
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- How to Define Risk-Based Authentication Rules with...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Being very cautious about the existing risks, you deny access from outside your corporate network or being very liberal, you allow access from anywhere?
Are you willing to set different rules for different users, for different applications and according to the network from which the users try to access the protected applications?
If yes, then SAP HANA Cloud Platform Identity Authentication(shortly Identity Authentication) can provide you with such flexibility of defining authentication rules, tailored to your exact business needs.

Let’s take a closer look at the available options and variants to configure Risk-Based Authentication.
With the Risk-Based Authentication, you are able to set different rules for each application according to the following factors:
1. User group membership of the authenticating user:
i. Cloud user group, defined in the Identity Authentication service
or
ii. On-premise user group(e.g. LDAP User Group, SAP NetWeaver AS UME Group or ABAP Roles as UME Groups), if you are using Corporate User Store scenario(authentication against on-premise user store(LDAP, SAP NW AS JAVA, SAP NW AS ABAP).
2. Network IP ranges from which the users are logging into the applications
For the combination of these factors, you can define actions to be performed:
- Allow access
- Enforce Two-Factor Authentication
- Deny access
The set of rules are executed by priority and if none of the conditions of the defined rules are met, then the default action would be performed.
In this blog you can find four examples of four different risk-based authentication rules sets defined:
- Enable Two-Factor Authentication for all the users of an application
- Deny access from outside corporate network for everybody, except a certain group of users that would be asked to authenticate with Two-Factor Authentication
- Allow access only for the users that exist in Microsoft Active Directory
- Deny Access to an application
- Apply stronger security for the administrators' access to the Administration Console of the Identity Authentication service
1. Enable Two-Factor Authentication for all the users of an application
For an application that needs higher level of protection, you can set all users to be prompted to provide an One-Time Password(code), generated on a mobile device(SAP Authenticator – available on iOS , Android and Windows or any authenticator app compatible with RFC 6238)
Here are the steps you need to take:
Prerequisites:
1. You have added your application and configured Trust between your application(SP) and the Identity Authentication(SAML IDP). For SAP HCP apps – see here
2. You have an Administrator account for Identity Authentication service with “Manage Applications” Role enabled
Steps:
1. Go to your application in the Administration Console of Identity Authentication service - Navigate to https://<your tenant ID>.accounts.ondemand.com/admin/ and login with your administrator’s credentials
2. In the left menu, go to "Applications and Resources" -> “Applications”

3. Choose your application from the list of applications on the left side
4. Navigate to the „Authentication and Access“ tab

5. Choose “Risk-Based Authentication”

6. Change Default Action from “Allow” to “Two-Factor Authentication” and click “Save”

The result for the end users:
All users would be prompted to provide One-Time Password when they log into the application



2. Deny access from outside corporate network for everybody, except a certain group of users that would be asked to authenticate with Two-Factor Authentication
Follow all the steps up to step 5 from the previous example, the prerequisites are also the same.
Define the following rules:

1st Rule: Allow access from within the IP-range of your corporate network.

2nd Rule: Require Two-Factor Authentication for any user that is member of the Cloud User Group “Manager“

In addition, deny access to any other users by setting Default Action to “Deny”

The rules are executed by the order of priority until the conditions of a rule are met. If none of the conditions of the defined rules is met then the default action is performed.
Once the users who are not members of the Cloud User Group “Manager” try to access the application from outside of the corporate network, they would get the following message:

Find more info about Cloud User Groups:
How to Add User Groups
Assign User Groups to an user
3. Allow access only for on-premise users that exist in Microsoft Active Directory
Prerequisites:
1. You have configured authentication against Corporate User Store(with Microsoft Active Directory), additionally see this blog
2. You have added your application and configured Trust between your application(SP) and the Identity Authentication service(SAML IDP). For SAP HCP apps – see here
3. You have an Administrator account for Identity Authentication service with “Manage Applications” Role enabled
Steps:
Follow all the steps up to step 5 from example 1.
Assign all the users to a Microsoft Active Directory group (e.g. called “MSAD Everybody”) so that you enable them to authenticate in your cloud application and deny access for all other users.


You can define other more complex rules for other Microsoft Active Directory Groups, for example:
- An Administrator would have access only from within corporate network and would be required to provide 2 means of authentication(Two-Factor Authentication).
- Partners outside of their corporate network would also be required to authenticated with Two-Factor Authentication.
- All the users of this applications shall belong to an on-premise Microsoft Active Directory User Group – “MSAD Everybody”.
- For all other users the access will be denied.
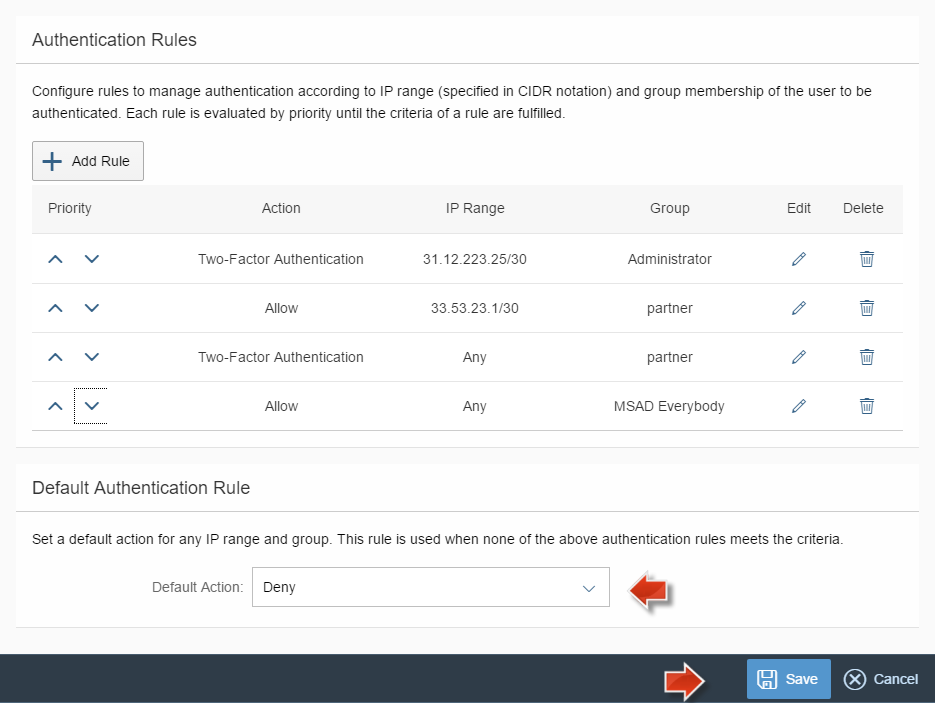
If you have configured Corporate User Store scenario of the Identity Authentication service to authenticate against SAP NetWeaver AS JAVA server, you can define the same type of rules for other types of On-premise User Groups – depending on the different options - UME Groups, User Groups of the connected multiple LDAP Directories or ABAP Roles as UME Groups, see documentation about UME Groups
4. Deny access to an application
Steps:
Follow all the steps up to step 5 from example 1, the prerequisites are also the same.
Before going live of your application you can deny access to everybody by setting Default Action “Deny”

Once you are ready to go live, you just change the Default Action to “Allow”
5. Apply stronger security for the administrators' access to the Administration Console of the Identity Authentication service
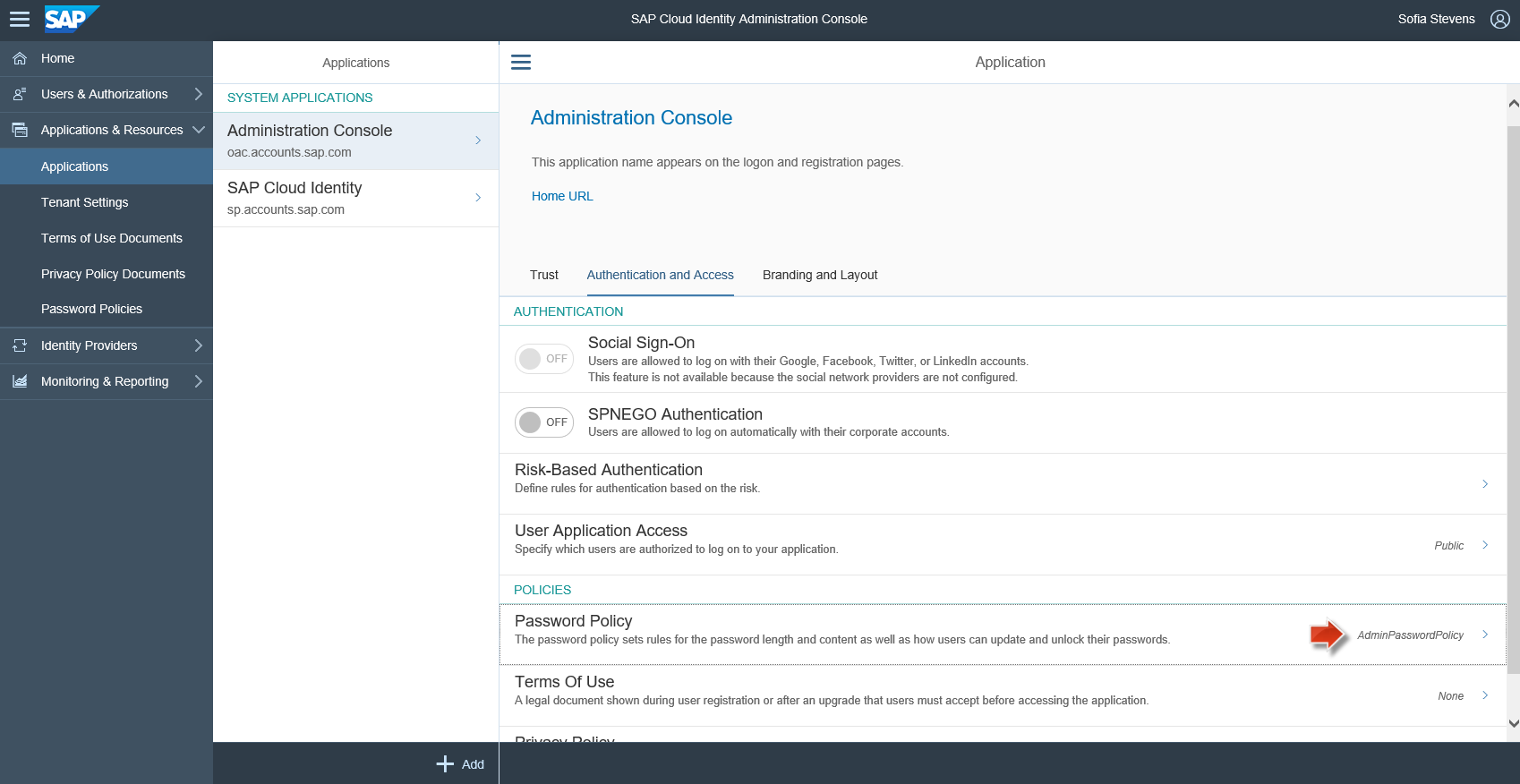
5.1. Define Risk-Based Authentication rules to the Administration console
You can find the Administration console as a System Application and you can define your own rules, e.g. allow access of the Administrators only from inside your corporate network or enforce the admins to authenticate always with a second factor.

5.2 Define a Custom Password Policy and assign it to the Administration Console
1. Go to "Password Policies" from the left menu and choose "Add Custom Policy"

2. Create your own Password Policy, according to your security needs

3. Assign it to the Administration Console
In a nutshell, you have the freedom to flexibly configure the authentication to your applications based on your security requirements and corporate needs. You can enforce more stronger password polices to applications, too.
Enjoy your journey with Risk-Based Authentication
- SAP Managed Tags:
- SAP Cloud Identity Services,
- Security,
- SAP Business Technology Platform
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
91 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
66 -
Expert
1 -
Expert Insights
177 -
Expert Insights
293 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
12 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
340 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
416 -
Workload Fluctuations
1
- Onboarding Users in SAP Quality Issue Resolution in Technology Blogs by SAP
- CAP authentication in Technology Q&A
- How to use AI services to translate Picklists in SAP SuccessFactors - An example in Technology Blogs by SAP
- Services not visible in BAS S/4 Hana Public Cloud. in Technology Q&A
- Real time access management with SAP BTP Kyma serverless workloads in Technology Blogs by SAP
| User | Count |
|---|---|
| 31 | |
| 24 | |
| 10 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 4 |