
- SAP Community
- Products and Technology
- Human Capital Management
- HCM Blogs by Members
- Bidirectional integration between SAP SuccessFacto...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In section, we will focus on the Technical configuration for SAP SuccessFactors to Azure Active Directory user provisioning.
Note:
For this demonstration, I have already created an Azure AD tenant and using SAP SuccessFactors & Azure trail account for the POC.
Steps need to perform in SAP SuccessFactors
Step 1: Create an API user in SuccessFactors
Create a API user creation (Example : sfapi2) request to the SuccessFactors admin .
Step 2: Create an API permissions role
2.1 Log in to SAP SuccessFactors with a user account that has access to the Admin Centre.
2.2 Search for Manage Permission Roles, then select Manage Permission Roles from the search results.

2.3 From the Permission Role List, click Create New.
2.4 Add a Role Name and Description for the new permission role. The name and description should indicate that the role is for API usage permissions.

2.5 Under Permission settings, click Permission.

2.6 Scroll down the permission list and click Manage Integration Tools. Check the box for Allow Admin to Access to OData API through Basic Authentication.

2.7 Scroll down in the same box and select Employee Central API. Add permissions as shown below to read using ODATA API and edit using ODATA API. Select the edit option as we plan to use the same account for the Writeback to SuccessFactors scenario.

2.8 In the same permissions box, go to User Permissions -> Employee Data and review the attributes that the service account can read from the SuccessFactors tenant.
Review the attributes "Employee Profile " and select the Email and Check the box for the read and write.
Make sure read option is enable for all attributes.

2.9 Click on Done. Click Save Changes.

Step 3: Create a Permission Group for the API user
3.1 In the SuccessFactors Admin Center, search for Manage Permission Groups, then select Manage Permission Groups from the search results.

3.2 From the Manage Permission Groups window, click Create New.

3.3 Add a Group Name for the new group. The group name should indicate that the group is for API users.

3.4 Add SFAPI2 user to the group.

3.5 Click Done to finish creating the Permission Group.

Step 4: Grant Permission Role to the Permission Group
4.1 In SuccessFactors Admin Center, search for Manage Permission Roles, then select Manage Permission Roles from the search results.
 4.2 From the Permission Role List, select the role that you created for API usage permissions.
4.2 From the Permission Role List, select the role that you created for API usage permissions.
4.3 Under Grant the role , click Add button.
4.4 Select Permission Group from the drop-down menu, then click Select to open the Groups window to search and select the group created above.
4.5 Review the Permission Role grant to the Permission Group.

4.6 Click Save Changes.
Steps need to perform in Microsoft Azure AD
Step 5: Add the provisioning connector app and download the Provisioning Agent
5.1 Login azure portal
5.2 In the left navigation bar, select Azure Active Directory
5.3 Select Enterprise Applications

5.4 Click on All application and Select Add new application

5.5 Search for "SuccessFactors to Azure Active Directory User Provisioning" and select

5.6 Click on create and add that app from the gallery.

5.7 Wait till adding the application "SuccessFactors to Azure Active Directory User Provisioning "

5.8 After the app is added and the app details screen is shown, select Provisioning

5.9 Change the Provisioning Mode to Automatic

5.10 Complete the Admin Credentials section as follows and click the Test Connection button.

5.11 If the connection test succeeds, click the Save button at the top. If it fails, double-check that the SuccessFactors credentials and URL are valid.



5.12 Once the credentials are saved successfully, the Mappings section will display the default mapping Synchronize SuccessFactors Users to Azure Active Directory

Step 6: Configure attribute mappings
6.1 On the Provisioning tab under Mappings, click Synchronize SuccessFactors Users to Azure Active Directory.
6.2 In the Source Object Scope field, you can select which sets of users in SuccessFactors should be in scope for provisioning to Azure AD, by defining a set of attribute-based filters.
The default scope is "all users in SuccessFactors"

6.3 In the Target Object Actions field, you can globally filter what actions are performed on Active Directory. Create and Update are most common.

6.4 In the Attribute mappings section, you can define how individual SuccessFactors attributes map to Active Directory attributes.

6.5 Click on an existing attribute mapping to update it, or click Add new mapping at the bottom of the screen to add new mappings.
6.6 To save your mappings, click Save at the top of the Attribute-Mapping section.
Once your attribute mapping configuration is complete, you can now enable and launch the user provisioning service.
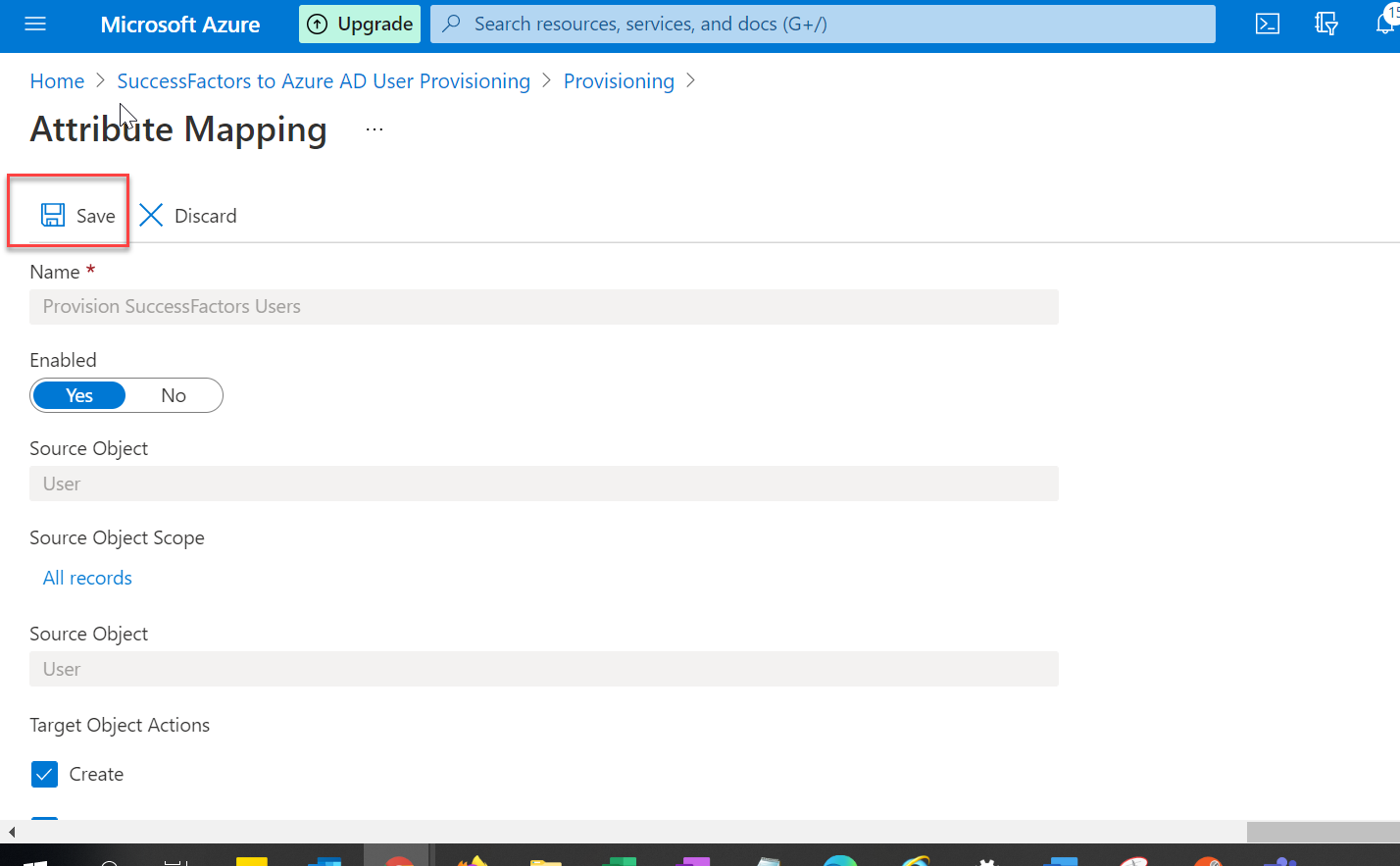


Once the SuccessFactors provisioning app configurations have been completed, you can turn on the provisioning service in the Azure portal.
Step 7: Enable and launch user provisioning
7.1 In the Provisioning tab, check the status.

7.2 set the Provisioning Status to On and Click Save.

7.3 This operation will start the initial sync, which can take a variable number of hours depending on how many users are in the SuccessFactors tenant. You can check the progress bar to the track the progress of the sync cycle.


7.4 At any time, check the Audit logs tab in the Azure portal to see what actions the provisioning service has performed. The audit logs lists all individual sync events performed by the provisioning service, such as which users are being read out of Workday and then subsequently added or updated to Active Directory.
7.5 Once the initial sync is completed, it will write an audit summary report in the Provisioning tab, as shown below.

Jump to Part 2 - Technical configuration for SuccessFactors Writeback to continue with the Technical configuration fo....
- SAP Managed Tags:
- SAP SuccessFactors Employee Central,
- SAP SuccessFactors platform,
- SAP Single Sign-On,
- Cloud Operations
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
1H 2024 Product Release
1 -
2H 2023 Product Release
1 -
ACCRUAL TRANSFER
1 -
Advanced Workflow
1 -
Anonymization
1 -
BTP
1 -
Business Rules
1 -
Canvas Report
1 -
Career Development
1 -
Certificate-Based Authentication
1 -
Cloud Platform Integration
1 -
Compensation
1 -
Compensation Information Management
1 -
Compensation Management
1 -
Compliance
2 -
Content
1 -
Conversational AI
2 -
Custom Data Collection
1 -
custom portlet
1 -
Data & Analytics
1 -
Data Integration
1 -
Dayforce
1 -
deep link
1 -
deeplink
1 -
Delimiting Pay Components
1 -
Deprecation
1 -
Employee Central
1 -
Employee Central Global Benefits
1 -
Employee Central Payroll
1 -
employee profile
1 -
Employee Rehires
1 -
external terminal
1 -
external time events
1 -
Generative AI
2 -
Getting Started
1 -
Global Benefits
1 -
Guidelines
1 -
H2 2023
1 -
HR
2 -
HR Data Management
1 -
HR Transformation
1 -
ilx
1 -
Incentive Management Setup (Configuration)
1 -
Integration Center
2 -
Integration Suite
1 -
internal mobility
1 -
Introduction
1 -
learning
3 -
LMS
2 -
LXP
1 -
Massively MDF attachments download
1 -
Mentoring
1 -
Metadata Framework
1 -
Middleware Solutions
1 -
OCN
1 -
OData APIs
1 -
ONB USA Compliance
1 -
Onboarding
2 -
Opportunity Marketplace
1 -
Pay Component Management
1 -
Platform
1 -
portlet
1 -
POSTMAN
1 -
Predictive AI
2 -
Recruiting
1 -
recurring payments
1 -
Role Based Permissions (RBP)
2 -
SAP CPI (Cloud Platform Integration)
1 -
SAP HCM (Human Capital Management)
2 -
SAP HR Solutions
2 -
SAP Integrations
1 -
SAP release
1 -
SAP SuccessFactors
5 -
SAP SuccessFactors Customer Community
1 -
SAP SuccessFactors OData API
1 -
SAP Workzone
1 -
SAP-PAYROLL
1 -
skills
1 -
Skills Management
1 -
sso deeplink
1 -
Stories in People Analytics
3 -
Story Report
1 -
SuccessFactors
2 -
SuccessFactors Employee central home page customization.
1 -
successfactors onboarding i9
1 -
Table Report
1 -
talent
1 -
Talent Intelligence Hub
2 -
talents
1 -
Tax
1 -
Tax Integration
1 -
Time Accounts
1 -
Workflows
1 -
XML Rules
1
- Standard integration templates in Talent Intelligence Hub in Human Capital Management Blogs by SAP
- Simplifying Employee and Manager Experiences with Employee Central Quick Actions in Human Capital Management Blogs by SAP
- Country Compliance - Configure overrides for US WTPA Form fields in Human Capital Management Blogs by SAP
- Career Development planning implementation in Human Capital Management Q&A
- Deep linking to SAP SuccessFactors Standard Portlets and Custom MDF portlets in Human Capital Management Blogs by Members
| User | Count |
|---|---|
| 4 | |
| 4 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |