
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Cryptography: Language of security
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content

Formulas are a powerful tool and a core part of AppGyver’s functionality. With an intuitive approach, you can perform any transformation with relevant data such as the device and system info, GPS location, sensor values, data properties and the application state.
In one of the recent updates, we have powered formulas with cryptography, enabling essential security features for your applications. You can encrypt all user data via the new six hashing functions.
Introduction to cryptography
Cryptography uses mathematical techniques to transform data and prevent it from being read or tampered with by unauthorized parties. That enables exchanging secure messages even in the presence of adversaries.
Nowadays, cryptography is an essential part of our day-to-day operations that facilitates strong, trusted standards and guidelines for data exchange. It is most commonly used in the following areas:
Authentication
Through the use of cryptography, it is made sure that data is not changed while being stored or while being sent from one party to another. In other words, while developing an app with SAP AppGyver, you can protect your user’s data during the application-to-server transfer, as well as while keeping it in the backend.
Privacy
From simple message cyphering to using virtual private networks, cryptography can provide day to day solutions for personal and enterprise privacy.
Hashing
Cryptography Formulas in SAP AppGyver are implemented in a form of hashing. It is a process of modifying raw data until it can no longer be reproduced in its original form. It takes a piece of data and runs it through a hash function that manipulates the plaintext numerically. You can see a graphical representation in the image below. Notice how "User's secret password" can only be modified in one direction.
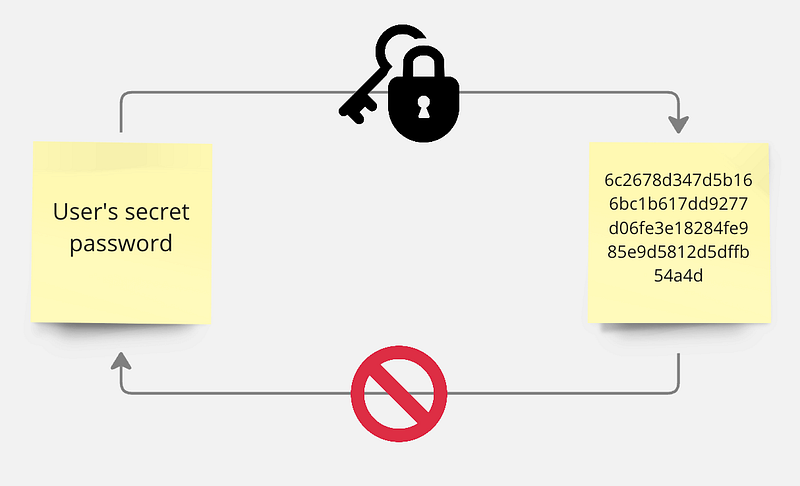
To implement hashing in your application and protect your users from data leakage, convert all passwords into a hash value before sending them to a server. Additionally, store hash values, rather than plaintext passwords, and compare the received hash for password validation.
Formula functions overview
KECCAK
Keccak or SHA-3 is the latest generation secure hashing algorithm released by NIST. On August 5, 2015, NIST announced that SHA-3 had become a hashing standard. In other words, it is the fastest and most secure option.
As a formula function, KECCAK accepts two inputs: text and a number of bits. That number can be 224, 256, 384 or 512. A higher bit number results in a larger output.
KECCAK(“Security is key”, 256)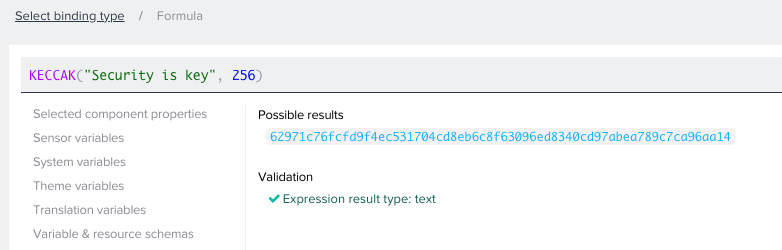
MD5
MD5 is a cryptographically broken, but still widely used 128-bit hash function. It is vulnerable by design, so it is best to avoid using it for sensitive data. It is most commonly used to check file integrity. MD5 file hashes before and after data transfer are compared to detect corruption.
MD5("Hide this")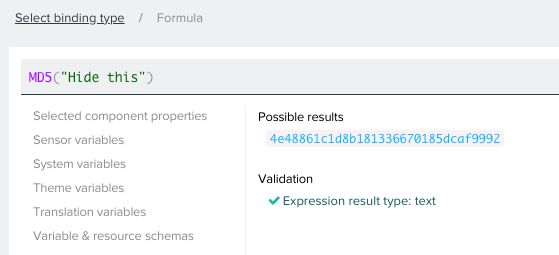
RIPEMD160
RIPEMD-160 is a cryptographic hash function based upon the Merkle–Damgård construction, which is a method of building collision-resistant cryptographic hash functions. It produces a 160-bit output, and is considered secure.
The most popular RIPEMD-160’s use case is Bitcoin.
RIPEMD160("My data is safe")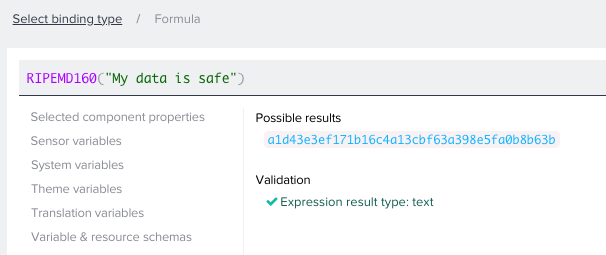
SHA1
Similarly to MD5, SHA1 is a cryptographically broken function. NIST formally deprecated use of SHA-1 in 2011 and disallowed its use for digital signatures in 2013. Despite that, SHA1 is still used in low-security use cases.
SHA1("Hack this hash")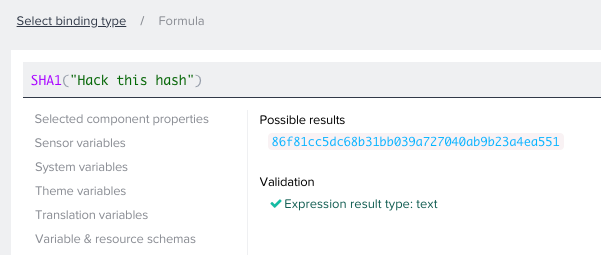
SHA256 & SHA512
Unlike their predecessor SHA1, SHA256 and SHA512 were designed using a one-way compression function, making them secure by design. SHA-2 functions are the industry standards for cryptography, used by the U.S. federal government and many other organizations globally.
256 and 512 represent the returned number of bits, respectively.
SHA256("Protect the users, not business")
SHA512("Information is the most valuable asset")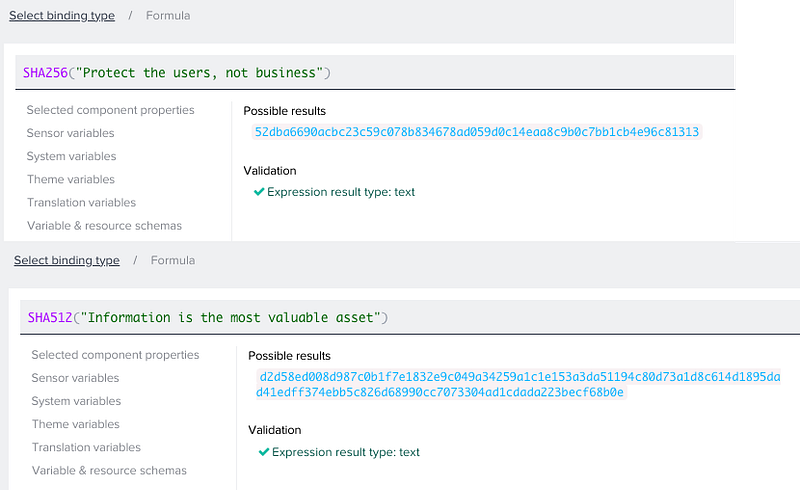
Final words
With our rapidly changing world, it is important to be up-to-date with tech standards and ensure that your client’s data is safe. Consider using the new cryptography formulas next time you use SAP AppGyver!
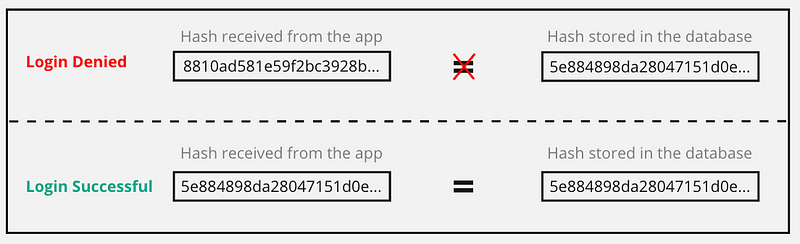
The image below should give you an idea, on how easy it is to enable security for your users - just hash the password.

👉 Let us know what you think about the new formulas!
Bibliography:
- NIST
- Wikipedia
- Fortinet
- SAP Managed Tags:
- SAP Build Apps,
- SAP Business Technology Platform
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
85 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
64 -
Expert
1 -
Expert Insights
178 -
Expert Insights
269 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
10 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,578 -
Product Updates
317 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
389 -
Workload Fluctuations
1
- Adobe Forms SFP: Caption from ABAP dictionary in Technology Q&A
- How to build SOAP service in SAP Cloud Integration in Technology Blogs by Members
- Consuming CAPM Application's OData service into SAP Fiori Application in Business Application Studio in Technology Blogs by Members
- Data Flows - The Python Script Operator and why you should avoid it in Technology Blogs by Members
- Experiencing Embeddings with the First Baby Step in Technology Blogs by Members
| User | Count |
|---|---|
| 12 | |
| 11 | |
| 11 | |
| 9 | |
| 9 | |
| 9 | |
| 9 | |
| 8 | |
| 7 | |
| 7 |