
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Opening the Black Box
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Product and Topic Expert
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
09-15-2022
11:52 AM
SAP Application Security Monitoring.
In a perfect world all of this would not happen, but today CISOs are sometimes surprised when their business applications are compromised and the company loses data or business is affected by data manipulation or manipulation of business processes.
The number of targeted cyber attacks on SAP business applications is strongly increasing. A successful attack on business applications most often compromises the confidentiality and integrity of the business application. This frequently goes unnoticed for a long period of time and can have serious consequences for the organization.

How this can happen & what can be the consequences.
Over 80% of breaches within hacking involved brute force or the use of lost and stolen credentials.
The misuse of such stolen identities cannot always be detected by an organization’s perimeter security. That makes it easy for hackers to stay underneath the radar and makes it difficult for the security operation to detect such attacks.
In 2020, The data breach life cycle of a malicious or criminal attack took an average of 315 days. In such a sophisticated and persistent cyber attack it's not the target to cause a denial of service, get a ransom payment and walk away with that. It is to stay! Stay undetected as long as possible and maximize the impact on the organization or maximize the profit out of the attack. Such an attack is not only about simple data theft of company IP, PII data, customer and partner information, or employee data, which should already ring everybody’s alarm bell. It's also about manipulation of documents in simple fraud cases as well as changes in business documents such as order quantities or payments, manipulation of documents in the financial books, such as tax information, vendor and customer information, or location information. This kind of manipulation can lead to an incorrect financial statement of an organization, loss of investor trust or even market leadership, regulatory fines or other legal penalties.
“Cybersecurity failure” is one of the risks that worsened the most through COVID-19.
There is still a cybersecurity workforce gap of more than 2.72 million positions worldwide.

picture 1
The World Economic Forum’s 2020 Global Risk Report states that the rate of detection is as low as 0....
This means that most of the cyber attacks remain unnoticed, giving hackers plenty of time to explore the landscape and to obtain the data they are looking for. A slow response to a data breach can cause even more trouble for your organization, resulting in a loss of customer trust, productivity, or regulatory fines.
To help customers detect threats in their business applications we have developed SAP Enterprise Threat Detection, cloud edition.
What is SAP Enterprise Threat Detection, cloud edition.
Definition
SAP Enterprise Threat Detection provides transparency about suspicious (user) behavior and anomalies in SAP business applications to identify and stop security breaches in real time.
Objective
SAP Enterprise Threat Detection uses highly efficient and automated processes based on HANA technology and machine learning to track hacker activity using SAP's predefined and easily customizable attack detection patterns.
The solution runs patterns and applies algorithms and statistical analysis to detect meaningful anomalies related to suspicious (user) events, correlates events, even over time, and detects anomalies in user behavior that indicate potential threats and fraud within SAP applications.
Why customers prefer SAP Enterprise Threat Detection monitoring SAP applications.
“IT and SAP Basis” – Two Worlds
The focus of known generic SIEM solution is on the real-time analysis of security alerts generated by network components, hardware, operating systems, and many other applications. When it comes to the monitoring of business applications like SAP, specific knowledge and skills are needed to interpret business application log files, for example monitoring changes to objects within the business environment. This is what SAP Enterprise Threat Detection is specialized in. Sure, it might seem obvious that in an ideal world all this should be combined in one solution but the reality looks different: when traveling from A to B it's difficult always using the same transportation technology, it would be very inefficient to go from Europe via Australia to the US using a bicycle or going from one town to another using a 747. In other terms we would always use the tool that fits best for the demand.
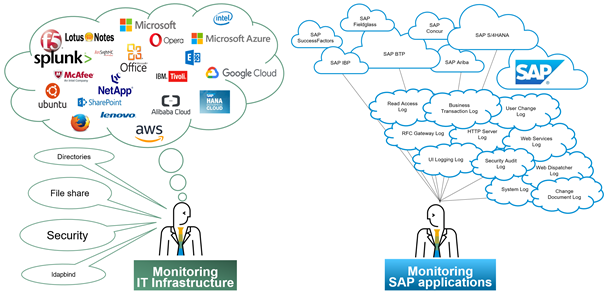
picture 2
What's in SAP Enterprise Threat Detection, cloud edition.
- Full cloud provisioning
- Integrated managed application security service
- SAP Enterprise Threat Detection, cloud edition ships with over 45 standard attack use cases Brings an included 24x7 alerting
- 5x8 risk based & prioritized investigation of alerts
- Monthly reporting of all incidents and all log data
- Collecting and storing of audit relevant business log information
- And to bridge the gap between the two worlds we integrate SAP Enterprise Threat Detection, cloud edition with the world's leading generic SIEM solutions as described in this blog post: SAP Enterprise Threat Detection (ETD) and Security Information and Event Management (SIEM). What is ... by Martin Mueller.
How SAP Enterprise Threat Detection integrates with generic SIEM and SOAR solutions.
SAP Enterprise Threat Detection integrates with generic SIEM and SOAR solutions such as FortiSOAR with standardized data formats so integration comes out of the box.

picture 3
How does SAP Enterprise Threat Detection, cloud edition work.

picture 4
- Business application and system events plus contextual data is sent to SAP Enterprise Threat Detection, cloud edition by SAP Enterprise Threat Detection log collector which needs to be installed in the environment.
- Data is then efficiently enriched, normalized, pseudonymized, analyzed, stored and correlated in the cloud.
- Use cases that automatically evaluate the attack path and identify the kill chain are executed in real-time and possible alarms are generated.
- Security analyst examines the alerts and evaluates the criticality (severity, true/false positive).
- Investigation report is created after completion by analyst.
- A Monthly report about all investigations is provided to the customer.
- If additional forensic analysis, threat hunting and modeling of new or existing attack detection patterns is needed, this can also be done leveraging additional services.

picture 5
Why would an organization use SAP Enterprise Threat Detection, cloud edition.
- Gain transparency and simplify the analysis of suspicious activities
- Detect threats to avoid financial loss, legal and reputation damage
- Ensure the continuity of business
- Reduce effort and identify security gaps
- Analyze huge amounts of information quickly
- No effort maintaining infrastructure and software
- Security operation managed by SAP (or partner / available Q2 2023)
How does SAP Enterprise Threat Detection, cloud edition look like.
To simplify access to relevant information about cyber attacks, we created a clearly designed user interface that is easy and intuitive to use.
The performed investigations can be filtered by severity, ID, creation date, description and customer message. The chosen report can immediately be downloaded and reviewed by the end user.
picture 6
The report includes an overview of what has happened and when and additionally includes a free text description from the investigator about the results of the investigation and recommended mitigation steps for further clarification. All technical details such as the triggering events are also provided with the report.
This enables the customer to take the right mitigation action at the right time. Overall, this managed cyber security service offered by SAP fills a significant gap by opening the black box and enabling continuous monitoring of SAP business applications as it's required by standard cyber security frameworks.

picture 7
Further information can also be found here:
SAP Enterprise Threat Detection | SAP Community
SIEM and Cybersecurity | SAP Enterprise Threat Detection
How to do (or not) an application log audit. (Fun)
Interesting partner blog:
Managed Service for SAP Enterprise Threat Detection - smarterSec
If you have questions or like to have a live demo session, please do not hesitate to contact your SAP sales representative.
Labels:
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
91 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
66 -
Expert
1 -
Expert Insights
177 -
Expert Insights
293 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
12 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
340 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
417 -
Workload Fluctuations
1
Related Content
- print open lines sales order sap b1 using crystal report in Technology Q&A
- SAC BW live connection: Error Illegal State: data area already existing in Technology Q&A
- WebIDE After building, code changes revert in Technology Q&A
- Streamlining Time Sheet Approvals in SuccessFactors: Time Sheet Approval Center in Technology Blogs by Members
- Enabling Support for Existing CAP Projects in SAP Build Code in Technology Blogs by Members
Top kudoed authors
| User | Count |
|---|---|
| 34 | |
| 25 | |
| 12 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 6 | |
| 5 | |
| 4 |
