
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Harmonized Single Sign-On for SAP RISE Customers i...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
updated date: 15.Jul.2023Security is one of the top priorities for enterprise customers. For enterprise end users, having a seamless log-in process to different systems automatically without manually inputting credentials, can not only improve user experience but also increase enterprise security. With that being said, SSO plays a key role in the process.
In this article, we are addressing scenarios where RISE with SAP Private Cloud Edition customers (their SAP workloads managed by SAP on hyperscalers or SAP DC) run in multi-cloud environments, and have more than one enterprise IDP. With this setup, how they can both federate SOO within their SAP landscape with SAP IDPs and security solutions, meanwhile can also harmonize SSO and security workflow management with other third-party IDPs (like, Azure AD). Meaning that each IDP for its own purpose can keep its autonomy, and can still be federated to a certain extent on demand.
In this article, we mainly focus on direct client-to-server SSO scenarios.
A follow-up blog with regard to SSO on the server side can be found here, 'Demystify Single Sign-On on Server Side for SAP RISE Customers'.

Terminologies and Abbreviations
| Single Sign-On (short as SSO) |
|
| Identity Provider (short as IDP) |
|
| Service Provider (short as SP) |
|
| Identity Management (short as IDM) |
|
| Identity and Access Management (short as IAM) |
|
| Federated SSO |
|
| Harmonized SSO [Highly Recommended] |
|
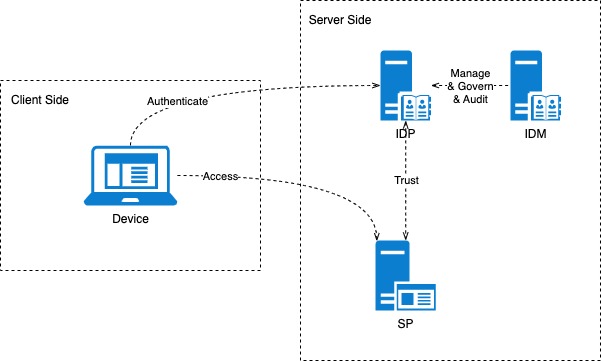
Fig. 1: SSO process roles and responsibilities
Architecture Design
In this section, we will first go through the SAP IDPs and IDMs used for SAP landscape SSO federation, and will also list the major SAP products SSO integration. Then by following, we will consider RISE with SAP Private Cloud Edition customers in multi-cloud environments, then propose the 'Security Hub and Spoke' concept which can do SSO harmonization in such setups.
SAP SSO Federation for SAP Workforce (SAP IDPs & IDMs integration with SAP SPs):
List of SAP Identity Provider Solutions:
| Identity Provider Solution | Supported Method | Deployment |
| SAP Cloud Identity Services - Identity Authentication | Kerberos SAML 2.0 OpenID Connect OAuth2 SPNEGO X.509 Social Sign-On (FaceBook, Google, Twitter, LinkedIn) | Cloud Subscription on BTP |
| SAP Single Sign-On 3.0 | Kerberos SPNEGO X.509 SAML 2.0 | SAP RISE managed VM |
SAP Identity Management Solutions:
SAP IDMs provide you enterprise-level IAM workflow management, identity lifecycle management, access governance and audition.
| Identity Management Solution | Deployment |
| SAP Cloud Identity Services | Cloud Subscription on BTP |
| SAP Cloud Identity Access Governance | Cloud Subscription on BTP |
| SAP Identity Management | SAP RISE managed VM |
| SAP Access Control | SAP RISE managed VM |
List of Major SAP Solutions SSO integration guide:
* Please note that the below list is not able to list all SAP products and all integration scenarios, more support could be found on SAP official documentation.
| SAP Product | SSO Method | Identity Provider |
| SAP GUI | Kerberos | SAP Secure Login Service on BTP |
| SAP Single Sign-On | ||
| X.509 | SAP Single Sign-On | |
| SAP Fiori | SAML | SAP Cloud Identity Services Fiori (for ABAP) SSO guide |
| Kerberos/X.509/SAML2.0 | SAP Single Sign-On Fiori SSO guide | |
| SAP NetWeaver (web GUI) | SAML/OAuth | SAP Cloud Identity Services Web-based SSO configuration |
| SAP Single Sign-On | ||
| SAP HANA | Kerberos | SAP Single Sign-On HANA Keberos SSO guide |
| SAML 2.0 | SAP Cloud Identity Services HANA SAML 2.0 SSO guide | |
| SAP BTP (PaaS) | SAML/OAuth | BTP SSO guide |
| SAP Analytics Cloud (PaaS) | SAML 2.0 | SAP Cloud Identity Services SAC SSO guide |
| SAP SuccessFactors (SaaS) | SAML 2.0 | SAP Cloud Identity Services |
| SAP Concur (SaaS) | SAML 2.0 / OpenID | SAP Cloud Identity Services |
| SAP Ariba (SaaS) | SAML 2.0 / OpenID | SAP Cloud Identity Services |
| SAP Fieldglass (SaaS) | SAML 2.0 | SAP Cloud Identity Services |
| SAP C4C | SAML 2.0 / OpenID | SAP Cloud Identity Services |
SAP SSO Harmonization with third-party SSO:
In a multi-cloud environment, there could be multiple identity providers (IDP), each IDP is designed for its own purpose with native integration with its own cluster of service providers.
Enterprise customers can always directly configure trust between SAP IDP (BTP CIS) and hyperscaler IDPs. For detailed guidance or tutorials, please consult hyperscaler providers (Microsoft, Amazon, or Google). Here we do a short review based on the hyperscaler documentation from hyperscaler providers' websites (see Fig. 2, 3, 6).
As most enterprise customers use Microsoft Office 365 and might already have Azure AD in place, hence we propose the 'Security Hub and Spoke' architecture. We suggest using Microsoft Azure AD as the 'hub' for SSO harmonization, then SAP IDP and other hyperscaler IDPs will play as 'spoke' in the multi-cloud landscape. (see Fig. 2, 4, 5)
In cases where customers use Google G-Suite instead, customers can still build trust between SAP IDP and Google IDP. (see Fig. 6)
With these setups, each IDP will keep its autonomy, while still having the 'trust' harmonized and having the sync in place.
| Integration with Azure IDP (Microsoft Entra, previously, Azure AD) | (see Fig. 2) |
| |
| Integration with AWS IDP (AWS IAM Identity Center) | (see Fig. 3) |
| |
| (see Fig. 4) |
| ||
| Integration with GCP IDP (Google Cloud Identity) | (see Fig. 5) |
| |
(see Fig. 6) |
| ||

Fig. 2: Architecture Design for RISE PCE customers doing Harmonized SSO in Multi-Cloud Environment (customer's own hyperscaler is Azure, as an example)

Fig. 3: Architecture Design for RISE PCE customers doing Harmonized SSO in Multi-Cloud Environment (customer's own hyperscaler is AWS, as an example)

Fig. 4: Architecture Design for RISE PCE customers doing Harmonized SSO in Multi-Cloud Environment (customer's own hyperscaler is AWS & Azure, as an example)

Fig. 5: Architecture Design for RISE PCE customers doing Harmonized SSO in Multi-Cloud Environment (customer's own hyperscaler is GCP & Azure, as an example)

Fig. 6: Architecture Design for RISE PCE customers doing Harmonized SSO in Multi-Cloud Environment (customer's own hyperscaler is GCP, as an example)
Disclaimer:
- SAP takes no responsibility for managing and operating customers’ own data center, nor for customers’ own hyperscaler subscription
- SAP takes no responsibility for provisioning and managing customers' SSO
- SAP product information is based on SAP official documentation online, as of this blog’s updated date of time.
- The architecture designs that appeared in this blog, have been considered with each hyperscalers' (Azure, AWS, GCP) reference architecture from hyperscalers providers’ (Microsoft, Amazon, and Google) official documentation online, as of this blog’s updated date of time.
Acknowledgment to contributors/reviewers/advisors:
Ke Ma (a.k.a. Mark), co-author, Senior Consultant, SAP IES AI CoE / RISE Cloud Advisory RA group
Frank Gong, co-author, Digital Customer Engagement Manager, SAP ECS
Stephan Andre, SAP BTP Security, Development Manager
Tommaso Nuccio, Security Architect, SAP IES Security
Yash Karia, SAP IAM Consultant, SAP IES Platform
Sven Herzog, SAP IAM Consultant, SAP IES Platform
Kevin Flanagan, Head of Cloud Architecture & Advisory, RISE Cloud Advisory, EMEA North
Luc DUCOIN, Cloud Architect & Advisor, RISE Cloud Advisory
Richard Traut, Cloud Architect & Advisor, RISE Cloud Advisory
Sven Bedorf, Head of Cloud Architecture & Advisory, RISE Cloud Advisory, MEE
Samuel Grevillot, Customer Engineer, Google
Ferry Mulyadi,Partner Solution Architect, Amazon Web Services
Extended Reading:
Demystify Single Sign-On on Server Side for SAP RISE Customers
SAP Secure Login Service for SAP GUI Now Available, by SAP colleague, martina.kirschenmann
Join our RISE with SAP community here
Join our SAP Single Sign-On community here
Join our BTP Security community here
Google Cloud Identity integration with SAP Cloud Identity Services, by SAP colleague,
alexander.zubev
A SSO Guide for SAP RISE PCE customers, by SAP colleague, matthias.kaempfer
SAP Lens - AWS Well-Architected Framework, by AWS official website
SSO with SAML 2.0: how does it work, by VMware Youtube Channel- SAP Managed Tags:
- SAP Fiori,
- RISE with SAP,
- SAP BTP Security,
- SAP HANA,
- SAP NetWeaver,
- SAP S/4HANA,
- SAP Business Technology Platform
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
88 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
64 -
Expert
1 -
Expert Insights
178 -
Expert Insights
280 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
11 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
330 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
408 -
Workload Fluctuations
1
- SAP Datasphere - Space, Data Integration, and Data Modeling Best Practices in Technology Blogs by SAP
- Deliver Real-World Results with SAP Business AI: Q4 2023 & Q1 2024 Release Highlights in Technology Blogs by SAP
- 10+ ways to reshape your SAP landscape with SAP Business Technology Platform – Blog Series in Technology Blogs by SAP
- Why Safety Data Sheets and What's New in Technology Blogs by SAP
- SAP Business Technology Platform - Part 1: “Change Agent” or “Scale Agent”, & how to enable it in Technology Blogs by SAP
| User | Count |
|---|---|
| 13 | |
| 10 | |
| 10 | |
| 8 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 4 |