
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by Members
- Resolve annoying self-signed SSL certificate issue...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
I'll share in a few simple steps, how I was able to generate my own local root CA with OpenSSL and use that to sign the SSL certificate that comes delivered in ABAP 1909 Developer Edition (CN=*.dummy.nodomain) to get rid of the annoying browser warning messages when accessing any URLs served through HTTPS on this local ABAP development environment.
Basically, we go from this....
Annoying browser error and SSL status that says Not secure
to this on Safari in MacOS or Chrome in Windows....



Ahhh...much better! A complete, no error valid SSL on a local ABAP dev server
Introduction
The ABAP 1909 Developer Edition comes with a self-signed certificate that will technically serve "secure" HTTPS traffic for local development but browsers and even some API software/tools today frown upon self-signed certificates so much so that they labelled it as "Not secure" or just wouldn't work with it - I am really over simplifying the reason here...
While looking around for some ideas, I came across this page on Let's Encrypt's website - https://letsencrypt.org/docs/certificates-for-localhost/ where it says and I quote below...
The best option: Generate your own certificate, either self-signed or signed by a local root, and trust it in your operating system’s trust store. Then use that certificate in your local web server.
So, first of all, we already have our own certificate that's self-signed on the local ABAP server - what's missing is just
- Generating the local root CA using OpenSSL
- Trust the local root CA it in Windows / MacOS.
- Add the local root CA into SAP using transaction STRUST
- And then finally, use OpenSSL again to sign the SSL certificate that's already on the ABAP server and import the certificate response back to the ABAP server.
4 simple steps - Let's get to it!
Prerequisite - You will need OpenSSL
You can get OpenSSL for Windows here - https://slproweb.com/products/Win32OpenSSL.html and I downloaded the Win64 version for my Windows 10 machine.
For MacOS - you simply need to run the following command in terminal.
brew install openssl
#or#
brew upgrade opensslStep 1 - Generate Local Certificate Authority with OpenSSL - 2mins
If you refer to Let's Encrypt's page above, it mentioned that you could use minica as a local root CA to sign and issue your certificates and it would be valid for 2 years and 30 days. This feels a little overkill for my use case of just trying to sign a single SSL for the ABAP server so, I opted for a complete manual way with OpenSSL - and it only takes 2 simple command.
The first command is to create a private key that is 2048 bits long and this will prompt you to enter a password to create the key file. I entered something simple like '12345' as the password.
openssl genrsa -des3 -out rootCA.key 2048
And with that private key generated, we will now use it to generate the root certificate using the following command below. You will be prompted to enter the password that you've created for the key in the step above and also enter some basic information for the local CA.
openssl req -x509 -new -nodes -key rootCA.key -sha256 -days 9999 -out rootCA.pem
That's it! We now have a local root CA (called ALBAN LOCAL CA - in my example above) certificate rootCA.pem that we can now use in the next step to trust it in Windows / MacOS and also in Step 3, to save it into our ABAP server as a Root CA.
Step 2 - Trust the local root CA in Windows / MacOS - 3 mins
Here are the steps for adding the local root CA to Windows.
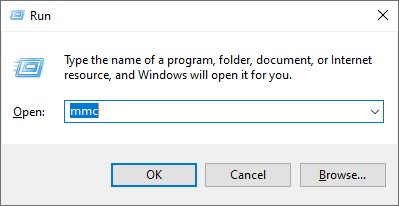
Step 2.1 (Windows)
2.1 (Windows) - Click on Start and Run > mmc

Step 2.2 (Windows)
2.2 (Windows) - Click on "File" > "Add/Remove Snap-in" to add the "Certificates" Snap-in (or Ctrl + M)
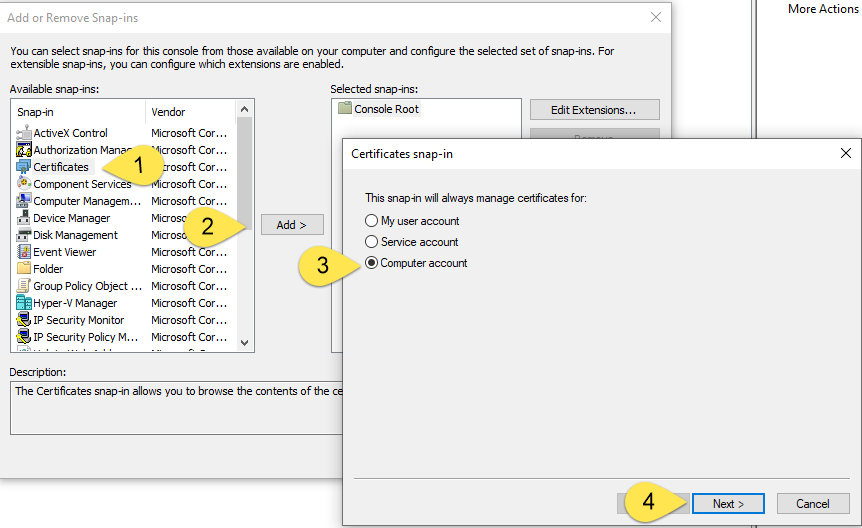
Step 2.3 (Windows)
2.3 (Windows) - Select manage certificates for "Computer account" and snap-in will always manage the "Local computer" in the next two prompt windows and click "Finish"

Step 2.4 (Windows)
2.4 (Windows) Double-click on "Trusted Root Certification Authorities" and in the Object Type window - Right-Click on "Certificates" > All Tasks > Import

Step 2.5 (Windows)
2.5 (Windows) - Click "Next" to advance to the next window and select the local root CA certificate "rootCA.pem" file that was generated earlier.

Step 2.6 (Windows)
2.6 (Windows) - Click "Next" again till you get to the end and save the certificate in "Trusted Root Certification Authorities".
2.7 (Windows) - Repeat step 4 - 6 above but this time, import the certificate into "Personal" > "Certificates" folder.
Here are the steps for adding the local root CA to MacOS and trust it.

Step 2.1 (Mac)
2.1 (Mac) - Run Keychain Access in Spotlight (Cmd + Space)

Step 2.2 (Mac)
2.2 (Mac) - Drag and drop the "rootCA.pem" file into the "System" keychain

Step 2.3 (Mac)
2.3 (Mac) - You should now see that the Certificate has been added but by default, it is still not trusted.

Step 2.4 (Mac)
2.4 (Mac) - Double-click on the certificate and in the "Trusted" section, change the drop-down to "Always Trust". This should then change all the other options below down to "Always Trust" as well.

Step 2.5 (Mac)
2.5 (Mac) - Close the window and now, it should show that the local root CA certificate is now trusted!
Step 3 - Add the local root CA to ABAP server (STRUST) - 5 mins
Now, we head into the ABAP server and add the local root CA certificate (rootCA.pem) in transaction STRUST. We have to first import the certificate, add it to the certificate list and then export the certificate as a Trust CA into the database table VSTRUSTCERT.

Step 3.1 (STRUST)
3.1 - Double click on "SSL client SSL Client (Standard)" folder and click on "Change".

Step 3.2 (STRUST)
3.2 - Import the certificate by selecting "Certificate" > "Import".

Step 3.3 (STRUST)
3.3 - Browse or enter the path to the "rootCA.pem" certificate file and click on the green tick.

Step 3.4 (STRUST)
3.4 - You should see the certificate details in the lower screen and click on the button "Add to Certificate List" (VERY IMPORTANT STEP). If the "Add to Certificate List" button is not active, means you're still not in Change mode.

Step 3.5 (STRUST)
3.5 - With the newly added local root CA certificate still selected, we now export this to the database as a Root CA by selecting "Certificate" > "Export".

Step 3.6 (STRUST)
3.6 - Click over to the "Database" tab and fill in the Trust Center, select Root CA as the Category and enter a Description. Make sure to prefix the Trust Center naming with a "Z". Click the green tick and you should get a success message that says "Certificate saved in database". This would then automatically create a new entry in the table VSTRUSTCERT. You can validate this by selecting "Certificate" > "Database" and you should see the newly created Root CA in the table.
Step 4 - Create a Certificate Signing Request, sign existing SSL cert in ABAP server with the local root CA and import the certificate response back into ABAP server - 5 mins
This are the last few remaining steps in transaction STRUST and also one more OpenSSL command. We're almost there... I promise.

Step 4.1 (STRUST)
4.1 - In STRUST - Double-click on "SSL server Standard" folder and click on the button "Create certificate request". Here, select SHA256 as the algorithm and also enter "*.dummy.nodomain" in the Alternative Owner Name (SAN) table.

Step 4.2 (STRUST)
4.2 - Save the certificate request as a local file and name it "server.csr" and save it in the same folder as the local root CA key and certificate.

Step 4.3 (EXT file)
4.3 - Now, in order to have a certificate that meets today's SSL standard, we will need to include in the certificate the Subject Alternative Names (SAN). To do this, using Notepad, create a file called “v3.ext” and enter the following into the file and SAVE it.
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
subjectAltName = @alt_names
[alt_names]
DNS.1 = *.dummy.nodomain
DNS.2 = vhcala4hci
Step 4.4 (OpenSSL)
4.4 - Using OpenSSL again, we run the following command to finally sign and issue a new SSL certificate (server.crt) using all the other files that we've generated so far. You will be prompted again for the password for the local root CA key.
openssl x509 -req -in server.csr -CA rootCA.pem -CAkey rootCA.key -CAcreateserial -out server.crt -days 999 -sha256 -extfile v3.ext
Step 4.5 (STRUST)
4.5 - Last and final step - in STRUST transaction, we import the signed certificate response (server.crt) file back into the ABAP server and remember to hit that "SAVE" button. You should see a success message that says "SSL PSE was saved!".
And we're DONE!
Our ABAP 1909 Developer Edition server is now capable of serving valid HTTPS urls and OData services that browsers and other software/tools will love (limited to your local computer :)). Oh and you don't even need to restart ICM because that's already being taken care of automatically...


ICM has been notified automatically.. w00t!
Hope you've liked this blog post and found it useful!
Note: Although I’m using the ABAP 1909 Developer Edition in this blog post, the steps above should also work for the previous ABAP Developer Editions.
Suggestion, maybe next time in the future, SAP can perhaps deliver the ABAP Dev Edition server along with a local root CA certificate (rootCA.PEM) and the SSL that’s signed with it. That way, we only need to do Step 2 of trusting the local root CA in the process above. Wishful/Hopeful thinking!
- SAP Managed Tags:
- ABAP Development,
- SAP NetWeaver Application Server for ABAP
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
"automatische backups"
1 -
"regelmäßige sicherung"
1 -
505 Technology Updates 53
1 -
ABAP
14 -
ABAP API
1 -
ABAP CDS Views
2 -
ABAP CDS Views - BW Extraction
1 -
ABAP CDS Views - CDC (Change Data Capture)
1 -
ABAP class
2 -
ABAP Cloud
2 -
ABAP Development
5 -
ABAP in Eclipse
1 -
ABAP Platform Trial
1 -
ABAP Programming
2 -
abap technical
1 -
absl
1 -
access data from SAP Datasphere directly from Snowflake
1 -
Access data from SAP datasphere to Qliksense
1 -
Accrual
1 -
action
1 -
adapter modules
1 -
Addon
1 -
Adobe Document Services
1 -
ADS
1 -
ADS Config
1 -
ADS with ABAP
1 -
ADS with Java
1 -
ADT
2 -
Advance Shipping and Receiving
1 -
Advanced Event Mesh
3 -
AEM
1 -
AI
7 -
AI Launchpad
1 -
AI Projects
1 -
AIML
9 -
Alert in Sap analytical cloud
1 -
Amazon S3
1 -
Analytical Dataset
1 -
Analytical Model
1 -
Analytics
1 -
Analyze Workload Data
1 -
annotations
1 -
API
1 -
API and Integration
3 -
API Call
2 -
Application Architecture
1 -
Application Development
5 -
Application Development for SAP HANA Cloud
3 -
Applications and Business Processes (AP)
1 -
Artificial Intelligence
1 -
Artificial Intelligence (AI)
4 -
Artificial Intelligence (AI) 1 Business Trends 363 Business Trends 8 Digital Transformation with Cloud ERP (DT) 1 Event Information 462 Event Information 15 Expert Insights 114 Expert Insights 76 Life at SAP 418 Life at SAP 1 Product Updates 4
1 -
Artificial Intelligence (AI) blockchain Data & Analytics
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise Oil Gas IoT Exploration Production
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise sustainability responsibility esg social compliance cybersecurity risk
1 -
ASE
1 -
ASR
2 -
ASUG
1 -
Attachments
1 -
Authorisations
1 -
Automating Processes
1 -
Automation
1 -
aws
2 -
Azure
1 -
Azure AI Studio
1 -
B2B Integration
1 -
Backorder Processing
1 -
Backup
1 -
Backup and Recovery
1 -
Backup schedule
1 -
BADI_MATERIAL_CHECK error message
1 -
Bank
1 -
BAS
1 -
basis
2 -
Basis Monitoring & Tcodes with Key notes
2 -
Batch Management
1 -
BDC
1 -
Best Practice
1 -
bitcoin
1 -
Blockchain
3 -
BOP in aATP
1 -
BOP Segments
1 -
BOP Strategies
1 -
BOP Variant
1 -
BPC
1 -
BPC LIVE
1 -
BTP
11 -
BTP Destination
2 -
Business AI
1 -
Business and IT Integration
1 -
Business application stu
1 -
Business Architecture
1 -
Business Communication Services
1 -
Business Continuity
1 -
Business Data Fabric
3 -
Business Partner
12 -
Business Partner Master Data
10 -
Business Technology Platform
2 -
Business Trends
1 -
CA
1 -
calculation view
1 -
CAP
3 -
Capgemini
1 -
CAPM
1 -
Catalyst for Efficiency: Revolutionizing SAP Integration Suite with Artificial Intelligence (AI) and
1 -
CCMS
2 -
CDQ
12 -
CDS
2 -
Cental Finance
1 -
Certificates
1 -
CFL
1 -
Change Management
1 -
chatbot
1 -
chatgpt
3 -
CL_SALV_TABLE
2 -
Class Runner
1 -
Classrunner
1 -
Cloud ALM Monitoring
1 -
Cloud ALM Operations
1 -
cloud connector
1 -
Cloud Extensibility
1 -
Cloud Foundry
3 -
Cloud Integration
6 -
Cloud Platform Integration
2 -
cloudalm
1 -
communication
1 -
Compensation Information Management
1 -
Compensation Management
1 -
Compliance
1 -
Compound Employee API
1 -
Configuration
1 -
Connectors
1 -
Consolidation Extension for SAP Analytics Cloud
1 -
Controller-Service-Repository pattern
1 -
Conversion
1 -
Cosine similarity
1 -
cryptocurrency
1 -
CSI
1 -
ctms
1 -
Custom chatbot
3 -
Custom Destination Service
1 -
custom fields
1 -
Customer Experience
1 -
Customer Journey
1 -
Customizing
1 -
Cyber Security
2 -
Data
1 -
Data & Analytics
1 -
Data Aging
1 -
Data Analytics
2 -
Data and Analytics (DA)
1 -
Data Archiving
1 -
Data Back-up
1 -
Data Governance
5 -
Data Integration
2 -
Data Quality
12 -
Data Quality Management
12 -
Data Synchronization
1 -
data transfer
1 -
Data Unleashed
1 -
Data Value
8 -
database tables
1 -
Datasphere
2 -
datenbanksicherung
1 -
dba cockpit
1 -
dbacockpit
1 -
Debugging
2 -
Delimiting Pay Components
1 -
Delta Integrations
1 -
Destination
3 -
Destination Service
1 -
Developer extensibility
1 -
Developing with SAP Integration Suite
1 -
Devops
1 -
digital transformation
1 -
Documentation
1 -
Dot Product
1 -
DQM
1 -
dump database
1 -
dump transaction
1 -
e-Invoice
1 -
E4H Conversion
1 -
Eclipse ADT ABAP Development Tools
2 -
edoc
1 -
edocument
1 -
ELA
1 -
Embedded Consolidation
1 -
Embedding
1 -
Embeddings
1 -
Employee Central
1 -
Employee Central Payroll
1 -
Employee Central Time Off
1 -
Employee Information
1 -
Employee Rehires
1 -
Enable Now
1 -
Enable now manager
1 -
endpoint
1 -
Enhancement Request
1 -
Enterprise Architecture
1 -
ETL Business Analytics with SAP Signavio
1 -
Euclidean distance
1 -
Event Dates
1 -
Event Driven Architecture
1 -
Event Mesh
2 -
Event Reason
1 -
EventBasedIntegration
1 -
EWM
1 -
EWM Outbound configuration
1 -
EWM-TM-Integration
1 -
Existing Event Changes
1 -
Expand
1 -
Expert
2 -
Expert Insights
1 -
Fiori
14 -
Fiori Elements
2 -
Fiori SAPUI5
12 -
Flask
1 -
Full Stack
8 -
Funds Management
1 -
General
1 -
Generative AI
1 -
Getting Started
1 -
GitHub
8 -
Grants Management
1 -
groovy
1 -
GTP
1 -
HANA
5 -
HANA Cloud
2 -
Hana Cloud Database Integration
2 -
HANA DB
1 -
HANA XS Advanced
1 -
Historical Events
1 -
home labs
1 -
HowTo
1 -
HR Data Management
1 -
html5
8 -
Identity cards validation
1 -
idm
1 -
Implementation
1 -
input parameter
1 -
instant payments
1 -
Integration
3 -
Integration Advisor
1 -
Integration Architecture
1 -
Integration Center
1 -
Integration Suite
1 -
intelligent enterprise
1 -
Java
1 -
job
1 -
Job Information Changes
1 -
Job-Related Events
1 -
Job_Event_Information
1 -
joule
4 -
Journal Entries
1 -
Just Ask
1 -
Kerberos for ABAP
8 -
Kerberos for JAVA
8 -
Launch Wizard
1 -
Learning Content
2 -
Life at SAP
1 -
lightning
1 -
Linear Regression SAP HANA Cloud
1 -
local tax regulations
1 -
LP
1 -
Machine Learning
2 -
Marketing
1 -
Master Data
3 -
Master Data Management
14 -
Maxdb
2 -
MDG
1 -
MDGM
1 -
MDM
1 -
Message box.
1 -
Messages on RF Device
1 -
Microservices Architecture
1 -
Microsoft Universal Print
1 -
Middleware Solutions
1 -
Migration
5 -
ML Model Development
1 -
Modeling in SAP HANA Cloud
8 -
Monitoring
3 -
MTA
1 -
Multi-Record Scenarios
1 -
Multiple Event Triggers
1 -
Neo
1 -
New Event Creation
1 -
New Feature
1 -
Newcomer
1 -
NodeJS
2 -
ODATA
2 -
OData APIs
1 -
odatav2
1 -
ODATAV4
1 -
ODBC
1 -
ODBC Connection
1 -
Onpremise
1 -
open source
2 -
OpenAI API
1 -
Oracle
1 -
PaPM
1 -
PaPM Dynamic Data Copy through Writer function
1 -
PaPM Remote Call
1 -
PAS-C01
1 -
Pay Component Management
1 -
PGP
1 -
Pickle
1 -
PLANNING ARCHITECTURE
1 -
Popup in Sap analytical cloud
1 -
PostgrSQL
1 -
POSTMAN
1 -
Process Automation
2 -
Product Updates
4 -
PSM
1 -
Public Cloud
1 -
Python
4 -
Qlik
1 -
Qualtrics
1 -
RAP
3 -
RAP BO
2 -
Record Deletion
1 -
Recovery
1 -
recurring payments
1 -
redeply
1 -
Release
1 -
Remote Consumption Model
1 -
Replication Flows
1 -
Research
1 -
Resilience
1 -
REST
1 -
REST API
1 -
Retagging Required
1 -
Risk
1 -
Rolling Kernel Switch
1 -
route
1 -
rules
1 -
S4 HANA
1 -
S4 HANA Cloud
1 -
S4 HANA On-Premise
1 -
S4HANA
3 -
S4HANA_OP_2023
2 -
SAC
10 -
SAC PLANNING
9 -
SAP
4 -
SAP ABAP
1 -
SAP Advanced Event Mesh
1 -
SAP AI Core
8 -
SAP AI Launchpad
8 -
SAP Analytic Cloud Compass
1 -
Sap Analytical Cloud
1 -
SAP Analytics Cloud
4 -
SAP Analytics Cloud for Consolidation
2 -
SAP Analytics Cloud Story
1 -
SAP analytics clouds
1 -
SAP BAS
1 -
SAP Basis
6 -
SAP BODS
1 -
SAP BODS certification.
1 -
SAP BTP
20 -
SAP BTP Build Work Zone
2 -
SAP BTP Cloud Foundry
5 -
SAP BTP Costing
1 -
SAP BTP CTMS
1 -
SAP BTP Innovation
1 -
SAP BTP Migration Tool
1 -
SAP BTP SDK IOS
1 -
SAP Build
11 -
SAP Build App
1 -
SAP Build apps
1 -
SAP Build CodeJam
1 -
SAP Build Process Automation
3 -
SAP Build work zone
10 -
SAP Business Objects Platform
1 -
SAP Business Technology
2 -
SAP Business Technology Platform (XP)
1 -
sap bw
1 -
SAP CAP
2 -
SAP CDC
1 -
SAP CDP
1 -
SAP Certification
1 -
SAP Cloud ALM
4 -
SAP Cloud Application Programming Model
1 -
SAP Cloud Integration for Data Services
1 -
SAP cloud platform
8 -
SAP Companion
1 -
SAP CPI
3 -
SAP CPI (Cloud Platform Integration)
2 -
SAP CPI Discover tab
1 -
sap credential store
1 -
SAP Customer Data Cloud
1 -
SAP Customer Data Platform
1 -
SAP Data Intelligence
1 -
SAP Data Migration in Retail Industry
1 -
SAP Data Services
1 -
SAP DATABASE
1 -
SAP Dataspher to Non SAP BI tools
1 -
SAP Datasphere
9 -
SAP DRC
1 -
SAP EWM
1 -
SAP Fiori
2 -
SAP Fiori App Embedding
1 -
Sap Fiori Extension Project Using BAS
1 -
SAP GRC
1 -
SAP HANA
1 -
SAP HCM (Human Capital Management)
1 -
SAP HR Solutions
1 -
SAP IDM
1 -
SAP Integration Suite
9 -
SAP Integrations
4 -
SAP iRPA
2 -
SAP Learning Class
1 -
SAP Learning Hub
1 -
SAP Odata
2 -
SAP on Azure
1 -
SAP PartnerEdge
1 -
sap partners
1 -
SAP Password Reset
1 -
SAP PO Migration
1 -
SAP Prepackaged Content
1 -
SAP Process Automation
2 -
SAP Process Integration
2 -
SAP Process Orchestration
1 -
SAP S4HANA
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Cloud for Finance
1 -
SAP S4HANA Cloud private edition
1 -
SAP Sandbox
1 -
SAP STMS
1 -
SAP SuccessFactors
2 -
SAP SuccessFactors HXM Core
1 -
SAP Time
1 -
SAP TM
2 -
SAP Trading Partner Management
1 -
SAP UI5
1 -
SAP Upgrade
1 -
SAP-GUI
8 -
SAP_COM_0276
1 -
SAPBTP
1 -
SAPCPI
1 -
SAPEWM
1 -
sapmentors
1 -
saponaws
2 -
SAPUI5
4 -
schedule
1 -
Secure Login Client Setup
8 -
security
9 -
Selenium Testing
1 -
SEN
1 -
SEN Manager
1 -
service
1 -
SET_CELL_TYPE
1 -
SET_CELL_TYPE_COLUMN
1 -
SFTP scenario
2 -
Simplex
1 -
Single Sign On
8 -
Singlesource
1 -
SKLearn
1 -
soap
1 -
Software Development
1 -
SOLMAN
1 -
solman 7.2
2 -
Solution Manager
3 -
sp_dumpdb
1 -
sp_dumptrans
1 -
SQL
1 -
sql script
1 -
SSL
8 -
SSO
8 -
Substring function
1 -
SuccessFactors
1 -
SuccessFactors Time Tracking
1 -
Sybase
1 -
system copy method
1 -
System owner
1 -
Table splitting
1 -
Tax Integration
1 -
Technical article
1 -
Technical articles
1 -
Technology Updates
1 -
Technology Updates
1 -
Technology_Updates
1 -
Threats
1 -
Time Collectors
1 -
Time Off
2 -
Tips and tricks
2 -
Tools
1 -
Trainings & Certifications
1 -
Transport in SAP BODS
1 -
Transport Management
1 -
TypeScript
2 -
unbind
1 -
Unified Customer Profile
1 -
UPB
1 -
Use of Parameters for Data Copy in PaPM
1 -
User Unlock
1 -
VA02
1 -
Validations
1 -
Vector Database
1 -
Vector Engine
1 -
Visual Studio Code
1 -
VSCode
1 -
Web SDK
1 -
work zone
1 -
workload
1 -
xsa
1 -
XSA Refresh
1
- « Previous
- Next »
- How to configure odata Service to be readonly for technical user in Technology Q&A
- Top Picks: Innovations Highlights from SAP Business Technology Platform (Q1/2024) in Technology Blogs by SAP
- SAP GUI for Java 8.10 on the Horizon in Technology Blogs by SAP
- Query on plateau.com Certificate Renewal notification email in Technology Q&A
- SAP Successfactors Implementation and Maintenance in Projects in 2024 in Technology Blogs by Members
| User | Count |
|---|---|
| 11 | |
| 9 | |
| 7 | |
| 6 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |