
- SAP Community
- Groups
- Interest Groups
- Security and Compliance
- Blog Posts
- “What Will SAP Basis Administrators Do Once We Mov...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
By Jay Thoden van Velzen, Technical Advisor, Office of the CSO
SAPinsider 2024 Las Vegas completed my world tour of similar events after Melbourne and Copenhagen, giving me a priceless opportunity to hear from customers in three very different regions. In Australia, many customers were already committed to the cloud and just wanted to make sure SAP understood the importance to their business we got it right. In Europe, many customers were more comfortable staying on-premise. In America, customers wanted to understand RISE with SAP S/4HANA Cloud (RISE) better but were clearly considering the option.
One customer question kept coming up in Las Vegas in both conference sessions and on the exhibition show floor: “What will SAP Basis administrators do after our organization moves to RISE?”. The short answer to that is “higher value activities”.
The question raised makes sense, when many responsibilities previously covered by Basis administrators or consultants in RISE are taken care of by the cloud provider. But since it is a trope in the cybersecurity profession that regardless how well we do, we’re never done, it is worth exploring the question further. Many on-premise ERP teams are struggling to keep up with complex landscapes. A move to RISE frees teams up for tasks that they couldn’t get to before.
Remaining Responsibilities
It is important to remember, though, that depending on your chosen edition and selected options, customers still must manage several remaining responsibilities. The RISE with SAP S/4HANA Cloud, private edition and SAP ERP, PCE Roles and Responsibilities document specifies clearly which services are standard, which are excluded and which are optional or additional services customers can choose to perform or have SAP manage for them. These services are broken down in five different categories.
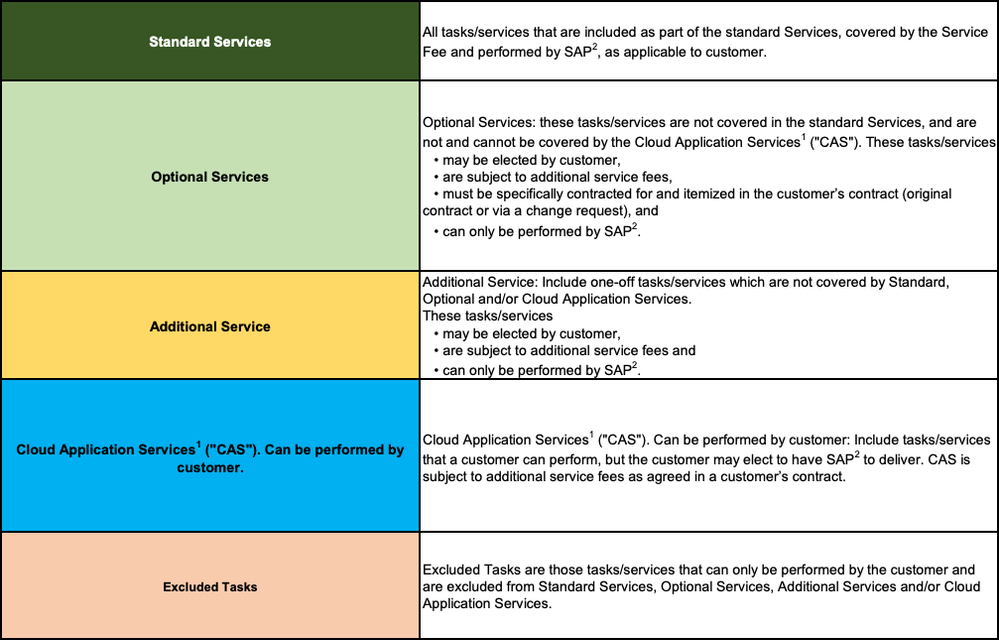
While many infrastructure tasks are done by SAP, the administration, security, and compliance of the ERP system itself, including roles and authorizations, or implemented business processes remain with the customer. That also extends to other cloud services. The Recommended Security Configurations for SAP Cloud Services lists security recommendations guides for many SaaS cloud services for the parts that customers must manage.
Governance, Risk and Compliance
Beyond system administration, the next layer up the value chain is in the area broadly covered by SAP’s Governance, Risk and Compliance (GRC) portfolio as well as partner offerings in the space. This also includes identity and access management, fraud detection, and process compliance. An increase in cybersecurity and data privacy regulations, as well as trade regulations and sanctions, make this topic of growing importance. And that further extends into Environmental, Social and Governance (ESG) management.
The rise of Business Artificial Intelligence only further increases the need for governance around data residency, data privacy, and security compliance regulations to ensure that data is only stored and accessed for the right purpose by the right people.
GRC is often the first step for customers towards SAP security and compliance beyond system administration. We can go a lot further.
Integration and Extension Security
Custom code isn’t going away but is done differently in the cloud. To ensure that systems stay agile and can be more easily kept up to date, the first responsibility for SAP Basis administrators is to keep the core clean. They must also manage secure and compliant processes for integrations and extensions developed on the Business Transformation Platform (BTP).
The security of BTP extensions includes authentication and authorizations across integrated systems, with SAP or third-party solutions. It also includes threat modeling, code scanning, governance of code repositories, version control, testing, and deployment controls. That is, all the aspects of secure software development and operations lifecycles (SDOL).
Many security incidents exactly exploit weaknesses in the boundaries between systems. Threat modeling for that reason explicitly focuses on risks associated with such security scope boundaries. In a cloud landscape, that especially focuses on authentication, authorizations, and Application Programming Interface (API) security to ensure that integrations are done on a least-privilege basis, and don’t inadvertently break authorization concepts or data residency and privacy requirements. Code repositories must be governed by oversight through pull requests and code checks, as well as code reviews before being merged into a main development branch and deployed.
Such processes may already be in place in your organization for in-house software development. But it should be easier than ever to align them to an SAP cloud environment than with on-premise ABAP code and transports in its own separate world. This will help improve dialogue with your cybersecurity teams.
Threat Detection
Such a dialogue is important as often cybersecurity and SAP teams are not on the best of terms. Only in rare cases have customers integrated threat detection for SAP systems into their broader cybersecurity threat detection processes, and many have little time for threat detection even among SAP Basis administrators. SAP and the partner ecosystem provide solutions in this space, but these are not adopted universally. Integration of SAP logs and alerts into Security Incident and Event Management (SIEM) solutions or security data lakes with effective detections built on top of them that engage their Security Operations Center (SOC) is even less common.
Phishing or credential compromise detection and the SOC raises an alert, this provides a lead for SAP Basis administrators to hunt down associated threats in their ERP systems. However, this one-way threat detection doesn’t help against threats that originate in the SAP system, involve an insider threat, or abuse credentials deliberately to target customer SAP cloud solutions. The infrastructure is monitored by SAP, but threat detection within the application itself is customer responsibility and SAP cloud operations teams do not have visibility, access, or context at that level.
For that, organizations need a bi-directional information flow, where SAP Basis administrators provide the domain expertise as cybersecurity teams generally have no familiarity with the solutions. SAP Basis administrators are best equipped to find out whether something in the landscape is not right and understand the potential impact.
Respond and Recover
The domain expertise of SAP Basis administrators in security incidents is similarly important – if only to prevent the response to the incident to be less disruptive than the incident itself. A natural reaction from the SOC would be to contain the incident and reimage the landscape, as they would with laptops and phones, or servers and cloud infrastructure.
But an attacker inside an SAP solution itself, manifest itself through a high-privileged user or service account. Such privileges and authorizations are part of the metadata of the application. Customers can certainly request restoration of systems from backups as part of their cloud service contract. But depending on how quickly it took to detect the intrusion, a system recovery could restore the access of the malicious actor, while causing significant business disruption.
SAP Basis teams may have incident response plans for system outages, but these must be accompanied with run books for security incident response. There must be agreed plans and roles and responsibilities defined between the SAP Basis and SOC teams. Threshold levels that match the priority and severity of the incident with the business impact of containment and response measures must be agreed with organizational stakeholders.
Then these run books must be practiced and trained by SOC and SAP Basis teams during tabletop exercises, fire drills, and red teaming. Security incidents in SAP systems are bound to be rare – compared to phishing or social engineering attacks, for instance. An active incident is the wrong time to find out that you don’t have the right authorizations or business mandate to act or are forced to make decisions that affect business operations in the heat of the moment and under pressure.
From System Administration to Managing Security and Compliance
Cybersecurity (or information security, depending on one’s career trajectory) grew out of infrastructure, network, and system integration into its own practice of managing security and compliance risks. Identity and Access Management (IAM) or vulnerability management are commonly understood to be cybersecurity disciplines. In an SAP context, these are seen as SAP Basis administration activities.
With common infrastructure tasks disappearing with RISE with SAP S/4HANA Cloud, SAP Basis can evolve into managing the security and compliance risks of SAP cloud solutions. Since cybersecurity teams don't have the SAP expertise, SAP Basis administrators are the prime candidates to make their organizations more resilient against security and compliance threats.
More Information
- RISE with SAP S/4HANA Cloud, private edition and SAP ERP, PCE Roles and Responsibilities
- Recommended Security Configurations for SAP Cloud Services
- SAP’s Governance, Risk and Compliance (GRC) portfolio
- Cyber Resilience and Cloud Transformation: Resolving the ERP Security Hamster Wheel
- Agile, Secure, and Compliant Business Operations Through Resilience
- SAP Managed Tags:
- Governance, Risk, Compliance (GRC), and Cybersecurity
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.


