
- SAP Community
- Products and Technology
- Financial Management
- Financial Management Blogs by SAP
- GRC Tuesdays: What really is SAP Governance, Risk,...
Financial Management Blogs by SAP
Get financial management insights from blog posts by SAP experts. Find and share tips on how to increase efficiency, reduce risk, and optimize working capital.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Product and Topic Expert
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
05-18-2021
6:50 AM
Data privacy and data protection regulations, and best practices, require organizations to implement both technical and organisational measures appropriate to the nature of data access and processing, and the associated risks of course.
Organizations need to ensure there are appropriate processes in place to test the effectiveness of both technical controls and policies, but also to undertake any required improvements.
This fourth blog on the “What is really SAP Governance, Risk, and Compliance (GRC)?” series will focus on the cybersecurity, data protection and privacy aspects of the portfolio.
Managing data protection and privacy
With that in mind, SAP solutions for Cybersecurity and Data Protection help customers:
- Develop, maintain and implement policies and regulatory compliance, with auditable evidence of gaps and remediation
- Provide technical access, masking and logging controls, geopolitical fencing, and management of digital identities
- Protect system and landscape security, and perform early watches
- Perform risk analysis and records of processing activities, linked technical measures, and data protection events to document and manage the appropriate and legal response
- Implement security frameworks such as the one from the National Institute of Standards and Technology (NIST)

SAP Enterprise Threat Detection – Address cyber-threats with real-time intelligence
Features and functionalities: * Analyze and efficiently enrich and correlate logs for review * Evaluate for automated detection of attack patterns with real-time alerting * Investigate with forensic analysis and modeling of existing and new attack detection patterns and dashboards * Integrate to collect SAP and non-SAP log data |  |
SAP Privacy Governance – Manage and comply with evolving data privacy regulations
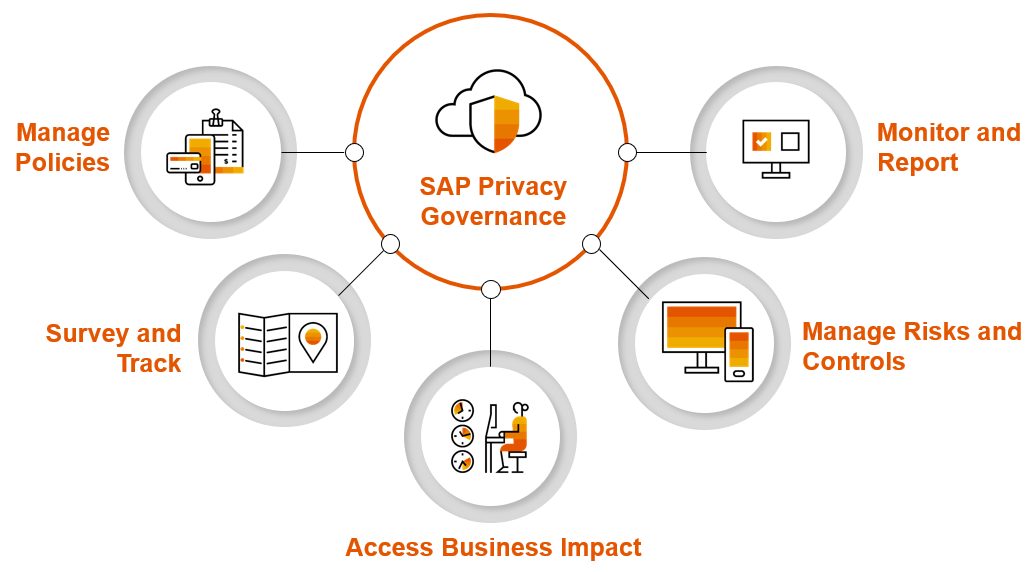 | Features and functionalities: * Manage policies by creating, disseminating, and acknowledging data protection and privacy (DPP) policies * Survey and track to gather and report on records of processing activities (RoPA) * Access business impact by performing data privacy (DPIA) and cybersecurity business impact analysis * Manage risks and controls to identify and audit related risks and mitigating controls * Monitor and report on status and details via a unified cockpit |
SAP Data Custodian – Gain greater visibility and control of your data in the public Cloud
Features and functionalities: * Data transparency to monitor and report on data access, storage, movement, processing, and location in the public Cloud * Data control to create and enforce public Cloud data access, location, movement, and processing policies |  |
SAP UI Logging – Data access transparency and analysis
 | Features and functionalities: * Log data access for coherent log of users’ input and system output on the user interface level, enriched with meta information for analysis * Gain insight to understand how and which data is accessed, and set up alerts in case of access to critical or sensitive data * Investigate by receiving alerts to specific, questionable activities, and enabling deep-dive into the log file to identify and prove improper data access * Report to draw on comprehensive access data to report internally and externally * Integrate with SAP UI Masking for better data protection, and with SAP Enterprise Threat Detection for advanced and automated analysis of access |
SAP UI Masking – Protect sensitive information in the user interface layer
Features and functionalities: * Secure access by determining sensitive fields and applying protective actions in runtime based on users’ authorizations * Automate authorization by determining users’ special authorization in runtime, based on static roles or dynamic attribute-role settings * Gain insights to understand who tries and who succeeds in accessing sensitive data, and whether to refine the solution setup * Integrate by leveraging SAP UI Logging and SAP Enterprise Threat Detection to identify potential data abuse |  |
I hope this helps in introducing the cybersecurity, data protection, and privacy offering from SAP’s Governance, Risk, and Compliance portfolio.
As a reminder, you can find all the other blogs in this series listed below:
- GRC Tuesdays – What really is SAP Governance, Risk, and Compliance (GRC)?
- GRC Tuesdays – What really is SAP Governance, Risk, and Compliance (GRC)? – Focus on the Enterprise ... (released on 20/04/2021)
- GRC Tuesdays – What really is SAP Governance, Risk, and Compliance (GRC)? – Focus on the Identity an... (released on 04/05/2021)
- GRC Tuesdays – What really is SAP Governance, Risk, and Compliance (GRC)? – Focus on the Internation... (released on 01/06/2021)
I look forward to reading your thoughts and comments either on this blog or on Twitter @TFrenehard
- SAP Managed Tags:
- Governance, Risk, Compliance (GRC), and Cybersecurity
Labels:
2 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
Business Trends
145 -
Business Trends
17 -
Event Information
35 -
Event Information
9 -
Expert Insights
8 -
Expert Insights
31 -
Life at SAP
48 -
Product Updates
521 -
Product Updates
69 -
Technology Updates
196 -
Technology Updates
11
Related Content
- GRC Tuesdays: Automate compliance with anti-forced labour regulations in Financial Management Blogs by SAP
- GRC Tuesdays: Takeaways from the 2024 Internal Controls, Compliance and Risk Management Conference in Financial Management Blogs by SAP
- GRC Tuesdays: Insights into Cybersecurity Supply Chain Risk Management: Why, What and How in Financial Management Blogs by SAP
- GRC Tuesdays: What’s New in SAP solutions for Three Lines, Q3 2023 to Q1 2024 in Financial Management Blogs by SAP
- Security by Default vs Security by Design in Financial Management Blogs by Members
Top kudoed authors
| User | Count |
|---|---|
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
