- SAP Community
- Groups
- Activity Groups
- SAP TechEd
- Blog Posts
- Achieve Security by Design and by Default #SAPTech...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content

Source: SAP
Ongoing problem
Data is going everywhere
Who has what data
How to protect endpoints if no patching happens
Zero trust architecture

Source: SAP
Secure operations map: link: https://support.sap.com/en/offerings-programs/support-services/security-optimization-services-portfo...
Building blocks to learn about SAP security
On premise view
Build a security culture at your organization
One customer mapped their solution to the building blocks for a framework and a road map
Solution Manager has capabilities - security optimization service

Source: SAP
For the cloud, a shared security responsibility

Source: SAP
RISE to S/4HANA
Your roles/responsibilities vs SAP vs hyperscaler

Source: SAP
CIO guide on sap.com
Work with cloud services - identity authentication, and access governance, and integrate with on premise solutions

Source: SAP
Tie once employee is onboarded
Automate workflow for identity and access

Source: SAP
Integrate with API's for on premise
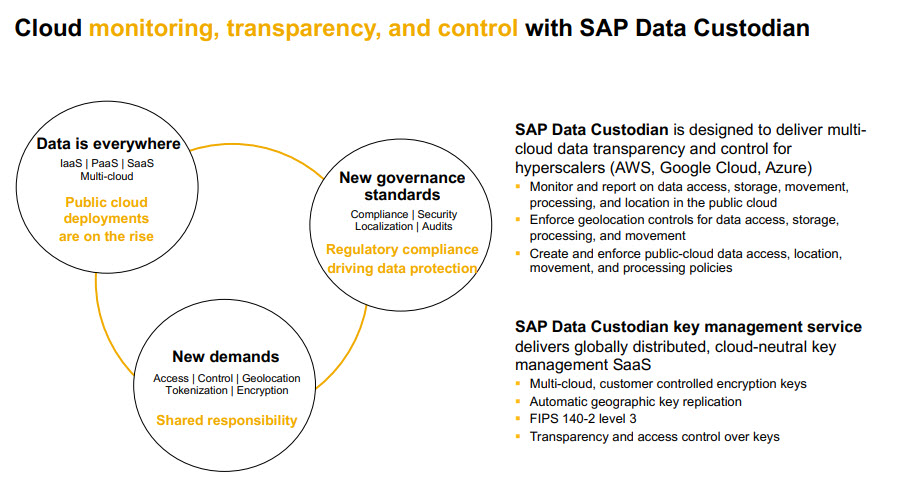
Source: SAP
Data Custodian in the cloud
Provides key management services

Can be on premise or cloud
Big data solution from SAP, using SAP HANA
Looks at log collectors, correlation against attack detection patterns

Source: SAP
Pulls in Security Notes
Mid Point Q&A:
Q: Is SAP Enterprise Threat Detection installed with out-of-the-box settings/monitoring ?
A: Yes, there are patterns available out of the box
Q: SAP Enterprise Threat Detection - is this available be default or to be purchased separately
A: It is a separate licensed product
Q: Do you recommend using System recommendations instead of Security notes in SAP ETD if available?
A: You can use both together or either depending on your requirements
Q: What is the average implementation time for SAP Enterprise Threat Detection?
A: Implementation timeframe depends on the requirements
Q: Can ETD feed off of ARA, with respect to SA Tcodes/Apps?
A: ETD can help track who did what in the SAP system, it highlights what a user actually did in the SAP system

Source: SAP
Use Signavio to see who is accessing what - determine what business processes make sense
Use Digital Boardroom to see data in a visual way

Source: SAP
Link:
https://www.sap.com/products/enterprise-threat-detection.html
this blog might help: https://blogs.sap.com/2020/08/12/sap-cloud-alm-vs-sap-solution-manager/
Session materials are here
The legal disclaimer applies to this session; anything in the future is subject to change.
- SAP Managed Tags:
- SAP TechEd,
- Security
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
Application Development and Automation (AD)
21 -
Applications and Business Processes (AP)
2 -
Artificial Intelligence (AI)
10 -
Channel 1
3 -
Data and Analytics (DA)
12 -
Devtoberfest
2 -
Digital Transformation with Cloud ERP (DT)
4 -
Digital Transformation with SAP S-4HANA (DT)
6 -
Expert Session
2 -
General
28 -
Integration (IN)
11 -
Keynote
5 -
Playlist
3 -
SAP Business Technology Platform (XP)
1 -
SAP Business Technology Platform - General (XP)
24 -
SAP Business Technology Platform General (XP)
5 -
Strategy Talk
1 -
Track Teaser Video
7 -
Track:App Dev & Integration
2 -
Track:Database & Data Management
1 -
Track:Intelligent Technologies
1 -
Use Case
11