
- SAP Community
- Products and Technology
- Enterprise Resource Planning
- ERP Blogs by SAP
- Domain Certificate Renewal (*businessbydesign.clou...
Enterprise Resource Planning Blogs by SAP
Get insights and updates about cloud ERP and RISE with SAP, SAP S/4HANA and SAP S/4HANA Cloud, and more enterprise management capabilities with SAP blog posts.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
hridesh
Explorer
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
10-17-2022
6:05 PM
Background
The existing server certificate for domain *businessbydesign.cloud.sap and *sapbydesign.com will be renewed as it is going to expire on 03rd December, 2022.
Scope
You will be affected if either of the below scenarios are applicable to you:
Impact
If you have third party integrations like web services/APIs in your Business ByDesign tenant, you may be required to update the domain certificate. These updates should be conducted by your internal IT resources, with the new certificate information that could be found below.
Download new certificate
Below are the steps to download new certificate:
FAQs
1) What are these certificates used for?
These certificates are used for the SSL/TLS handshake that any system using the ‘secure’ protocol does before allowing connection to/from the system. In our case, SAP Business ByDesign uses the ‘secure’ HTTPS protocol and hence the SSL handshake is must for any system to connect to these URLs.
2) Are the new certificates known to modern web browsers?
DigiCert Root Certificates are automatically recognized by all common web browsers, mobile devices, and mail clients, therefore for browser scenarios there is nothing to do. The same is true if one relies on the standard sapjvm trust list.
The CA root certificate is included in:
3) How do I download or install the certificate?
You must have admin access to the server where you need to install the certificate. If you do not have access to your company’s SSL server, notify your IT team and provide them the respective certificate download link from the above table.
4) How do Import Single Certificate in SAP CPI Key Store?
Follow the steps mentioned in the link.
5) How to check the certificate in my browser trust list?
Navigate to chrome://settings and scroll down to ‘Advanced’.
6) How to import the certificate into my browser?
Procedure
7) I notice a discrepancy in the validity start date and end date mentioned in this knowledge article table and my downloaded certificate. What does this indicate?
Sometimes, due to time zone difference, you may see a different date in the downloaded certificate. There is no impact on the certificate update activity due to this. You will be renewing the certificate well in advance, before the certificate expiry date.
Please do share feedback and your thoughts in the comment section below.
You can also refer SAP Business ByDesign environment Topic page (https://community.sap.com/topics/business-bydesign), post and answer questions (https://answers.sap.com/tags/01200615320800000691), and read other posts on the topic (https://blogs.sap.com/tags/01200615320800000691/).
The existing server certificate for domain *businessbydesign.cloud.sap and *sapbydesign.com will be renewed as it is going to expire on 03rd December, 2022.
Scope
You will be affected if either of the below scenarios are applicable to you:
- Your browser does not have DigiCert Certificates.
- You have an inbound/outbound communication integration to your Byd product.
Impact
If you have third party integrations like web services/APIs in your Business ByDesign tenant, you may be required to update the domain certificate. These updates should be conducted by your internal IT resources, with the new certificate information that could be found below.
Download new certificate
Below are the steps to download new certificate:
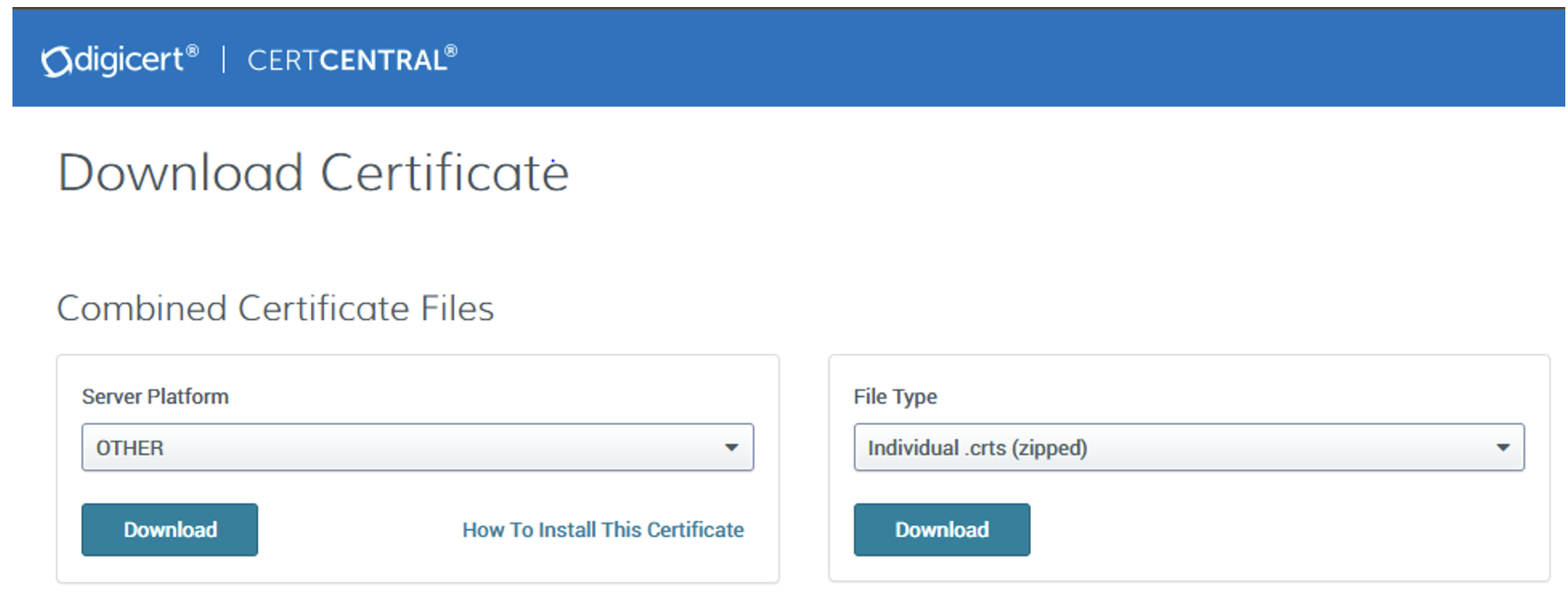
- Kindly click on download link. You will be redirected to Digi Cert Website, here ensure Combined Certificate Files is set as shown below.

- Click download as shown below.

- A zip file by name: star_businessbydesign_cloud_sap_278466338 would be downloaded.
- Please unzip this file and we can see required certificate: star_businessbydesign_cloud_sap.crt.

FAQs
1) What are these certificates used for?
These certificates are used for the SSL/TLS handshake that any system using the ‘secure’ protocol does before allowing connection to/from the system. In our case, SAP Business ByDesign uses the ‘secure’ HTTPS protocol and hence the SSL handshake is must for any system to connect to these URLs.
2) Are the new certificates known to modern web browsers?
DigiCert Root Certificates are automatically recognized by all common web browsers, mobile devices, and mail clients, therefore for browser scenarios there is nothing to do. The same is true if one relies on the standard sapjvm trust list.
The CA root certificate is included in:
- SAP JVM patch level 8.1.035 or 7.1.054
- Cloud Foundry buildpack SAP-Java (sap_java_buildpack) version 1.6.15
3) How do I download or install the certificate?
You must have admin access to the server where you need to install the certificate. If you do not have access to your company’s SSL server, notify your IT team and provide them the respective certificate download link from the above table.
4) How do Import Single Certificate in SAP CPI Key Store?
Follow the steps mentioned in the link.
5) How to check the certificate in my browser trust list?
Navigate to chrome://settings and scroll down to ‘Advanced’.
- Under “Privacy and Security,” click “Manage Certificates.”
- On the popup that was launched, select “Trusted Root Certification Authorities’. The certificate will be displayed there.
6) How to import the certificate into my browser?
Procedure
- Open the browser.
- Click Customize and control Google Chrome button in the upper right corner.
- Choose Settings. …
- Under Privacy and security section, click More. …
- Click Manage certificates, The new window will appear. …
- Choose Trusted Root Certification Authorities tab.
- Click Import. …
- In the opened window, click Next
7) I notice a discrepancy in the validity start date and end date mentioned in this knowledge article table and my downloaded certificate. What does this indicate?
Sometimes, due to time zone difference, you may see a different date in the downloaded certificate. There is no impact on the certificate update activity due to this. You will be renewing the certificate well in advance, before the certificate expiry date.
Please do share feedback and your thoughts in the comment section below.
You can also refer SAP Business ByDesign environment Topic page (https://community.sap.com/topics/business-bydesign), post and answer questions (https://answers.sap.com/tags/01200615320800000691), and read other posts on the topic (https://blogs.sap.com/tags/01200615320800000691/).
- SAP Managed Tags:
- SAP Business ByDesign
Labels:
12 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
Artificial Intelligence (AI)
1 -
Business Trends
363 -
Business Trends
21 -
Customer COE Basics and Fundamentals
1 -
Digital Transformation with Cloud ERP (DT)
1 -
Event Information
461 -
Event Information
24 -
Expert Insights
114 -
Expert Insights
152 -
General
1 -
Governance and Organization
1 -
Introduction
1 -
Life at SAP
415 -
Life at SAP
2 -
Product Updates
4,685 -
Product Updates
208 -
Roadmap and Strategy
1 -
Technology Updates
1,502 -
Technology Updates
88
Related Content
- SAP S/4HANA Cloud Public Edition: Security Configuration APIs in Enterprise Resource Planning Blogs by SAP
- What You Need to Know: Security and Compliance when Moving to a Cloud ERP Solution in Enterprise Resource Planning Blogs by SAP
- Print customer specific inspection plan results on Outbound Certificate of Analysis in SAP QM in Enterprise Resource Planning Q&A
- How enter the MSME CERTIFICATE NUMBER on vendor master? in Enterprise Resource Planning Q&A
- Beyond Basic (2): Certificate-Based Authentication in SAP S/4HANA Cloud Public Edition in Enterprise Resource Planning Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 8 | |
| 6 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 |