Center
1 -
Integration Suite
1 -
intelligent enterprise
1 -
Java
1 -
job
1 -
Job Information Changes
1 -
Job-Related Events
1 -
Job_Event_Information
1 -
joule
4 -
Journal Entries
1 -
Just Ask
1 -
Kerberos for ABAP
8 -
Kerberos for JAVA
8 -
Launch Wizard
1 -
Learning Content
2 -
Life at SAP
1 -
lightning
1 -
Linear Regression SAP HANA Cloud
1 -
local tax regulations
1 -
LP
1 -
Machine Learning
2 -
Marketing
1 -
Master Data
3 -
Master Data Management
14 -
Maxdb
2 -
MDG
1 -
MDGM
1 -
MDM
1 -
Message box.
1 -
Messages on RF Device
1 -
Microservices Architecture
1 -
Microsoft Universal Print
1 -
Middleware Solutions
1 -
Migration
5 -
ML Model Development
1 -
Modeling in SAP HANA Cloud
8 -
Monitoring
3 -
MTA
1 -
Multi-Record Scenarios
1 -
Multiple Event Triggers
1 -
Neo
1 -
New Event Creation
1 -
New Feature
1 -
Newcomer
1 -
NodeJS
2 -
ODATA
2 -
OData APIs
1 -
odatav2
1 -
ODATAV4
1 -
ODBC
1 -
ODBC Connection
1 -
Onpremise
1 -
open source
2 -
OpenAI API
1 -
Oracle
1 -
PaPM
1 -
PaPM Dynamic Data Copy through Writer function
1 -
PaPM Remote Call
1 -
PAS-C01
1 -
Pay Component Management
1 -
PGP
1 -
Pickle
1 -
PLANNING ARCHITECTURE
1 -
Popup in Sap analytical cloud
1 -
PostgrSQL
1 -
POSTMAN
1 -
Process Automation
2 -
Product Updates
4 -
PSM
1 -
Public Cloud
1 -
Python
4 -
Qlik
1 -
Qualtrics
1 -
RAP
3 -
RAP BO
2 -
Record Deletion
1 -
Recovery
1 -
recurring payments
1 -
redeply
1 -
Release
1 -
Remote Consumption Model
1 -
Replication Flows
1 -
Research
1 -
Resilience
1 -
REST
1 -
REST API
1 -
Retagging Required
1 -
Risk
1 -
Rolling Kernel Switch
1 -
route
1 -
rules
1 -
S4 HANA
1 -
S4 HANA Cloud
1 -
S4 HANA On-Premise
1 -
S4HANA
3 -
S4HANA_OP_2023
2 -
SAC
10 -
SAC PLANNING
9 -
SAP
4 -
SAP ABAP
1 -
SAP Advanced Event Mesh
1 -
SAP AI Core
8 -
SAP AI Launchpad
8 -
SAP Analytic Cloud Compass
1 -
Sap Analytical Cloud
1 -
SAP Analytics Cloud
4 -
SAP Analytics Cloud for Consolidation
2 -
SAP Analytics Cloud Story
1 -
SAP analytics clouds
1 -
SAP BAS
1 -
SAP Basis
6 -
SAP BODS
1 -
SAP BODS certification.
1 -
SAP BTP
20 -
SAP BTP Build Work Zone
2 -
SAP BTP Cloud Foundry
5 -
SAP BTP Costing
1 -
SAP BTP CTMS
1 -
SAP BTP Innovation
1 -
SAP BTP Migration Tool
1 -
SAP BTP SDK IOS
1 -
SAP Build
11 -
SAP Build App
1 -
SAP Build apps
1 -
SAP Build CodeJam
1 -
SAP Build Process Automation
3 -
SAP Build work zone
10 -
SAP Business Objects Platform
1 -
SAP Business Technology
2 -
SAP Business Technology Platform (XP)
1 -
sap bw
1 -
SAP CAP
2 -
SAP CDC
1 -
SAP CDP
1 -
SAP Certification
1 -
SAP Cloud ALM
4 -
SAP Cloud Application Programming Model
1 -
SAP Cloud Integration for Data Services
1 -
SAP cloud platform
8 -
SAP Companion
1 -
SAP CPI
3 -
SAP CPI (Cloud Platform Integration)
2 -
SAP CPI Discover tab
1 -
sap credential store
1 -
SAP Customer Data Cloud
1 -
SAP Customer Data Platform
1 -
SAP Data Intelligence
1 -
SAP Data Migration in Retail Industry
1 -
SAP Data Services
1 -
SAP DATABASE
1 -
SAP Dataspher to Non SAP BI tools
1 -
SAP Datasphere
9 -
SAP DRC
1 -
SAP EWM
1 -
SAP Fiori
2 -
SAP Fiori App Embedding
1 -
Sap Fiori Extension Project Using BAS
1 -
SAP GRC
1 -
SAP HANA
1 -
SAP HCM (Human Capital Management)
1 -
SAP HR Solutions
1 -
SAP IDM
1 -
SAP Integration Suite
9 -
SAP Integrations
4 -
SAP iRPA
2 -
SAP Learning Class
1 -
SAP Learning Hub
1 -
SAP Odata
2 -
SAP on Azure
1 -
SAP PartnerEdge
1 -
sap partners
1 -
SAP Password Reset
1 -
SAP PO Migration
1 -
SAP Prepackaged Content
1 -
SAP Process Automation
2 -
SAP Process Integration
2 -
SAP Process Orchestration
1 -
SAP S4HANA
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Cloud for Finance
1 -
SAP S4HANA Cloud private edition
1 -
SAP Sandbox
1 -
SAP STMS
1 -
SAP SuccessFactors
2 -
SAP SuccessFactors HXM Core
1 -
SAP Time
1 -
SAP TM
2 -
SAP Trading Partner Management
1 -
SAP UI5
1 -
SAP Upgrade
1 -
SAP-GUI
8 -
SAP_COM_0276
1 -
SAPBTP
1 -
SAPCPI
1 -
SAPEWM
1 -
sapmentors
1 -
saponaws
2 -
SAPUI5
4 -
schedule
1 -
Secure Login Client Setup
8 -
security
9 -
Selenium Testing
1 -
SEN
1 -
SEN Manager
1 -
service
1 -
SET_CELL_TYPE
1 -
SET_CELL_TYPE_COLUMN
1 -
SFTP scenario
2 -
Simplex
1 -
Single Sign On
8 -
Singlesource
1 -
SKLearn
1 -
soap
1 -
Software Development
1 -
SOLMAN
1 -
solman 7.2
2 -
Solution Manager
3 -
sp_dumpdb
1 -
sp_dumptrans
1 -
SQL
1 -
sql script
1 -
SSL
8 -
SSO
8 -
Substring function
1 -
SuccessFactors
1 -
SuccessFactors Time Tracking
1 -
Sybase
1 -
system copy method
1 -
System owner
1 -
Table splitting
1 -
Tax Integration
1 -
Technical article
1 -
Technical articles
1 -
Technology Updates
1 -
Technology Updates
1 -
Technology_Updates
1 -
Threats
1 -
Time Collectors
1 -
Time Off
2 -
Tips and tricks
2 -
Tools
1 -
Trainings & Certifications
1 -
Transport in SAP BODS
1 -
Transport Management
1 -
TypeScript
2 -
unbind
1 -
Unified Customer Profile
1 -
UPB
1 -
Use of Parameters for Data Copy in PaPM
1 -
User Unlock
1 -
VA02
1 -
Validations
1 -
Vector Database
1 -
Vector Engine
1 -
Visual Studio Code
1 -
VSCode
1 -
Web SDK
1 -
work zone
1 -
workload
1 -
xsa
1 -
XSA Refresh
1
- « Previous
- Next »
- [BIG PROBLEM] SAP Host Agent cannot connect to SYSTEMDB in Technology Q&A
- Corporate Git Setup on SAP BTP versus connecting to Corporate Git directly from SAP BAS in Technology Q&A
- Top Picks: Innovations Highlights from SAP Business Technology Platform (Q1/2024) in Technology Blogs by SAP
- Connecting SAP CAP with SAP Cloud ALM in Technology Q&A
- Unable to connect to Datasphere using the CLI in Technology Q&A
| User | Count |
|---|---|
| 11 | |
| 9 | |
| 7 | |
| 6 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |