
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- SAP Cloud Identity Services - Identity Directory
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Product and Topic Expert
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
02-01-2022
5:44 PM
Let’s recap what are the SAP Cloud Identity Services
The SAP Cloud Identity Services are the default SAP cloud services for authentication and user/group provisioning.
Several SAP integrations revolve around the usage of SAP Cloud Identity Services and their number is expected to increase. One of the biggest gains being the delivery of ready-to-use and secure cloud solutions from SAP. This does not hold true only for the Recruit to Retire business process, although this is the most obvious case.
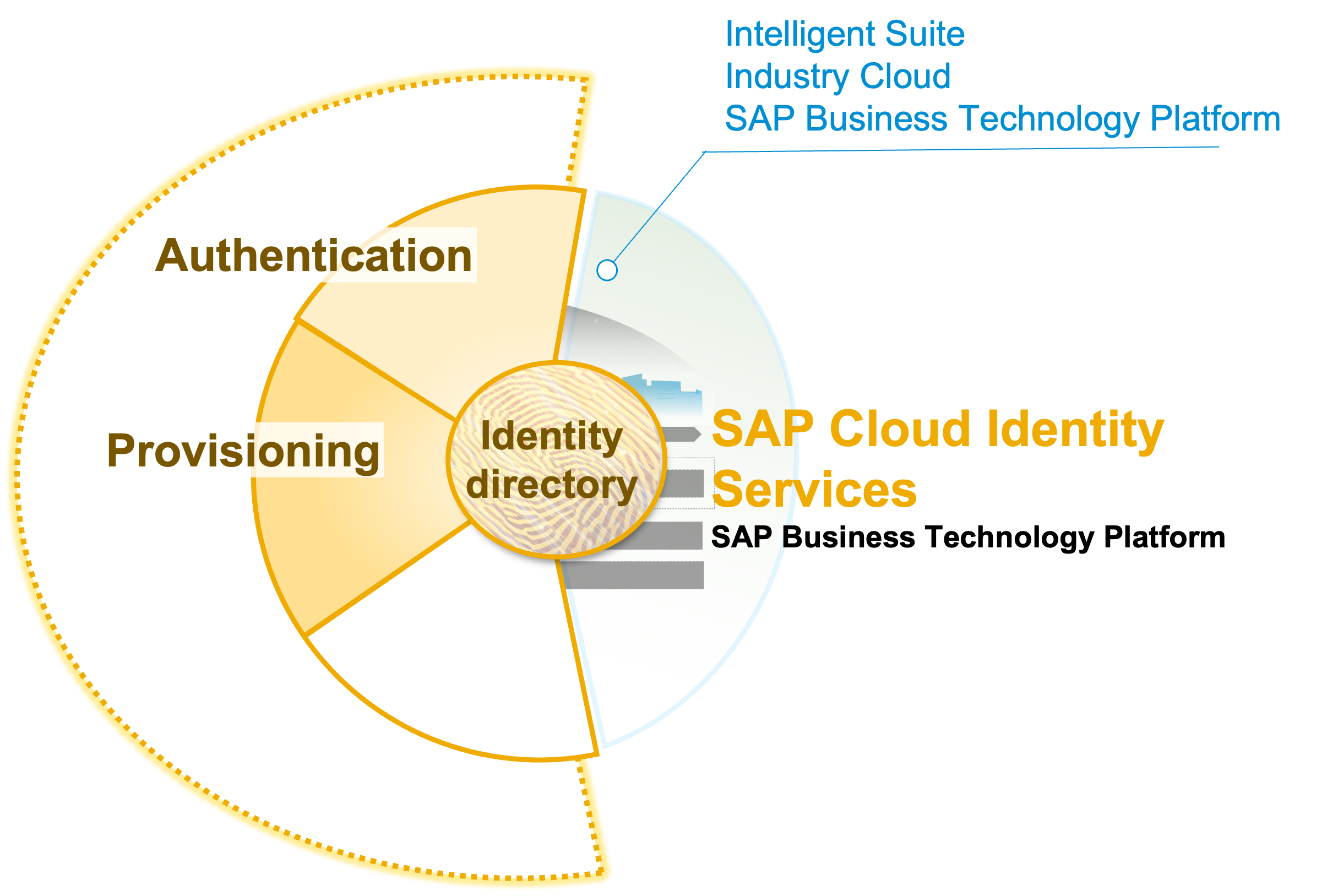
SAP Cloud Identity Services
As previously announced by my colleagues marko.sommer and matthias.kaempfer in previous blogs (links here and here), the Identity Authentication service (IAS) and Identity Provisioning service (IPS) evolved into SAP Cloud Identity Services, integrated now through the common Identity Directory.
What exactly is the Identity Directory?
The Identity Directory is the central component for persisting users and groups inside the SAP Cloud Identity Services. Coming from outside the SAP landscape, it represents the central point of truth for users that have or will have access to SAP cloud applications. Its SCIM 2.0 REST API allows you to programmatically access the resources (user, groups and customer schemas) inside the directory, but more to this in the sections below.
The functionality of the Local Identity Directory that some of you used with the standalone Identity Provisioning tenants has been enhanced and shifted meanwhile to the present Identity Directory inside the SAP Cloud Identity Services.
Unlike the Local Identity Directory, the data stored in the Identity Directory is not only visible at API level but also in the UI of the Identity Authentication service itself. The data stored under User Management and User Groups is actually the Identity Directory data.
User persistency in the SAP Cloud Identity Services
For some new features, the SAP Cloud Identity Services user persistency is mandatory and an automated integration with SAP SuccessFactors is already in place. Other well-known SAP cloud applications that require user persistency are SAP Task Center and SAP Identity Access Governance.
SAP Task Center offers a single-entry point for business users to access tasks coming from specific SAP solutions, called SAP task provider. Therefore, it is necessary that the users can be correctly identified in all these solutions otherwise the tasks cannot be correctly mapped. For this, SAP Task Center relies on the user Unique Universal Identifier that is generated in the Identity Directory.
The User Unique Universal Identifier
One of the user attributes that is created upon user persistency in Identity Directory is the User Unique Universal Identifier (UUID). For the time being its value is automatically generated and cannot be changed, but this is subject to change in the future. This attribute is immutable and can be used as a federation identifier or as a correlation attribute in a landscape that lacks such an immutable and unique attribute. The SAP Task Center functionality depends on this attribute for the correct identification of tasks for the users.
Here is a sequence of steps that is to be followed in landscapes where the usage of the UUID for the user identification in the SAP landscape is necessary (the premise is that there is a Corporate Identity Provider used in this scenario) :
1. Identity Federation - “Use Identity Authentication user store” IAS Leading for attributes sent to the application with the option to amend corporate IdP attributes

Corporate Identity Providers settings
2. SAML Assertion Attributes – add the User UUID to the list

Applications settings
3. SAML Default Attributes - the token can be enhanced with attributes from IAS and/or from the Corporate IdP

Applications settings
4. SAML Default Attributes - the token can be enhanced with attributes from IAS and/or from the Corporate IdP

Applications settings
How does one access and use the Identity Directory?
Besides the Identity Authentication user interface, one has two methods of managing the data inside the Identity Directory:
- API Business Hub: SAP Cloud Identity Services – Identity Directory
- With the Identity Provisioning Service SAP Cloud Identity Services – Identity Provisioning . Identity Provisioning can write users to the Identity Directory with the Identity Authentication connector by specifying the SCIM version 2 in the property section for ias.api.version.
Only tenant administrators with specific authorizations can access the Identity Directory.
Speaking about the data in the Identity Directory, it is important to know, that it is not only possible to view the predefined schemas but also to define own custom schemas with own attributes. This facilitates for example, the extension of the user resource with new attributes and values. One can have up to 20 custom schemas per tenant, each schema having a maximum of 20 attributes. The multivalued attributes (type complex) allow 20 sub-attributes.
The usage of the Identity Directory is meant to simplify how the customers are connecting to our SAP SaaS applications, by using it as a central point of truth for the SAP cloud environment.

Customer landscape integration with the SAP Cloud Identity Services
After the users are brought here, the Identity Provisioning service takes care of user provisioning to SAP applications that have an own user store. This will save you the effort of creating point to point connections. There are already automatic scenario deployments that ensure that the users are correctly distributes to SAP target systems, with minimum administrative effort. One such scenario is the integration between SAP SuccessFactors and People Analytics. Furthermore, once the users are centrally stored, it is easier to ensure an end of user lifecycle.
What is the connection to the SAP ID Service?
The Identity Directory must not be confused with the SAP ID service, which is SAP’s own instance of the SAP Cloud Identity service.
The SAP ID service is:
- SAP managed
- designed for interactions with SAP such as: BTP entitlements, support tickets, community postings
- does not allowed customer specific configurations such as Multi Factor Authentication, hence making its usage restrictive for scenarios that go beyond trial accounts
Key Takeaways
The Identity Directory represents the central point of truth for users that have or will have access to SAP cloud applications. It allows flexibility through the possibility of defining own customer schemas.
Storing users centrally in the Identity Directory not only simplifies the process of ensuring a proper user lifecycle, but also lays the foundation for integration with the SAP Cloud Identity Access Governance and SAP Task Center.
The integration with SAP’s Identity Management system is standard and brings many benefits as outlined in the Identity Lifecycle Blog Post series: Identity Lifecycle: SAP Reference Architecture for Identity Access Management – Part 1
For the customers using non-SAP identity management solution, storing the users in Identity Directory and afterwards leveraging automatic user provisioning with Identity Provisioning represent an easy integration with the SAP landscape as only one connection point is necessary. The one to the SAP Cloud Identity Services.
Related Information sources
SAP Cloud Identity Services
CIO Guide: Identity Lifecycle in Hybrid Landscapes
System Integration Guide for SAP Cloud Identity Services and SAP Task Center
SAP Task Center
Manage Deleted Entities in the SAP Cloud Identity Services – Identity Provisioning
SAP Cloud Identity Access Governance – Setting Up User Authentication and Access
System for Cross-domain Identity Management: Core Schema
- SAP Managed Tags:
- SAP Cloud Identity Services,
- Identity Provisioning,
- SAP Cloud Identity Access Governance
Labels:
6 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
88 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
65 -
Expert
1 -
Expert Insights
178 -
Expert Insights
280 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
11 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
330 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
408 -
Workload Fluctuations
1
Related Content
- Top Picks: Innovations Highlights from SAP Business Technology Platform (Q1/2024) in Technology Blogs by SAP
- Consuming SAP with SAP Build Apps - Connectivity options for low-code development - part 2 in Technology Blogs by SAP
- SAP SABRIX UPGRADE in Technology Blogs by Members
- How can assign in Identity Authentication Service IAS bulk users to a group? in Technology Q&A
- Identity Provisioning Documentation Joined the Family of SAP Cloud Identity Services in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 13 | |
| 11 | |
| 10 | |
| 9 | |
| 9 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 5 |