
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- SAP Cloud Identity Services - Identity Authenticat...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Advisor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
01-31-2023
5:03 PM
Scenario Overview
As modern enterprise landscape is evolving and becoming more and more cloud oriented, we have seen direct impact of this evolution on the way SAP customers run and deploy their mission critical applications. SAP customers are adopting SAP Business Technology platform to achieve their journey into cloud world.
Without compromising security one of the key ask of applications hosted on SAP BTP is simplified and great user experience.
In this scenario, I will take you through the steps to deploy an application on SAP BTP and give access to EXTERNAL users for this application using Microsoft Azure Active Directory B2C
and SAP Cloud Identity Services - Identity Authentication.
Few things to keep in mind
- External Users: Users who are not employees of your organisation. For example Vendors
- This scenarios covers authentication part and not authorisation part
- The steps covered in this scenario for Microsoft Azure Active Directory B2C are on a Trial Test Tenant
- This scenario covers authentication using Open ID Connect (OIDC) protocol
- You will also need admin access to your SAP IAS tenant
- You will also need admin/developer access in SAP BTP subaccount
References and links to helpful blogs and material
- How OIDC flow works and various components of the flow
- Authentication and Principal Propagation between Microsoft Azure Active Directory and SAP BTP
Special Thanks and Mention
I would like to specially thank mraepple and martijn.deboer for their help and guidance during this setup.
High Level Diagram

High Level Diagram
Authorisation Flow Diagram

Authorisation Flow Diagram
Steps:
Note: These are the steps which I took to understand the concept and also for my PoC. There are some shortcuts here. For your live implementation all relevant stake holders from SAP skillset and Microsoft skillset need to be involved.
Config in SAP BTP Subaccount
Pre-requisite
- Make sure your SAP IAS tenant is setup under 'SAP BTP Global Account->Security->Trust Configuration' as shown below:

Configuration in BTP Subaccount
- Go to your subaccount and choose 'Security->Trust Configuration'. Click on 'Establish Trust'. If pre-requisite are met, you will see a popup 'Establish Trust to Custom Identity Provider' and in this popup when you will click on drop down, you will see you IAS tenant as shown below

- Please make sure in next screen, you select 'Available for User Logon' check box
Quick Hello World Application
- There are hundreds if not thousands blogs available on developing SAPUI5 applications, CAP applications therefore I won't be explaining how to create an application in this blog
- For my PoC, I used SAP Business Application studio to create a SAPUI5 free style application and deployed it to my SAP BTP subaccount
- This application is 'Managed Router' application. But in case of custom router you will have to create service binding of your application but you will have to bind your application to 'SAP Cloud Identity Service' instead of XSUAA
- Here is my simple 'Hello World' application deployed as HTML5 application in SAP BTP Subaccount

Configuration in Microsoft Azure Active Directory B2C
Now the fun begins.........
Disclaimer: I am not Microsoft Expert. Following knowledge is what I gathered during implementation of PoC. If you don't have access to Microsoft Azure Active Directory B2C tenant, you can spin up your trial tenant at this link Azure Active Directory B2C—Free Trial | Microsoft Azure ( Please bear in mind that you will need a credit card and also you need to keep an eye on any charges etc)
As this whole authentication works on principle of JWT tokens, the JWT token issued by Azure AD B2C should be in a format that SAP IAS is able to decode it and pass it on to your application.
Challenge:
JWT token created from standard Azure AD B2C User Flow gets rejected by SAP IAS!!!
As of now when you create an application(user flow) in Azure AD B2C, you have choice to pick
- Sign Up and Sign In Flow
- Profile Editing
- Password Reset
- Sign Up
- Sign In
- Sign in using resource owner password credentials
For our need we chose 'Sign Up and Sign In Flow'. As with this flow an external user can create a user in AD B2C by registering and after registering they can authenticate themselves against AD B2C. However the JWT token which gets issued as 'Email' claim as an Array and SAP IAS expects Email claim as single parameter.
To over come this challenge, we had to create a 'Custom Policy' in Azure AD B2C. Now with restricted knowledge of Microsoft AD B2C, the challenge was how to create a custom policy. I do hear all security experts screaming its easy!!! May be it is.....!!!
If you are also not Microsoft Azure AD B2C expert like me. There is an incredible way to create these custom policies in your AD B2C tenant.
- Go to https://b2ciefsetupapp.azurewebsites.net/
- Enter your AD B2C Domain
- I chose checkbox of 'Remove Facebook references'
- And click on 'Custom Policy Starter Pack'

Once this pack is deployed and if you will login to your AD B2C tenant, you will see custom policies under Identity Experience Framework section as shown below. You will also see an App called 'IEF Test App' under All applications.

- Go to 'App registrations' and click 'All applications' and there you will see IEF Test App. Click on 'IEF Test App' and you will following kind of screen.
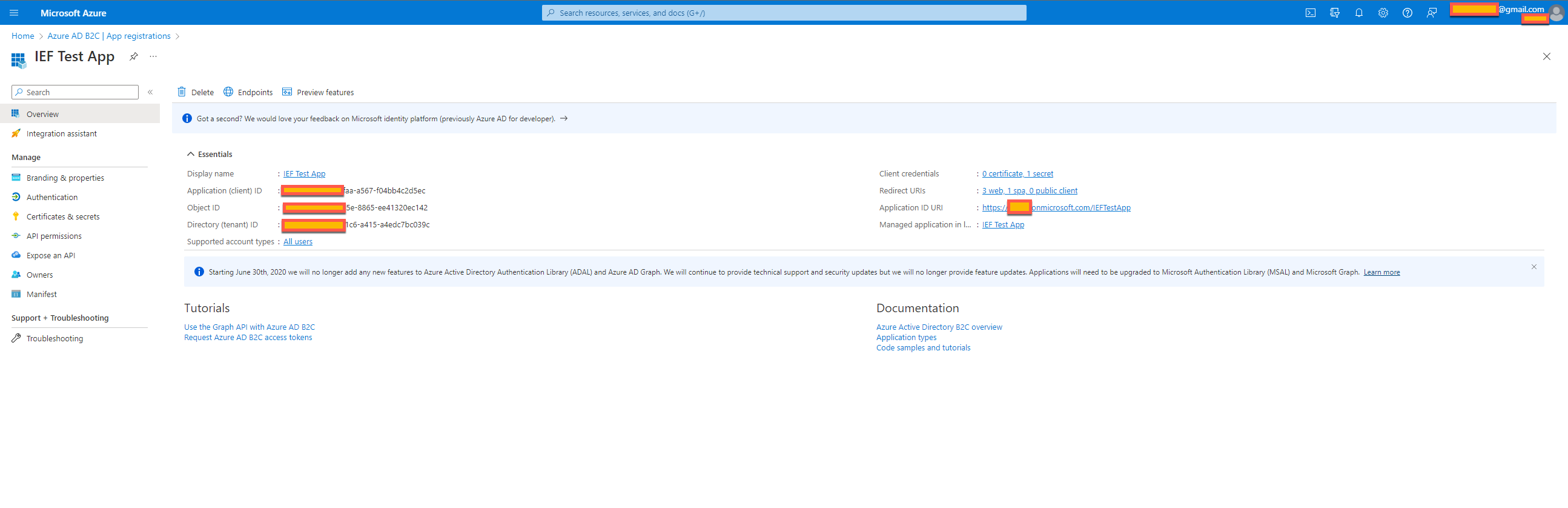
- Click on Authentication and under Web click on 'Add URI' and enter the oauth URL IAS tenant ( https://<IASTenant ID>.accounts.ondemand.com/oauth2/callback
- Afterwards click on 'Certificates & Secrets' for IEF Test App and click 'New Client Secret'. Please note down the 'Value' as this gets displayed once and can not be viewed again and this is needed in your IAS tenant setting
With this you have configured your AD B2C tenant to accept requests from your SAP IAS tenant for authentication
Configuration in SAP IAS tenant
- Logon to your IAS tenant as administrator
- Click on Identity Providers and select 'Corporate Identity Providers'
- Click on Create
- For Identity Provider type, choose 'OpenID Connect Compliant'
- Under OpenID Connect Configuration, please do as explained below

- You can do further settings here for your logon hint etc if needed
- Now we will move on to create an 'application' under 'Application and Resources' Tab in IAS tenant
- Click Create to create a new application and give it a name
- Choose protocol as 'OpenID Connect'
- Under 'OpenID Connect Configuration', you can set your redirect URI

- Under 'Subject Name Identifier' choose 'Email' as select basic attribute
- Under 'Client Authentication', you will get a client ID which is automatically generated
- Click on 'Add' under 'JSON Web Token' and choose issuer from drop down, it will be your AD B2C tenant which you configured under 'Corporate Identity Providers' in previous steps
- For subject take value of 'Object ID' from your AD B2C tenant under Application registrations details for your application. For Example IEF Test App in my case
- Under Conditional Authentication, choose 'Default authentication provider' as the corporate identity provider which you created in previous steps
With these settings, you are all set to test your application.
Outcome
- Launch your HTML5 application from SAP BTP. To launch copy the URL of application and use 'Incognito mode' of browser. Once you will launch application, your application will ask to choose Identity Provider you want to use. Depending upon your settings, you will have 'Default Identity Provider' and 'your IAS Tenant' as shown below

- Choose your IAS tenant to login
- When you click on it, if everything has been configured properly, IAS will delegate authentication to Azure AD B2C and you will be presented with a screen like this

- Here you will authenticate with your Azure AD B2C user. As this custom policy in Azure AD B2C which we used has 'Sign Up' and 'Sign In' flow. New users can sign up as well. This will create a new user in AD B2C tenant and will provide that user access to this application.
- As there is no authorisations setup so users will get access by default
Important Things if you are stuck:
- Make sure your settings in Azure AD B2C are correct and try to do testing locally in AD B2C and check JWT token claims in local testing(Azure AD B2C help documentation provides how to test and I have provided links above in this blog
- In SAP IAS make sure that Corporate Identity provider has correct values for Client ID and Client Secret!
I am sure there are other clever ways to achieve this, looking forward to comments/suggestions!!
- SAP Managed Tags:
- SAP Cloud Identity Services
Labels:
2 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
91 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
66 -
Expert
1 -
Expert Insights
177 -
Expert Insights
293 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
12 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
340 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
416 -
Workload Fluctuations
1
Related Content
- SAP IAS - Password Synchronisation with Active Directory in Technology Q&A
- Lowest SAP ECC version that can be integrated with SAP BTP through Cloud Connector in Technology Q&A
- how to read the name of groovy script sap cloud integration cpi in Technology Q&A
- How to host static webpages through SAP CPI-Iflow in Technology Blogs by Members
- How to use AI services to translate Picklists in SAP SuccessFactors - An example in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 31 | |
| 24 | |
| 8 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 5 | |
| 4 |