
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Refresh Scenarios With SAP Landscape Management (L...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Part 1: Refresh Scenarios With SAP Landscape Management (LaMa): Across Azure Regions and Subscriptions
Part 2: Refresh Scenarios With SAP Landscape Management (LaMa): Across IaaS with LaMa SP21 (HANA Single Tenant Database Replication)
In this blog the use of Backint to perform HANA refresh will be covered. We will use the services available in AWS (AWS Backint Agent) and GCP (Cloud Storage Backint Agent).
Azure Backup with Backint is not supported by LaMa. See explanation below.
As explained in part 1, LaMa supports refresh of HANA using multiple approaches that fall in 3 categories:
- Leveraging storage integration (e.g. with the cloud adapters for AWS, Azure and GCP)
- Using HANA replication
- Restore based refresh
In the 3rd category of 'Restore based refresh', we already covered using filesystem based backups which rely on the built-in backup/restore capabilities in HANA. Another approach is to use 3rd party backup solutions and this relies on Backint. According to the HANA administration guide:
"A third-party backup tool communicates with an SAP HANA database through the Backint for SAP HANA interface. Backint for SAP HANA uses named pipes to back up the database, and performs all the actions needed to manage external storage."
In order to use Backint, the 3rd party tool must be certified by SAP but this alone is not sufficient for it to be used in LaMa for refresh purposes. Due to the nature of performing a refresh, access to the source database backup is needed from the target system. In Azure such access is currently not possible and therefore Azure Backup can not be used by LaMa via backint and standard processes.
Azure Backint supports cross system restore but only from the Azure console or using Azure API calls. It also supports restore as files to a shared filesystem (by the source database) which the target can then use to perform a database restore. Both of these options require building a custom process in LaMa but is outside the scope of this blog where we cover only built-in functionality. I may write a blog on this custom approach outside of the current blog series.
In addition to the cloud providers' own backup solution, other 3rd party backup solutions can also be used in AWS, GCP or Azure and of course on-premise. Support for LaMa depends on the implementation of backint. In general if the target system can access the backup of source via backint then LaMa will also support it out of the box.
1.0 AWS Backint Agent for SAP HANA
This section will cover the use of the AWS Backint Agent that allows backup of SAP HANA to AWS S3 and is certified by SAP (and validated with LaMa as will be shown below).
1.1 AWS Lab Environment

As shown in the diagram above, I have 2 SAP systems residing in the US East region of AWS and belonging to the same AWS account. A single S3 bucket will be used for backup/restore of both systems but not a requirement. Separate buckets can also be used for each system provided the target has access to the bucket holding backups of the source.
Below table shows some additional info but use of virtual hostnames are not mandatory at least for restore based refresh.
| TYPE | SID/HANASID | VM Hostname | Virtual Hostname |
| ASCS (source) | A4H | a4h-vm1 | a4h-ascs |
| HANA DB (source) | HDB | hdb-vm1 | hdb-db |
| PAS (source) | A4H | a4h-vm2 | a4h-app-0 |
| LaMa | J2E | nm-lama | n/a |
| ASCS (target) | B4H | a4h-vm1-c | a4h-ascs-c |
| HANA (target) | BDB | hdb-vm1-c | hdb-db-clone |
| PAS (target) | B4H | a4h-vm2-c | a4h-app-clone |
- HANA version 2.00.052
- Netweaver ABAP Release 7.52
- SUSE Linux Enterprise 12 SP3
- LaMa 3.0 Enterprise edition SP23
- SAP Host Agent Patch 56
- SAP Adaptive Extensions 1.0 EXT Patch 69
- PCA installed/activated
Ensure ahead of time that release versions match for source and target
- The support package level can differ within the same SAP_BASIS release
- Applicable if following prerequisites are met:
- Source and target need to be on the same SAP_BASIS release, e.g on 754
- PCA Task content needs to be on the same build level
1.2 AWS Backint Configuration
Follow the steps in the AWS Document or the summarized ones below:
1.2.1 AWS Authentication Setup
- On the HANA server create your AWS credentials (assumes that AWS CLI is already installed)
Login as <sid>adm on the HANA server
aws configure
AWS Access Key ID []: <your access key id>
AWS Secret Access Key []: <your secret key>
Default region name []: us-east-1
Default output format []: json
Above is needed so that CLI can be used for both our commands below as well as by the backint agent later
1.2.2 AWS S3 Setup
If you already have an S3 bucket then skip to preparation.
- Create an S3 bucket for the HANA backups and configure for secure access
This example shows the AWS CLI but you can also use the console
Step 1: Initial create. Note that the bucket name needs to be unique. If you get an error about the name then try a different name
aws s3api create-bucket --bucket MyBucket --region us-east-1Step 2: Block public access
aws s3api put-public-access-block \
--bucket MyBucket \
--public-access-block-configuration "BlockPublicAcls=true,IgnorePublicAcls=true,BlockPublicPolicy=true,RestrictPublicBuckets=true"Step 3: Enable default encryption. Replace <account id> with actual value
aws s3api put-bucket-encryption --bucket MyBucket --server-side-encryption-configuration '{
"Rules": [
{
"ApplyServerSideEncryptionByDefault": {
"SSEAlgorithm": "aws:kms",
"KMSMasterKeyID": "arn:aws:kms:us-east-1:<account id>:alias/aws/s3"
}
}
]
}'Step 4: Add policy to use only https
Create a file e.g. policy.json with below content:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Deny",
"Principal": "*",
"Action": "s3:*",
"Resource": "arn:aws:s3:::MyBucket/*",
"Condition": {
"Bool": {
"aws:SecureTransport": "false"
}
}
}
]
}
Now run the command below:
aws s3api put-bucket-policy --bucket MyBucket --policy file://policy.json1.2.3 Preparation of backint installer script
The initial backint configuration is done via a script provided by AWS. We need a few parameters before we run the script.
Step 1: Obtain S3 master key id
aws s3api get-bucket-encryption --bucket MyBucket
--> Note down the master key idStep 2: Obtain S3 KMS ARN and the AWS Account ID
aws kms describe-key --key-id <above key id>
--> Note down the "Arn" and "AWSAccountId" (we will need it later)
--> Example: "Arn": "aws:kms:us-east-1:xxxxxxxxxx:key/yyyyyy"
"AWSAccountId": "xxxxxxxxxxxx"1.2.4 Execute the AWS Backint Agent configuration script
Use the interactive installer approach as described here or follow the steps below. Perform on the source HANA server.
Step 1: Download and run the script
cd /tmp
sudo aws s3 cp s3://awssap-backint-agent/binary/latest/install-aws-backint-agent /tmp/
sudo python install-aws-backint-agentStep 2: Enter the information requested as below:
| Location of Install | /hana/shared |
| Account ID | Enter AWS account ID as noted earlier above |
| Region | Same region where your bucket is located |
| Bucket Name | The name given when creating S3 |
| Folder in S3 | Enter SID name or other identifier for source. This will put the backup in the folder with this name |
| Encryption | Enter the ARN noted earlier above |
| SAP HANA system ID | Enter the HANA SID (e.g. HDB) |
| HANA opt directory | Default |
| Modify global.ini | Enter modify to let script edit it |
| HANA SYSTEM db global.ini file | Check if location is correct |
| Verify signature of the agent binary tar file | y or n |
| Save responses for future use | y |
Step 3: Verify that directory '/hana/shared/aws-backint-agent' is created
Step 4: Configure parameter files
On the source HANA server go into the directory /hana/shared/aws-backint-agent. Here you will find the aws-backint-agent-config.yaml file that was created by the installation script.
We need to create symbolic links to the above file in the directory /usr/sap/<hana sid>/SYS/global/hdb/opt/hdbconfig
cd /usr/sap/HDB/SYS/global/hdb/opt/hdbconfig
ln -s /hana/shared/aws-backint-agent/aws-backint-agent-config.yaml aws-backint-agent-config.yaml
ln -s /hana/shared/aws-backint-agent/aws-backint-agent-config.yaml aws-backint-agent-config_HDB.yaml
ln -s /hana/shared/aws-backint-agent/aws-backint-agent-config.yaml aws-backint-agent-config_HDB_HDB.yamlNote that we created versions that include "_HDB" and "_HDB_HDB". We do this because LaMa will use the variables $(SAPSYSTEMNAME) and $(DBNAME). In my case both values equate to HDB but your scenarios maybe different so use your corresponding values.
Step 5: Modify global.ini with HANA Studio
catalog_backup_parameter_file: use aws-backint-agent-config_$(SAPSYSTEMNAME).yaml for system database
data_backup_parameter_file: use aws-backint-agent-config_$(SAPSYSTEMNAME)_$(DBNAME).yaml for tenant database
log_backup_parameter_file: use aws-backint-agent-config_$(SAPSYSTEMNAME)_$(DBNAME).yaml for tenant database
Verify that catalog_backup_using_backint is set to true for both databases
Verify that log_backup_using_backint is set to true for both databases
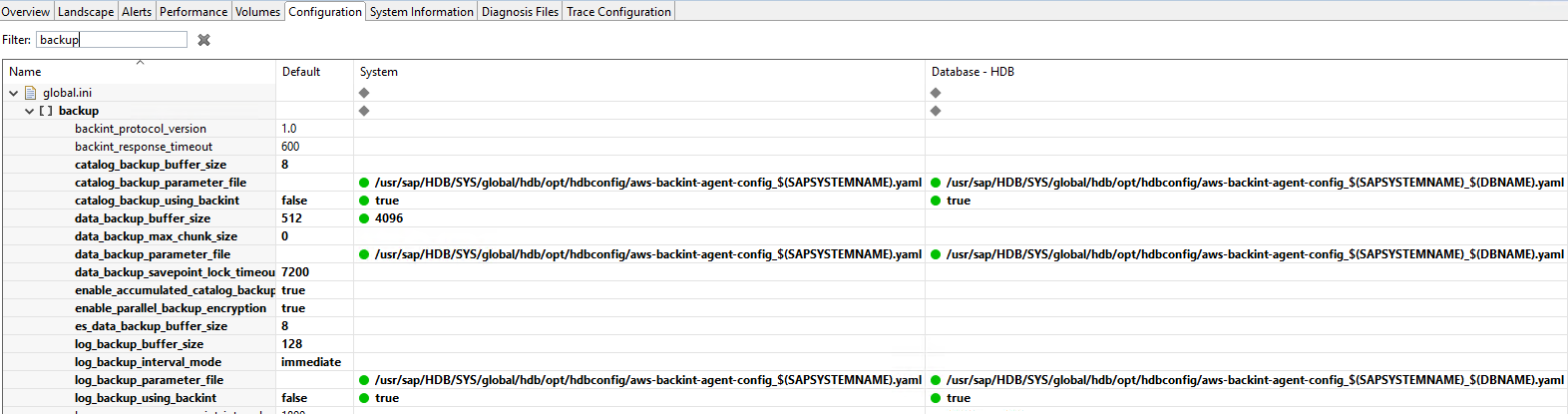
1.2.6 Verify backup via HANA Studio
We will check that backup is successful via HANA Studio and uses the destination type as Backint

1.2.7 Backint installation step on the target system
All the steps are identical to that performed on the source HANA server except the following.
Step 1: Download and run - same as steps for source
Step 2: Same as source except the folder name for the target server will be different:
| Folder in S3 | Enter SID name or other identifier for target |
Step 3: Verify as in source
Step 4: Configure parameters -- slight variation
Create the symbolic links using corresponding values of SAPSYSTEMNAME and DBNAME of the target
cd /usr/sap/HDB/SYS/global/hdb/opt/hdbconfig
ln -s /hana/shared/aws-backint-agent/aws-backint-agent-config.yaml aws-backint-agent-config.yaml
ln -s /hana/shared/aws-backint-agent/aws-backint-agent-config.yaml aws-backint-agent-config_BDB.yaml
ln -s /hana/shared/aws-backint-agent/aws-backint-agent-config.yaml aws-backint-agent-config_BDB_BDB.yamlCopy the parameter files of the source to the target.
copy source:/usr/sap/HDB/SYS/global/hdb/opt/hdbconfig/aws-backint-agent-config_HDB.yaml to target:/usr/sap/BDB/SYS/global/hdb/opt/hdbconfig/aws-backint-agent-config_HDB.yaml
copy source:/usr/sap/HDB/SYS/global/hdb/opt/hdbconfig/aws-backint-agent-config_HDB_HDB.yaml to target:/usr/sap/BDB/SYS/global/hdb/opt/hdbconfig/aws-backint-agent-config_HDB_HDB.yamlYou should now see the following in the directory where HDB refers to source and BDB refers to target:
cd /usr/sap/BDB/SYS/global/hdb/opt/hdbconfig
ls -1
aws-backint-agent-config.yaml
aws-backint-agent-config_BDB.yaml
aws-backint-agent-config_BDB_BDB.yaml
aws-backint-agent-config_HDB.yaml
aws-backint-agent-config_HDB_HDB.yamlStep 5: Modify global.ini -- Same steps as source but this time for the target database
1.3 LaMa Setup
Ensure that your two systems are configured in LaMa. Refer to part 1 of the blog series. Especially make sure that the "System Provisioning & RFC" of B4H specifies A4H as source.
Do not configure HANA backup share as it is needed only for file based restore and will interfere with backint option. If already configured then remove this. Source system configuration for HANA backups showing empty table:

View of the source and target in LaMa:

Retrieve profile in LaMa for both source and target database instances by clicking on "Retrieve from Instance Agent" and then save. This is a crucial step as LaMa will use these values to use backint for the refresh.

1.4 Perform Refresh in LaMa
- Provisioning View -> B4H -> Provisioning -> Refresh Processes -> Restore-based Refresh
Since there is no HANA share configured, LaMa now defaults to Backint.

- Basic screen: Enter master password
- Hosts screen: Verify and accept defaults
- Host Names screen: Verify host names and IP addresses
- User screen: Accept default as we have pre-existing account
- Database Restore screen: Select the backup you want to use
- LaMa used the parameter file to retrieve the backup list from the catalog of the source database
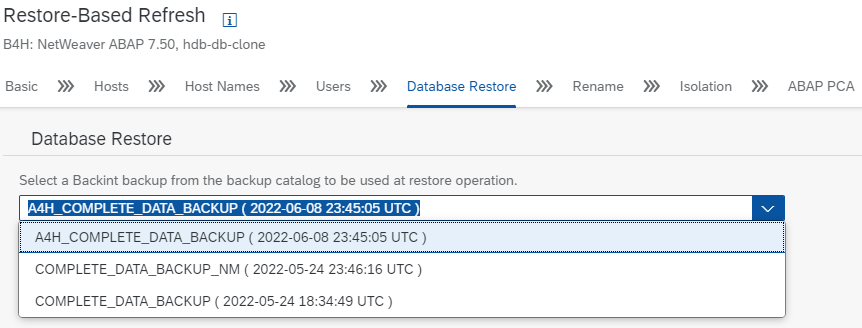
- You will get a warning which you can ignore (but take note of it)

- On the Rename screen, either accept defaults or if passwords differ from the Master then change them accordingly.

In the isolation screen, select the default network access control list. During the initial configuration in LaMa these default rules are defined.
- Select “Unfence target system without confirmation”. You may also select the other two options based on your scenario. For unfencing without prompt users take full responsibility for unfencing the target.
- For PCA, you can add any task list variant that you may have created as well as any other task list you would like to execute, for example the BDLS task list with its improvements. In this example we kept the default.
- The activity should now run and progress bar will eventually reach 100%


2.0 GCP - Cloud Storage Backint Agent for SAP HANA
In this section we will cover the use of Google's Cloud Storage Backint Agent that allows backup of SAP HANA to Google Cloud Storage bucket and is certified by SAP (and validated with LaMa). The procedure is very similar to that covered in the AWS section so most of the steps will be abbreviated.
2.1 GCP Lab Environment

As in the case of my AWS lab environment, here also I have 2 SAP systems. Region for GCP is US West and belonging to the same GCP account. A single Cloud Storage bucket will be used for backup/restore of both systems but you can use different ones for source and target.
My environment was installed identical to that in AWS so SIDs are similar. A different instance of LaMa was used.
| TYPE | SID/HANASID | VM Hostname | Virtual Hostname |
| ASCS (source) | A4H | a4h-vm1 | a4h-ascs |
| HANA DB (source) | HDB | hdb-vm1 | hdb-db |
| PAS (source) | A4H | a4h-vm2 | a4h-app-0 |
| LaMa | J2E | nm-lama | n/a |
| ASCS (target) | B4H | a4h-vm1-c | a4h-ascs-c |
| HANA (target) | BDB | hdb-vm1-c | hdb-db-clone |
| PAS (target) | B4H | a4h-vm2-c | a4h-app-clone |
- HANA version 2.00.052
- Netweaver ABAP Release 7.52
- SUSE Linux Enterprise 12 SP3
- LaMa 3.0 Enterprise edition SP23
- SAP Host Agent Patch 56
- SAP Adaptive Extensions 1.0 EXT Patch 69
2.2 GCP Backint Configuration
Follow the steps in the GCP Document or the summarized steps below.
2.2.1 GCP Authorization Setup
When using a Compute Engine instance, you're not required to authorize the gcloud or gsutil CLI.
In our setup the source HANA and the target HANA are all compute engines and thus already able to use the CLI
If the following command (executed as <sid>adm) returns your GCP project id correctly then you are all set and can move to the next section.
gcloud config list core/projectIf for some reason the authentication is missing or has been removed, then follow these steps to re-authorize.
gcloud init --console-onlyOpen a browser on your laptop and paste the URL from above command output to complete the authorization process.
Repeat on other HANA server.
2.2.2 Cloud Storage Bucket Setup
If you already have a bucket then skip to next section.
The below command creates a bucket with name "xx-bucket", storage class of "nearline", region us-west1, access control "uniform" (-b flag), public access blocked (--pap flag)
gsutil mb -p <project id> -c nearline -l us-west1 -b on --pap "enforced" gs://xx-bucket2.2.3 Execute the GCP Backint configuration script
- Download and execute the install script
Login as <sid>adm then issue below commands:
curl -O https://storage.googleapis.com/cloudsapdeploy/backint-gcs/install.sh
chmod +x install.sh
./install.sh- Configure parameter files
Edit the file /usr/sap/<SID>/SYS/global/hdb/opt/backint/backint-gcs/parameters.txt and add the bucket name.
NOTE: Do not remove the "#" in front of BUCKET
#BUCKET xx-bucket
#DISABLE_COMPRESSION
Create versions of the parameter files using the SAPSYSTEMNAME and SAPSYSTEMNAME_DBNAME values.
cd /usr/sap/HDB/SYS/global/hdb/opt/backint
cp -p parameters.txt parameters_HDB.txt
cp -p parameters.txt parameters_HDB_HDB.txt2.2.4 Configure global.ini via HANA Studio
The steps here are identical to the AWS section. Only difference is the name of the parameter files.
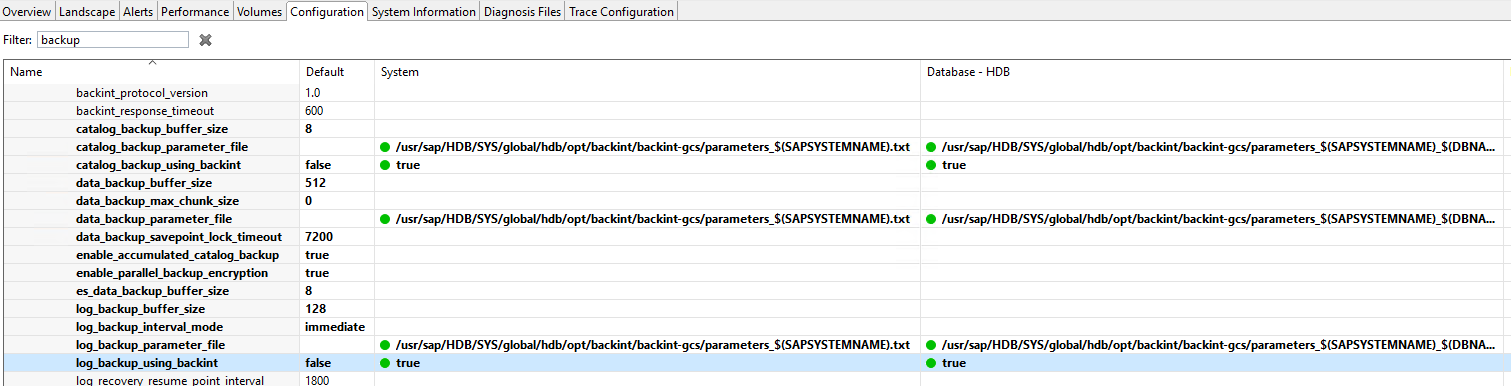
2.2.5 Verify backup via HANA Studio
Perform a backup using backint as shown in section 1.2.6
2.2.6 Backint installation step on the target system
All the steps are identical to that performed on the source HANA server except the following.
Create versions of the parameter files (target system SAPSYSTEMNAME and SAPSYSTEMNAME_DBNAME)
cd /usr/sap/HDB/SYS/global/hdb/opt/backint
cp -p parameters.txt parameters_BDB.txt
cp -p parameters.txt parameters_BDB_BDB.txtCopy the parameter files of the source to the target.
copy source:/usr/sap/HDB/SYS/global/hdb/opt/hdbconfig/parameters.txt to target:/usr/sap/BDB/SYS/global/hdb/opt/hdbconfig/parameters_HDB.txt
copy source:/usr/sap/HDB/SYS/global/hdb/opt/hdbconfig/parameters_HDB_HDB.txt to target:/usr/sap/BDB/SYS/global/hdb/opt/hdbconfig/parameters_HDB_HDB.txtYou should now see the following in the directory where HDB refers to source and BDB refers to target:
cd /usr/sap/BDB/SYS/global/hdb/opt/hdbconfig
ls -1
parameters.txt
parameters_BDB.txt
parameters_BDB_BDB.txt
parameters_HDB.txt
parameters_HDB_HDB.txtModify global.ini of target database with HANA Studio as done on the source database
2.3 LaMa Setup
Follow the same steps as in the AWS section
2.4 Perform Refresh in LaMa
Follow the same steps as in the AWS section
References
- List of SAP certified 3rd party Backint Providers
- LaMa Documentation on Refresh with Backint
- SAP Note 2877917 - SAP Landscape Management - Prerequisites for third-party tool parameter files' na...
- SAP Note 2905510 - SAP HANA system configuration for Copying a Database Using Third-Party Backup Too...
- SAP Note 3010872 - SAP Landscape Management - An Empty List of Backups at Restore Refresh via Backin...
- AWS Backint Agent Guide
- Cloud Storage Backint Agent for SAP HANA
- SAP Managed Tags:
- SAP HANA,
- SAP Landscape Management,
- SAP Landscape Management, enterprise edition
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
87 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
64 -
Expert
1 -
Expert Insights
178 -
Expert Insights
273 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
11 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
323 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
400 -
Workload Fluctuations
1
- 10+ ways to reshape your SAP landscape with SAP Business Technology Platform - Blog 7 in Technology Blogs by SAP
- 10+ ways to reshape your SAP landscape with SAP BTP - Blog 4 Interview in Technology Blogs by SAP
- 10+ ways to reshape your SAP landscape with SAP Business Technology Platform – Blog 4 in Technology Blogs by SAP
- Top Picks: Innovations Highlights from SAP Business Technology Platform (Q1/2024) in Technology Blogs by SAP
- How to delete an ABAP system from Cloud ALM Landscape Management? in Technology Q&A
| User | Count |
|---|---|
| 11 | |
| 10 | |
| 9 | |
| 9 | |
| 7 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 5 |