- SAP Community
- Products and Technology
- Enterprise Resource Planning
- ERP Blogs by Members
- Microsoft Sentinel and Logic Apps can be the 'Guar...
Enterprise Resource Planning Blogs by Members
Gain new perspectives and knowledge about enterprise resource planning in blog posts from community members. Share your own comments and ERP insights today!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
former_member12
Active Contributor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
03-14-2022
8:05 PM
"Microsoft Security delivers new multi-cloud capabilities"
Hello Community Members,
I'm back with some interesting PoV to demonstrate the SecOps & SAP Security elements on 'SAP on Azure (or AWS, GCP, or on-prem systems)', leveraging Cloud-based SIEM and SOAR solutions.
As we know SAP is the custodian for immense amounts of sensitive data in many of the most prominent organizations in the world. Since these applications are business-critical, and SAP security breach can be disastrous. However, protecting SAP applications is uniquely challenging always. We constantly require a prominent security squad and resources, characterizing with The Guardians of the galaxy to protect from any internal or external violations. SecOps on hyperscalers is a very comprehensive topic, so I will begin with a clear lodestar. In today’s post, I'd like to exhibit how the Azure services like Microsoft Sentinel, Logic Apps, SAP Connector can be configured altogether to protect all SAP users...An incredibly straightforward use case for advanced SAP users.
Sounds fascinating! Let's hop into the technical elements!
 Source: Bing images
Source: Bing images
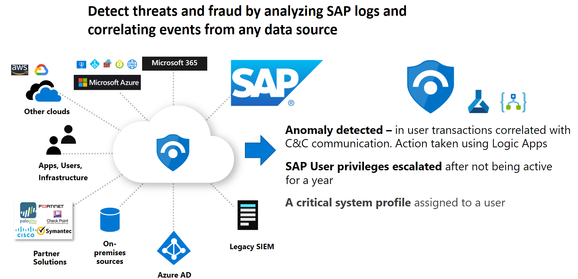
It has been notoriously challenging to detect these threats to SAP applications, while the consequences of an undetected threat can be profoundly serious, especially breaches from inside or outside. This hardship in detection stems in part from the complex internal nature of SAP systems, as well as the fact that these systems usually have lots of cross-connections between distinct third-party applications and interfaces, specifically banking and finance segments.
Hence Microsoft Azure provides the new solution to tackle these SAP security challenges with the new SAP threat monitoring solution for Azure Sentinel. (First cloud-native SIEM from a major cloud provider.)
Continuous Threat Monitoring for SAP in Microsoft Sentinel
Azure provides the new solution to tackle these SAP security challenges with the new SAP threat monitoring solution for Azure Sentinel. Please note, is in public preview today, this solution provides continuous threat detection and analytics for SAP systems deployed on Azure, in other clouds, or on-premises. Now, SecOps teams can use Azure Sentinel’s visibility, threat detection, and investigation tools to protect their SAP systems and cross-correlate across their entire organization.
Prerequisite - I presume you completed the deployment of your SAP system and Microsoft Sentinel connection by referring- Deploy SAP continuous threat monitoring | Microsoft Docs (Microsoft documentation)
The Continuous Threat Monitoring for SAP in Microsoft Sentinel enables you to monitor your SAP environment and helps you with cross-correlating various logs from numerous systems with your SAP logs. With the Microsoft Sentinel SAP connector, you can monitor your SAP systems for sophisticated threats within the business and application layers. The connector uses a docker container, which pulls the data from SAP and then sends it through to Microsoft Sentinel. Don't worry, you will see the architecture flow outlying in this article.
By deploying the data connector, we can now import the SAP logs into Sentinel, correlate the logs with other data, and analyze and hunt the logs for emerging threats. Install the SAP solution security content to gain insight into your organization's SAP environment and enhance any related security operation capabilities.
For a comprehensive synopsis of what is included in the Sentinel SAP solution content,
see Microsoft Sentinel SAP solution - security content reference | Microsoft Docs
Microsoft Sentinel contains a substantial Security Orchestration and Automated Response (SOAR) capability which will help SAP applications respond to incidents rapidly with AI and automation features built in to use. Many SOAR integrations can be deployed as part of a Microsoft Sentinel solution, together with related data connectors, analytics rules, and workbooks.
For more information, see the Microsoft Sentinel solutions catalog.
Source: Microsoft Azure documentation
In this composition, we will see how you can use the SOAR capabilities of Sentinel with SAP Application, by using the Azure playbook that automatically takes on remediation actions in the SAP system directly with the Logic App connector.
Let’s glimpse!
Overview & Use case
We are stirring to focus on a pragmatic use case criterion for automating SAP actions as a response to an incident in Sentinel with SAP code triggered with Logic Apps support.
Use case: An SAP user with developer privileges could exploit those privileges to view sensitive human resources or financial data by perpetrating a function module to gain elevated access privileges which are not authorized to this SAP user. Microsoft Sentinel gives you the ability to quickly detect these threats and hazards in the SAP system without drowning in noise.
Obstruct the SAP dialog or RFC user(s) after a suspicious user incident is notified.
- The SOC (SecOps) team is alerted of a suspicious atypical travel alert.
- After triaging the incident, the SOC team decides to block the user's access to sensitive environments. One of these sensitive environments is the SAP system to which the user can't have access anymore.
- The SOC team runs playbooks for these automatic remediations and one of the playbooks is the ‘BlockSAPUser’-playbook.
The objective here is to block the SAP dialog or RFC user credential by locking the dialog or RFC user accessing SAP S/4HANA or ECC/NetWeaver system in an automated way with help of Logic Apps BAPI function triggers.
Getting Started
For this blog post, we make use of the on-prem data gateway to leverage the SOAR capabilities from Sentinel on SAP.
This gateway makes it possible to have a secure data transfer between data sources and services in the cloud. The data gateway should be installed on a Windows system. It is feasible to use a dedicated machine or install it on the machine on which SAP is running, but you must ensure that both the VMs can intercommunication with each other over the private IPs or the same VNET.
- For more information on the installation and prerequisites for this data gateway, please visit Install on-premises data gateway - Azure Logic Apps | Microsoft Docs
- You can download the gateway via Download On-premises data gateway from Official Microsoft Download Center
When you have installed the data gateway, you will also need to install the SAP Connector for Microsoft .NET 3.0 on the identical machine as the data gateway. The SAP Connector for Microsoft .NET 3.0 will allow us to use BAPIs and remote-enabled function modules in a .NET application. You can download the SAP connector via Software Downloads - SAP ONE Support Launchpad
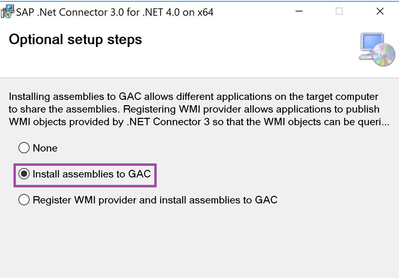
Make sure to use “Install assemblies to GAC” when setting up the SAP connector and afterward restart the data gateway.
For our conclusive preliminary step, we will have to create the gateway cloud service to conclude the handshake between the cloud services and the on-premises data gateway on the windows host.
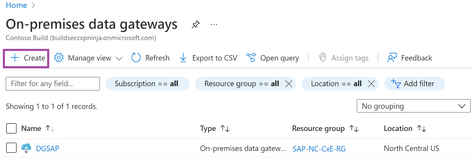
More information on creating the Azure gateway resource can be found on Access data sources on-premises - Azure Logic Apps | Microsoft Docs
Reference Architecture for SAP System(s)
connected with Azure Cloud Services and Workflow

- SAP Users/RFC User(s) connected from SAP system using SAP RFC /SOAP to Docker container running on Azure Cloud (SAP running on-prem or Azure or any other hyperscalers like AWS or GCP as depicted above in Architecture diagram.)
- Microsoft Sentinel triggers an atypical travel Alert/incident if any specific SAP user breaches after detecting by Microsoft Sentinel.
- Azure Logic Apps connected with Microsoft Sentinel and on-prem gateway (using SAP connector) triggers SAP BAPI locking function.
- This BAPI function triggered by Logic Apps connected to the SAP system locks the SAP user automatically. You can send email via Logic Apps to SecOps for SAP user locked alter (optional step can be added for alerts)
Let's see this Playbook in detail
In this use case, a suspicious developer user will be intercepted from accessing the SAP environment.
The SOC team has been notified of an ‘Atypical travel’ alert in Sentinel. After thorough investigations, they decide to block the user entity from accessing the SAP environment and use the “Run playbook” action to begin automatic remediation.
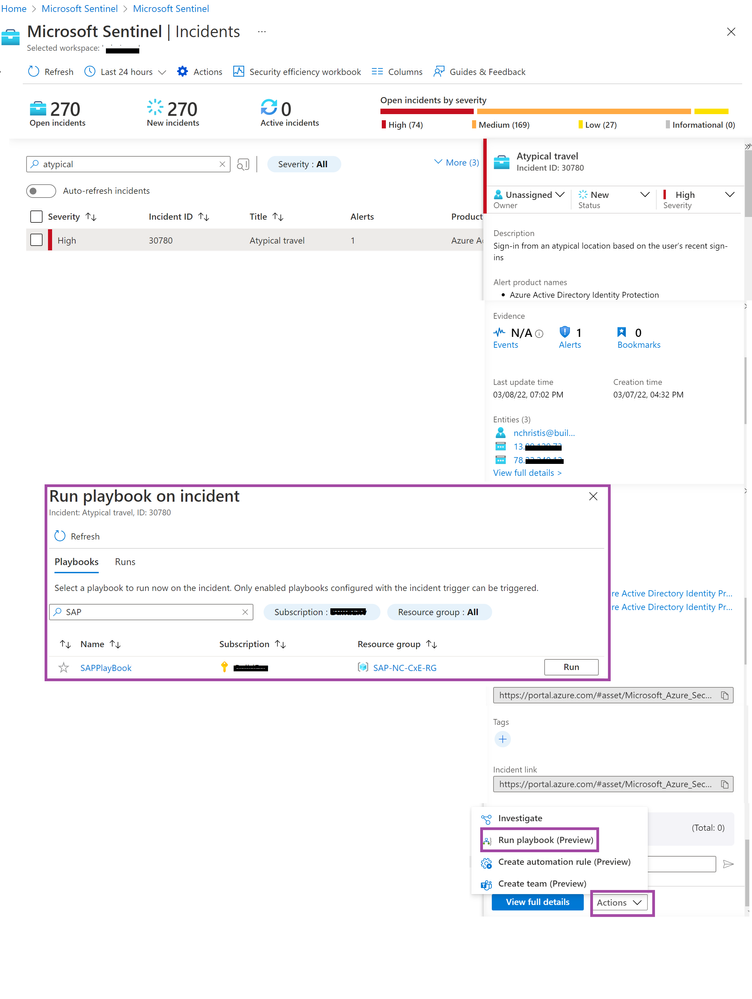 Atypical travel has been detected. Playbook will be used as an automatic remediation action. This playbook will use the Microsoft Sentinel incident as a trigger so that you can use it as an automatic action on an incident. In the playbook, the ‘Create stateful session’ action from the SAP connector (see: SAP - Connectors | Microsoft Docs) is used to make the connection with SAP.
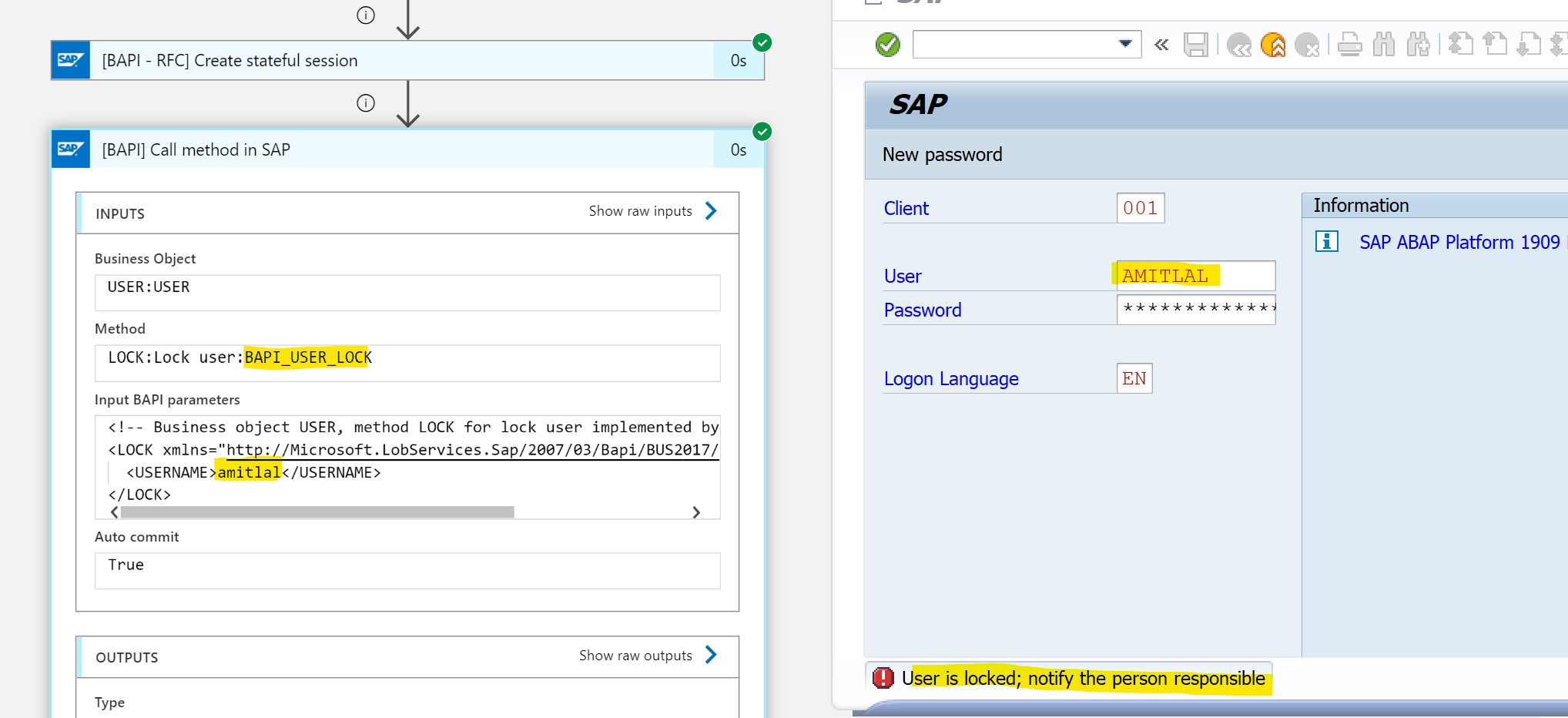
Atypical travel has been detected. Playbook will be used as an automatic remediation action. This playbook will use the Microsoft Sentinel incident as a trigger so that you can use it as an automatic action on an incident. In the playbook, the ‘Create stateful session’ action from the SAP connector (see: SAP - Connectors | Microsoft Docs) is used to make the connection with SAP. When the connection has been made, extract the user entity from the Sentinel incident and use the ‘BAPI - Call method’ to block the user in SAP.
For more information visit Connect to SAP systems - Azure Logic Apps | Microsoft Docs

- Azure Logic App script available on GitHub page for Input BAPI code - Link
<!-- Business object USER, method UNLOCK for Unlock user implemented by RFC BAPI_USER_UNLOCK -->
<UNLOCK xmlns="http://Microsoft.LobServices.Sap/2007/03/Bapi/BUS2017/">
<USERNAME>SAPUSERNAME</USERNAME>
</UNLOCK>
When my SAP user "Amitlal" attempts to logon to the SAP S/4HANA system, I cannot access the system since my user got locked out:
Final run
∑ Conclusion
Azure provides enterprise-grade cloud infrastructure & Security for SAP workload on which customers and partners can rely. No matter what your service level objectives are, Azure empowers you to achieve your organization's reliability goals. More complex use cases (e.g., with supplementary steps for authorization from SecOps/SOC manager via Microsoft Teams or Delete the SAP user account after a specific period, removing specific roles or blocking it!) are possible and we encourage you to try it out on your own!
Microsoft Sentinel and Logic Apps can be the 'Guardians of SAP Security Operations'?
Yes, one hundred percent!
Please share your views and comment. Thank you!

Special Thanks to Naomi Christis -Microsoft Sentinel Expert for co-authoring this article published on -
-Microsoft Tech Community
Disclaimer- The Microsoft Sentinel SAP solution is currently in PREVIEW include supplementary legal terms that apply to Azure features that are in beta, preview, or otherwise not yet released into general availability. I have blogged this article to share information that is intended as an unrestricted resource and personal insights. Errors or omissions are not intentional. Products and services cited in this article are not endorsements or favor. Opinions are my own and not the views of my employers (past, present, or future) or any organization that I may be affiliated with. Your comments to my posts are your views and I'm not responsible for anything shared by anyone in the article. SAP and hyperscalers Customers are responsible for making their own independent assessment of the information in this document. This article is for informational purposes only. The GitHub code is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. Thank you!
- SAP Managed Tags:
- SAP S/4HANA,
- NW ABAP User Administration and Authorization
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
"mm02"
1 -
A_PurchaseOrderItem additional fields
1 -
ABAP
1 -
ABAP Extensibility
1 -
ACCOSTRATE
1 -
ACDOCP
1 -
Adding your country in SPRO - Project Administration
1 -
Advance Return Management
1 -
AI and RPA in SAP Upgrades
1 -
Approval Workflows
1 -
Ariba
1 -
ARM
1 -
ASN
1 -
Asset Management
1 -
Associations in CDS Views
1 -
auditlog
1 -
Authorization
1 -
Availability date
1 -
Azure Center for SAP Solutions
1 -
AzureSentinel
2 -
Bank
1 -
BAPI_SALESORDER_CREATEFROMDAT2
1 -
BRF+
1 -
BRFPLUS
1 -
Bundled Cloud Services
1 -
business participation
1 -
Business Processes
1 -
CAPM
1 -
Carbon
1 -
Cental Finance
1 -
CFIN
1 -
CFIN Document Splitting
1 -
Cloud ALM
1 -
Cloud Integration
1 -
condition contract management
1 -
Connection - The default connection string cannot be used.
1 -
Custom Table Creation
1 -
Customer Screen in Production Order
1 -
Data Quality Management
1 -
Date required
1 -
Decisions
1 -
desafios4hana
1 -
Developing with SAP Integration Suite
1 -
Direct Outbound Delivery
1 -
DMOVE2S4
1 -
EAM
1 -
EDI
3 -
EDI 850
1 -
EDI 856
1 -
edocument
1 -
EHS Product Structure
1 -
Emergency Access Management
1 -
Energy
1 -
EPC
1 -
Financial Operations
1 -
Find
1 -
FINSSKF
1 -
Fiori
1 -
Flexible Workflow
1 -
Gas
1 -
Gen AI enabled SAP Upgrades
1 -
General
1 -
generate_xlsx_file
1 -
Getting Started
1 -
HomogeneousDMO
1 -
IDOC
2 -
Integration
1 -
Learning Content
2 -
LogicApps
2 -
low touchproject
1 -
Maintenance
1 -
management
1 -
Material creation
1 -
Material Management
1 -
MD04
1 -
MD61
1 -
methodology
1 -
Microsoft
2 -
MicrosoftSentinel
2 -
Migration
1 -
mm purchasing
1 -
MRP
1 -
MS Teams
2 -
MT940
1 -
Newcomer
1 -
Notifications
1 -
Oil
1 -
open connectors
1 -
Order Change Log
1 -
ORDERS
2 -
OSS Note 390635
1 -
outbound delivery
1 -
outsourcing
1 -
PCE
1 -
Permit to Work
1 -
PIR Consumption Mode
1 -
PIR's
1 -
PIRs
1 -
PIRs Consumption
1 -
PIRs Reduction
1 -
Plan Independent Requirement
1 -
Premium Plus
1 -
pricing
1 -
Primavera P6
1 -
Process Excellence
1 -
Process Management
1 -
Process Order Change Log
1 -
Process purchase requisitions
1 -
Product Information
1 -
Production Order Change Log
1 -
purchase order
1 -
Purchase requisition
1 -
Purchasing Lead Time
1 -
Redwood for SAP Job execution Setup
1 -
RISE with SAP
1 -
RisewithSAP
1 -
Rizing
1 -
S4 Cost Center Planning
1 -
S4 HANA
1 -
S4HANA
3 -
Sales and Distribution
1 -
Sales Commission
1 -
sales order
1 -
SAP
2 -
SAP Best Practices
1 -
SAP Build
1 -
SAP Build apps
1 -
SAP Cloud ALM
1 -
SAP Data Quality Management
1 -
SAP Maintenance resource scheduling
2 -
SAP Note 390635
1 -
SAP S4HANA
2 -
SAP S4HANA Cloud private edition
1 -
SAP Upgrade Automation
1 -
SAP WCM
1 -
SAP Work Clearance Management
1 -
Schedule Agreement
1 -
SDM
1 -
security
2 -
Settlement Management
1 -
soar
2 -
Sourcing and Procurement
1 -
SSIS
1 -
SU01
1 -
SUM2.0SP17
1 -
SUMDMO
1 -
Teams
2 -
User Administration
1 -
User Participation
1 -
Utilities
1 -
va01
1 -
vendor
1 -
vl01n
1 -
vl02n
1 -
WCM
1 -
X12 850
1 -
xlsx_file_abap
1 -
YTD|MTD|QTD in CDs views using Date Function
1
- « Previous
- Next »
Related Content
- Demystifying Transformers and Embeddings: Some GenAI Concepts in Enterprise Resource Planning Blogs by SAP
- Correct usage of SBO_Application.RemoveWindowsMessage in Enterprise Resource Planning Q&A
- Key Takeaways from Rise Into the Future Event: What You Need to Know in Enterprise Resource Planning Blogs by SAP
- SAP S/4HANA Service and integration with SAP Field Service Management in Enterprise Resource Planning Blogs by SAP
- SAP S/4HANA Cloud Private Edition | 2023 FPS01 Release – Part 1 in Enterprise Resource Planning Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 5 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |