
- SAP Community
- Products and Technology
- Additional Blogs by Members
- Creating and Using Checkgroups
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Hi,
In this blog i am going to describe about the checkgroups.This plays a crucial role in giving the user the authority to enable or disable the breakpoints in the program.Log the entries if he wants or set abort so that the program gets aborted if someone tries to execute it without the condition being fulfilled.
The transaction that takes care of these checkpoints and the place where they are maintained is SAAB.These checks are transportable and can be transported. The Checkpoints now can be created for break-points and checkpoints and the two statements for this are :-
1. Assertions
2. Break-points
The one which actually does not checks the errors but is used to log the data that u want is LOG-POINT.
To start with step by step explanation of the checkpoints we start first with the Assertions.
Assertions syntax as per the SAP Library that is to be used in the coding is as below…
ASSERT[ [ID group [SUBKEY subkey] ]
[FIELDS field1 field2 table1 table2...]
CONDITION] log_exp.
Assertions are used as a high quality means of problem determination in the case of code failure. .Assertions are invoked at run time. They can be made active or inactive. Assertions can be left in codewhen promoted to production with no impact to the code. They are only invoked if the checkpoint groupis activated.The checkpoint groups can be activated through the transaction SAAB and that is referred by ID in the programs with assert statements.
This is the transaction below SAAB where in the checkpoint group we can create the group ID.
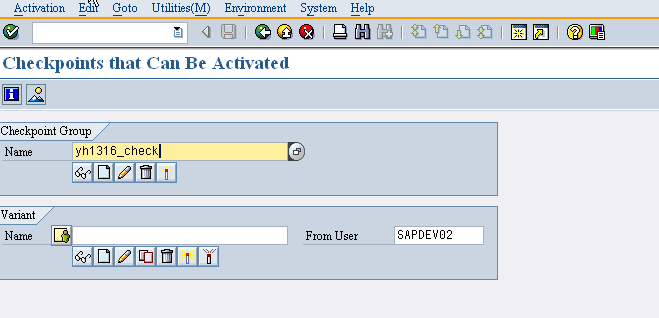
Clicking on the create button below the Name we get to the below screen where you can check the actions that you want for the three of them shown below..

Now the checkgroup activation can be done with three levels
1. Personal Activation
2. User Level activation
3. Server Level Activation.
In the personal level activation that checkgroup will be active for the current user only and for the User level Activation the Checkgroup will be active for that user that has been defined and same is for the Server.The User when clicked there you can define the Specific users for it as this…
The breakpoints can be made active or inactive. Inactive then that particular statement will be ignored and if break then in the program , wherever the statement occurs the program gets into debugging.
The Statement as per the SAP Library that goes with this in the Program is as below...
BREAK-POINT { [ID groupID]
| [log text] }.
Ex. BREAK-POINT ID YH_check.
Without the addition ID, the breakpoint is always active. The log text is the text which you can specify for the system log which is seen in the logs getting created.
During background processing the program execution is not interrupted. If the program reaches a breakpoint, the entry "Breakpoint reached" is written to the system protocol under which the program name and the location of the breakpoint in the program are recorded. An inactive breakpoint is ignored.
In HTTP sessions like the BSP applications and Web Dynpros the system only stops at an active breakpoint in the Code and goes to the ABAP Debugger if external debugging is switched on for the particular .If the external debugging is not switched on then the breakpoint behave the same as it would have been behaving in the background mode.
Coming again back to assertions,
There are 4 ways the assertion can be used:-
- Inactive (default): statement is ignored
- Log: occurrence is logged
- Abort: program terminates with runtime error ASSERTION_FAILED
The below two options come with a pop-up having options as:-
- Break/Log: program is interrupted and starts the debugger / like LOG mode in background, batch etc.
- Break/Abort: program is interrupted and starts the debugger / like ABORT mode in background, batch etc.
The below two options come as this...
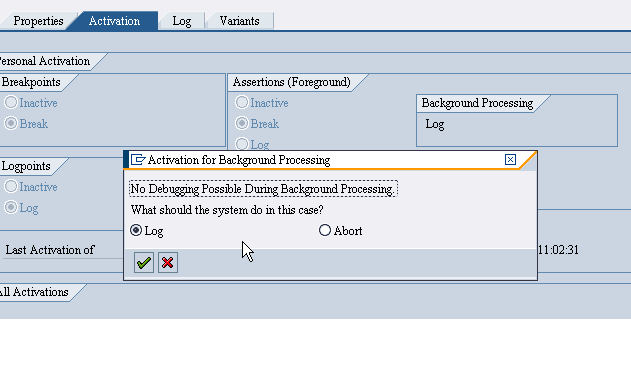
Assertion RULES:
- Exception handling should always be used to trap and handle failures. DO NOT use an assertion in the place of exceptions.
- Assertions should only be used on custom code rather than on standard codes.
- When an assertion is invoked, it should create a log entry unless and until there is a compelling reason to terminate with a run time error.
Here is a sample program where the LOG-Points and ASSERTIONS are used.
REPORT yh1316_test_checkgrp.
. .
** Parameters Declarations
PARAMETERS:
p_carrid LIKE sflight-carrid.
*Types Declarations of sflight
TYPES : BEGIN OF type_s_sflight,
carrid TYPE sflight-carrid,
connid TYPE sflight-connid,
fldate TYPE sflight-fldate,
price TYPE sflight-price,
max TYPE i,
END OF type_s_sflight
*Field String Declarations for sflight
DATA: fs_sflight TYPE type_s_sflight.
*Internal table for Sflight Data
DATA : t_sflight LIKE
STANDARD
TABLE OF fs_sflight.
DATA yh1316_subkey TYPE char200.
IF p_carrid IS INITIAL.
SELECT carrid
connid
fldate
price
FROM sflight
INTO fs_sflight.
WRITE: / fs_sflight-carrid,
fs_sflight-connid,
fs_sflight-fldate,
fs_sflight-price.
APPEND fs_sflight TO t_sflight.
ASSERT ID yh1316_check SUBKEY 'YH1316_parameter_if_initial'
FIELDS p_carrid
t_sflight
fs_sflight-carrid
fs_sflight-connid
fs_sflight-fldate
fs_sflight-price
condition p_carrid eq 'LH' .
ENDSELECT.
ASSERT ID yh1316_check SUBKEY 'YH1316_1'
FIELDS p_carrid
t_sflight
CONDITION p_carrid EQ 'LH' .
EXIT.
ELSE.
ASSERT ID yh1316_check SUBKEY 'YH1316_2'
FIELDS p_carrid
t_sflight
CONDITION p_carrid EQ 'LH'.
SELECT carrid connid fldate MAX( price ) AS max
INTO CORRESPONDING FIELDS OF fs_sflight
FROM sflight
WHERE carrid EQ p_carrid
GROUP BY carrid connid fldate
ORDER BY carrid max DESCENDING.
IF sy-dbcnt < 4.
APPEND fs_sflight TO t_sflight.
LOG-POINT ID yh1316_check SUBKEY 'LOG_POINT'
FIELDS p_carrid
t_sflight
fs_sflight-connid
fs_sflight-fldate
fs_sflight-max.
WRITE: / fs_sflight-carrid, fs_sflight-connid, fs_sflight-fldate,
fs_sflight-max.
ENDIF.
ENDSELECT.
ENDIF.
A variant is created for the Particular Checkgroup created. Variant can be created as a Local as well as at a user level. Here it is created at the User Level.
Click on create and enter the following entries.
 There are four kind of object type for which a variant can be created as
There are four kind of object type for which a variant can be created as
- Check Group
- Program
- Class
- Function Group
And for particular Object type the Different options can be given for Breakpoint, Logpoint and Assert. The Options for them are same as stated before in the Personal Activation screen for check group.
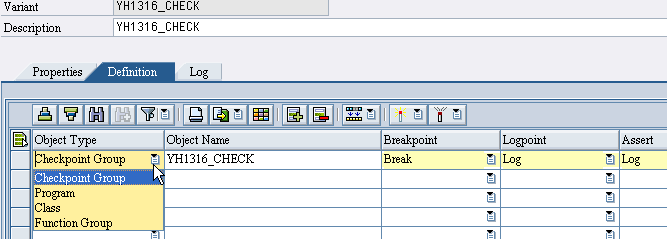
Now save the variant and then go back to the checkgroup for which we have created the variant. Don't forget to activate the variant.
As above it is seen the Local variant is visible in the Variants tab the same way we can create a Global variant also.
Now run the Program.
If the assertion condition is violated the listed logs are created for the assertion as we have selected the log for assertion in the SAAB transaction in the Check Group.
The log will also be created for the LOG-POINT statement and the SUBKEY there defines the Key to distinguish that the log has been created for which Assertion and checkpoint.
In the Log the data is segregated according to the two Hierarchies:-
- Gropu/Subkey/Program/Procedure
- Group/Program/Procedure/Subkey
The log seen is like this.
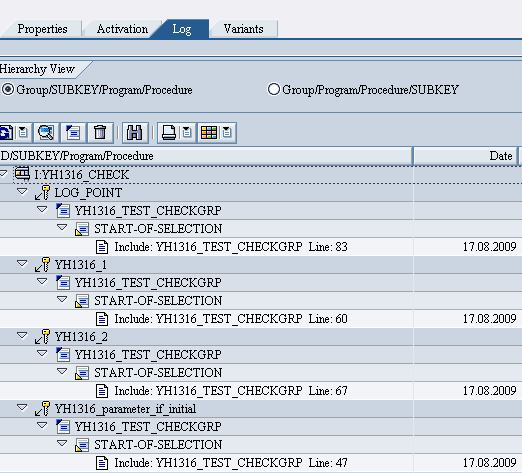
Double clicking on the Line where the Include line number is seen we can see the description of the log as below. The number of times the programs have been in run can also be seen in the Frequency with the last run time and date.
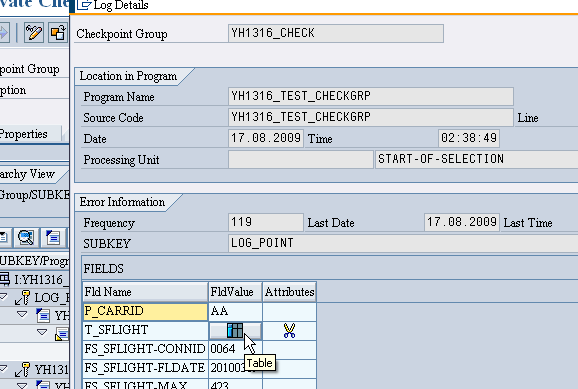
As we have logged the table entries also double clicking on the table we can see the table entries too.

We can even check the check groups in the new debugger with the watchpoints and Breakpoints. This is how the Logs get created and how the Checkpoints works in the Efficient way to check the Codes.
Richa.
- How to create a Sales Order in the new fiori application with configurable materials ? in Enterprise Resource Planning Q&A
- Create destination service in the global account. in Technology Q&A
- Unable to create E-Way Bill for Sub Contracting Challan in S/4Hana Public Cloud in Enterprise Resource Planning Q&A
- API Management: Unlocking OAuth Strategies in Technology Blogs by SAP
- How to create Activity and Return Activitycode after add Success use DIAPI Using SDK ? in Enterprise Resource Planning Q&A