
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- SAP Identity Authentication (IAS) Security Feature...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Hi All,
This article is an overview of security-relevant information that applies to SAP Identity Authentication and contains recommendations about how administrators should secure it.
While this article is intended to support administrators and security responsible specialists to use Identity Authentication in a secure manner, there may be further elements to consider depending on usage, integrations as well as applicable industry or local legal country regulations.
👉 Data Protection & Privacy

Communication Protocol
Identity Authentication is a full web browser-based application, with all access over HTTPS. Every page of the Identity Authentication application is currently delivered via Transport Layer Security (TLS). Access to Identity Authentication is encrypted-in-transit over HTTPS using 256-bit TLS encryption.
Password Security
Identity Authentication does not store plain text passwords in the database, but only their iterated random-salted secure hash values. The random salt is at least 512 bits, and it is different for each password. Only generic hash functions are used with a minimum of 512 bits key length. No default passwords are delivered, used, or accepted anywhere.
Identity Authentication can use also passwords from on-premise systems for user authentication. These passwords are not stored by Identity Authentication. It sends the user ID and the password for authentication to the on-premise system via the Transport Layer Security (TLS) connection. The management of these passwords depends on the integrated on-premise system that supports them, for example, Microsoft Active Directory.
Identity Authentication supports three levels of password security. You should use the highest level of security that matches the requirements of your application. The passwords are managed based on password policy rules. For more information, see Configuring Password Policies.
Session Security
Session cookies in Identity Authentication are protected with a Transport Layer Security (TLS) and with the Secure and HttpOnly attributes. You do not need to make any additional configurations for Identity Authentication.
Network and Communication Security
Identity Authentication is set up in a fenced network, separated from the SAP internal network.
Customer applications run in a shared environment where the business data is isolated from each other, the SAP BTP services use a shared SAP BTP infrastructure. The internal traffic is controlled by firewalls. SAP administrative access is done via a terminal service that requires strong authentication.
All communication channels are protected with TLS, and you should configure the cloud application to use TLS and to check the SAML 2.0 signature.
Data Storage Security
Data storage security is about how Identity Authentication protects its own database. Data storage security is ensured by the isolated tenant that each customer receives. Only tenant-specific requests can access the tenant's database. These requests are performed by a tenant service, which works with a dependency injection framework and makes sure that all the services, for example, the persistence service and the mail service, are injected with the instances dedicated to the given tenant.
Security-Relevant Logging and Tracing
You can download a CSV file with a history of operations performed by administrators. For more information, see Export Change Logs with a History of Administration Operations.
You can retrieve the statistics on the number of user logon requests per month. This number is counted on every single authentication managed via Identity Authentication. For more information, see View Usage Statistics.

➡️Block or Delete Users Due to Inactivity
Tenant administrators can configure specific user types to be blocked and deleted, or only blocked, or only deleted after a certain period of inactivity.

Blocking and Deletion
- Choose a user type and enable it.
- Configure at least one of the periods: Delete after or Block after.

Note:
The automatic configuration is based on the current date plus the days specified in the Delete after a period. The deletion process starts from the chosen date and is executed nightly at 04:00 UTC.

➡️Security Alerting
Send security alert e-mails to end-users or administrators when changes in their accounts are made.


➡️Password Policies
Passwords for the authentication of users are subject to certain rules. These rules are defined in the password policy. Identity Authentication provides you with two predefined password policies, in addition to which you can create and configure a custom one.
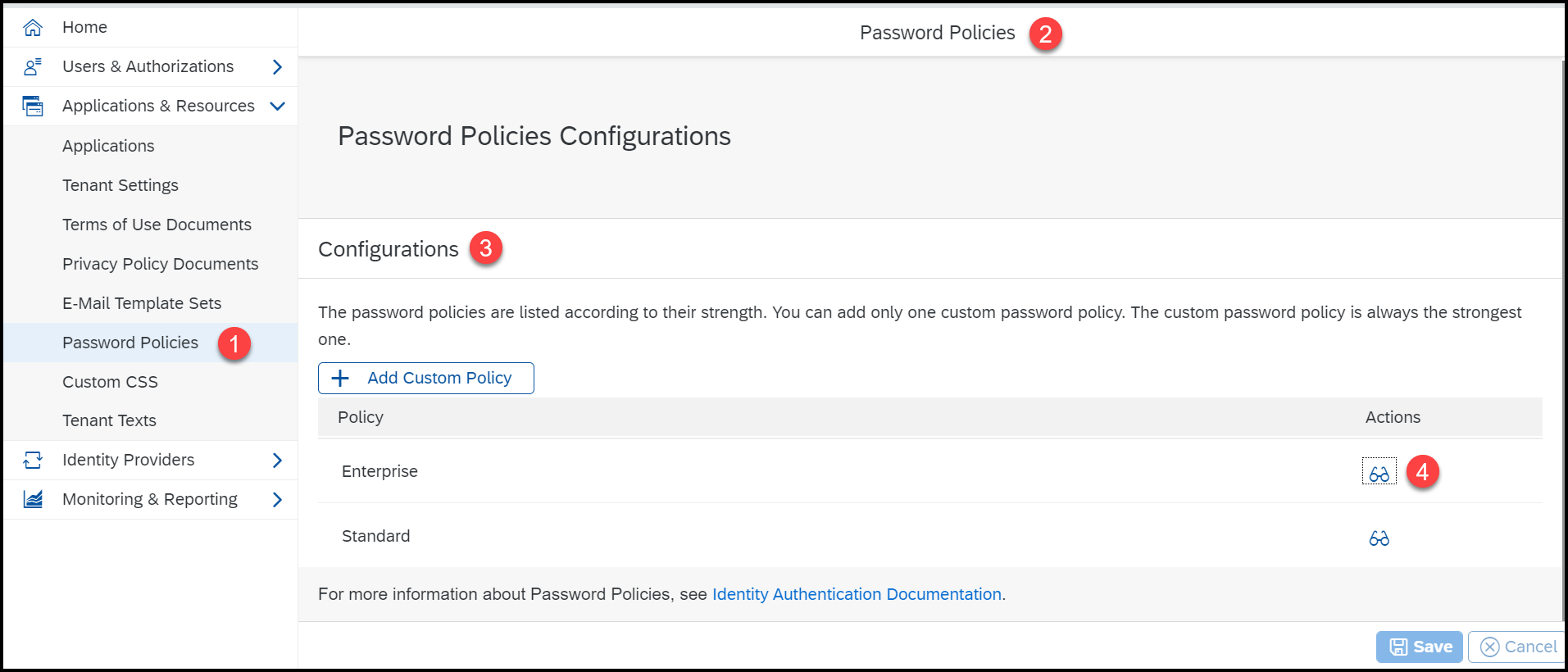
Enterprise Password Policy
(Predefined) Use this option to set enhanced password management features. It is stronger than the standard policy but weaker than the custom one.

Custom Password Policy
(Configurable) Use this option to set the strongest password management features for the password policy.
This option is only possible if you have configured a custom password policy in the administration console for Identity Authentication. For more information, see Configure Custom Password Policy.


➡️Session Timeout
As a tenant administrator, you can configure when the session, created at the Identity Authentication tenant, expires.


➡️Enable Multi-Factor Authentication
Below is the steps to be followed by an Admin to enable 2MFA (2-factor/ Multi-Factor Authentication)
Based on the configurations for the application, you can be asked to provide a time-based, one-time (TOTP) passcode, generated on a mobile device, a passcode sent via SMS, or a PIN security key. You can choose one of the enabled second-factor authentication methods or press the button to enable a new method.


Product Updates and Notifications
Identity Authentication has production releases (updates) every second Wednesday, 10:00 UTC. For more information about the features delivered every task, see the What's New for Identity Authentication published regularly. To get notifications for the new features and fixes every release, subscribe to the SAP Community wiki
 by choosing the Watch icon.
by choosing the Watch icon.Reasons for Updates
- Bi-weekly updates (standard) - planned each second Wednesday at 10:00 UTC.
- Immediate updates - in case of fixes required for bugs that affect productive application operations, or due to urgent security fixes.
➡️References
SAP IAS Product Documentation
SAP IPS Product Documentation
- SAP Managed Tags:
- SAP BTP Security,
- SAP Cloud Identity Services,
- SAP Cloud Identity Access Governance,
- Security
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
91 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
66 -
Expert
1 -
Expert Insights
178 -
Expert Insights
293 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
12 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
340 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
416 -
Workload Fluctuations
1
- Onboarding Users in SAP Quality Issue Resolution in Technology Blogs by SAP
- What’s new in Mobile development kit client 24.4 in Technology Blogs by SAP
- Mistral gagnant. Mistral AI and SAP Kyma serverless. in Technology Blogs by SAP
- Creating a JDBC Connection for Google BigQuery using SSO with Oauth 2.0 in Technology Q&A
- SAP HANA Cloud Vector Engine: Quick FAQ Reference in Technology Blogs by SAP
| User | Count |
|---|---|
| 30 | |
| 23 | |
| 10 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 4 |