
- SAP Community
- Products and Technology
- Financial Management
- Financial Management Blogs by SAP
- Security Safeguards for SAP Cloud Services: Addres...
Financial Management Blogs by SAP
Get financial management insights from blog posts by SAP experts. Find and share tips on how to increase efficiency, reduce risk, and optimize working capital.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Advisor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
08-31-2023
3:58 AM
(Jana Subramanian serves as APJ Principal Cybersecurity Advisor for Cloud Security and a Fellow of Information Privacy (FIP), awarded by the International Association of Privacy Professionals (IAPP). In this role, Jana supports strategic customer engagements on cybersecurity, data privacy, multi-cloud security integration architecture, contractual assurance, audit, and compliance.)
Introduction
Enterprise businesses are rapidly adopting to cloud-based solutions, as part of their digital transformation efforts and these cloud services are becoming increasingly popular among enterprises of all sizes, from startups to established corporations. Adopting to these platforms offer a number of advantages to enterprises, including cost-effectiveness, business transformation and agility, operational effectiveness, scalability, and flexibility among others. However, as enterprises move their data and operations to the cloud, it is important to evaluate threats, assess risks and take steps to protect their critical information and assets.
The Cloud Security Alliance (CSA) releases the Top Threats to Cloud Computing every year. The Pandemic Eleven report is a valuable resource for organizations that are using or considering using cloud computing. It provides a comprehensive overview of the top threats to cloud security and offers recommendations for mitigating these threats.
In this blog, we review enhanced security controls available with SAP Cloud Services in addressing "Top Threats to Cloud Computing Pandemic Eleven" report released by Cloud Security Alliance in June 2022.
SAP Holistic Approach to Cloud Security
Before delving into security safeguards available with SAP cloud services to protect against top threats to cloud computing listed in CSA Pandemic 11 report, we will briefly examine SAP’s holistic approach to cloud security. SAP places a strong emphasis on cloud security, embedding it into every aspect of its business from its high-level strategy to its day-to-day operations. In delivering cloud services, SAP adheres to industry-leading best practices and continually evaluates the effectiveness of its security measures to protect against a wide array of threats.
With comprehensive strategies like zero-trust and defense-in-depth in place, SAP enhances its security posture by implementing multiple layers of protection and an approach that assumes no inherent trust, ensuring robust safeguarding against potential threats. SAP's Cyber Fusion Center (CFC) is a unified strategy that merges cyber threat intelligence, security operations, and incident response. This synergy facilitates proactive defense measures to safeguard critical technological and data resources. By leveraging the Cyber Fusion Center, SAP is well-equipped to navigate the ever-changing landscape of cybersecurity threats.
With extensive “Threat Modelling” exercises throughout the Secure Software Development Lifecycle (SSDLC), SAP uncovers possible cyber risks and develops ways to lower these risks through effective mitigation strategies. The concepts of "shift left" and "shield right" moving security testing and prevention to earlier stages of the development and deployment process is adopted. This helps to catch security problems earlier and prevent them from causing damage. This proactive approach helps SAP identify and address potential security issues early on, making their software more resilient to cyber threats. These principles include the zero-trust model, a multi-layered defense approach, and a risk-based perspective.
In a hyperscale environment, SAP effectively owns and securely manages Hyperscale provider cloud accounts, safeguarding the environment and enforcing strong security measures to prevent any potential security misconfigurations within public cloud services. SAP’s approaches to manages cloud infrastructure is very well articulated in this blog and many more blogs related to this topic written by jay.thodenvanvelzen.
Threats to Cloud Computing Pandemic Eleven:
It is vital for organization to understand cloud computing threats to evolve strong security measures. Many businesses use cloud computing for business applications, software development, integration, extensions, analytics, business intelligence, and automation among others. Moving to the cloud has many benefits, but it's important to remain vigilant about potential risks. By understanding these risks and creating plans to handle them, businesses can keep their data safe and follow top cybersecurity guidelines.
The Cloud Security Alliance (CSA) "Top Threats to Cloud Computing Pandemic Eleven" report provides an overview of the top eleven threats to cloud computing. The CSA Pandemic Eleven report is a valuable resource for organizations that are looking to improve their cloud security posture. The report provides insights into the latest cloud security threats and best practices for mitigating them.
The eleven top threats to cloud computing, as identified by the Cloud Security Alliance, are as follows:
Security Safeguards in SAP Cloud Services to Address Cloud Computing Threats
In this following section, we will explore range of the security tools or services available with SAP cloud services that can be leveraged by customers or underlying SAP operational security to mitigate to common cloud computing threats highlighted in Pandemic 11.
Threat 1: Insufficient Identity, Credentials, Access, and Key Management
Security Safeguards Available with SAP Cloud Services:
This threat can be mitigated by implementing identity access management, authenticating users with multi-factor authentication, role-based access control. Only authorized users should access data, which can be managed by job roles using Role Based Access Control (RBAC). Customer Data should be encrypted both in transit and at rest with an ability to store the encryption securely. Auditing all user activity can help identifying suspicious behavior and take action to prevent data breaches.
Most of the SAP's cloud offerings are integrated with SAP Identity Authentication Service (IAS) and SAP Identity Provisioning Services (IPS). These services are consolidated into a centralized offering known as SAP Cloud Identity Services available in SAP BTP as a standard service.
The IAS can act as an identity provider itself or be used as an identity proxy to delegate and federate authentication to customer owned IDP with an existing single sign-on infrastructure.
Additionally, SAP IAS offers Risk Based Authentication which provides an extra layer of security. Administrators can define rules for authentication according to different risk factors and apply actions like Allow, Deny, and Two-Factor Authentication.
SAP offers SAP Identity Access Governance (IAG) which is a cloud-based service running on SAP BTP. This service has wide range of capabilities which includes.
For further reading and reference, please refer to the following blog:
Secure CCKMS/BYOK Key Management:
SAP protects customer data in the cloud by encrypting it in transit and at rest using strong encryption algorithms. Following, Segregation of Duties (SoD) Principle, SAP also separates the responsibility for data access and encryption key management function, which minimizes the risk of unauthorized access to your data. For few cloud solutions such as SAP S/4HANA cloud, private edition, SAP S/4HANA cloud, public edition, customer can use BYOK/CCKMS leveraging SAP Data Custodian Key Management Service (KMS), which gives customers even more control over customer data security. This feature enables customers to exercise greater control by employing their own encryption keys, known as Bring Your Own Key (BYOK). With this capability, customers retain full authority over the entire lifecycle of their encryption keys, further enhancing data security.
For most of the cloud services, SAP manages keys in a secure environment to protect these encryption keys from unauthorized access, alteration, or theft. This can involve physical security (like secure data centers), technical measures (like secure key storage solutions or hardware security modules), and operational practices (like regular audits and restricted access protocols). SAP apply segregation of duties principle ensuring no single individual has control over all aspects of any critical cloud operation relating to secure key management.
Threat 2: Insecure Interfaces and API
Security Safeguards Available with SAP Cloud Services:
The SAP cloud connector is critical software element that establishes a secure TLS1.2 mutual authentication tunnel between customer on-premises and the SAP Business Technology Platform. The SAP cloud Connector can be in DMZ or customer on-premises firewall, the cloud connector functions as a reverse invoke proxy, securely initiating a connection to your SAP BTP subaccount.
The cloud connector acts as a reverse invoke proxy, establishing a secure connection to the SAP BTP subaccount without altering firewall settings. It supports various protocols like HTTP and RFC for connecting to ABAP systems and links both SAP and non-SAP on-premises systems to SAP BTP. The SAP cloud connector also supports principal propagation, and it ensures user identity continuity between cloud and on-premises systems for comprehensive traceability.
Threat 3: Misconfiguration and Inadequate Change Control
Security Safeguards Available with SAP Cloud Services:
According to the 2023 IBM Cost of Data Breach Report, 11% of cyberattacks are as a result of cloud misconfigurations. The report also noted that, on average, it takes 278 days to detect and address these misconfigurations and financial loss due to cloud misconfiguration.
For SAP cloud customers, SAP cloud application delivers ability to configure access to resources based on the principle of least privilege and Role Based Access Control (RBAC). Additionally, application audit logs are enabled for at the application level including read access logs, change document logs which are accessible by customers. SAP also provides the SAP Cloud ALM (Application Lifecycle Management) as part of its SAP Cloud Services package. Among other advantages, this allows users to monitor modifications made to ABAP-based systems set up in SAP Cloud ALM.
For additional reference, please refer to SAP document on “Seven Ways SAP Helps Secure Technology Stacks on Public Clouds” and also read SAP community blogs published by jay.thodenvanvelzen
Threat 4: Lack of Cloud Security Architecture and Strategy
Security Safeguards Available with SAP Cloud Services:
It is important to emphasize that every SAP cloud service adheres to standard reference architectures, embedding both secure by design and secure by default principles. These services are built on the tenets of defense-in-depth and zero-trust architectural principles. Whether data is in transit or at rest, it is safeguarded with strong cryptographic algorithms. Each customer environment is segregated and isolated from others, ensuring utmost data security. On the software front, SAP employs a stringent Secure Software Development Lifecycle (SSDLC) process. This encompasses features such as: Role-based access control (RBAC), Identity and access management (IAM), Application Security, Data Encryption, least privilege access, Security audit logs.
These features are supported by robust operational security, including Vulnerability advisory services, a cyber fusion center, Continuous logging and monitoring mechanisms.
SAP provides comprehensive contractual assurances for its cloud services. These guarantees our commitment to data privacy regulation through data processing agreements and a service-level agreement (SLA) for system availability and support policies. Security Architecture is supported by an extensive framework of risk assessments, threat modelling, and SSDLC. The diagram below provides an overview of multi-layer approach to cloud security.
Threat 5: Insecure Software Development
Security Safeguards Available with SAP Cloud Services:
SAP employs a multi-layer approach to ensure the security of its software. SAP follows a secure software development process, which incorporates security best practices and regular reviews to identify and address vulnerabilities during the development phase.
SAP secure software development involve use a range of security tools to meticulously scan their code for any vulnerabilities. SAP performs both static and dynamic application security testing (SAST and DAST). Before any new software is launched, it undergoes scrutiny by a SAP security review board to ensure its robustness. Additionally, a bug bounty program is instituted, offering rewards to security researchers who pinpoint vulnerabilities, thereby leveraging the global community's expertise in enhancing their security posture. Recognizing the importance of continual learning, SAP regularly conducts security training for its staff to keep them abreast of the latest threats and best practices. Moreover, in the event of any security discrepancies, SAP is equipped with a security incident response plan, ensuring swift and effective actions to mitigate potential risks.
The SAP Secure Software Development Lifecycle approach can be referenced in this link.
Threat 6: Unsecured 3rd Party Resources
Security Safeguards Available with SAP Cloud Services:
SAP ensures integrity, reliability, and security of products and services throughout their lifecycle and across the entire supply chain. This includes vendor selection, software development, deployment, and maintenance. SAP conducts comprehensive risk assessment third party services to manage risks at each stage. Before onboarding a new vendor or third-party service, SAP performs risk assessment and due-diligence and ensure they meet SAP's security standards. Contracts with suppliers typically include clauses that obligate them to maintain certain security standards and master data processing agreements. When 3rd party software is involved, SAP examines 3rd party SSDLC and performs security assessments including vulnerability and patch management. SAP ensures that 3rd party services are securely configured by default and remain secure through updates and changes.
SAP utilizes sub-processors in the delivery of its cloud services. For transparency, customers can subscribe to the sub-processors list and will be automatically notified of any changes. Customers require S-User ID to login and download the sub-processor list from SAP Trust Center
Threat 7: System Vulnerabilities
Security Safeguards Available with SAP Cloud Services:
SAP has a comprehensive vulnerability management program that includes vulnerability assessments, penetration testing, and patch management. Vulnerability assessments are used to identify vulnerabilities in SAP cloud services. Penetration testing is used to simulate an attack on SAP cloud services to see if any vulnerabilities can be exploited. Patch management is used to apply security patches to SAP cloud services to fix vulnerabilities. SAP frequently releases security patches and updates to address identified vulnerabilities. SAP cloud services apply these patches promptly to ensure their systems are protected.
Threat 8: Accidental Cloud Data Disclosure
Security Safeguards Available with SAP Cloud Services:
Accidental cloud data disclosure can result from misconfigurations, malicious insiders, human errors, or insufficient access controls. To address this threat, SAP has implemented robust controls at multiple levels.
Threat 9: Misconfiguration and Exploitation of Serverless and Container workloads
Security Safeguards Available with SAP Cloud Services:
Misconfigurations and exploitation of serverless and container workloads are significant threats in cloud environments. SAP recognizes these threats and has integrated multiple controls to mitigate them in its cloud services, including SAP Business Technology Platform (SAP BTP).
These controls include:
These controls, combined with SAP's comprehensive approach to cloud security, provide robust protection against misconfigurations and potential exploitations of serverless and container workloads. However, it's also important for SAP's customers to be aware of and follow best practices when configuring and deploying their applications on the SAP Business Technology Platform.
Threat 10: Organized Crime/Hacker/APT
Security Safeguards Available with SAP Cloud Services:
Besides all the protective and detective security controls outlined in the previous section, the SAP Cyber Fusion Center also incorporates enhanced security measures such as analytics, defensive automation, cyber intelligence, and cloud security. SAP maintains both internal research teams and collaborates with external threat intelligence to comprehend emerging threats, taking proactive steps to address them. Cyber Fusion Center helps in assimilating and disseminating crucial threat insights.
SAP utilizes a Security Incident and Event Management platform. Within this system, SAP cloud services continuously collect and correlate platform logs, implement security use cases, and, where feasible, automate the remediation of security issues.
The SAP Cyber Fusion Center covers broadly following aspects for Cyber Threat Intelligence:
SAP Enterprise Threat Detection Cloud Edition: SAP has launched SAP Enterprise Threat Detection which is a cloud based (SaaS) SIEM application. This helps customer detect, analyse, and respond to cyberattacks on customer SAP systems. This is offered as cloud based managed service, where SAP manages all the underlying infrastructure and application. SAP takes the responsibility for the day-to-day operations of the SAP ETD platform. SAP's monitoring agents work around the clock, leveraging the application to identify and dissect security incidents 24/7. The application collects and analyses log data from customer's SAP systems to detect potential attacks. Customer can have access to security logs and real-time security dashboards and receive alerts in real time so customer can respond to security events swiftly.
Threat 11: Cloud Storage Data Exfiltration
Security Safeguards Available with SAP Cloud Services:
Data exfiltration is a threat that leads to the unauthorized transfer or retrieval of data from cloud storage environments. To mitigate against this threat, SAP maintains several security controls that are implemented as part of security by default and secure by design.
Data encryption:
Identity and access management (IAM):
Activity monitoring and logging:
Endpoint security:
Multi-layer defense:
Security awareness training:
Secure APIs:
Regular audits:
Backup and versioning:
Incident response plan:
Third Party Security Risk Assessment:
Conclusion
This blog summarizes how SAP Cloud Services mitigate and maintain security controls to address top threats facing cloud computing. As enterprises navigate their digital transformation journey to cloud computing, the security and integrity of data and applications remain paramount. For businesses leveraging SAP Cloud Services or considering a move to the cloud, it is essential to understand the associated threats and safeguards. As cyber threats grow in sophistication, SAP's defense strategies also evolve in tandem. Ultimately, organizations using cloud services must instil a culture of security awareness, invest in ongoing training, and stay up to date on the latest cybersecurity trends to protect themselves from cyber threats.
While technology provides the tools to secure our assets, it is the human element—vigilance, knowledge, and proactive approach to security that ultimately determines the strength of our cyber defense. In conclusion, cloud computing can match or even surpass the security standards of traditional computing environments when organizations implement proactive security governance, risk assessment, and meticulous attention to security measures. This will unlock the cloud's vast potential to its fullest extent.
Disclaimer
© 2023 SAP SE or an SAP affiliate company. All rights reserved. See Legal Notice on www.sap.com/legal-notice for use terms, disclaimers, disclosures, or restrictions related to SAP Materials for general audiences.
Introduction
Enterprise businesses are rapidly adopting to cloud-based solutions, as part of their digital transformation efforts and these cloud services are becoming increasingly popular among enterprises of all sizes, from startups to established corporations. Adopting to these platforms offer a number of advantages to enterprises, including cost-effectiveness, business transformation and agility, operational effectiveness, scalability, and flexibility among others. However, as enterprises move their data and operations to the cloud, it is important to evaluate threats, assess risks and take steps to protect their critical information and assets.
The Cloud Security Alliance (CSA) releases the Top Threats to Cloud Computing every year. The Pandemic Eleven report is a valuable resource for organizations that are using or considering using cloud computing. It provides a comprehensive overview of the top threats to cloud security and offers recommendations for mitigating these threats.
In this blog, we review enhanced security controls available with SAP Cloud Services in addressing "Top Threats to Cloud Computing Pandemic Eleven" report released by Cloud Security Alliance in June 2022.
SAP Holistic Approach to Cloud Security
Before delving into security safeguards available with SAP cloud services to protect against top threats to cloud computing listed in CSA Pandemic 11 report, we will briefly examine SAP’s holistic approach to cloud security. SAP places a strong emphasis on cloud security, embedding it into every aspect of its business from its high-level strategy to its day-to-day operations. In delivering cloud services, SAP adheres to industry-leading best practices and continually evaluates the effectiveness of its security measures to protect against a wide array of threats.
With comprehensive strategies like zero-trust and defense-in-depth in place, SAP enhances its security posture by implementing multiple layers of protection and an approach that assumes no inherent trust, ensuring robust safeguarding against potential threats. SAP's Cyber Fusion Center (CFC) is a unified strategy that merges cyber threat intelligence, security operations, and incident response. This synergy facilitates proactive defense measures to safeguard critical technological and data resources. By leveraging the Cyber Fusion Center, SAP is well-equipped to navigate the ever-changing landscape of cybersecurity threats.
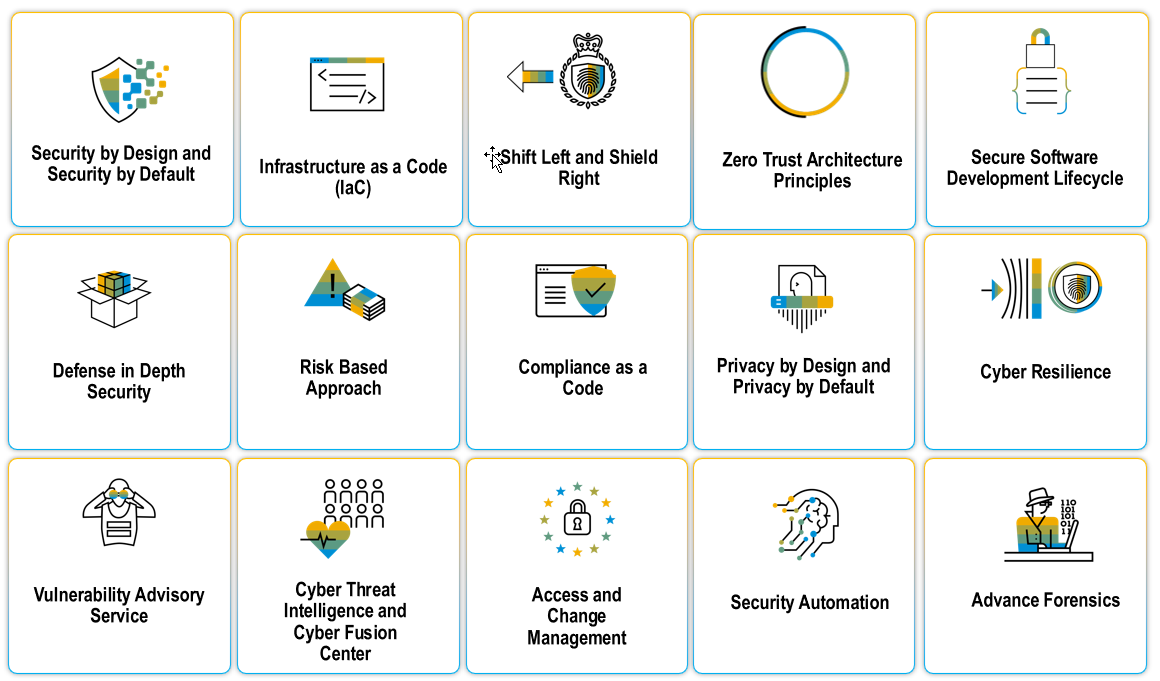
Figure 1: SAP Holistic Approach Against Cyber Threats
With extensive “Threat Modelling” exercises throughout the Secure Software Development Lifecycle (SSDLC), SAP uncovers possible cyber risks and develops ways to lower these risks through effective mitigation strategies. The concepts of "shift left" and "shield right" moving security testing and prevention to earlier stages of the development and deployment process is adopted. This helps to catch security problems earlier and prevent them from causing damage. This proactive approach helps SAP identify and address potential security issues early on, making their software more resilient to cyber threats. These principles include the zero-trust model, a multi-layered defense approach, and a risk-based perspective.
In a hyperscale environment, SAP effectively owns and securely manages Hyperscale provider cloud accounts, safeguarding the environment and enforcing strong security measures to prevent any potential security misconfigurations within public cloud services. SAP’s approaches to manages cloud infrastructure is very well articulated in this blog and many more blogs related to this topic written by jay.thodenvanvelzen.
Threats to Cloud Computing Pandemic Eleven:
It is vital for organization to understand cloud computing threats to evolve strong security measures. Many businesses use cloud computing for business applications, software development, integration, extensions, analytics, business intelligence, and automation among others. Moving to the cloud has many benefits, but it's important to remain vigilant about potential risks. By understanding these risks and creating plans to handle them, businesses can keep their data safe and follow top cybersecurity guidelines.
The Cloud Security Alliance (CSA) "Top Threats to Cloud Computing Pandemic Eleven" report provides an overview of the top eleven threats to cloud computing. The CSA Pandemic Eleven report is a valuable resource for organizations that are looking to improve their cloud security posture. The report provides insights into the latest cloud security threats and best practices for mitigating them.
The eleven top threats to cloud computing, as identified by the Cloud Security Alliance, are as follows:

Figure 2: Top Threats to Cloud Computing Pandemic Eleven
Security Safeguards in SAP Cloud Services to Address Cloud Computing Threats
In this following section, we will explore range of the security tools or services available with SAP cloud services that can be leveraged by customers or underlying SAP operational security to mitigate to common cloud computing threats highlighted in Pandemic 11.
Threat 1: Insufficient Identity, Credentials, Access, and Key Management
Security Safeguards Available with SAP Cloud Services:
This threat can be mitigated by implementing identity access management, authenticating users with multi-factor authentication, role-based access control. Only authorized users should access data, which can be managed by job roles using Role Based Access Control (RBAC). Customer Data should be encrypted both in transit and at rest with an ability to store the encryption securely. Auditing all user activity can help identifying suspicious behavior and take action to prevent data breaches.
Most of the SAP's cloud offerings are integrated with SAP Identity Authentication Service (IAS) and SAP Identity Provisioning Services (IPS). These services are consolidated into a centralized offering known as SAP Cloud Identity Services available in SAP BTP as a standard service.
The IAS can act as an identity provider itself or be used as an identity proxy to delegate and federate authentication to customer owned IDP with an existing single sign-on infrastructure.
- Single Sign-On (SSO)
- Multi-factor Authentication (MFA)
- Identity Federation: SAML 2.0. Open ID, OAuth 2.0. Authentication can be delegated to Corporate IDP
- Social Sign-On: SAP IAS can be integrated with social network identities like Google, Facebook, and LinkedIn.
- User Self-Service: Users can manage their account data and password themselves.

Figure 3: SAP Cloud Identity Services
Additionally, SAP IAS offers Risk Based Authentication which provides an extra layer of security. Administrators can define rules for authentication according to different risk factors and apply actions like Allow, Deny, and Two-Factor Authentication.
SAP offers SAP Identity Access Governance (IAG) which is a cloud-based service running on SAP BTP. This service has wide range of capabilities which includes.
- Access Analysis (enables you to detect and remediate segregation of duties (SoD) and critical access risks),
- Role Design Service (define and maintain compliant business roles),
- Access Request Service (create self-service access requests to business applications and HR-event driven identity lifecycle),
- Access Certification Service (review and certify user access with auditable workflow),
- Privileged Access Management Service (monitor access to sensitive and critical transactions, giving you better insight into how users with elevated authorizations are interacting with your organization’s data)

Figure 4: SAP Cloud Identity Access Governance
For further reading and reference, please refer to the following blog:
- Enterprise Security Services – Cloud Identity Services
- SAP Cloud Identity Services
- A Single Sign-On Guide for SAP S/4HANA Cloud, Private Edition (RISE with SAP)
Secure CCKMS/BYOK Key Management:
SAP protects customer data in the cloud by encrypting it in transit and at rest using strong encryption algorithms. Following, Segregation of Duties (SoD) Principle, SAP also separates the responsibility for data access and encryption key management function, which minimizes the risk of unauthorized access to your data. For few cloud solutions such as SAP S/4HANA cloud, private edition, SAP S/4HANA cloud, public edition, customer can use BYOK/CCKMS leveraging SAP Data Custodian Key Management Service (KMS), which gives customers even more control over customer data security. This feature enables customers to exercise greater control by employing their own encryption keys, known as Bring Your Own Key (BYOK). With this capability, customers retain full authority over the entire lifecycle of their encryption keys, further enhancing data security.
For most of the cloud services, SAP manages keys in a secure environment to protect these encryption keys from unauthorized access, alteration, or theft. This can involve physical security (like secure data centers), technical measures (like secure key storage solutions or hardware security modules), and operational practices (like regular audits and restricted access protocols). SAP apply segregation of duties principle ensuring no single individual has control over all aspects of any critical cloud operation relating to secure key management.
Threat 2: Insecure Interfaces and API
Security Safeguards Available with SAP Cloud Services:
- In the cloud environment, every resource is essentially an API resource, making its protection paramount. SAP recognizes this and delivers to maintaining top-tier API (Application Programming Interface) security standards.
- These protocols not only ensure the secure flow of data between different applications, but they also emphasize the importance of protecting each API resource from potential threats.
- SAP provides comprehensive API management capabilities for building new applications, integration, and extension.
- The API Management capabilities incorporate built-in security concepts, including authentication, authorization, rate limiting, input validation control, spike control, protection against SQL injection, and data encryption. Regular security reviews are also conducted. As a result, these API resources are thoroughly protected against security vulnerabilities, both within the SAP ecosystem and externally

Figure 5: Securing API Management
The SAP cloud connector is critical software element that establishes a secure TLS1.2 mutual authentication tunnel between customer on-premises and the SAP Business Technology Platform. The SAP cloud Connector can be in DMZ or customer on-premises firewall, the cloud connector functions as a reverse invoke proxy, securely initiating a connection to your SAP BTP subaccount.
The cloud connector acts as a reverse invoke proxy, establishing a secure connection to the SAP BTP subaccount without altering firewall settings. It supports various protocols like HTTP and RFC for connecting to ABAP systems and links both SAP and non-SAP on-premises systems to SAP BTP. The SAP cloud connector also supports principal propagation, and it ensures user identity continuity between cloud and on-premises systems for comprehensive traceability.

Figure 6: Secure Integration with API Management
Threat 3: Misconfiguration and Inadequate Change Control
Security Safeguards Available with SAP Cloud Services:
According to the 2023 IBM Cost of Data Breach Report, 11% of cyberattacks are as a result of cloud misconfigurations. The report also noted that, on average, it takes 278 days to detect and address these misconfigurations and financial loss due to cloud misconfiguration.
- SAP has been using Hyperscaler providers such as AWS, Azure, and Google Cloud to run cloud applications.
- Security compliance is important for protecting SAP and its customers, and for meeting contractual, regulatory, and certification requirements. While different teams are responsible for implementing security policies, configurations and controls, the multi-cloud team is specifically tasked by SGS to conduct comprehensive compliance assessments of SAP's cloud accounts. This ongoing validation ensures that the systems in use are always compliant.
- The assessment process identifies potential security gaps, notifies teams, remediate any weakness identified in SAP cloud services. This helps to bring non-compliant systems into alignment with prescribed policies. This team has developed Multi-Cloud Security Compliance Scanning features that are directly mapped to SAP's Global Security policies for Hyperscaler.
- Cloud deployments are implemented using 'Secure Infrastructure as Code', based on SAP security validated and approved reference architectures.
- SAP conducts comprehensive scans of the entire environment regularly. The compliance scanning solution helps SAP report on the security compliance of all cloud accounts. It provides a centralized platform for line of businesses to scan their cloud accounts for compliance with SAP Global Security guidelines.

Figure 7: Preventative Controls in Cloud Accounts
For SAP cloud customers, SAP cloud application delivers ability to configure access to resources based on the principle of least privilege and Role Based Access Control (RBAC). Additionally, application audit logs are enabled for at the application level including read access logs, change document logs which are accessible by customers. SAP also provides the SAP Cloud ALM (Application Lifecycle Management) as part of its SAP Cloud Services package. Among other advantages, this allows users to monitor modifications made to ABAP-based systems set up in SAP Cloud ALM.
For additional reference, please refer to SAP document on “Seven Ways SAP Helps Secure Technology Stacks on Public Clouds” and also read SAP community blogs published by jay.thodenvanvelzen
- Preventative controls – using organizational policies to provide guardrails for SAP’s public cloud a...
- Public Cloud Infrastructure Compliance Scanning at SAP with Chef InSpec
- Multicloud Security Compliance Scanning: Compliance-as-Code and Operational Benefits
- Security Reporting and Analytics for Public Cloud Policy Compliance in SAP
Threat 4: Lack of Cloud Security Architecture and Strategy
Security Safeguards Available with SAP Cloud Services:
It is important to emphasize that every SAP cloud service adheres to standard reference architectures, embedding both secure by design and secure by default principles. These services are built on the tenets of defense-in-depth and zero-trust architectural principles. Whether data is in transit or at rest, it is safeguarded with strong cryptographic algorithms. Each customer environment is segregated and isolated from others, ensuring utmost data security. On the software front, SAP employs a stringent Secure Software Development Lifecycle (SSDLC) process. This encompasses features such as: Role-based access control (RBAC), Identity and access management (IAM), Application Security, Data Encryption, least privilege access, Security audit logs.
These features are supported by robust operational security, including Vulnerability advisory services, a cyber fusion center, Continuous logging and monitoring mechanisms.
SAP provides comprehensive contractual assurances for its cloud services. These guarantees our commitment to data privacy regulation through data processing agreements and a service-level agreement (SLA) for system availability and support policies. Security Architecture is supported by an extensive framework of risk assessments, threat modelling, and SSDLC. The diagram below provides an overview of multi-layer approach to cloud security.

Figure 8: Multi-Layer Security
Threat 5: Insecure Software Development
Security Safeguards Available with SAP Cloud Services:
SAP employs a multi-layer approach to ensure the security of its software. SAP follows a secure software development process, which incorporates security best practices and regular reviews to identify and address vulnerabilities during the development phase.
SAP secure software development involve use a range of security tools to meticulously scan their code for any vulnerabilities. SAP performs both static and dynamic application security testing (SAST and DAST). Before any new software is launched, it undergoes scrutiny by a SAP security review board to ensure its robustness. Additionally, a bug bounty program is instituted, offering rewards to security researchers who pinpoint vulnerabilities, thereby leveraging the global community's expertise in enhancing their security posture. Recognizing the importance of continual learning, SAP regularly conducts security training for its staff to keep them abreast of the latest threats and best practices. Moreover, in the event of any security discrepancies, SAP is equipped with a security incident response plan, ensuring swift and effective actions to mitigate potential risks.
The SAP Secure Software Development Lifecycle approach can be referenced in this link.
Threat 6: Unsecured 3rd Party Resources
Security Safeguards Available with SAP Cloud Services:
SAP ensures integrity, reliability, and security of products and services throughout their lifecycle and across the entire supply chain. This includes vendor selection, software development, deployment, and maintenance. SAP conducts comprehensive risk assessment third party services to manage risks at each stage. Before onboarding a new vendor or third-party service, SAP performs risk assessment and due-diligence and ensure they meet SAP's security standards. Contracts with suppliers typically include clauses that obligate them to maintain certain security standards and master data processing agreements. When 3rd party software is involved, SAP examines 3rd party SSDLC and performs security assessments including vulnerability and patch management. SAP ensures that 3rd party services are securely configured by default and remain secure through updates and changes.
SAP utilizes sub-processors in the delivery of its cloud services. For transparency, customers can subscribe to the sub-processors list and will be automatically notified of any changes. Customers require S-User ID to login and download the sub-processor list from SAP Trust Center
Threat 7: System Vulnerabilities
Security Safeguards Available with SAP Cloud Services:
SAP has a comprehensive vulnerability management program that includes vulnerability assessments, penetration testing, and patch management. Vulnerability assessments are used to identify vulnerabilities in SAP cloud services. Penetration testing is used to simulate an attack on SAP cloud services to see if any vulnerabilities can be exploited. Patch management is used to apply security patches to SAP cloud services to fix vulnerabilities. SAP frequently releases security patches and updates to address identified vulnerabilities. SAP cloud services apply these patches promptly to ensure their systems are protected.

Figure 9: Approach to Threat Management
Threat 8: Accidental Cloud Data Disclosure
Security Safeguards Available with SAP Cloud Services:
Accidental cloud data disclosure can result from misconfigurations, malicious insiders, human errors, or insufficient access controls. To address this threat, SAP has implemented robust controls at multiple levels.
- Data classification: SAP employs rigorous data classification, ensuring that assets are categorized and labelled based on their criticality. The level of security controls applied is dependent on this classification, ensuring that highly sensitive data has more stringent access and security controls.
- Encryption: SAP Security Policy requires all customer data to be encrypted using AES-256 encryption when at rest and is protected with TLS 1.2 during transit. This measure significantly reduces the risk of unauthorized data interception and access.
- Access control: All SAP cloud applications utilize role-based access control (RBAC), ensuring that only authorized personnel can access specific data pertinent to their role. Additionally, all cloud services incorporate identity and access management (IAM), ensuring that only authenticated and authorized users can access the respective resources.
- Security awareness training: All operational personnel go through role-specific security awareness training regularly.
- Backups: At the operational level, SAP performs regular backups and has defined retention periods for these backups.
- Vulnerability assessments and penetration testing: SAP regularly conducts vulnerability assessments and penetration testing. Remediations are carried out in a prioritized manner based on risk assessments.
Threat 9: Misconfiguration and Exploitation of Serverless and Container workloads
Security Safeguards Available with SAP Cloud Services:
Misconfigurations and exploitation of serverless and container workloads are significant threats in cloud environments. SAP recognizes these threats and has integrated multiple controls to mitigate them in its cloud services, including SAP Business Technology Platform (SAP BTP).
These controls include:
- Configuration management tools: SAP uses automated tools to enforce and validate configurations, ensuring that serverless and container workloads meet SAP security standards before deployment.
- Regular scanning and auditing: SAP cloud services regularly scan and audit both serverless functions and containers to detect vulnerabilities or misconfigurations.
- Immutable infrastructure: SAP maintains principle of immutable infrastructure where serverless and container workloads are never modified after they're deployed. Instead, any necessary changes are made in the development phase, and a new instance of the workload is deployed. This applies for patch management or new enhancement functions.
- Container security: SAP uses tools that provide full lifecycle security for containers, ensuring they're secure from the point of creation through runtime.
- Least privilege Access: SAP ensures that serverless functions and containers operate with the least privilege necessary, reducing the potential damage if an attacker compromises a function or container.
- Container runtime security: SAP monitors and protects the runtime environment of containers against suspicious activities.
- API Management controls: For serverless functions triggered by HTTP requests, SAP deploys API Management that provide an additional layer of security such as authentication, rate limiting, and input validation.
- Segmentation and zero-trust: SAP employs network segmentation to isolate container workloads from each other and from other parts of the environment. The zero-trust model ensures that every request is authenticated and authorized, regardless of its source.
- SAP Credential Store: SAP has tools and practices in place to securely handle secrets (like API keys, certificates, passwords, or database credentials)
- Patch management: SAP regularly updates and patches both the serverless platforms and the container orchestration tools to address known vulnerabilities.
- Monitoring and logging: SAP performs comprehensive logging and real-time monitoring of all serverless and container activities to detect and respond to any suspicious actions promptly.
- Education and training: SAP provide regular training sessions for developers and administrators about best practices in serverless and container security to prevent common mistakes and oversights.
These controls, combined with SAP's comprehensive approach to cloud security, provide robust protection against misconfigurations and potential exploitations of serverless and container workloads. However, it's also important for SAP's customers to be aware of and follow best practices when configuring and deploying their applications on the SAP Business Technology Platform.
Threat 10: Organized Crime/Hacker/APT
Security Safeguards Available with SAP Cloud Services:
Besides all the protective and detective security controls outlined in the previous section, the SAP Cyber Fusion Center also incorporates enhanced security measures such as analytics, defensive automation, cyber intelligence, and cloud security. SAP maintains both internal research teams and collaborates with external threat intelligence to comprehend emerging threats, taking proactive steps to address them. Cyber Fusion Center helps in assimilating and disseminating crucial threat insights.
SAP utilizes a Security Incident and Event Management platform. Within this system, SAP cloud services continuously collect and correlate platform logs, implement security use cases, and, where feasible, automate the remediation of security issues.
The SAP Cyber Fusion Center covers broadly following aspects for Cyber Threat Intelligence:
- Indicators of Compromise (IoCs): Identify and investigate potentially malicious activity, such as system malware signatures or suspicious IP addresses.
- Tactics, Techniques, and Procedures (TTPs): Understand an attacker's TTPs to anticipate their actions and develop defenses accordingly.
- Strategic Intelligence: Gain insights into the broader trends and motivations behind cyber threats.
- Operational Intelligence: Obtain details about specific cyber-attack campaigns, including who is being targeted and how.
- Source Attribution: Identify the potential actors or groups behind a cyber-attack to help predict their objectives and methods.
- Improved Defense: Use accurate and timely threat intelligence to enhance proactive and reactive defense mechanisms.
- Risk Management: Assess and prioritize risks to make informed decisions about where to allocate resources.

Figure 10: SAP Cyber Fusion Center Capabilities
SAP Enterprise Threat Detection Cloud Edition: SAP has launched SAP Enterprise Threat Detection which is a cloud based (SaaS) SIEM application. This helps customer detect, analyse, and respond to cyberattacks on customer SAP systems. This is offered as cloud based managed service, where SAP manages all the underlying infrastructure and application. SAP takes the responsibility for the day-to-day operations of the SAP ETD platform. SAP's monitoring agents work around the clock, leveraging the application to identify and dissect security incidents 24/7. The application collects and analyses log data from customer's SAP systems to detect potential attacks. Customer can have access to security logs and real-time security dashboards and receive alerts in real time so customer can respond to security events swiftly.
Threat 11: Cloud Storage Data Exfiltration
Security Safeguards Available with SAP Cloud Services:
Data exfiltration is a threat that leads to the unauthorized transfer or retrieval of data from cloud storage environments. To mitigate against this threat, SAP maintains several security controls that are implemented as part of security by default and secure by design.
Data encryption:
- Encryption of data in transit and data at rest in the cloud.
- Use of industry-standard encryption algorithms and key management practices.
- Encryption of data at the application layer, the network layer, and the storage layer.
Identity and access management (IAM):
- Strong authentication mechanisms, such as multi-factor authentication (MFA).
- Role-based access control (RBAC) to restrict access to data based on user roles.
- Regular reviews user access permissions to ensure that they are up to date.
Activity monitoring and logging:
- Logs all access to data in the cloud.
- Monitors all logs for suspicious activity.
- Application Security Audit Logs.
Endpoint security:
- Endpoint detection and response (EDR) solutions to monitor for potential exfiltration activities on all endpoints.
- Antivirus and anti-malware solutions to protect endpoints.
Multi-layer defense:
- Defense-in-depth and Zero Trust approach to security.
- Multiple security controls for protection, detection and automatic remediations.
Security awareness training:
- SAP provides regular security awareness training to users.
- The training covers the risks of data exfiltration, phishing attacks, and best practices to prevent unauthorized data transfers.
Secure APIs:
- Secure APIs to access data in the cloud.
- The APIs are encrypted and authenticated.
- The APIs are monitored for suspicious activity.
Regular audits:
- SAP regularly audits cloud storage configurations and permissions.
- The audits ensure that the configurations and permissions are aligned with best practices.
Backup and versioning:
- SAP maintains data backups to restore data in the event of a data breach.
- The backups are encrypted and stored in a secure location.
Incident response plan:
- SAP has a robust incident response plan in place.
- The plan outlines how SAP will respond to a data breach, meeting contractual obligation as a Data processor.
- The plan includes steps to contain the breach, investigate the breach, and recover from the breach.
Third Party Security Risk Assessment:
- SAP performs comprehensive risk assessments of third-party IaaS providers.
- The risk assessments identify and mitigate the risks associated with using third-party IaaS providers.
Conclusion
This blog summarizes how SAP Cloud Services mitigate and maintain security controls to address top threats facing cloud computing. As enterprises navigate their digital transformation journey to cloud computing, the security and integrity of data and applications remain paramount. For businesses leveraging SAP Cloud Services or considering a move to the cloud, it is essential to understand the associated threats and safeguards. As cyber threats grow in sophistication, SAP's defense strategies also evolve in tandem. Ultimately, organizations using cloud services must instil a culture of security awareness, invest in ongoing training, and stay up to date on the latest cybersecurity trends to protect themselves from cyber threats.
While technology provides the tools to secure our assets, it is the human element—vigilance, knowledge, and proactive approach to security that ultimately determines the strength of our cyber defense. In conclusion, cloud computing can match or even surpass the security standards of traditional computing environments when organizations implement proactive security governance, risk assessment, and meticulous attention to security measures. This will unlock the cloud's vast potential to its fullest extent.
Disclaimer
© 2023 SAP SE or an SAP affiliate company. All rights reserved. See Legal Notice on www.sap.com/legal-notice for use terms, disclaimers, disclosures, or restrictions related to SAP Materials for general audiences.
Labels:
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
Business Trends
145 -
Business Trends
15 -
Event Information
35 -
Event Information
9 -
Expert Insights
8 -
Expert Insights
29 -
Life at SAP
48 -
Product Updates
521 -
Product Updates
63 -
Technology Updates
196 -
Technology Updates
10
Related Content
- Summer SAP Cloud Security Articles You May Have Missed in Financial Management Blogs by SAP
- Understanding SAP Security in Financial Management Blogs by Members
- GRC Tuesdays: Governance, Risk, and Compliance as an Enabler to a Successful IPO in Financial Management Blogs by SAP
- Planning comes home in Financial Management Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |