
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- SAP Cloud Integration – OAuth2 SAML Bearer/X.509 C...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Introduction
SAP Cloud Integration version 3.36.**/5.20.**/6.12.** comes with enhancement on SuccessFactors OData V2 outbound connector with OAuth2 SAML Bearer/X.509 Certificate authentication.
Note: The forecasted SAP Cloud Integration customer tenant updates/availability of this version is planned on or after 3rd/10th April 2021 as per the phased tenant update procedures, which may be subjected to change.
OAuth2 SAML Bearer /X.509 Certificate authentication is not new to SuccessFactors OData V2 outbound connector in SAP Cloud Integration, because it has been used in the context of principal propagation as described in the blog https://blogs.sap.com/2018/07/30/sap-cloud-platform-integration-principal-propagation-with-successfa... , but here in this blog, the support of OAuth2 SAML Bearer in the context of a dedicated/technical user has been described to support planned retirement of Basic Authentication in SAP SuccessFactors system as per the plan https://help.sap.com/viewer/62b1a0b4b34c4c36869e21c8db128e49/latest/en-US/a2f874d8f3194cc5adba237d00....
Setup
To consume this new feature, below steps have to be followed.
Step 1: Creating a key pair in SAP Cloud Integration (or you can also upload one if you have)
Step 2: Registering an OAuth2 client in SAP SuccessFactors System
Step 3: Deploying OAuth2 SAML Bearer credentials in SAP Cloud Integration
Step 4: Designing Integration Flow with SuccessFactors OData V2 outbound connector
Step 1: Creating a Key Pair in SAP Cloud Integration
In this example, a new key pair creation is considered, if you have a valid key pair, you can re-use it by uploading the same.
In SAP Cloud Integration Web UI Monitoring section, click on Keystore tile

Keystore UI Tile
Click on the Create -> Key Pair

Create Key Pair
Provide the relevant details. The value for Common Name (CN) should be the user name exists in your SAP SuccessFactors instance who has the access/authority to invoke the SuccessFactors API through OAuth2 token.

Key Pair details. CN value should be of a user at SAP SuccessFactors system
Click on Create button once finished providing details. Copy (or remember) the Alias name for further use. In this example, the alias is "samplekeypair1".
After creation, download the certificate part of it. The public key of this file will be used while registering the OAuth2 client in SAP SuccessFactors system.

Download Certificate
Step 2: Registering an OAuth2 client in SAP SuccessFactors System
Login to your SAP SuccessFactors system as administrator and then create a new OAuth2 Client in ‘Manage OAuth2 Client Applications” section. .

Click on Register Client Application
Open the certificate file you have downloaded in Step 1 in text editor.

Certificate File in text editor
In creating OAuth2 Client Application, provide relevant details, copy the certificate part (the content between -----BEGIN CERTIFICATE----- and -----END CERTIFICATE-----) and add/paste that into X.509 Certificate place. Click on Register, and get hold of API Key (which will be treated as Client Key when deploying OAuth2 SAML Bearer credentials in SAP Cloud Integration)

Click on Register button

Click on View button of your OAuth2 client application

Copy the API Key value, which will be treated as Client Key while deploying OAuth2 SAML Bearer credentials in SAP Cloud Integration
Step 3: Deploying OAuth2 SAML Bearer credentials
In the Monitoring Section of SAP Cloud Integration, click on the 'Security Material' UI tile, and then click on Create -> OAuth2 SAML Bearer Assertion. Provide the relevant details, and select User ID as Key Pair Common Name (CN) and provide the alias of Key Pair created in step 1, in this case, samplekeypair1.

Monitoring Security Material UI tile

Create - OAuth2 SAML Bearer Assertion credentials
While creating the credentials,
Name, allowed name of your choice, 'sampleOAuth2Alias' in this example
Client Key will be the API Key received after registering the OAuth2 client in SAP SuccessFactors system.
Token Service URL is the URL of SAP SuccessFactors OAuth2 token server.
User ID select Key Pair Common Name(CN) in the drop down control.

Select User ID as Key Pair Common Name (CN)

Provide the Key Pair Alias, and click on Deploy
Step 4: Designing Integration Flow
In SAP Cloud Integration, create an integration flow with SuccessFactors OData V2 outbound adapter and select the authentication as OAuth2 SAML Bearer, and provide the credential alias created in step 3, in this example, it is 'sampleOAuth2Alias'

Note: A side remark; the Accept-Encoding GZIP configuration has been provided for the newer SuccessFactors OData V2 connector version 1.18, which is aimed to reduce the time taken between SAP Cloud Integration and SAP SuccessFactors endpoint HTTP communication through zip stream over the network.

Querying User API/Entity as an example under Processing tab
In this Integration Flow example, I am using HTTP sender adapter, which will provide an HTTP endpoint after deployment. After invoking that HTTP endpoint, the integration flow message executes, the OAuth2 token is fetched by the SAP SuccessFactors OData V2 outbound connector and further invokes the SAP SuccessFactors system endpoint to fetch all the User records with OAuth2 SAML Bearer authentication.
The token caching is also handled as well.
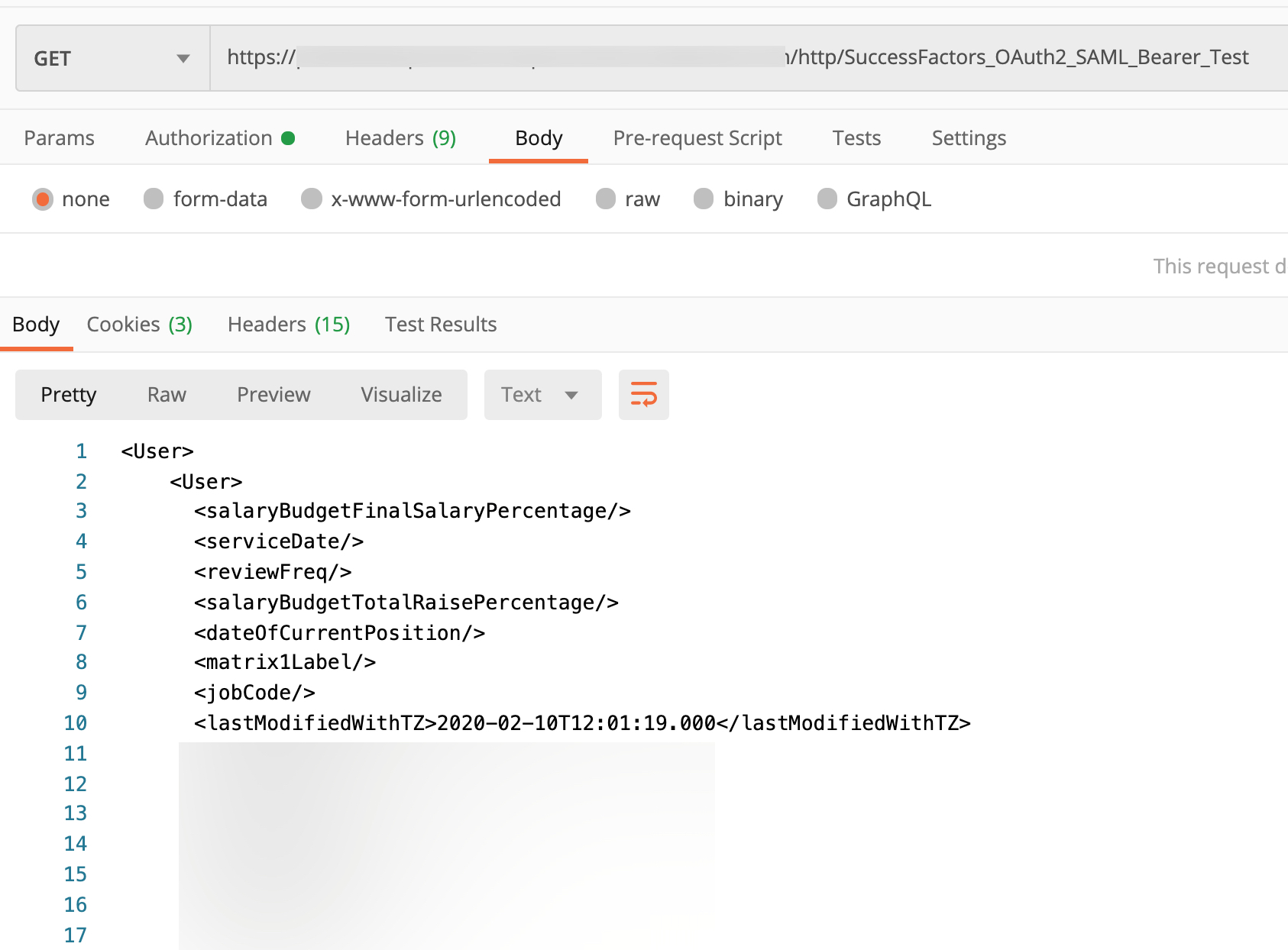
Result of invoking HTTP endpiont of Integration Flow in this example
Next Steps
As you might have observed, currently, the SuccessFactors OData V2 outbound connector has got the OAuth2 SAML Bearer assertion for a dedicated/technical user.
As next steps, the same support for
- SuccessFactors SOAP outbound connector : Update : The support for OAuth2 SAML Bearer/x.509 authentication has been enabled for SuccessFactors SOAP outbound connector with SAP Cloud Integration version 5.23.**/6.15.**. You can refer the blog post https://blogs.sap.com/2021/07/29/how-to-use-oauth2-saml-bearer-assertion-in-sap-cloud-platform-integ... for more details.
- SuccessFactors OData V2 Query Wizard and SuccessFactors SOAP Query Wizard : Update : The support for OAuth2 SAML Bearer/x.509 authentication has been enabled for SuccessFactors OData V2 Query Wizard and SuccessFactors SOAP Query Wizard with SAP Cloud Integration version 5.24.**/6.16.**.
will be provided in next increments, for which the blog shall be updated.
Summary
The support for OAuth2 SAML Bearer assertion/X.509 Certificate authentication has now been enabled for SuccessFactors OData V2 for a dedicated/technical user to support the planned retirement activities of Basic Authentication in SAP SuccessFactors. Now, the OAuth2 SAML Bearer can be used in the context of principal propagation as well as in the context of a dedicated/technical user.
- SAP Managed Tags:
- SAP Integration Suite,
- Cloud Integration
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
93 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
66 -
Expert
1 -
Expert Insights
177 -
Expert Insights
299 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
345 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,872 -
Technology Updates
427 -
Workload Fluctuations
1
- SAP LICENSE RENEWAL FROM BASIS END #ATR in Technology Blogs by Members
- Switch off 'SSL certificate verification' setting in BPA in Technology Q&A
- Consuming SAP with SAP Build Apps - Mobile Apps for iOS and Android in Technology Blogs by SAP
- Demystifying the Common Super Domain for SAP Mobile Start in Technology Blogs by SAP
- How to use AI services to translate Picklists in SAP SuccessFactors - An example in Technology Blogs by SAP
| User | Count |
|---|---|
| 42 | |
| 25 | |
| 17 | |
| 14 | |
| 9 | |
| 7 | |
| 6 | |
| 6 | |
| 6 | |
| 6 |