
- SAP Community
- Products and Technology
- CRM and Customer Experience
- CRM and CX Blogs by Members
- SAP Commerce - Identity Management using Azure AD
CRM and CX Blogs by Members
Find insights on SAP customer relationship management and customer experience products in blog posts from community members. Post your own perspective today!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
former_member66
Explorer
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
02-04-2021
4:43 PM
Overview
User authentication and authorization is an integral part of any B2B or B2C implementation. Traditional approach is to maintain an on-premise LDAP directory to authenticate users.The customer’s profile is maintained in LDAP and is used for user authentication. This design approach works well for most of the commerce implementation. However, this design lacks to meet some of the modern day requirements introduced by social media and cloud adoption.
Historically commerce applications require a customer to share his/her identity by user registration.The customer needs to provide basic information which will be used to entitle customer for certain operations to a commerce site. If a customer has to register multiple sites, user needs to remember user ID password of each site. What if, a user brings his social media identity to register to a commerce site without worrying about long registration process and maintaining multiple log-in ID password for all sites.This capability was missing in traditional LDAP based authentication and authorization.
Authorization is another key aspect of cloud based identity management. If an enterprise has several applications, one needs to implement authorization in each application to control user access and provide the right access to the right users. This ends up lot of repeated work and need optimization. Cloud based identity management has addressed this issue by providing a centralized authorization process.
The recent industry trend has depicted a clear shift in direction from an on-premises based commerce implementation to a cloud based commerce implementation. A cloud based identity and access management solution is the natural choice for a cloud based commerce implementation.
LDAP based approach lacks the latest security feature like two factor authentication, self -service password reset etc. If a commerce application wants to adopt these features, it needs to be built from scratch which requires significant time and effort. There is no support for the smart brute force attack and requires custom development.
Commerce sector has evolved over a period of time and is offering a multi - channel platform to meet end user requirements. The capabilities and features offered by these channels varies based on business needs. To meet these requirements, commerce platform support various apps, e.g. Web apps, Mobile apps and front end heavy single page web apps ( e.g. Angular, Ract js). These apps have different security and authentication requirements and needs a unified approach to centrally manage authentication and authorization for each platform which is again a challenging task for the traditional LDAP based authentication approach.
The above points are some of the key pain points observed by commerce sector, which were difficult to solve with traditional identity management solution.The industry came up with cloud based identity management solution to address these challenges. The cloud based solution can handle millions of users and billions of authentication per day. The cloud platform has been designed to scale up as per transaction volume. It has best in class safety of the platform capable of automatically handling threats like denial of service, brute force attacks etc.
There are several players offering cloud based identity management solution. Microsoft is one of the dominant player in this space offering cloud based identity and access management.
Technical Considerations
Azure AD is Microsoft cloud based identity and access management solution. Microsoft Azure AD provides two flavors of cloud based identity management.
Microsoft Azure AD B2B : Microsoft Azure AD B2B allows business to business collaboration. Companies can share their applications and resources with a guest user’s organization without worrying about user roles with-in their organization.
Microsoft Azure AD B2C : Azure AD B2C provides business to customer interface for identity management as service. Customers user their preferred social media ,enterprise or government provided identity management to get access to the application.
The primary difference between B2B & B2C is B2B is meant for collaboration between partner and supplier organization. It uses Azure AD B2B to authenticate users and manage the life cycle of guest users. These accounts are managed in the same directory as employee and annotated as guest account.
B2C is meant for customers and other groups that does not require access to internal resources. These accounts are managed in a directory which is separate from internal user accounts. B2C accounts are either managed by customers or by the commerce application.
Azure AD provides several out of the box capability to meet the need of a commerce application. These features can be enabled through Azure AD portal by the click of a few buttons.
- Microsoft AAD leverages identity management by social media sites (E.g. Google, Facebook, LinkedIn etc.) along with the traditional approach of allowing user to register to the site.
- Single identity management can be leveraged by webapps, mobile apps , desktop apps and any other interface used.
- Avoid code duplicate : Usually every application needs to have a requirement of authentication and authorization. Azure AD takes care of this complexity by incorporating authentication and authorization service.
- Microsoft has provided several out of the box capabilities e.g. two factor authentication , self -service password reset. There are few OOB workflows policies. These polices can be used as it is to meet most of the requirements.
- Azure AD supports external identity .With external identities organizations can allow people outside your organization to access application and resources with-in your organizations using whatever identity they want to use. This allows external users to log-in local application accounts ,various supported social identities and users with corporate and government issued identities via direct federation.
- Single sign on to customer owned apps with-in Azure AD B2C is supported.
- Following application type can leverage Microsoft Azure AD as identity provider.
- Single page App rely heavily on front end technology developed in modern frameworks like Angular React etc.
- WebApps -> User apps used by users through browser.
- WebAPI -> Microsoft identity platform can be used to secure
- Mobile & Native APP
- Multi-factor authentication : Azure AD B2C provides additional security by enabling multi-factor authentication.
- Smart Account locks: Azure AD provides smart password locking to avoid any brute force password guessing attempt.
Integration approach:
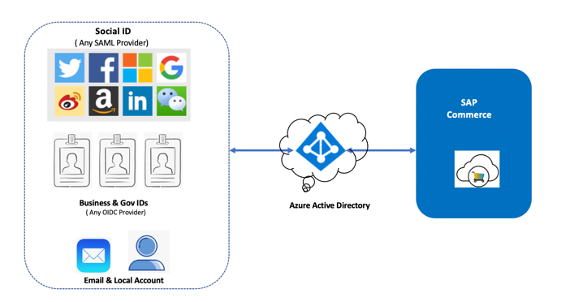
User Registration
User flows are quick , out of box configuration which which allows to enable common identity tasks like sign-up & sign-in , update profile , password reset , Azure AD support three distinct identity provision capability.
- Social identity provide like Facebook, LinkedIn, Twitter etc. Azure AD supports more than 40 identity providers.
- External identity providers: This supports protocols like OAuth 2.0 , OpenID Connect etc.
- Local accounts: Similar to conventional LDAP, It allows users to sign-up with email address /other ID and password.
Sign-In
Sign-In flow to SAP Commerce with Azure AD as Identity provider is significantly different as compared to traditional LDAP based user authentication approach. Diagram below elaborates key points of user log-in flow.

Step1: User enters commerce URL. Request hits the SAP commerce server. SAP commerce checks if user has a valid token. As user trying to log-in, system will not find token in the user’s session.
Step2: Commerce calls Azure AD sign-in user flow by passing client secret through a user’s browser.
Step3: Request is redirected to Azure AD. Azure AD checks if user has logged-in by checking Azure AD cookie. If it does not find any cookie, Azure and redirect to user log-in page hosted in Azure AD.
Step-4 : User enters ID & Password and clicks submit button.
Step-5: Azure AD authenticates user , generate a token, include claims in token or assertion. Claims are IDP attributes (e.g. email , name etc.) needs to be included by IDP as part of response. The response will include ID-Token(JWT token) for openConnect and assertion SAML authentication.At this stage Azure AD will also create a cookie to be placed in the user’s browser to enable single sign on across enterprise applications.
Step 6: Azure AD forward the request to Commerce.
Step 7: SAP commerce validates the assertion , creates a session and redirect user to the commerce landing page.
Single Sign On within Enterprise Applications
Azure AD can be leveraged as an IDP to authorize enterprise applications. As part of commerce application I had a specific need to enable single sign on between SAP commerce and other enterprise applications. Traditionally, two applications are hard-wired to enable single sign on. A cloud based IDP solution has simplified the SSO configuration between enterprise applications. Now I need not write explicit code to enable single sign-on between two applications, rather I will ask every enterprise application to authenticate and authorize users through the IDP. IDP decides if the user is authenticated and authorized to access a particular application.
In continuation to above log-in flow , Step 6 creates an Azure AD specific cookie in the user’s browser. Now if I have to enable SSO from commerce to custom application as shown below, commerce will simply send the request to custom enterprise application. At this stage enterprise application will call sign-in userflow to azure to authenticate user. However, Azure has already authenticated user during commerce log-in, Azure AD will not ask user to re-enter user ID/Password. It will redirect user landing page of the custom application.This is a seamless SSO setup which can be configured across enterprise applications without hard – wiring between source and target applications.

Key steps to integrate Azure AD with SAP Commerce and enable SSO
In this setup SAP Commerce plays roles of service provider and Microsoft Azure AD acts as a identity provider.
SAP Commerce setup needs to add extension samlsnglesignon in the commerce workspace and its entry should be made in the localextension.xml. Following are other key configuration activities
- Configure Azure AD as identity provider
- Install and configure authorization certificate and identity provider meta data
- Configure Azure AD with the service provider details .This includes including metadata.xml to AzureAD
- Enable integration of Azure AD with commerce backoffice by creating an empty extension. Azure AD employees need to be added to group SAMLSingleSignon
- Enable authorization token in SAP commerce backoffice.
Logout flow from SAP Commerce & Azure AD
Logout URL of the application needs to be explicitly registered with Azure AD during application registration.Azure AD uses this logout URL to redirect users after they are signed out. The SAP commerce platform will send a logout request message to Azure AD to indicate that session has been terminated. Azure AD sends a logout response to a logout request element.This eliminates SAP commerce session and invalidates Azure AD cookie. The user will be logged out from all active Azure AD sessions. User will be logged out from all enterprise applications s/he has logged-in through the Azure AD active directory.
Migration to Azure AD Cloud Platform
Migration to Azure AD follows commerce application development life cycle. However, there are few pre-requisites to set up Azure AD before commerce development can be started with Azure AD.
- Needs to decide Azure AD platform B2B or B2C.
- Needs to configure following building blocks of Azure AD.
- Set up tenant in Azure AD. A tenant in Azure AD represents and organization, and directory of its users.
- Set up a directory which stores user credentials and profile data.
- Setup application registration identity management. Each enterprise application should have an app registered in Azure AD along with app specific configuration.
- Define user flows and custom policies to be used in commerce application.
- Post development, one of the challenging tasks is to migrate user’s password from legacy LDAP to Azure AD. This is a bit tricky as legacy LDAP has one way encrypted password which cannot be decrypted. Microsoft provides few connectors which will be sitting on top of legacy LDAP. Whenever a user changes his/her password, the connector will sync the password to Azure AD. However, connectors has few limitations.
- Connector offered by Microsoft does not work with Azure AD B2C set-up.
- Password sync is triggered only during the password change event. It means, there is no convenient way migrate password of all users before go-live.
Other approach to migrate user’s password is a hybrid approach where a custom connector is deployed to legacy systems. Whenever a user log-in to legacy system and authenticated successfully, system checks if password has been synchronized to Azure AD. If not, system will update password to Azure. This solution needs to be implemented well ahead go-live to update password of most of the users in Azure AD.
Conclusion
With advent of cloud and many commerce applications are moving to cloud based solution, A cloud based identity and access management solution is a must to meet modern day commerce requirements.The cloud based solution is preferred way to go as it brings many innovative features, improve over all security of the platform along with inherited advantage of a cloud platform. Considering all these points , it is advisable to go with a cloud based solution to implement identity and access management.
References:
SAP Help Portal - samlsinglesignon Extension
Azure Active Directory B2C - Microsoft
- SAP Managed Tags:
- SAP Commerce,
- SAP Commerce Cloud
2 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP
1 -
API Rules
1 -
c4c
1 -
CRM
1 -
Custom Key Metrics
1 -
Customer Data
1 -
Determination
1 -
Determinations
1 -
Introduction
1 -
KYMA
1 -
Kyma Functions
1 -
open SAP
1 -
Sales and Service Cloud Version 2
1 -
Sales Cloud
1 -
Sales Cloud v2
1 -
SAP
1 -
SAP Community
1 -
SAP CPQ
1 -
SAP CRM Web UI
1 -
SAP Customer Data Cloud
1 -
SAP Customer Experience
1 -
SAP Integration Suite
1 -
SAP Sales Cloud v2
1 -
SAP Service Cloud v2
1 -
SAP Service Cloud Version 2
1 -
Service Cloud v2
1 -
Validation
1 -
Validations
1
Related Content
- When is the right time to compose? in CRM and CX Blogs by SAP
- Power of E-commerce Subscription Models in Increasing Conversions and Boosting Average Order Value in CRM and CX Blogs by SAP
- SAP Commerce Cloud Q1 ‘24 Release Highlights in CRM and CX Blogs by SAP
- SAP Customer Data Cloud Integration with Commerce Cloud and Composable Storefront in CRM and CX Blogs by SAP
- A Robust Security Package for the SAP Customer Data Cloud (CIAM) in CRM and CX Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |