- SAP Community
- Groups
- Interest Groups
- Security and Compliance
- Discussions
- Safeguarding Success: Navigating SAP Governance & ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Safeguarding Success: Navigating SAP Governance & Security with SAP IAG, Process Control & BIS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
a month ago
Safeguarding Success: Navigating SAP Governance & Security with SAP IAG, Process Control & BIS
Introduction:
This blog is dedicated to the intricate world of governance, security, and controls within SAP environments. Delve into the realm where SAP Identity Access Governance (IAG), process control, and SAP Business Integrity Screening converge to fortify organizational integrity. Join us as we explore the critical intersection of technology and governance, ensuring compliance, risk mitigation, and operational excellence. Uncover insights, strategies, and best practices to navigate the complexities of SAP systems with precision and confidence.
SAP Cloud Identity Access Governance (IAG)
SAP Cloud Identity Access Governance (IAG) will enable organizations to achieve robust access control and governance across on-premises and cloud applications. Built on SAP Business Technology Platform (BTP) and SAP's proprietary HANA database, IAG integrates seamlessly with SAP Identity Authentication Service (IAS) and Identity Provisioning Service (IPS), offering a multi-tenant environment.
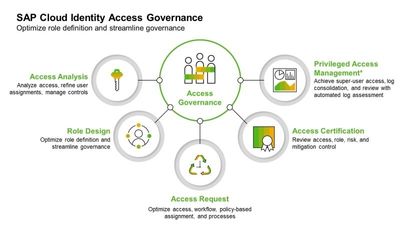
The various facets of SAP Cloud IAG in scope are depicted below.
Scope:
Services:
The below services have been considered in-scope are:
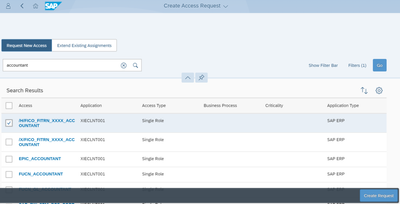
- Access Request Service: A self-service access request form for user and role provisioning into cloud applications and the S/4Hana application. This will include workflow-driven access provisioning mechanisms, empowering users while maintaining control. The access request service will be configured to utilize workflow management, provisioning, and business logic. SAP Cloud IAG provides compliant provisioning of user access to the SAP applications mentioned in scope.
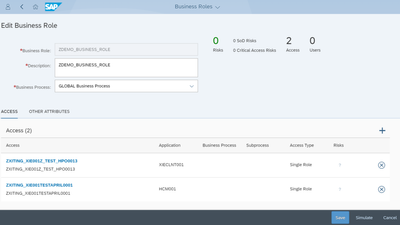
- Role Design Service: Design of roles with a bottom-up approach, refining and defining roles. Machine learning (ML) algorithms to optimize access roles will also be used. Risk metrics will be defined, and usage trends within a business role will be used to evaluate the impact it has on end-users (so that role adjustments can be made).
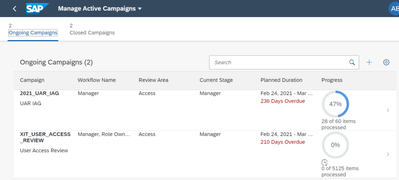
- Access Certification Service: Audits and certification of roles assigned across multiple cloud solutions to ensure compliance with security policies and refine access as needed. review user access, roles, risks, and mitigation controls, and periodic user access reviews (UAR) and campaigns.
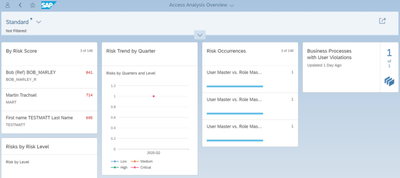
- Access Analysis Service: Analysis of access risks across applications and refinement or remediation of access to meet audit requirements, including SAP S/4HANA, SAP Fiori, SAP cloud solutions, SAP Ariba, and SAP Fieldglass. Continuous access analysis uses real-time insights to support access compliance management.
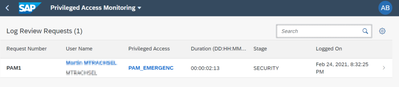
- Privileged Access Management Service: Setup to monitor access to sensitive and critical transactions by users with elevated authorizations. Provision of super-user access, log consolidation, and review of logs with monitoring, reporting, and auditing.
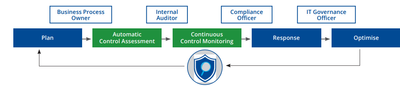
SAP Process Control
SAP Process Control, delivered as an add-on to SAP NetWeaver AS for ABAP 7.52, will enable to
- Document their control environments
- Test and assess controls
- Track issues for remediation
- Certify and report on the state and quality of process controls
- Manage policies
- Perform continuous monitoring of controls using a combination of data forms, automated workflows, certification, and interactive reports
The 2 facets of process control include:
Compliance Management: Manage and monitor their internal control environment to proactively remediate any identified issues, and then certify and report on the overall state of the corresponding compliance activities.
Policy Management: Manage the overall policy lifecycle, including the distribution and attestation of policies by target groups.
SAP Business Integrity Screening
SAP Business Integrity Screening is being proposed for detecting, investigating, and analysing irregularities in data, as well as preventing fraud.
The steps to be performed during implementation include
Design:
- Determine Screening Lists
- Analyze patterns
- Define detection rules and models
Setup:
- Define detection strategies based on fine granular criteria
- Define screening strategies for business partners
- Use real time simulations and calibration of strategies
Detect:
- Execute mass and real-time detection runs
- Stop anomalies or irregular transactions
Investigate:
- Manage alert workload with evaluation & qualification
- Remediation of issues
Analyze:
- Monitor key performance indicators
- Management reporting
By virtue of being on S/4 HANA, BIS handles large volumes of payments, processing through real-time simulations. SAP BIS also integrates with different process areas like master data management, invoice processing, payment execution (payment runs),
BIS has a highly flexible detection and screening strategy for business partners where new rules can be added and it can make composite rule scenarios, resulting in an overall risk score being awarded.
For example, a weighted score may be determined based on individual Rules like:
- Payment value banding.
- Consecutive payments to the same beneficiary.
- Beneficiary address in an ‘at-risk’ country.
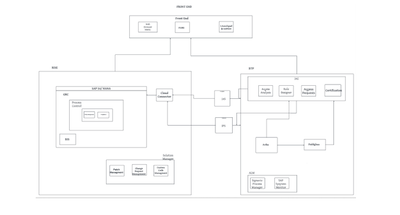
Architecture
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
3 weeks ago
Hello
why in this scenario you didn't use SAP access Control instead of IAG? there could be an option to have single system with SAP GRC AC+PC+BIS. It is helpful to understand the reason for different scenario selection 🙂
Thanks
Samir