
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Winning Trust. SAP Data Custodian Co-Innovation Pr...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Product and Topic Expert
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
10-23-2020
9:59 AM

Moving beyond Gold!

Data is the most valuable resource in today’s world. It is the unique driving force that powers national economies, global enterprises, and digital platforms. From clinical research to gene therapy to autonomous enterprises, there are myriad ways in which data can improve business and humanity. The influence of data can be seen across all lines of business and has become more valuable than gold in our modern economies.
As businesses become increasingly data-driven, they must also recognize and respond to vulnerabilities that threaten the personal data and trust of their customers, employees, and partners. We must manage the dark side of data and safeguard our valuable resources in the cloud and on-premise. Transparency and Control are important factors when protecting against these risks, especially for businesses driven by data-value chains.
With the SAP Data Custodian Solution, you can protect your data with innovative Transparency, Control, and Key Management features.
Customer Requirements and Use Cases
For a customer in the retail industry, currently embarking on a digital transformation journey through a brownfield SAP S/4HANA implementation and adoption of a multi-cloud strategy with Software-as-a-Service solutions.
Challenge – Requirements
The evolution of global data protection laws has resulted in new challenges to multi-cloud era deployments in landscape. The key challenges include:
- Innovation Factory Approach to establish a solid Data Transparency & Control foundation for the latest technology adoptions
- Deploy new dimensions for real-time risk insights and automatically detect anomalies at the infrastructure and application layers, using advanced machine learning algorithms
- Implement the leading industry best practices, for the design and process of Data Privacy & Protection
- Comply with Global Regulations (for example, GDPR) and industry standards
Solution Scope
To address the challenges faced by the customer, the SAP Data Custodian Co-Innovation Project was proposed. SAP Data Custodian is a Multi-Cloud SaaS application designed to achieve the following business objectives:
- Create and enforce public-cloud data access, data transfer, and data at rest policies
- Monitor and report on these various policies in the public cloud
- Enforce geolocation controls for data access, data transfer, and data at rest
- Control the full lifecycle of encryption keys
For this customer, SAP ERP systems (SAP S/4HANA, SAP ECC) hosted on hyperscalers (AWS, Azure) were connected to SAP Data Custodian pre-production tenant. Five use cases were implemented in the Co-Innovation Project. This includes data regulation, data protection, anomaly detection, information detectors, and key management.

Use Case 1: Data Regulation

Supported by infrastructure transparency and control
Objective:
- Provide data regulation features to address global legislation, data sovereignty, and localization.
- Establish consistent data guidelines through SAP Data Custodian’s pre-built policy templates, automated alerts for policy violations, incident management workflows, and audit reporting.
Benefits:
- Comply with global data regulations such as GDPR, CCSL, CCRF, India Privacy Bill, and China Cyber Law.
- Achieve governance of data sovereignty, support legislative compliance, and prevent data exfiltration to embargoed countries.
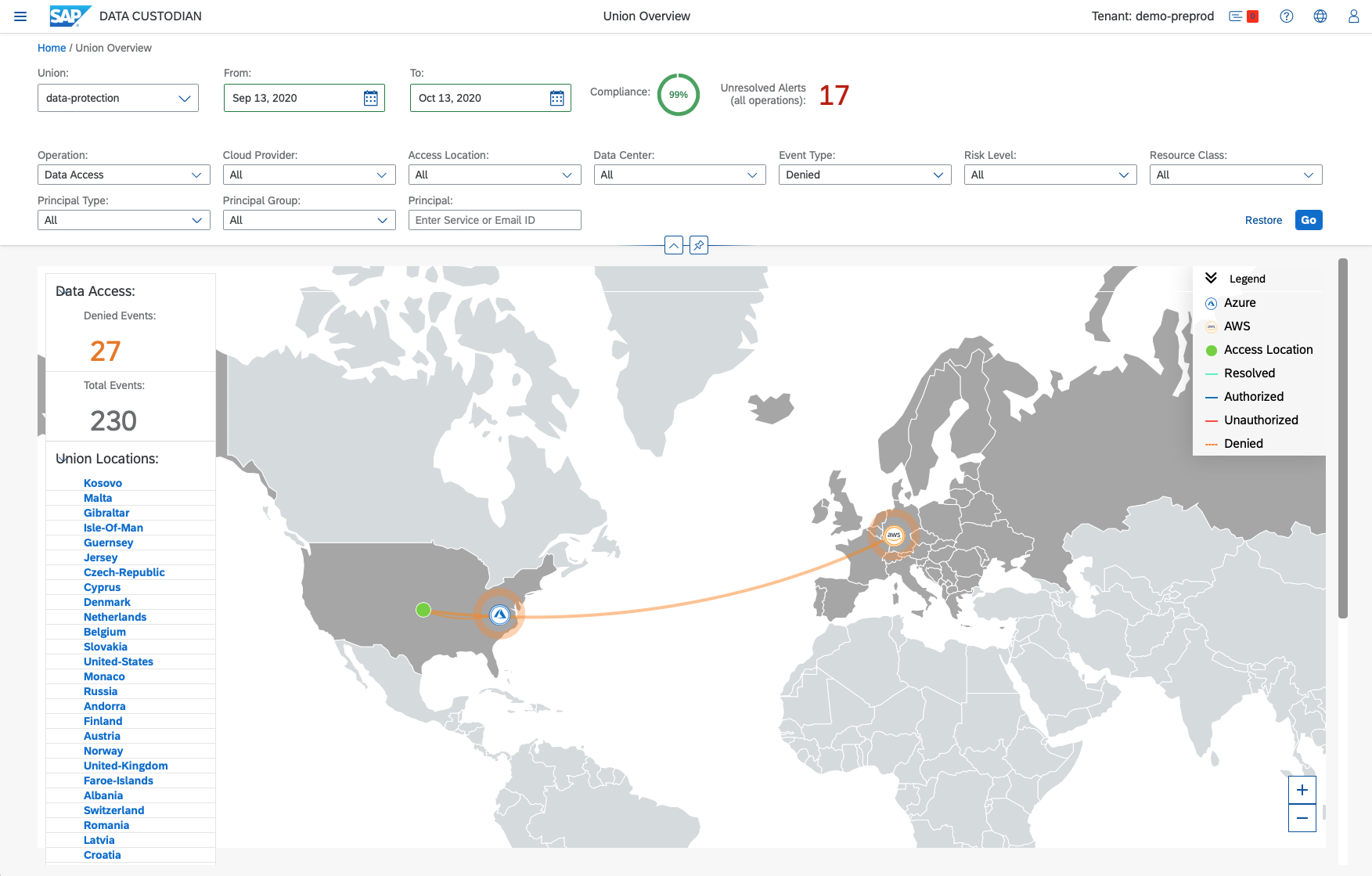 |  |
Use Case 2: Data Protection
Supported by application transparency and control

Objective: Apply data protection policies based on a Customer’s Privacy framework, to monitor and safeguard data in SAP Applications that are hosted on public clouds and on-premise environments.
Benefits: Continuously monitor activities and safeguard data by implementing data protection policies to monitor activities for critical operations, prevent exposure of sensitive data to unauthorized users, minimize personal data exposure through contextual masking policies, and notify users if privileged accounts access confidential data.
 |  |
Use Case 3: Anomaly Detection
Identify suspicious activity
Objective: Monitor system activity and raise alerts on suspicious actions without setting policies.
Benefits: Anomalies can be identified for suspicious resource instances, operations, principals, resource zones, and locations. New policy requirements can also be pinpointed.
 |  |
Use Case 4: Information Detectors
Identify and tag sensitive data

Objective: Detect sensitive information (e.g. SSN, credit card number, etc.) for resource objects at the infrastructure level and label resources that contain personally identifying information (PII).
Benefits:
- Apply appropriate policies on resources, based on labels generated by the information detector
- Reduce data protection risk through identification of data storage locations
- Rapidly identify most sensitive data locations in near real time, prior to configuring control policies to prevent unauthorized access or to detect data breaches and data exfiltration activities
 |  |
Use Case 5: Key Management Service

Provides Customer with complete control over their encryption keys
Objective: Protect sensitive and confidential data in SAP Applications that are hosted on public clouds and on-premise.
Benefits: Key management and data encryption capabilities allow Customer to:
- Protect the data in their Hyperscalers
- Prevent unauthorized information disclosures from third parties
- Secure data against breaches by internal and external entities
- Control the complete lifecycle of their encryption keys
- Segregate duties and manage their keys separately from their data
 |  |
Conclusion
In conclusion, as a result of evolving data protection laws and new security perspectives, challenges on Multi-cloud Era deployments are growing. In order to help customers to comply and protect data on the public cloud, SAP Data Custodian solution offer cloud data insight and protection for full stack (from Database – infrastructure, SAP HANA, SAP S/4HANA Application). The following diagram provides a summary of the business value offered by SAP Data Custodian.

Key Team Members
Authors/ MaxAttention IDG Contact: rohit.dwivedi , kiran.kola , balajigaddam , Thomas Walther
Product Management: wasif.gilani, priyank.patel01
SAP MaxAttention PE Package Info: SAP Data Custodian PE Package (External)
- SAP Managed Tags:
- SAP Data Services,
- SAP Innovation Management,
- SAP S/4HANA,
- Cloud,
- Digital Transformation,
- SAP Integration Strategy
Labels:
1 Comment
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
87 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
64 -
Expert
1 -
Expert Insights
178 -
Expert Insights
273 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
11 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
326 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
403 -
Workload Fluctuations
1
Related Content
- Enhancing Cloud Security: How SAP Business Technology Platform (SAP BTP) Security Capabilities Tackle OWASP Vulnerabilities in Technology Blogs by SAP
- Decoding Cybersecurity and Data Privacy Controls with SAP Cloud Services in Technology Blogs by SAP
- RISE with SAP: Adopting to Zero Trust Architecture Principles with SAP Cloud Services in Technology Blogs by SAP
- Top Innovations of 2020 for SAP Customers in the AWS Cloud in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 12 | |
| 10 | |
| 9 | |
| 7 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 4 |