
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Group Assignments Based on User Attributes – a Fle...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Product and Topic Expert
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
03-16-2023
8:52 AM
Triggering group assignments based on a user attribute is among the recent enhancements of Identity Provisioning capabilities.
What does this mean and how can you make use of it?
It means that you can directly assign or unassign whatever users you want (based on their attribute values) to any group that exists on the target system. As simple it sounds, as powerful it is.
Note: A similar functionality is still possible with Identity Authentication version 1. However, it is not recommended for complex scenarios where the users’ groups on the target systems are managed additionally via another identity management processes (as assignments done by those processes could be overwritten).
Let’s say you are managing your users in SAP SuccessFactors (SFSF) and synchronizing them to Identity Authentication service.
Although there are many use case scenarios where this flexible management of user group assignments can be used, these two are the most common ones:
For the purpose of this scenario, we’ll show you how to configure risk-based authentication in your Identity Authentication service using the new feature.
Let’s take as an example the following requirement: The employees working in the Executive Office division must login to the SFSF application with two-factor authentication (TFA). All the rest should be able to access it just with username and password. And of course, if any of these “Executive” employees move on to other division, this TFA should be no longer required as part of the login to SFSF application.
You probably know that rules for risk-based authentication can be configured on a group, and not on an attribute (in our case division= Executive Office). Well, this is where the latest enhancement steps in to help you.
Achieving the above scenario requires separate configuration in three places:
1. In SAP SuccessFactors, make sure all users that work in the Executive Office division have the attribute division= Executive Office (EXEC).
In this scenario, we’ll give you an example with 2 users:
2. In Identity Authentication, create a group and configure risk-based authentication rule with TFA based on it.
In this scenario, we’ll name it: TFA-Required. It’s Group ID is: bf9e73e6-759e-4d93-a6d4-0e2171aad239
3. In Identity Provisioning, configure SAP SuccessFactors source system and Identity Authentication target system.
In this scenario:
Note: Be aware that currently in bundle tenants SAP SFSF version 2 is preconfigured to work with Identity Authentication version 1.
4. Open the Identity Authentication system, select the Transformations tab and choose Edit.
5. Add the following transformation code at the end of the user entity:
What does this transformation tell us?
1st mapping:
2nd mapping:
Note: You can add more than one group IDs in the “constant” array element, that is, you can assign and unassign users to/from multiple groups at the same time.
Note: The group ID that should be specified in the transformation mapping is the SCIM ID of the group resource in IAS SCIM v2 API which is also visible in the SAP Cloud Identity Services administration console under Users & Authorizations -> User Groups -> details of the group:
6. Finally, run a provisioning job.
3. He tries to login to the SFSF application with username and password.
4. In addition to the basic authentication, two factor authentication is required.
Once he scans the QR code and provides the Passcode, he can login to the SFSF application.
A few important notes about direct group assignments:
For more information, see Enabling Group Assignment.
What does this mean and how can you make use of it?
It means that you can directly assign or unassign whatever users you want (based on their attribute values) to any group that exists on the target system. As simple it sounds, as powerful it is.
Before You Start
- This feature is supported for SCIM-based target systems that support PATCH operations, like Identity Authentication version 2.
Note: A similar functionality is still possible with Identity Authentication version 1. However, it is not recommended for complex scenarios where the users’ groups on the target systems are managed additionally via another identity management processes (as assignments done by those processes could be overwritten).
- The user group you want to assign should exist on the target system.
Use Case Scenario
Let’s say you are managing your users in SAP SuccessFactors (SFSF) and synchronizing them to Identity Authentication service.
Although there are many use case scenarios where this flexible management of user group assignments can be used, these two are the most common ones:
- Configuring conditional authentication based on the value of the loginMethod attribute in SFSF that differentiates users authenticated by Identity Authentication from those authenticated by corporate identity provider.
- Enforcing two-factor authentication by Identity Authentication service based on user attributes that are coming from the user source system (via group assignments).
For the purpose of this scenario, we’ll show you how to configure risk-based authentication in your Identity Authentication service using the new feature.
Let’s take as an example the following requirement: The employees working in the Executive Office division must login to the SFSF application with two-factor authentication (TFA). All the rest should be able to access it just with username and password. And of course, if any of these “Executive” employees move on to other division, this TFA should be no longer required as part of the login to SFSF application.
You probably know that rules for risk-based authentication can be configured on a group, and not on an attribute (in our case division= Executive Office). Well, this is where the latest enhancement steps in to help you.
Achieving the above scenario requires separate configuration in three places:
1. In SAP SuccessFactors, make sure all users that work in the Executive Office division have the attribute division= Executive Office (EXEC).
In this scenario, we’ll give you an example with 2 users:
- Martin Snow – works in the Executive Office division
- John Parker – works in the Corporate Services division
2. In Identity Authentication, create a group and configure risk-based authentication rule with TFA based on it.
In this scenario, we’ll name it: TFA-Required. It’s Group ID is: bf9e73e6-759e-4d93-a6d4-0e2171aad239
3. In Identity Provisioning, configure SAP SuccessFactors source system and Identity Authentication target system.
In this scenario:
- SAP SFSF uses SCIM API version 2 and is configured with certificate-based authentication
- Identity Authentication uses SCIM API version 2 and is configured with certificate-based authentication
Note: Be aware that currently in bundle tenants SAP SFSF version 2 is preconfigured to work with Identity Authentication version 1.
4. Open the Identity Authentication system, select the Transformations tab and choose Edit.
5. Add the following transformation code at the end of the user entity:

What does this transformation tell us?
1st mapping:
- “condition” – Apply this mapping to all users with division attribute set to Executive Office (EXEC).
- “constant” – Assign all the users matching the condition to the given group “TFA-Required” by specifying its group ID.
- “targetVariable” – Execute assign operation.
2nd mapping:
- “condition” – Apply this mapping to all users with no division attribute set to Executive Office (EXEC).
- “constant” – Unassign all the users matching the condition from the specified group “TFA-Required” by specifying its group ID.
- “targetVariable” – Execute unassign operation.
Note: You can add more than one group IDs in the “constant” array element, that is, you can assign and unassign users to/from multiple groups at the same time.
Note: The group ID that should be specified in the transformation mapping is the SCIM ID of the group resource in IAS SCIM v2 API which is also visible in the SAP Cloud Identity Services administration console under Users & Authorizations -> User Groups -> details of the group:

6. Finally, run a provisioning job.
Login With TFA
- User Martin Snow is provisioned to Identity Authentication with attribute division set to Executive Office (EXEC).

2. He is assigned to group TFA-Required.

3. He tries to login to the SFSF application with username and password.

4. In addition to the basic authentication, two factor authentication is required.

Once he scans the QR code and provides the Passcode, he can login to the SFSF application.
Login Without TFA
- User John Parker is provisioned to Identity Authentication with attribute division set to Corporate Services (CORP_SVCS).

2. As expected, he is not assigned the TFA-Required group.
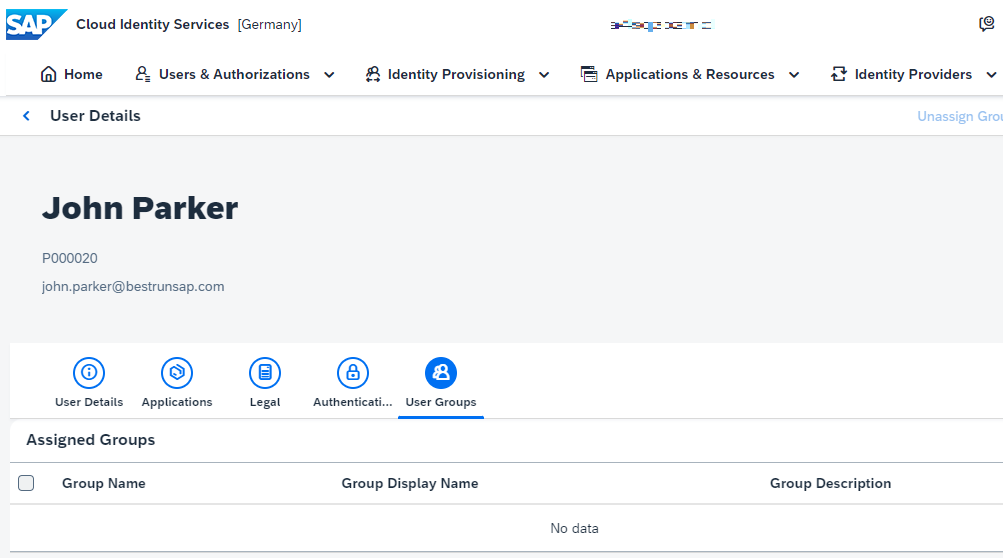
3. He tries to login to the SAP SFSF application with username and password.
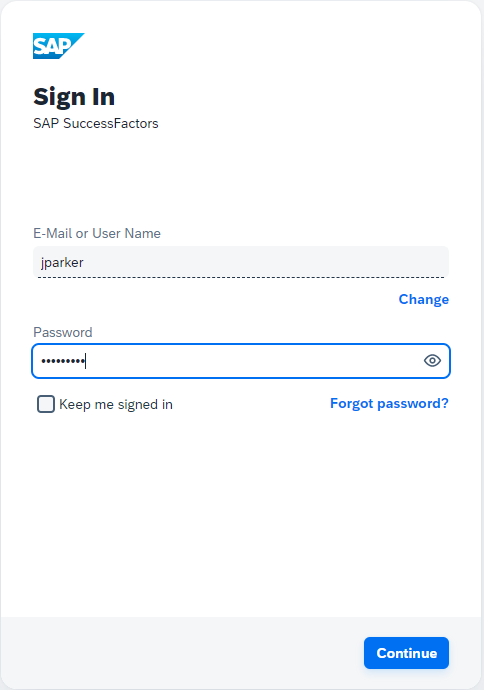
4. He is not required to provide TFA and logs in successfully.

A few important notes about direct group assignments:
- It works for standard provisioning and real-time provisioning.
- It works for target systems with or without enabled bulk operations.
- If the group you want to assign to a user does not exist on the target during user creation, the user provisioning fails.
For more information, see Enabling Group Assignment.
- SAP Managed Tags:
- SAP Cloud Identity Services,
- Identity Provisioning,
- SAP SuccessFactors HXM Suite
Labels:
3 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
88 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
65 -
Expert
1 -
Expert Insights
178 -
Expert Insights
280 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
11 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
330 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
408 -
Workload Fluctuations
1
Related Content
- Activation of IAS in Technology Q&A
- Consuming SAP with SAP Build Apps - Connectivity options for low-code development - part 2 in Technology Blogs by SAP
- How can assign in Identity Authentication Service IAS bulk users to a group? in Technology Q&A
- Identity Federation: SAP Ariba SSO with SAP Cloud Identity Services - Identity Authentication in Technology Blogs by SAP
- Single Sign On to SAP Cloud Integration (CPI runtime) from an external Identity Provider in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 13 | |
| 11 | |
| 10 | |
| 9 | |
| 9 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 5 |