
- SAP Community
- Products and Technology
- Additional Blogs by SAP
- Encryption everywhere -- Securing your Duet landsc...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
 0.1. In my example I am getting all three warnings: the certificate is issued by a company you have not chosen to trust (which just means that my browser does not yet know the certificate and it is not signed by a so called root certificate that is trusted) 0.2. the security has expired or is not yet valid (well, I guess this is self explaining; each certificate is valid only for a certain amount of time – mine is already expired) 0.3. The name of the security certificate is invalid or does not match the name of the site (here the most common problem is “does not match the name of the site”. I have accessed the J2EE Engine via {code:html}http://*DuetServer*:50001{code}. This is the hostname of the J2EE Engine, but the certificate was issued for localhost (as you can see in the next screenshot). When creating the certificate make sure that it matches the URL you are going to use for calls from the Client and the ABAP server)
0.1. In my example I am getting all three warnings: the certificate is issued by a company you have not chosen to trust (which just means that my browser does not yet know the certificate and it is not signed by a so called root certificate that is trusted) 0.2. the security has expired or is not yet valid (well, I guess this is self explaining; each certificate is valid only for a certain amount of time – mine is already expired) 0.3. The name of the security certificate is invalid or does not match the name of the site (here the most common problem is “does not match the name of the site”. I have accessed the J2EE Engine via {code:html}http://*DuetServer*:50001{code}. This is the hostname of the J2EE Engine, but the certificate was issued for localhost (as you can see in the next screenshot). When creating the certificate make sure that it matches the URL you are going to use for calls from the Client and the ABAP server)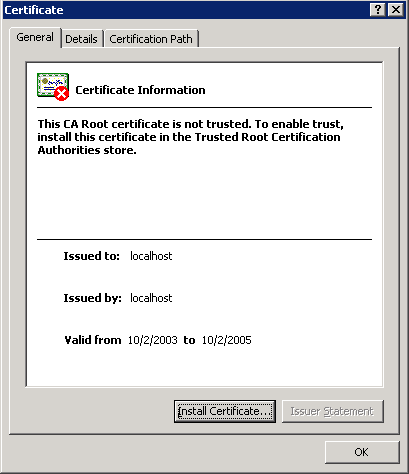 OK, now after getting these three warnings, I have requested a correct certificate and I have installed it on the J2EE. When I call the URL now, and take a look at the certificate everything is fine. h6. Links for securing J2EE Engine 0.1. [Configuring the Use of SSL on the J2EE Engine | http://help.sap.com/saphelp_nw70/helpdata/en/f1/2de3be0382df45a398d3f9fb86a36a/content.htm] 0.2. [J2EE Engine Ports | http://help.sap.com/saphelp_nw70/helpdata/en/a2/f9d7fed2adc340ab462ae159d19509/content.htm] 0.3. [Transport Layer Security on the SAP J2EE Engine | http://help.sap.com/saphelp_nw70/helpdata/en/bc/2ee9a2d023d64eac961745ea2cb503/frameset.htm] 0.4. [Using certificates with the SAP NetWeaver Portal | Using certificates with the SAP NetWeaver Portal] h5. Preparing the ABAP system The J2EE Engine can access the ABAP system in two ways: via WebService calls and RFCs. For both we have to make sure that they are encrypted. h6. HTTP -> HTTPS The WebService-calls use ICM to connect. If you go to transaction SICM you can select Goto -> Parameters -> Display which will show you the current configuration:
OK, now after getting these three warnings, I have requested a correct certificate and I have installed it on the J2EE. When I call the URL now, and take a look at the certificate everything is fine. h6. Links for securing J2EE Engine 0.1. [Configuring the Use of SSL on the J2EE Engine | http://help.sap.com/saphelp_nw70/helpdata/en/f1/2de3be0382df45a398d3f9fb86a36a/content.htm] 0.2. [J2EE Engine Ports | http://help.sap.com/saphelp_nw70/helpdata/en/a2/f9d7fed2adc340ab462ae159d19509/content.htm] 0.3. [Transport Layer Security on the SAP J2EE Engine | http://help.sap.com/saphelp_nw70/helpdata/en/bc/2ee9a2d023d64eac961745ea2cb503/frameset.htm] 0.4. [Using certificates with the SAP NetWeaver Portal | Using certificates with the SAP NetWeaver Portal] h5. Preparing the ABAP system The J2EE Engine can access the ABAP system in two ways: via WebService calls and RFCs. For both we have to make sure that they are encrypted. h6. HTTP -> HTTPS The WebService-calls use ICM to connect. If you go to transaction SICM you can select Goto -> Parameters -> Display which will show you the current configuration:  Here you can see that HTTPS is not yet enabled (if you can already see an entry like icm/server_port_2 = PROT=HTTPS, PORT=8081 then your system is already configured for HTTPS using port 8081). Instead of listing all the steps here in the blog I strongly recommend to take a look at the links mentioned below. The information in the Note, on help.sap.com and the blogs are already great! You basically just have to set some parameters in RZ10 and create a SSL server Standard certificate. After following all these steps you should see at least two green lights in STRUST:
Here you can see that HTTPS is not yet enabled (if you can already see an entry like icm/server_port_2 = PROT=HTTPS, PORT=8081 then your system is already configured for HTTPS using port 8081). Instead of listing all the steps here in the blog I strongly recommend to take a look at the links mentioned below. The information in the Note, on help.sap.com and the blogs are already great! You basically just have to set some parameters in RZ10 and create a SSL server Standard certificate. After following all these steps you should see at least two green lights in STRUST:  If you go back to SMICM and select Goto -> Services. You should also see the entry for HTTPS:
If you go back to SMICM and select Goto -> Services. You should also see the entry for HTTPS: 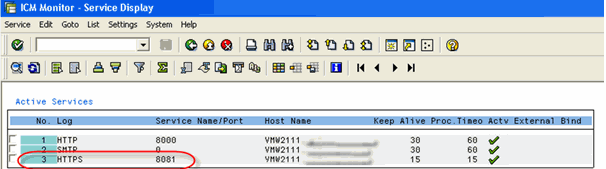 With this information open a browser window and just call https://%3Cabap%3E/sap/bc/bsp/sap/it00/default.htm (https://%3Cabap%3E/sap/bc/bsp/sap/it00/default.htm) You will be prompted for username & password, but that is fine. The important thing is that you either get a Certificate warning again (like before with the J2EE Engine) or that you see the small Security lock in the bottom of your Internet Explorer (indicating that you have accessed a secure web site). If you double click there than you should see the valid certificate. h6. Links for securing ABAP HTTP 0.1. {code:html}Note 510007 - Setting up SSL on Web Application Server ABAP{code}0.1. [Using the Secure Sockets Layer Protocol with the AS ABAP | http://help.sap.com/saphelp_nw70/helpdata/en/3a/7cddde33ff05cae10000000a128c20/frameset.htm] 0.2. [Setup HTTPS for the SAP NetWeaver Testdrive SR1 on Linux | Setup HTTPS for the SAP NetWeaver Testdrive SR1 on Linux] 0.3. [Setup HTTPS (SSL) for the Sneak Preview SAP NetWeaver 04 ABAP Edition on Windows | Setup HTTPS (SSL) for the Sneak Preview SAP NetWeaver 04 ABAP Edition on Windows] h6. RFC -> SNC As you probably know Duet makes some calls from the J2EE Engine to the ABAP system via RFC / JCo calls. In order to have a secure communication there we have to use Secure Network Communications (SNC). Again please follow the links mentioned below. This time it is a little more complicated because you have to follow some steps in ABAP and on the J2EE. On the ABAP side it is important that the SNC SAPCryptolib is active in STRUST. You might also consider to set the parameters like snc/accept_insecure_gui, snc/accept_insecure_cpic, snc/accept_insecure_rfc, snc/accept_insecure_r3int_rfc, snc/enable, (see here (http://help.sap.com/saphelp_nw70/helpdata/en/59/e74eec7c394322869c752947412bb2/frameset.htm) for details) to enable also non-secure connections in parallel. If that is done, check the SNC Status via SM51 -> GOTO -> SNC Status (Ctrl – F10)
With this information open a browser window and just call https://%3Cabap%3E/sap/bc/bsp/sap/it00/default.htm (https://%3Cabap%3E/sap/bc/bsp/sap/it00/default.htm) You will be prompted for username & password, but that is fine. The important thing is that you either get a Certificate warning again (like before with the J2EE Engine) or that you see the small Security lock in the bottom of your Internet Explorer (indicating that you have accessed a secure web site). If you double click there than you should see the valid certificate. h6. Links for securing ABAP HTTP 0.1. {code:html}Note 510007 - Setting up SSL on Web Application Server ABAP{code}0.1. [Using the Secure Sockets Layer Protocol with the AS ABAP | http://help.sap.com/saphelp_nw70/helpdata/en/3a/7cddde33ff05cae10000000a128c20/frameset.htm] 0.2. [Setup HTTPS for the SAP NetWeaver Testdrive SR1 on Linux | Setup HTTPS for the SAP NetWeaver Testdrive SR1 on Linux] 0.3. [Setup HTTPS (SSL) for the Sneak Preview SAP NetWeaver 04 ABAP Edition on Windows | Setup HTTPS (SSL) for the Sneak Preview SAP NetWeaver 04 ABAP Edition on Windows] h6. RFC -> SNC As you probably know Duet makes some calls from the J2EE Engine to the ABAP system via RFC / JCo calls. In order to have a secure communication there we have to use Secure Network Communications (SNC). Again please follow the links mentioned below. This time it is a little more complicated because you have to follow some steps in ABAP and on the J2EE. On the ABAP side it is important that the SNC SAPCryptolib is active in STRUST. You might also consider to set the parameters like snc/accept_insecure_gui, snc/accept_insecure_cpic, snc/accept_insecure_rfc, snc/accept_insecure_r3int_rfc, snc/enable, (see here (http://help.sap.com/saphelp_nw70/helpdata/en/59/e74eec7c394322869c752947412bb2/frameset.htm) for details) to enable also non-secure connections in parallel. If that is done, check the SNC Status via SM51 -> GOTO -> SNC Status (Ctrl – F10)  On the J2EE Engine we also have to create a PSE first. In short you have to download / install the SAP Cryptographic Library on the J2EE (don’t forget to set the Environment variable SECUDIR). Then you have to create a new PSE file. In my example I have put all the files in D:usrsapSAPCryptolib: D:usrsapSAPCryptolib>sapgenpse gen_pse -p SP2-ASJava.pse Please enter PIN: Please reenter PIN: get_pse: Distinguished name of PSE owner: CN=ASJAVA, O=RIG, C=DE PKCS#10 certificate request for "D:usrsapSAPCryptolibsecSP2-ASJava.pse": -----BEGIN CERTIFICATE REQUEST-----
On the J2EE Engine we also have to create a PSE first. In short you have to download / install the SAP Cryptographic Library on the J2EE (don’t forget to set the Environment variable SECUDIR). Then you have to create a new PSE file. In my example I have put all the files in D:usrsapSAPCryptolib: D:usrsapSAPCryptolib>sapgenpse gen_pse -p SP2-ASJava.pse Please enter PIN: Please reenter PIN: get_pse: Distinguished name of PSE owner: CN=ASJAVA, O=RIG, C=DE PKCS#10 certificate request for "D:usrsapSAPCryptolibsecSP2-ASJava.pse": -----BEGIN CERTIFICATE REQUEST-----xxx
-----END CERTIFICATE REQUEST-----
Now export the client certificate for later:
D:usrsapSAPCryptolib>sapgenpse export_own_cert -v -p SP2-ASJava.pse -o SP2-ASJava.crt
Opening PSE "D:usrsapSAPCryptolibsecSP2-ASJava.pse"...
No SSO credentials found for this PSE.
Please enter PIN:
PSE (v2) open ok.
Retrieving my certificate... ok.
Writing to file (PEM-framed base64-encoded)... ok.
SP2-ASJava.crt is created.
Then import the CRT via STRUST in the SNC store of the ABAP system:

Before we export the ABAP SNC server certificate we can set the ACL for this J2EE certificate (SM30 -> table SNCSYSACL, view VSNCSYSACL, type=E):

Next export the SNC server certificate:

Then import this certificate to the Client PSE:
D:usrsapSAPCryptolib>sapgenpse maintain_pk -v -a E05-SNC.crt -p SP2-ASJava.pse
Opening PSE "D:usrsapSAPCryptolibsecSP2-ASJava.pse"...
No SSO credentials found for this PSE.
Please enter PIN:
PSE (v2) open ok.
retrieving PKList
Adding new certificate from file "E05-SNC.crt"
---------
Subject : CN=E05, OU=ISAP-INTERN, OU=SAP Web AS, O=SAP Trust Community, C=DE
Issuer : CN=E05, OU=ISAP-INTERN, OU=SAP Web AS, O=SAP Trust Community, C=DE
Serialno: 00
KeyInfo : RSA, 1024-bit
Validity - NotBefore: Sun Aug 16 09:41:04 2009 (090816084104Z)
NotAfter: Fri Jan 1 01:00:01 2038 (380101000001Z)
--------------------------------------------------------------------------- PKList updated (1 entries total, 1 newly added) Then create a cred_v2 file: D:usrsapSAPCryptolib>sapgenpse seclogin -p SP2-ASJava.pse -O devwdf16SAPServiceSP2 running seclogin with USER="SAPServiceSP2" creating credentials for user "DEVWDF16SAPServiceSP2"... Please enter PIN: Adjusting credentials and PSE ACLs to include "DEVWDF16SAPServiceSP2"... Oh, you supplied your own name explicitly ... ok. D:usrsapSAPCryptolibseccred_v2 ... ok. D:usrsapSAPCryptolibsecSP2-ASJava.pse ... ok. Added SSO-credentials for PSE "D:usrsapSAPCryptolibsecSP2-ASJava.pse" "CN=ASJAVA, O=RIG, C=DE" That should be it. h6. Links for securing JCo 0.1. [Configuring SNC: AS Java à AS ABAP | http://help.sap.com/saphelp_nw70/helpdata/en/c3/d2281db19ec347a2365fba6ab3b22b/frameset.htm] 0.2. [Setup data encryption between RFC Client and Web AS ABAP with SNC | Setup data encryption between RFC Client and Web AS ABAP with SNC] 0.3. {code:html}Note 66687 - Use of network security products{code}0.1. [Secure Network Communications Test Plan | https://weblogs.sdn.sap.com/cs/blank/edit/wlg/] h5. h5. Preparing the IIS In order to enable the IIS for SSL you have to create a certificate request first which you then have to sign by a certificate authority. The steps are all outlined in “{code:html}How to implement SSL in IIS{code}” mentioned below. For my test I was using a self signed certificate which I created with the help of SSLDiag.exe which is part of the IIS Diagnostics Toolkit / {code:html}http://www.microsoft.com/downloads/details.aspx?familyid=9bfa49bc-376b-4a54-95aa-73c9156706e7&displa...{code}. For this I just ran SSLDiag.exe /s:X /selfssl /n:CN=myduet.server.com Where X is the number of the WebSite that is used by the Duet components (1 to 4 in my case)  After that make sure that you set a SSL port in each web Site property
After that make sure that you set a SSL port in each web Site property  Now restart the IIS and you should be able to access all MSFT Duet WebServices on the IIS via HTTPS. {code:html}https://IIS-Server:1081/RequestHandler/RequestHandler.asmx{code} [https://vmw2626.wdf.sap.corp:8091/DuetReadService.asmx | https://vmw2626.wdf.sap.corp:8091/DuetReadService.asmx] [https://vmw2626:8092/DuetServiceProvider.asmx | https://vmw2626:8092/DuetServiceProvider.asmx] [https://vmw2626:8093/DuetAzManService.asmx | https://vmw2626:8093/DuetAzManService.asmx] h6. Links for securing IIS 0.1. {code:html}How to implement SSL in IIS{code} Now all components should be ready for a secure connection. Since we did not configure the components to only accept secure calls you can still run the landscape in “non-ssl mode”. So I would always recommend to start with a non-secure setup and only once that is working continue with the following steps in which we connect the components. ---- h5. J2EE to ABAP h6. HTTP Connection Like previously mentioned the J2EE Engine uses HTTP and JCo to connect to the ABAP system. So let’s start with HTTP. With Duet 1.5 SP3, configuring HTTPS is quite simple. At first you have to exchange the certificates. For this go to STRUST on the ABAP system and export the SSL server Standard certificate (you do not have to do this if the certificate is signed and the J2EE engine already trusts the signer)
Now restart the IIS and you should be able to access all MSFT Duet WebServices on the IIS via HTTPS. {code:html}https://IIS-Server:1081/RequestHandler/RequestHandler.asmx{code} [https://vmw2626.wdf.sap.corp:8091/DuetReadService.asmx | https://vmw2626.wdf.sap.corp:8091/DuetReadService.asmx] [https://vmw2626:8092/DuetServiceProvider.asmx | https://vmw2626:8092/DuetServiceProvider.asmx] [https://vmw2626:8093/DuetAzManService.asmx | https://vmw2626:8093/DuetAzManService.asmx] h6. Links for securing IIS 0.1. {code:html}How to implement SSL in IIS{code} Now all components should be ready for a secure connection. Since we did not configure the components to only accept secure calls you can still run the landscape in “non-ssl mode”. So I would always recommend to start with a non-secure setup and only once that is working continue with the following steps in which we connect the components. ---- h5. J2EE to ABAP h6. HTTP Connection Like previously mentioned the J2EE Engine uses HTTP and JCo to connect to the ABAP system. So let’s start with HTTP. With Duet 1.5 SP3, configuring HTTPS is quite simple. At first you have to exchange the certificates. For this go to STRUST on the ABAP system and export the SSL server Standard certificate (you do not have to do this if the certificate is signed and the J2EE engine already trusts the signer)  Then go to the J2EE -> Visual Admin and import the certificate as a trustedCA
Then go to the J2EE -> Visual Admin and import the certificate as a trustedCA  Now the SSL connection should work. If you want, you can verify these settings by performing the following steps (they are not required for setting up a secure Deut landscape, but show that SSL is working now): Go to Destinations in the Visual Admin and create a dummy HTTP conection under HTTP and enter the URL {code:html}http://%3Cabap-sever%3E/sap/bc/bsp/sap/it00/default.htm{code}
Now the SSL connection should work. If you want, you can verify these settings by performing the following steps (they are not required for setting up a secure Deut landscape, but show that SSL is working now): Go to Destinations in the Visual Admin and create a dummy HTTP conection under HTTP and enter the URL {code:html}http://%3Cabap-sever%3E/sap/bc/bsp/sap/it00/default.htm{code}  After entering a username and password, a "Save and Test" should work fine. Now change the URL to HTTPS and don’t forget to adjust the port to the SSL port on the ABAP system (that’s the one that was visible in SMICM before). A test should still work. As a final step you have to tell Duet to use SSL now. To do that go to System Environment -> Landscape -> SAP Systems and select the backend system that you want to connect to via SSL.
After entering a username and password, a "Save and Test" should work fine. Now change the URL to HTTPS and don’t forget to adjust the port to the SSL port on the ABAP system (that’s the one that was visible in SMICM before). A test should still work. As a final step you have to tell Duet to use SSL now. To do that go to System Environment -> Landscape -> SAP Systems and select the backend system that you want to connect to via SSL.  The SSL port should be fetched automatically and it should be displayed under Port. As a final test, lets call the Web Service navigator and call a simple URL: {code:html}http://J2EE-Engine:50000/wsnavigator{code}. In my case I have Leave Management deployed, so I select the LeaveManagementFacadeWS -> Test -> getLeaveInfo
The SSL port should be fetched automatically and it should be displayed under Port. As a final test, lets call the Web Service navigator and call a simple URL: {code:html}http://J2EE-Engine:50000/wsnavigator{code}. In my case I have Leave Management deployed, so I select the LeaveManagementFacadeWS -> Test -> getLeaveInfo  After entering end-users credentials you should get a valid response.
After entering end-users credentials you should get a valid response.  If you want to be very thourough you can also monitor the call with a HTTP tracer like YaTT. Here the SSL port has to be used and you should not be able to see anything (in contrast to a HTTP call where you would see the clear response & reply):
If you want to be very thourough you can also monitor the call with a HTTP tracer like YaTT. Here the SSL port has to be used and you should not be able to see anything (in contrast to a HTTP call where you would see the clear response & reply):  h6. Links for HTTP Connection 0.1. [Configuration of the Web Service SSL Connection | http://help.sap.com/saphelp_nw70/helpdata/en/90/71d273fa724cc9bb644ab00405e6f8/content.htm] h6. JCO -> Calls We have already exchanged the certificates on the J2EE and the ABAP System. So the final step is to change the configuration: If the configuration for SNC as mentioned before is done, then this step is fairly simple: Go to Visual Admin -> Server -> Services -> Destinations -> RFC -> (Select your System you want to connect to) When you go to the SNC tab select “Active” and enter the data for My SNC name, SNC partner name and SNC Library Path.
h6. Links for HTTP Connection 0.1. [Configuration of the Web Service SSL Connection | http://help.sap.com/saphelp_nw70/helpdata/en/90/71d273fa724cc9bb644ab00405e6f8/content.htm] h6. JCO -> Calls We have already exchanged the certificates on the J2EE and the ABAP System. So the final step is to change the configuration: If the configuration for SNC as mentioned before is done, then this step is fairly simple: Go to Visual Admin -> Server -> Services -> Destinations -> RFC -> (Select your System you want to connect to) When you go to the SNC tab select “Active” and enter the data for My SNC name, SNC partner name and SNC Library Path.  Click on “Save and Test” and you should be done. h6. Links for JCO -> Calls 0.1. [Configuring an RFC Destination to use a Secure Network Connection (SNC) | http://help.sap.com/saphelp_nw70/helpdata/en/32/958f404880b118e10000000a1550b0/frameset.htm] 0.2. [Tracing JCo Calls | http://help.sap.com/saphelp_nw70/helpdata/en/44/0dae09247a3989e10000000a114cbd/frameset.htm] 0.3. [Security Trace | https://service.sap.com/sap/support/notes/495911] 0.4. {code:html}Note 800240 - FAQ: SAP Cryptographic Library error analysis (App. Server){code}0.1. {code:html}Note 912405 - SSF_ERRORMESSAGE: handling of unknown error codes{code} h5. ABAP to J2EE This way should be fairly simple again. During your Duet configuration you have setup at least one RFC destination via SM59 that points to the J2EE Engine. Right now it probably points to the default HTTP port 50000. All we have to do is change this to the SSL port defined earlier. So go to Visual Admin and export the certificate (the one that you chose in Server Identity tab when preparing J2EE Engine) by clicking on Export:
Click on “Save and Test” and you should be done. h6. Links for JCO -> Calls 0.1. [Configuring an RFC Destination to use a Secure Network Connection (SNC) | http://help.sap.com/saphelp_nw70/helpdata/en/32/958f404880b118e10000000a1550b0/frameset.htm] 0.2. [Tracing JCo Calls | http://help.sap.com/saphelp_nw70/helpdata/en/44/0dae09247a3989e10000000a114cbd/frameset.htm] 0.3. [Security Trace | https://service.sap.com/sap/support/notes/495911] 0.4. {code:html}Note 800240 - FAQ: SAP Cryptographic Library error analysis (App. Server){code}0.1. {code:html}Note 912405 - SSF_ERRORMESSAGE: handling of unknown error codes{code} h5. ABAP to J2EE This way should be fairly simple again. During your Duet configuration you have setup at least one RFC destination via SM59 that points to the J2EE Engine. Right now it probably points to the default HTTP port 50000. All we have to do is change this to the SSL port defined earlier. So go to Visual Admin and export the certificate (the one that you chose in Server Identity tab when preparing J2EE Engine) by clicking on Export:  On the ABAP side go to STRUST and add this certificate to SSL Client (Standard)
On the ABAP side go to STRUST and add this certificate to SSL Client (Standard)  Then go to SM59, select the RFC destination, click on the tab „Technical Settings” and change the port. Then go to Logon & Security and under Status of Secure Protocol click on Active. Since we exchanged the SSL Certificates under Standard, select this entry in the drop down
Then go to SM59, select the RFC destination, click on the tab „Technical Settings” and change the port. Then go to Logon & Security and under Status of Secure Protocol click on Active. Since we exchanged the SSL Certificates under Standard, select this entry in the drop down  Now you should test the connection. If you get an ICM error, go to SMICM -> Goto -> Trace File -> Display End. Here you will see more details, e.g.
Now you should test the connection. If you get an ICM error, go to SMICM -> Goto -> Trace File -> Display End. Here you will see more details, e.g.  In this example I have not imported the J2EE certificate to the ABAP system. So something must have gone wrong when using STRUST. Go back and make sure that the J2EE certificate is really under SSL client SSL Client (Standard) like mentioned before. You might also want to restart ICM via SMICM -> Administration -> ICM -> Exit Soft -> Global to check if this has any effect. h6. Links for ABAP to J2EE 0.1. [ADS SSL configuration journal I. / ABAP -> JAVA / 640 - 70x | ADS SSL configuration journal I. / ABAP -> JAVA / 640 - 70x] 0.2. [http://help.sap.com/saphelp_nw70/helpdata/en/2e/797bf5543d4f38aecdd2cabd5206ae/content.htm | http://help.sap.com/saphelp_nw70/helpdata/en/2e/797bf5543d4f38aecdd2cabd5206ae/content.htm] h5. J2EE to IIS The J2EE connects to the IIS via three web sites: the Request Handler, the Service Provider and the AzMan service. We already enabled SSL for all of them so we just have to trust the certificate of the IIS and change the configuration of these services from the Duet Admin page. For the trusting part, just export the certificate used by the IIS and import it to the Key Store via Visual admin (same as before with the J2EE to ABAP HTTP connection). To change the configuration go to /duet -> System Environment -> Landscape -> Microsoft Components -> Request Handler. Here select Use SSL and change the port to the SSL port.
In this example I have not imported the J2EE certificate to the ABAP system. So something must have gone wrong when using STRUST. Go back and make sure that the J2EE certificate is really under SSL client SSL Client (Standard) like mentioned before. You might also want to restart ICM via SMICM -> Administration -> ICM -> Exit Soft -> Global to check if this has any effect. h6. Links for ABAP to J2EE 0.1. [ADS SSL configuration journal I. / ABAP -> JAVA / 640 - 70x | ADS SSL configuration journal I. / ABAP -> JAVA / 640 - 70x] 0.2. [http://help.sap.com/saphelp_nw70/helpdata/en/2e/797bf5543d4f38aecdd2cabd5206ae/content.htm | http://help.sap.com/saphelp_nw70/helpdata/en/2e/797bf5543d4f38aecdd2cabd5206ae/content.htm] h5. J2EE to IIS The J2EE connects to the IIS via three web sites: the Request Handler, the Service Provider and the AzMan service. We already enabled SSL for all of them so we just have to trust the certificate of the IIS and change the configuration of these services from the Duet Admin page. For the trusting part, just export the certificate used by the IIS and import it to the Key Store via Visual admin (same as before with the J2EE to ABAP HTTP connection). To change the configuration go to /duet -> System Environment -> Landscape -> Microsoft Components -> Request Handler. Here select Use SSL and change the port to the SSL port.  Currently we do have an issue with configuring the Metadata service via SSL to the IIS via the UI. So you have to go to the Visual Admin and change the corresponding destinations manually: Go to Server -> Services -> Destinations -> WebServices and select sap.com/xapps~osp~fw~wsproxies/com.sap.xapps.osp.fw.wsproxies.azman.AzmanService/*DuetAZMan*ServiceProviderSoap
Currently we do have an issue with configuring the Metadata service via SSL to the IIS via the UI. So you have to go to the Visual Admin and change the corresponding destinations manually: Go to Server -> Services -> Destinations -> WebServices and select sap.com/xapps~osp~fw~wsproxies/com.sap.xapps.osp.fw.wsproxies.azman.AzmanService/*DuetAZMan*ServiceProviderSoap
Now in the URL change the protocol to HTTPs and the port to the SSL-Port

Click on Save and Test to make sure the settings are correct.
Do the same for sap.com/xapps~osp~fw~wsproxies/com.sap.xapps.osp.fw.wsproxies.msft.ServiceProvider/*ServiceProvider*ServiceSoap  Again click Save and Test to make sure the settings are correct. h5. ---- h5. Clients To J2EE In the Duet Administration go to System Environment -> Landscape and enter the settings for HTTPS Port for Duet Server and Duet Server AddOn.
Again click Save and Test to make sure the settings are correct. h5. ---- h5. Clients To J2EE In the Duet Administration go to System Environment -> Landscape and enter the settings for HTTPS Port for Duet Server and Duet Server AddOn.  Then go to General Settings and Tools and under General -> Authentication select the Authentication method: Kerberos with SSL
Then go to General Settings and Tools and under General -> Authentication select the Authentication method: Kerberos with SSL  That should be it. The next time the client fetches new metadata it will then retrieve the data via HTTPS from the J2EE Engine. h5. ---- There are only very few items left: the connection from the J2EE to the Active Directory and the connection from the Request Handler to the Exchange. I have not covered the part where the Client gets the data from the Read Service via SSL. Ideally you should only have to configure the IIS on the ReadService to use SSL and then change the URL in the Group Policies for the ReadService to SSL -- unfortunately we have currently an issue here which will be fixed with the next patch. If you still want/have to use this, there is a workaround in place. h5. J2EE to ADS To finish your secure Duet landscape you should also encrypt the communication from the J2EE Engine to the ADS. This is again quite well documented (and simple), so I am just referring to the links mentioned below. Basically you just have to exchange certificates again and then via Config Tool change the port and enable SSL:
That should be it. The next time the client fetches new metadata it will then retrieve the data via HTTPS from the J2EE Engine. h5. ---- There are only very few items left: the connection from the J2EE to the Active Directory and the connection from the Request Handler to the Exchange. I have not covered the part where the Client gets the data from the Read Service via SSL. Ideally you should only have to configure the IIS on the ReadService to use SSL and then change the URL in the Group Policies for the ReadService to SSL -- unfortunately we have currently an issue here which will be fixed with the next patch. If you still want/have to use this, there is a workaround in place. h5. J2EE to ADS To finish your secure Duet landscape you should also encrypt the communication from the J2EE Engine to the ADS. This is again quite well documented (and simple), so I am just referring to the links mentioned below. Basically you just have to exchange certificates again and then via Config Tool change the port and enable SSL:  h6. Links J2EE to ADS 0.1. [Configuring SSL Between the UME and an LDAP Directory | http://help.sap.com/saphelp_nw70/helpdata/en/7d/77fa735e5f47a2a50b5336fd1b5a61/frameset.htm] 0.2. [Configuring SSL between Microsoft Active directory and Enterprise portal | Configuring SSL between Microsoft Active directory and Enterprise portal] h5. RequestHandler to Exchange Once you have installed the Request Handler (if you have not yet installed with SSL from the beginning) you can open and edit the file C:InetpubRequestHandlerRootRequestHandlerweb.config. There you just have to change the configuration in two or three places:
h6. Links J2EE to ADS 0.1. [Configuring SSL Between the UME and an LDAP Directory | http://help.sap.com/saphelp_nw70/helpdata/en/7d/77fa735e5f47a2a50b5336fd1b5a61/frameset.htm] 0.2. [Configuring SSL between Microsoft Active directory and Enterprise portal | Configuring SSL between Microsoft Active directory and Enterprise portal] h5. RequestHandler to Exchange Once you have installed the Request Handler (if you have not yet installed with SSL from the beginning) you can open and edit the file C:InetpubRequestHandlerRootRequestHandlerweb.config. There you just have to change the configuration in two or three places: 
- Upload file capability in landscape manager in Technology Q&A
- SAP Commerce Best Practices for Performance in CRM and CX Blogs by SAP
- Receive a notification when your storage quota of SAP Cloud Transport Management passes 85% in Technology Blogs by SAP
- Capture Your Own Workload Statistics in the ABAP Environment in the Cloud in Technology Blogs by SAP
- 10+ ways to reshape your SAP landscape with SAP Business Technology Platform - Blog 7 in Technology Blogs by SAP