
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by Members
- SAP private linky swear with Azure – to WAF or not...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
This post is part of a series sharing service implementation experience and possible applications of SAP Private Link Service on Azure. Find the table of contents and my curated news regarding series updates here. Find the associated GitHub repos here. |
Dear community,
Continuing with the implementation journey of SAP Private Link Service (PLS) for Azure we will have a closer look at connecting privately to your Azure workloads via the Azure Application Gateway (App Gateway) using the Microsoft backbone. Why is this interesting?
First, the App Gateway offers a managed Web Application Firewall (WAF). Yes, you heard that correctly. From now on you may inspect 🧐 the https traffic coming from the shared tenant SAP BTP environment based on your needs. Compliance and Security anyone?
Second, the App Gateway simplifies your end-to-end setup regarding TLS compared to maintaining “Server Name Indicator” on your SAP Web Dispatcher or NetWeaver. You will see further down how much easier. Oh boy was I excited. Self-renewing certificate generated in Key Vault. Much wow!
Third, the App Gateway offers a managed way of addressing all your private virtual network integrated Azure workloads via https directly. And did I mention auto-scaling, high-availability, high-traffic support, and many more web app features?
Below architecture overview describes a typical OData scenario with the SAP Gateway. Customers link their BTP apps or SAP SaaS products like SuccessFactors, Cloud for Customer etc. with their backends using this pattern. SAP Cloud Integration offers the standard integration content for the required business logic.

Fig.1 Architecture overview
Additional popular fronting targets for the Azure App Gateway that enable further business cases are Azure API Management, Azure Storage Accounts, Azure App Service, Azure Functions, or Azure Kubernetes Service as ingress controller. These options extend the capabilities of the BTP hosted apps and services.
You may privately connect to the listed services individually without the App Gateway but at the expense of linking service-by-service and the WAF functionality. SAP maintains a guide by each target service. See also my aggregator blog post for additional context.

Which integration target do you require most? Let me know on the comments, so I can tailor the write up to be most relevant to you going forward.
Great listening skills are essential for any relationship – or how App Gateway is making sure everyone gets heard
To begin with, a private link needs to be configured for your App Gateway instance. I am describing the process for the WAF v2 tier. It might slightly differ for other SKUs.
🛈Note: A fully configured listener and routing rule need to be setup for the initial SAP Private Link approval process to work. A typical symptom of missing configuration is a failed create-status on BTP despite correct networking setup. |
Let’s get going: Add a private frontend IP configuration named “appGwPrivateFrontendIp” to your App Gateway and maintain a dedicated private IP for the link to target.
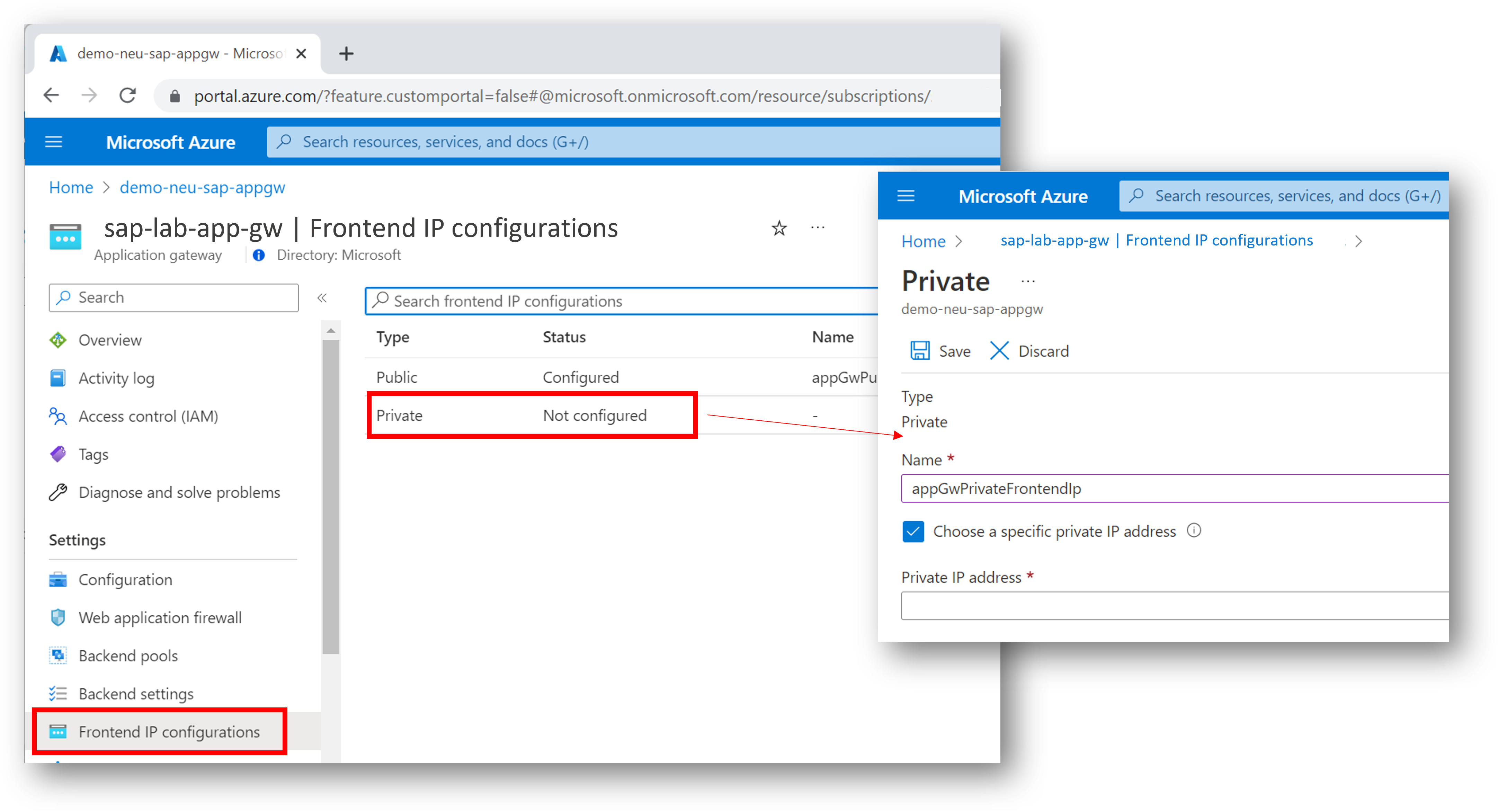
Fig.2 Screenshot of private Frontend IP configuration
Now, move on to the Private Link section and add a link with that new config and allocate one private IP address for BTP to target.

Fig.3 Screenshot of Private Link create experience
Next, copy your App Gateway’s resource ID, Frontend IP configuration name and supply them to the Private Link create wizard in SAP BTP to complete the linking process:

Fig.4 Illustration of SAP Private Link App Gateway create experience
If everything went to plan you will see a pending connect request with “hello from btp” on your App Gateway. Oh, look at that 😊

Fig.5 Illustration of SAP Private Link approval
Ok great, Link established. Don’t forget to bind at least one application on BTP to the service to generate your hostnames. You may use my example Java app to start with. Git clone it in Business Application Studio for instance, maintain your SAP Private Link instance name on the manifest.yaml, build the project and “cf push” it into your CloudFoundry space. Once the binding completes, retrieve your “short” hostname from the SAP Private Link service.
I suggest the shorter hostname for ease of maintenance regarding the trust certificates we are going to maintain in a bit and for dealing with multiple links. Have a look at this post in the series for staging and networking topology considerations.

Fig.6 Screenshot of SAP Private Link short host name retrieval for App Gateway
Since we now have a fully operational private link, let’s move on to the listening part on the App Gateway. You want to work with all those “hellos” from BTP after all, don’t you?
Oh shuuut, trust setup for end-to-end SSL!
Remember this incident from part 1 of the series? Poor broken pinky.

Fig.7 Illustration of need for trust setup between App Gateway and BTP destination
We are smarter this time!
Back in the day we needed to maintain the hostname on the responding service and select it for the host header for requests coming from SAP BTP. At that time, we did that with SNI and the SAP Web Dispatcher. Have a look at this post for reference. Today we have the mighty App Gateway 💪🏾🦸🏾♀️ to do all this for us in a managed way!
Well, App Gateway needs some contribution from Azure Key Vault. See here, how to obtain a well-known trusted certificate instead of self-signed.
⚠️Be aware that the self-signed leaf certificate approach requires some BTP apps to restart to reflect changed leaf certificates in the trust store⚠️

Fig.8 Illustration of trust setup in App Gateway for SAP Private Link short host name
Auto-renewal for the self-signed certificate!? NICE! As mentioned, before I am using wildcards and the shorter DNS name for ease of maintenance. Now every one of my SAP Private Links in the p1 rooster may talk to this App Gateway.
🛈Note: A self-signed certificate is not optimal. You may favor bringing your own domain and certificate as described by SAP here. Furthermore, you might desire trusting the root or intermediate certificate of your Certificate Authority in BTP. That way there is no need for populating the certificate at all. See here, how to create a certificate with a well-known certificate authority like DigiCert or GlobalSign automatically from Azure Key Vault. Azure App Gateway polls the certificates to check for new versions every 4 hours. ⚠️Be aware that the self-signed leaf certificate approach requires some BTP apps to restart to reflect changed leaf certificates in the trust store⚠️ |
Next, we need to allow our App Gateway to read that certificate from Key Vault. For that we require a user assigned managed identity. Follow the steps here to create one and remember its resource ID. Assign this new managed identity permissions to work with certificates and secrets on your Key Vault. Find the settings under Overview -> Access Policies -> Create. In my example I gave it full rights for certificates and Secrets.
Learn more about the authorization scope here.
Download the certificate to upload it later into your trust store on BTP Destination service. One way of exporting would be to navigate: Open your certificate -> Current Version -> Download in CER format. Unfortunately, the SAP trust store wants the certificate string surrounded by a certain string. Add it to your cert file like so:

-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----Now, open the Azure Cloud Shell and execute the following command to assign your managed identity to your App Gateway instance:
az network application-gateway identity assign --gateway-name sap-lab-app-gw -g your-resource-group-name --identity /subscriptions/00000-00000-0000-00000/resourceGroups/eun-saplab-rg/providers/Microsoft.ManagedIdentity/userAssignedIdentities/your-managed-identity-name
Fig.9 Screenshot of cloud shell command for App Gateway identity assignment
Ok great. At this point we can configure our listener on the App Gateway to use this self-signed certificate setup to trust requests from SAP BTP using the SAP Private Link hostname 😊

Fig.10 Screenshot of App Gateway listener setup with BTP trust
Remaining setup for the backend pool and backend settings works the same as before when we did this configuration exercise for the standard load balancer in part 1. Before introducing Azure API Management into the mix, let’s test the OData request via the Java app in BTP first 😊
Import self-renewing certificate into BTP Destination trust store
I am again assuming that you configured a Destination on BTP like described at the beginning of this blog series. In my example below I am referring to the Cloud Foundry destination service instance “az-destinations” and maintained my target like so:

Fig.11 Screenshot of App Gateway trust setup in BTP destination with trust store
And now hitting that destination from the Java app requesting the example OData service gets us… drum roll 🥁 …

Heavy scrolling to finally the see the output. The suspension is killing me…
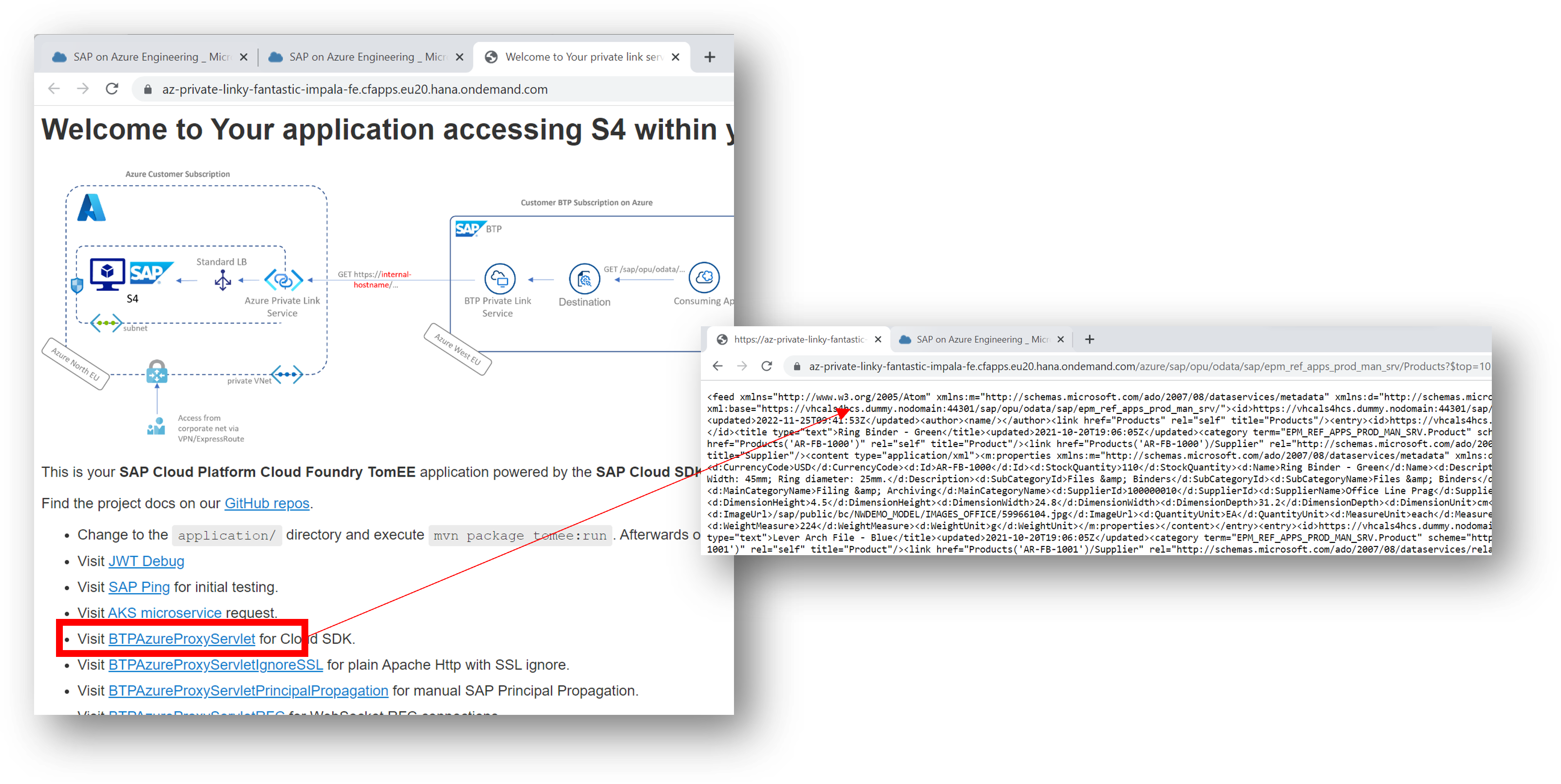
Fig.12 Screenshot of successful private OData response via App Gateway and SAP Private Link
Eureka! 🥳 🤸🏼♀️ marvel at the nicely printed and well readable OData response. But hey, the integration is working.
For a fully automatic process regarding the self-signed certificate lifecycle, you still need to orchestrate the import into the BTP Destination trust store. Use the Destination Service (Cloud Foundry) API for the import on the BTP side. For the trigger Azure Key Vault offers the events “NearExpiry” and “CertificateNewVersionCreated” exposed to the Azure Event Grid, that can be fed to a web hook or Azure Integration Services. A typical pattern would be to connect that with an Azure Logic App or any compute on the SAP BTP side.
Have a look at this blog to learn more about the automation part. Sneak peak: certificates issued by well-known certificate authorities drop the need for automation entirely. Also there is no risk of downtime for the BTP apps compared to the self-signed certificates rotating.
🛈Note: With certificates issued by a Certificate Authority like DigiCert you may consider trusting the intermediate or root certificate. That way you rotate the certificate in Azure but don’t need populate the renewed certificate to the BTP trust store. Instead bring your own domain as described by SAP here and create your certificate with a well-known provider like so with Azure Key Vault. |
If you are happy with this direct API connection from BTP to your SAP backend, you may stop at this point. But what about that nasty colleague creating an app that hits your backend with this viciously powerful load testing app during financial closing?

Source: makeameme.org
I would highly encourage to consider request throttling, usage quotas and uniform governance with API Management on top. And to be clear there are more reasons to apply request throttling, than restricting load tests. Black Friday anyone? 😉
Inject API Management to mediate between the SAP BTP apps and your target workload on Azure
Since fronting Azure APIM with App Gateway privately with virtual network integration is a standard pattern, its configuration is being discussed widely as part of the standard Microsoft docs as well as by various blog posts. I’d like to mention these two sources that I found comprehensive to finish the setup:
- Use API Management in a virtual network with Azure Application Gateway - Azure API Management | Micr...
- Azure API Management and Application Gateway integration | by Andrew Kelleher | Azure Architects | M...

Fig.13 Architecture overview with API Management taking care of your private SAP APIs
More scenarios for the App Gateway with SAP Private Link
In general, any service targeted via https can be fronted with the App Gateway and therefore with SAP Private Link 😊 For instance, another popular application of this private integration pattern would be the Azure Blob storage, Azure Data Lake or Azure Kubernetes Service. See this blog post to learn more about the setup for the mentioned storage services.
Thoughts on production readiness
SAP Private Link is generally available and therefore completely ready for prime time (quoting gowrisankar.m2 from the SAP engineering team 😊).
Since Application Gateway configuration changes impact the routing setup it is recommended to have two instances per workload. One for production purposes and for non-production where changes can be applied and tested prior move to production.
The Azure Application Gateway powers and secures high traffic applications running on Azure globally. Furthermore, it is a standard solution fronting SAP Fiori, SAP PI/PO etc. Have a look here for reference.
The Web Application Firewall (WAF) allows inspection of your incoming traffic from BTP based on the industry standard OWASP rules. Learn more about WAF for SAP on our YouTube session🎥.
API Management ensures governance, security, and usage guard rails of the private link exposed APIs.
The use of self-signed certificates is not optimal. See this SAP docs entry to learn how to bring your own domain and certificate for SAP Private Link. Use Azure Key Vault to create a certificate with one of the well-known certificate authorities (CA) or with your own CA. Azure App Gateway automatically pulls from your Key Vault every 4 hours to check for new versions. When trusting the root or intermediate certificates of your CA, there is no need to populate renewed certificates to BTP.
⚠️Be aware that the self-signed leaf certificate approach requires some BTP apps to restart to reflect changed leaf certificates in the trust store⚠️avoid downtimes with well-known certificates.
Find additional details about Private Link and App Gateway see the Microsoft docs.
Final Words
So, what do you say? Will you be “WAF-ing” 🐶 with me and apply Application Gateway with SAP Private Link for your BTP integration scenarios?
SAP BTP as a multi-tenant shared service and Platform-as-a-Service offering runs on the public Internet by design. Hence, inspecting traffic originating from there sounds like a good idea. Do you agree?
You saw today how SAP Private Link combined with the Azure Application Gateway can securely connect to various of your Azure workloads to enrich your apps on BTP. In addition to that you learnt about the benefits of adding API Management to the mix and how to configure it.
The Application Gateway further simplifies the configuration if multiple Azure services in the customer subscription are involved, because they can be “bundled” into the Application Gateway rather than exposing them one by one individually to BTP via SAP Private Link.
Cherry on the cake🍰: automated certificate renewal bringing down your maintenance efforts 😊
Any comments regarding your integration journey with SAP Private Link SAP @Developers and @Architects?
The next part of the blog series discusses connecting Azure storage PaaS solutions like MySQL via PLS.
Find the related GitHub repos here.
Find your way back to the aggregator blog post here.
#Kudos to Christof Claessens and Vinod Deshmukh for speeding me up in the prototyping big time!
As always feel free to ask lots of follow-up questions.
Best Regards
Martin
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
"automatische backups"
1 -
"regelmäßige sicherung"
1 -
"TypeScript" "Development" "FeedBack"
1 -
505 Technology Updates 53
1 -
ABAP
14 -
ABAP API
1 -
ABAP CDS Views
2 -
ABAP CDS Views - BW Extraction
1 -
ABAP CDS Views - CDC (Change Data Capture)
1 -
ABAP class
2 -
ABAP Cloud
2 -
ABAP Development
5 -
ABAP in Eclipse
1 -
ABAP Platform Trial
1 -
ABAP Programming
2 -
abap technical
1 -
absl
2 -
access data from SAP Datasphere directly from Snowflake
1 -
Access data from SAP datasphere to Qliksense
1 -
Accrual
1 -
action
1 -
adapter modules
1 -
Addon
1 -
Adobe Document Services
1 -
ADS
1 -
ADS Config
1 -
ADS with ABAP
1 -
ADS with Java
1 -
ADT
2 -
Advance Shipping and Receiving
1 -
Advanced Event Mesh
3 -
AEM
1 -
AI
7 -
AI Launchpad
1 -
AI Projects
1 -
AIML
9 -
Alert in Sap analytical cloud
1 -
Amazon S3
1 -
Analytical Dataset
1 -
Analytical Model
1 -
Analytics
1 -
Analyze Workload Data
1 -
annotations
1 -
API
1 -
API and Integration
3 -
API Call
2 -
Application Architecture
1 -
Application Development
5 -
Application Development for SAP HANA Cloud
3 -
Applications and Business Processes (AP)
1 -
Artificial Intelligence
1 -
Artificial Intelligence (AI)
5 -
Artificial Intelligence (AI) 1 Business Trends 363 Business Trends 8 Digital Transformation with Cloud ERP (DT) 1 Event Information 462 Event Information 15 Expert Insights 114 Expert Insights 76 Life at SAP 418 Life at SAP 1 Product Updates 4
1 -
Artificial Intelligence (AI) blockchain Data & Analytics
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise Oil Gas IoT Exploration Production
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise sustainability responsibility esg social compliance cybersecurity risk
1 -
ASE
1 -
ASR
2 -
ASUG
1 -
Attachments
1 -
Authorisations
1 -
Automating Processes
1 -
Automation
2 -
aws
2 -
Azure
1 -
Azure AI Studio
1 -
B2B Integration
1 -
Backorder Processing
1 -
Backup
1 -
Backup and Recovery
1 -
Backup schedule
1 -
BADI_MATERIAL_CHECK error message
1 -
Bank
1 -
BAS
1 -
basis
2 -
Basis Monitoring & Tcodes with Key notes
2 -
Batch Management
1 -
BDC
1 -
Best Practice
1 -
bitcoin
1 -
Blockchain
3 -
bodl
1 -
BOP in aATP
1 -
BOP Segments
1 -
BOP Strategies
1 -
BOP Variant
1 -
BPC
1 -
BPC LIVE
1 -
BTP
12 -
BTP Destination
2 -
Business AI
1 -
Business and IT Integration
1 -
Business application stu
1 -
Business Application Studio
1 -
Business Architecture
1 -
Business Communication Services
1 -
Business Continuity
1 -
Business Data Fabric
3 -
Business Partner
12 -
Business Partner Master Data
10 -
Business Technology Platform
2 -
Business Trends
4 -
CA
1 -
calculation view
1 -
CAP
3 -
Capgemini
1 -
CAPM
1 -
Catalyst for Efficiency: Revolutionizing SAP Integration Suite with Artificial Intelligence (AI) and
1 -
CCMS
2 -
CDQ
12 -
CDS
2 -
Cental Finance
1 -
Certificates
1 -
CFL
1 -
Change Management
1 -
chatbot
1 -
chatgpt
3 -
CL_SALV_TABLE
2 -
Class Runner
1 -
Classrunner
1 -
Cloud ALM Monitoring
1 -
Cloud ALM Operations
1 -
cloud connector
1 -
Cloud Extensibility
1 -
Cloud Foundry
4 -
Cloud Integration
6 -
Cloud Platform Integration
2 -
cloudalm
1 -
communication
1 -
Compensation Information Management
1 -
Compensation Management
1 -
Compliance
1 -
Compound Employee API
1 -
Configuration
1 -
Connectors
1 -
Consolidation Extension for SAP Analytics Cloud
2 -
Control Indicators.
1 -
Controller-Service-Repository pattern
1 -
Conversion
1 -
Cosine similarity
1 -
cryptocurrency
1 -
CSI
1 -
ctms
1 -
Custom chatbot
3 -
Custom Destination Service
1 -
custom fields
1 -
Customer Experience
1 -
Customer Journey
1 -
Customizing
1 -
cyber security
3 -
cybersecurity
1 -
Data
1 -
Data & Analytics
1 -
Data Aging
1 -
Data Analytics
2 -
Data and Analytics (DA)
1 -
Data Archiving
1 -
Data Back-up
1 -
Data Flow
1 -
Data Governance
5 -
Data Integration
2 -
Data Quality
12 -
Data Quality Management
12 -
Data Synchronization
1 -
data transfer
1 -
Data Unleashed
1 -
Data Value
8 -
database tables
1 -
Datasphere
3 -
datenbanksicherung
1 -
dba cockpit
1 -
dbacockpit
1 -
Debugging
2 -
Delimiting Pay Components
1 -
Delta Integrations
1 -
Destination
3 -
Destination Service
1 -
Developer extensibility
1 -
Developing with SAP Integration Suite
1 -
Devops
1 -
digital transformation
1 -
Documentation
1 -
Dot Product
1 -
DQM
1 -
dump database
1 -
dump transaction
1 -
e-Invoice
1 -
E4H Conversion
1 -
Eclipse ADT ABAP Development Tools
2 -
edoc
1 -
edocument
1 -
ELA
1 -
Embedded Consolidation
1 -
Embedding
1 -
Embeddings
1 -
Employee Central
1 -
Employee Central Payroll
1 -
Employee Central Time Off
1 -
Employee Information
1 -
Employee Rehires
1 -
Enable Now
1 -
Enable now manager
1 -
endpoint
1 -
Enhancement Request
1 -
Enterprise Architecture
1 -
ETL Business Analytics with SAP Signavio
1 -
Euclidean distance
1 -
Event Dates
1 -
Event Driven Architecture
1 -
Event Mesh
2 -
Event Reason
1 -
EventBasedIntegration
1 -
EWM
1 -
EWM Outbound configuration
1 -
EWM-TM-Integration
1 -
Existing Event Changes
1 -
Expand
1 -
Expert
2 -
Expert Insights
2 -
Exploits
1 -
Fiori
14 -
Fiori Elements
2 -
Fiori SAPUI5
12 -
Flask
1 -
Full Stack
8 -
Funds Management
1 -
General
1 -
General Splitter
1 -
Generative AI
1 -
Getting Started
1 -
GitHub
8 -
Grants Management
1 -
GraphQL
1 -
groovy
1 -
GTP
1 -
HANA
6 -
HANA Cloud
2 -
Hana Cloud Database Integration
2 -
HANA DB
2 -
HANA XS Advanced
1 -
Historical Events
1 -
home labs
1 -
HowTo
1 -
HR Data Management
1 -
html5
8 -
HTML5 Application
1 -
Identity cards validation
1 -
idm
1 -
Implementation
1 -
input parameter
1 -
instant payments
1 -
Integration
3 -
Integration Advisor
1 -
Integration Architecture
1 -
Integration Center
1 -
Integration Suite
1 -
intelligent enterprise
1 -
iot
1 -
Java
1 -
job
1 -
Job Information Changes
1 -
Job-Related Events
1 -
Job_Event_Information
1 -
joule
4 -
Journal Entries
1 -
Just Ask
1 -
Kerberos for ABAP
8 -
Kerberos for JAVA
8 -
KNN
1 -
Launch Wizard
1 -
Learning Content
2 -
Life at SAP
5 -
lightning
1 -
Linear Regression SAP HANA Cloud
1 -
Loading Indicator
1 -
local tax regulations
1 -
LP
1 -
Machine Learning
2 -
Marketing
1 -
Master Data
3 -
Master Data Management
14 -
Maxdb
2 -
MDG
1 -
MDGM
1 -
MDM
1 -
Message box.
1 -
Messages on RF Device
1 -
Microservices Architecture
1 -
Microsoft Universal Print
1 -
Middleware Solutions
1 -
Migration
5 -
ML Model Development
1 -
Modeling in SAP HANA Cloud
8 -
Monitoring
3 -
MTA
1 -
Multi-Record Scenarios
1 -
Multiple Event Triggers
1 -
Myself Transformation
1 -
Neo
1 -
New Event Creation
1 -
New Feature
1 -
Newcomer
1 -
NodeJS
2 -
ODATA
2 -
OData APIs
1 -
odatav2
1 -
ODATAV4
1 -
ODBC
1 -
ODBC Connection
1 -
Onpremise
1 -
open source
2 -
OpenAI API
1 -
Oracle
1 -
PaPM
1 -
PaPM Dynamic Data Copy through Writer function
1 -
PaPM Remote Call
1 -
PAS-C01
1 -
Pay Component Management
1 -
PGP
1 -
Pickle
1 -
PLANNING ARCHITECTURE
1 -
Popup in Sap analytical cloud
1 -
PostgrSQL
1 -
POSTMAN
1 -
Process Automation
2 -
Product Updates
4 -
PSM
1 -
Public Cloud
1 -
Python
4 -
python library - Document information extraction service
1 -
Qlik
1 -
Qualtrics
1 -
RAP
3 -
RAP BO
2 -
Record Deletion
1 -
Recovery
1 -
recurring payments
1 -
redeply
1 -
Release
1 -
Remote Consumption Model
1 -
Replication Flows
1 -
research
1 -
Resilience
1 -
REST
1 -
REST API
2 -
Retagging Required
1 -
Risk
1 -
Rolling Kernel Switch
1 -
route
1 -
rules
1 -
S4 HANA
1 -
S4 HANA Cloud
1 -
S4 HANA On-Premise
1 -
S4HANA
3 -
S4HANA_OP_2023
2 -
SAC
10 -
SAC PLANNING
9 -
SAP
4 -
SAP ABAP
1 -
SAP Advanced Event Mesh
1 -
SAP AI Core
8 -
SAP AI Launchpad
8 -
SAP Analytic Cloud Compass
1 -
Sap Analytical Cloud
1 -
SAP Analytics Cloud
4 -
SAP Analytics Cloud for Consolidation
3 -
SAP Analytics Cloud Story
1 -
SAP analytics clouds
1 -
SAP BAS
1 -
SAP Basis
6 -
SAP BODS
1 -
SAP BODS certification.
1 -
SAP BTP
21 -
SAP BTP Build Work Zone
2 -
SAP BTP Cloud Foundry
6 -
SAP BTP Costing
1 -
SAP BTP CTMS
1 -
SAP BTP Innovation
1 -
SAP BTP Migration Tool
1 -
SAP BTP SDK IOS
1 -
SAP Build
11 -
SAP Build App
1 -
SAP Build apps
1 -
SAP Build CodeJam
1 -
SAP Build Process Automation
3 -
SAP Build work zone
10 -
SAP Business Objects Platform
1 -
SAP Business Technology
2 -
SAP Business Technology Platform (XP)
1 -
sap bw
1 -
SAP CAP
2 -
SAP CDC
1 -
SAP CDP
1 -
SAP CDS VIEW
1 -
SAP Certification
1 -
SAP Cloud ALM
4 -
SAP Cloud Application Programming Model
1 -
SAP Cloud Integration for Data Services
1 -
SAP cloud platform
8 -
SAP Companion
1 -
SAP CPI
3 -
SAP CPI (Cloud Platform Integration)
2 -
SAP CPI Discover tab
1 -
sap credential store
1 -
SAP Customer Data Cloud
1 -
SAP Customer Data Platform
1 -
SAP Data Intelligence
1 -
SAP Data Migration in Retail Industry
1 -
SAP Data Services
1 -
SAP DATABASE
1 -
SAP Dataspher to Non SAP BI tools
1 -
SAP Datasphere
9 -
SAP DRC
1 -
SAP EWM
1 -
SAP Fiori
3 -
SAP Fiori App Embedding
1 -
Sap Fiori Extension Project Using BAS
1 -
SAP GRC
1 -
SAP HANA
1 -
SAP HCM (Human Capital Management)
1 -
SAP HR Solutions
1 -
SAP IDM
1 -
SAP Integration Suite
9 -
SAP Integrations
4 -
SAP iRPA
2 -
SAP LAGGING AND SLOW
1 -
SAP Learning Class
1 -
SAP Learning Hub
1 -
SAP Master Data
1 -
SAP Odata
2 -
SAP on Azure
1 -
SAP PartnerEdge
1 -
sap partners
1 -
SAP Password Reset
1 -
SAP PO Migration
1 -
SAP Prepackaged Content
1 -
SAP Process Automation
2 -
SAP Process Integration
2 -
SAP Process Orchestration
1 -
SAP S4HANA
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Cloud for Finance
1 -
SAP S4HANA Cloud private edition
1 -
SAP Sandbox
1 -
SAP STMS
1 -
SAP successfactors
3 -
SAP SuccessFactors HXM Core
1 -
SAP Time
1 -
SAP TM
2 -
SAP Trading Partner Management
1 -
SAP UI5
1 -
SAP Upgrade
1 -
SAP Utilities
1 -
SAP-GUI
8 -
SAP_COM_0276
1 -
SAPBTP
1 -
SAPCPI
1 -
SAPEWM
1 -
sapmentors
1 -
saponaws
2 -
SAPS4HANA
1 -
SAPUI5
5 -
schedule
1 -
Script Operator
1 -
Secure Login Client Setup
8 -
security
9 -
Selenium Testing
1 -
Self Transformation
1 -
Self-Transformation
1 -
SEN
1 -
SEN Manager
1 -
service
1 -
SET_CELL_TYPE
1 -
SET_CELL_TYPE_COLUMN
1 -
SFTP scenario
2 -
Simplex
1 -
Single Sign On
8 -
Singlesource
1 -
SKLearn
1 -
Slow loading
1 -
soap
1 -
Software Development
1 -
SOLMAN
1 -
solman 7.2
2 -
Solution Manager
3 -
sp_dumpdb
1 -
sp_dumptrans
1 -
SQL
1 -
sql script
1 -
SSL
8 -
SSO
8 -
Substring function
1 -
SuccessFactors
1 -
SuccessFactors Platform
1 -
SuccessFactors Time Tracking
1 -
Sybase
1 -
system copy method
1 -
System owner
1 -
Table splitting
1 -
Tax Integration
1 -
Technical article
1 -
Technical articles
1 -
Technology Updates
14 -
Technology Updates
1 -
Technology_Updates
1 -
terraform
1 -
Threats
2 -
Time Collectors
1 -
Time Off
2 -
Time Sheet
1 -
Time Sheet SAP SuccessFactors Time Tracking
1 -
Tips and tricks
2 -
toggle button
1 -
Tools
1 -
Trainings & Certifications
1 -
Transformation Flow
1 -
Transport in SAP BODS
1 -
Transport Management
1 -
TypeScript
2 -
ui designer
1 -
unbind
1 -
Unified Customer Profile
1 -
UPB
1 -
Use of Parameters for Data Copy in PaPM
1 -
User Unlock
1 -
VA02
1 -
Validations
1 -
Vector Database
2 -
Vector Engine
1 -
Visual Studio Code
1 -
VSCode
1 -
Vulnerabilities
1 -
Web SDK
1 -
work zone
1 -
workload
1 -
xsa
1 -
XSA Refresh
1
- « Previous
- Next »
- Configuring SAP CI/CD pipeline for Deploying ReactJS application in Cloud Foundry in Technology Q&A
- SAP Build Process Automation Pre-built content for Finance Use cases in Technology Blogs by SAP
- How to improve the ADT Class Runner with additional Features in Technology Blogs by Members
- Recommended approach for Fiori Adapt UI in S/4H On-Premise system (Customizing client) with no data in Technology Q&A
- fuzzy search with multiple name fields in Technology Q&A
| User | Count |
|---|---|
| 8 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 | |
| 4 | |
| 3 | |
| 3 |