
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- User Attribute Mapping in BI4 - in depth
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
A new feature available with BI 4.0 Feature Pack 3 is the ability to import & manage extended user attributes. This is accessible in the CMC:
These extended attributes can be used for filtering and applying security at the universe (.unx) level.
For example if your LDAP server has an attribute called “Country”, you can make use of those values, and filter content in your report based on the value of the Country attribute for any given user, or outright set security so that someone from Canada cannot read content from Germany, and vice versa.
The filtering & security will be set up using the Information Design tool.
Let’s walk through a sample scenario here.
Let’s say I have some users, one residing in the United States, the other in France.
While I can represent this membership through user groups, although in some cases this extended information such as region, country, and department can also be stored in your Active Directory or LDAP server. You may not always have groups configured to represent these extended attributes.
With BI4 Feature Pack 3, you can now reference and consume these extended attributes from your external identity store such as SAP, AD, LDAP, as well as manage these directly for the BI ‘enterprise’ users.
To do so, you must first configure your authentication plugin in and enable the attribute binding options:
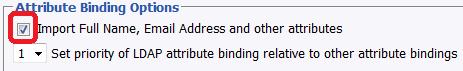
Previously, this option would allow you to import the full name and email address, and we have now extended this to do much more.
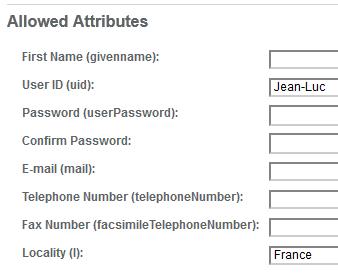
Once you have enabled this setting, you will need to know the attribute names that you wish to query. In this LDAP example which is a screenshot from my LDAP server, I have an attribute called “Locality” which will be used for country.
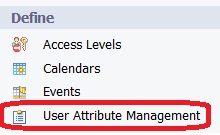
To map this value to your users, click on the User Attribute Management link in the CMC
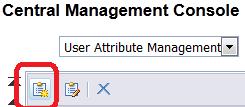
Click on the “Add new Custom Mapped Attribute button”
In the screen you are presented, select the source of the attribute, in our case it will be LDAP:
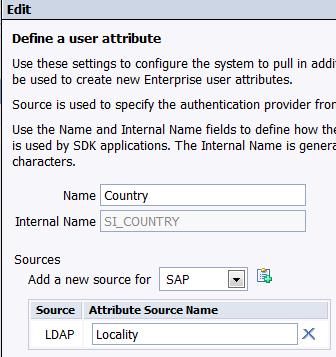
A quick explanation of the values.
The Name is what will be used in all the UI where you interact with this in the BI tools.
The Internal name is referenced by the internal SDK, and the Information Design Tool.
The Attribute Source name is the attribute value from our LDAP server mentioned earlier.
Once this is done, you can run a user update in the LDAP authentication plugin, or logon as one of the LDAP users to validate that your users have been updated with the appropriate values. In order for the various attribute sources to appear, you must have the authentication plugin correctly configured and enabled. To validate, look at a user’s properties page.

You can now see that the name we defined “Country” has the value from the LDAP server which is stored under “Locality”.
Great! So now what?!
Let’s say I want Jean-Luc’s reports to only contain data for his region, France.
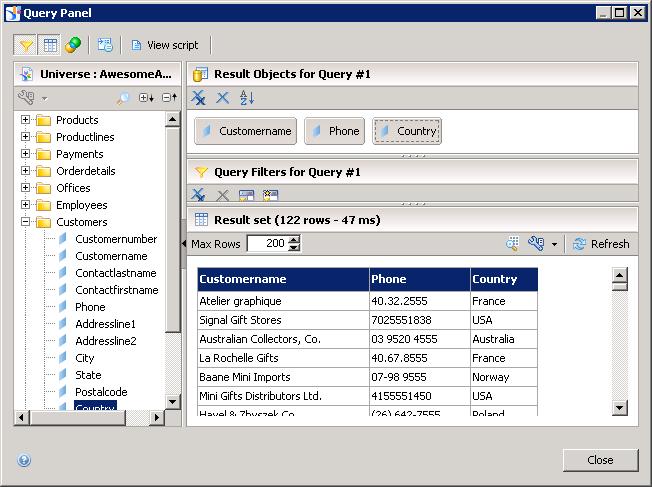
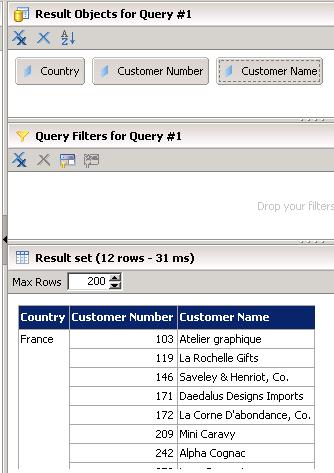
If I first logon to Information Design Tool with Jean-Luc as the user account and run a query on my universe with no filters, I’ll get everything returned:
However applying a filter on country will limit my results to the value of the user’s attribute:
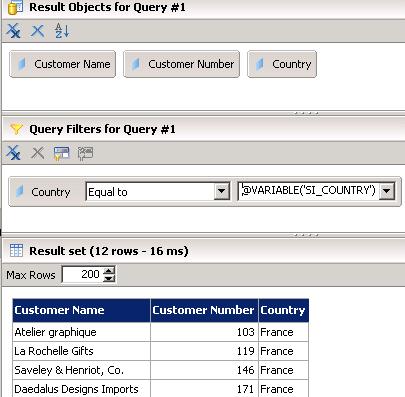
The value we input here is @VARIABLE(‘SI_COUNTRY’) to make use of the custom mapped attributes. Recall that this is the internal name that was set when we created the attribute mapping in the CMC.
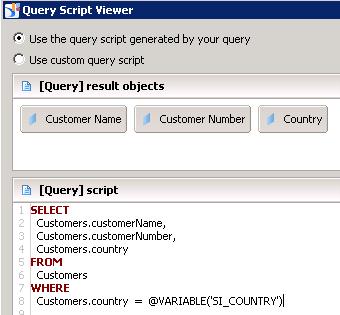
If we view the details of our resulting query to see what happens behind the scenes, we’ll get the following:
Where this can become even more useful beyond filtering is during in applying security. Suppose you don’t want users to view data outside their region, as defined by the “Country” attribute in our example.
In the security builder of the Information Design Tool, Insert a Data Security Profile:
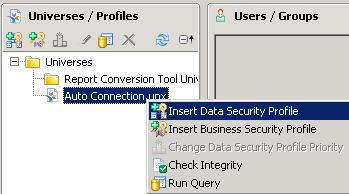
Let’s now add a Rows security restriction on the Customers table

Make sure you assign this security to an appropriate group, you can do this for ‘Everyone’, and save your universe.
Now if we logon again with our Jean-Luc user, whose attribute value to ‘Country’ is “France”, our query will always be limited to this value only, and I will not be able to access data for other countries:
If Jean-Luc relocates to the USA, assuming the underlying attribute is updated, their security access will automatically get updated as well, and their data will be filtered to “Germany” only.
While the feature is primarily intended for taking advantage of information in your existing Identity Provider like your LDAP directory store or your Active Directory, you can set this on Enterprise users, and you can also use the SDK to access & set these values.
Failover:
You will notice that you can set multiple attribute sources for any single custom attribute, for example you can configure both your SAP authentication plugin and your AD plugin to pull in the value of Country. The priority of each source is defined when configuring authentication. If a user has an alias for an authentication source, the system tries to take the attribute value from that source, even if the value is empty. If unsuccessful, the system uses the next available source for which the user has an alias. In other words, if I have both SAP & AD configured, with SAP having priority, the value from AD will be pulled in only if my user does not have an SAP user alias, or if they do have an SAP user alias but the attribute points to a non-existing attribute on the SAP system.
About SAP system attributes.
The functionality is limited to the BAPIADDR3 SAP Structure. You can view this information and more if you enter the Structure name BAPIADDR3 into the relevant SAP transaction such as SE11 or SE80.
- SAP Managed Tags:
- SAP BusinessObjects Business Intelligence platform
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
88 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
65 -
Expert
1 -
Expert Insights
178 -
Expert Insights
280 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
11 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
330 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
408 -
Workload Fluctuations
1
- Deep dive into Q4 2023, What’s New in SAP Cloud ALM for Implementation Blog Series in Technology Blogs by SAP
- Nested JSON to SAP HANA Tables with SAP Integration Suite in Technology Blogs by Members
- Single Sign On to SAP Cloud Integration (CPI runtime) from an external Identity Provider in Technology Blogs by SAP
- SAP Sustainability Footprint Management: Q1-24 Updates & Highlights in Technology Blogs by SAP
- SAP Datasphere - Space, Data Integration, and Data Modeling Best Practices in Technology Blogs by SAP
| User | Count |
|---|---|
| 13 | |
| 11 | |
| 10 | |
| 9 | |
| 9 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 5 |