
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Creating a Key Pair and Public-Key Certificate wit...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Procedure
- Open the Key Storage Content tab.
- Select the view for which you want to create a key pair and certificate from the Key Storage Views.

- In the View Entries tab, choose Create.
The New Entry dialog appears.
- In Step 1, define the basic settings of the new entry.
- In the Entry Name field, specify a name for the certificate.
- Select the certificate algorithm in Algorithm, for example, RSA (Rivest, Shamir, Adleman) or DSA (Digital Signature Algorithm).
- Choose the certificate key length in Key Length.
- Specify the certificate validity period in the Valid From and Valid To fields.
Enter the values using the format mm/dd/yyyy.
- If you want to have a copy of the new certificate as a separate keystore entry next to the new key pair in the key storage, select Store Certificate.
Choose Next.

- In Step 2, specify the properties of the Subject field for the certificate. If no property has value, the Subject Alternative Name extension will be denoted as critical.
Choose Next.

- In Step 3, specify the properties of the Subject Alternative Name extension of the certificate. If at least one property of the Subject has a value, the Subject Alternative Name extension will be denoted as non-critical.
- Add the directory name properties. You can also use the Move Up and Move Down buttons to sort the properties.

- Add all other subject alternative name properties and choose Next.
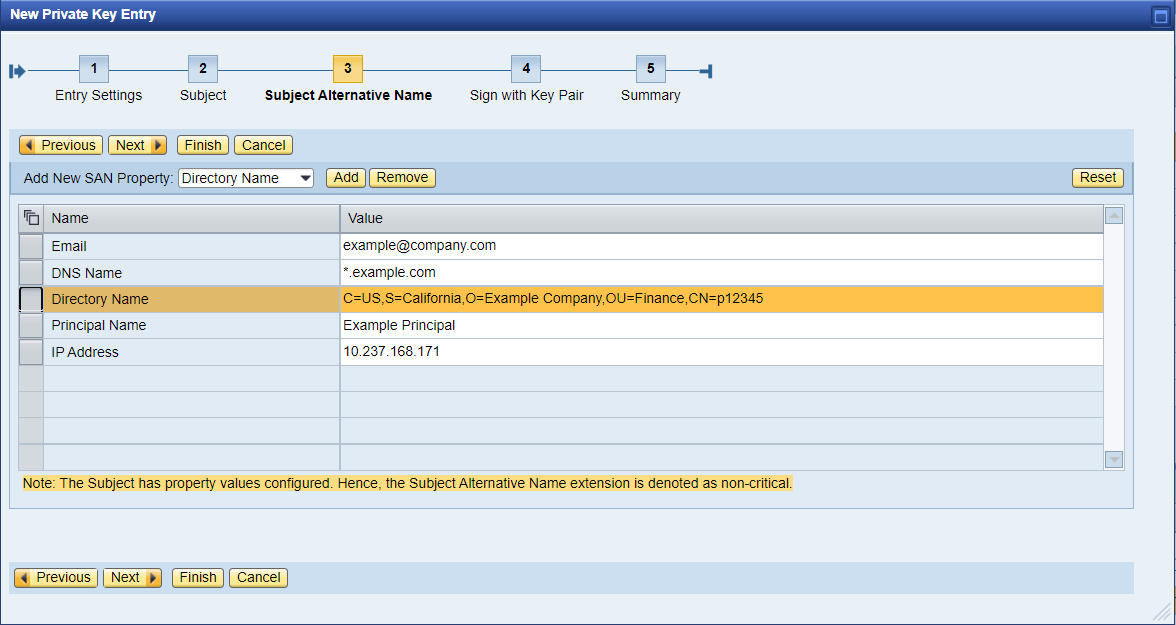
- Add the directory name properties. You can also use the Move Up and Move Down buttons to sort the properties.
- In Step 4, sign the new entry with a key pair and choose the signature hashing algorithm for the certificate. This step is optional.
If you want to specify a Certification Authority (CA) key pair, choose Select Issuer Key Pair and select the view from which to specify the CA key pair.

If you create a self-signed certificate, then specify hashing algorithm for the certificate signature in the Signature Hashing Algorithm menu. If you specify a signing CA , the hashing algorithm will be used from the CA certificate.
Choose Next.
- In Step 5, preview your settings.
To create the new entry, choose Finish.

Result
A progress bar indicates the generation of the key pair and certificate. Once generated, they are displayed on the View Entries list.
Your Feedback
Your feedback on this configuration is appreciated. Please tell us if:
- You can intuitively use this functionality, and what we can improve on its usability.
- The newly added SAN support for the certificate generation solves your previous issues.
- You need other certificate generation features that will improve your daily work.
- SAP Managed Tags:
- SAP NetWeaver Application Server for Java
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
91 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
66 -
Expert
1 -
Expert Insights
177 -
Expert Insights
293 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
341 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
419 -
Workload Fluctuations
1
- Mistral gagnant. Mistral AI and SAP Kyma serverless. in Technology Blogs by SAP
- Cloud Integration: Manually Sign / Verify XML payload based on XML Signature Standard in Technology Blogs by SAP
- Cloud Integration: AMQP Adapter, Client Certificate, Solace PubSub+ [2]: Certificate Chain in Technology Blogs by SAP
- Cloud Integration: Manually Encrypt/Decrypt XML payload based on XML-Enc Standard in Technology Blogs by SAP
- What’s New for SAP Integration Suite – February 2024 in Technology Blogs by SAP
| User | Count |
|---|---|
| 35 | |
| 25 | |
| 14 | |
| 13 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 5 |