
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- SAP Business Technology Platform Security | Hands-...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Product and Topic Expert
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
02-01-2021
4:03 PM
With Microsoft Azure AD as Identity Provider (IdP) and SAP BTP as Service Provider (SP)
SAP Partner Innovation Lab and SAP HANA Academy have published a series of video tutorials on the topic of SAP Business Technology Platform security. In this blog post you will find the videos embedded with references and additional information. For the related blog post, see
Questions? Please post as comment. Useful? Give us a like and share on social media. Thanks! |

As recently announced, the SAP Cloud Platform portfolio brand is no longer being used to avoid confusing with the SAP Business Technology Platform (BTP). As it will take some time before the user interfaces and documentation is updated, for the time being, we will continue to use both terms. |

Hands-On Video Tutorials
SAP ID service is the default identity provider of the SAP Business Technology Platform. However, with a few clicks we can configure the platform to use a custom identity provider to provide authentication and authorisation for our business applications hosted in the Cloud Foundry environment.
You can watch the video tutorial in a little over 10 minutes. What you learn is
- How to configure Azure AD to trust a SAP Cloud Platform subaccount as service provider
- How to configure your SAP Cloud Platform subaccount to trust Azure AD as identity provider
How to configure the mapping between the identity provider user groups and the XSUAA role collections is covered below.


Using Azure AD as Identity Provider
Tutorial Video
In the first video, we show how we can configure Azure AD as identity provider (IdP) and SAP Cloud Platform Cloud Foundry environment tenant as service provider (SP).
This requires the exchange of SAML metadata on both sides with some modifications of the user attributes.
https://youtu.be/KvAzoGHKPA0
0:00 - Introduction
0:40 - Create an enterprise application for SAP Cloud Platform in Azure AD
2:30 - Set up single sign-on with SAML
3:30 - Download SAML metadata from service provider
4:00 - Upload metadata and add sign on URL
4:30 - Configure user attributes and claims
5:45 - Download SAML metadata from identity provider
5:50 - Create new trust configuration and upload metadata
7:00 - Test single sign-on for the service provider
7:50 - Grant user access to the application (service provider)
8:45 - Showcase sample application using SAP ID services and Azure ID
9:50 - SAP BTP authorisation with roles and role collections
11:00 - Disable SAP ID service as default identity provider
Exchanging SAML Metadata
Three parameters are required. two of which are populated by uploading the SAML metadata file from the service provider, i.e. the SAP Cloud Platform subaccount.
To establish the mutual trust, download the federation metadata XML file and upload it to SAP Cloud Platform subaccount.

Updating Attributes and Claims
User attributes and claims need to be modified configuring e-mail as unique attribute and adding a group claim.

Configuring Role Collection Mappings
In previous videos of this series we covered how the design-time artifacts Scope relates to Role Template and how this maps to the platform runtime attributes Role and Role Collection, as defined in xs-security.json (or mta.yaml).
SAP Business Application Studio | Design-time Configuration

Azure AD | Groups
To illustrate this concept, we have created two groups. For clarity, we used the same name for the group but this can be any name you want as the mapping is made using the group object ID.

SAP Cloud Platform | Role Collection Mappings
Using the Security > Trust Configuration menu of the SAP Cloud Platform cockpit, selecting the custom identity provider we created, Azure AD, provides access to a menu to create role collection mappings.
- Role Collection: select the role collection from the list (as defined in xs-security.json)
- Attribute: as configured in Azure AD "Groups"
- Value: corresponding object ID of the group created for the service provider (enterprise application)
Create Role Collection Mapping

List Role Collection Mappings for the custom identity provider
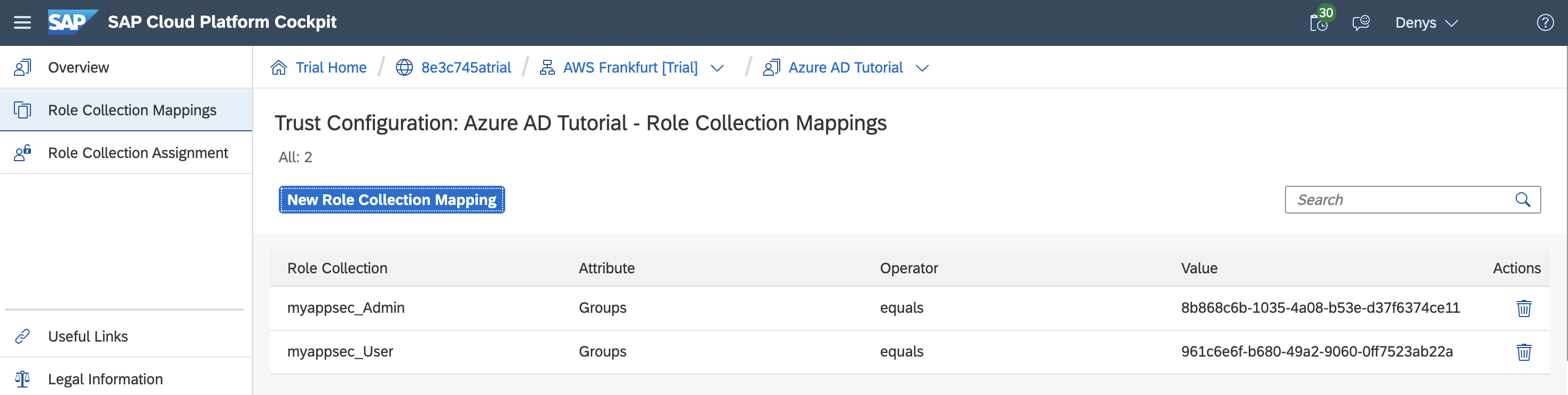
Security > Role Collections shows the user group mapping.

Details = True
When two or more identity providers are available for user logon, a default selection screen is displayed with the default identity provider SAP ID service (sap.default) with the custom identity provider(s) with the link text as defined when the trust was created.
The URL of the page is
<subaccount>.authentication.<region>.hana.ondemand.com/login
Appending config?action=who&details=true to the URL returns information about about the SAML context, including the object ID for the SAML groups.
https://8e3c745atrial.authentication.eu10.hana.ondemand.com/config?action=who&details=true

Additional References
SAP HANA Academy YouTube Playlist and Code Repository
To bookmark the playlist on YouTube, go to
For the code snippets, see
Documentation
The steps are documented in generic terms (any SAML Identity Provider) in the documentation for the SAP Cloud Platform.
- Security Administration: Managing Authentication and Authorization
- Establish Trust and Federation with UAA Using Any SAML Identity Provider
- Federation Attribute Settings of Any Identity Provider
The configuration guide from the Microsoft Documentation provides some information but not all as it covers the Neo environment and not Cloud Foundry.
Blogs
For an earlier blog post on the topic, see

Share and Connect
Questions? Please post as comment.
Useful? Give us a like and share on social media.
Thanks!
If you would like to receive updates, connect with me on
- LinkedIn > linkedin.com/in/dvankempen
- Twitter > @dvankempen
For the author page of SAP PRESS, visit
Over the years, for the SAP HANA Academy, SAP’s Partner Innovation Lab, and à titre personnel, I have written a little over 300 posts here for the SAP Community. Some articles only reached a few readers. Others attracted quite a few more. For your reading pleasure and convenience, here is a curated list of posts which somehow managed to pass the 10k-view mile stone and, as sign of current interest, still tickle the counters each month. |

- SAP Managed Tags:
- Security,
- SAP Business Technology Platform
Labels:
2 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
92 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
66 -
Expert
1 -
Expert Insights
177 -
Expert Insights
293 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
341 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
419 -
Workload Fluctuations
1
Related Content
- LLM, RAG and Cloud Foundry: No space left on device in Technology Q&A
- Consuming SAP with SAP Build Apps - Mobile Apps for iOS and Android in Technology Blogs by SAP
- Onboarding Users in SAP Quality Issue Resolution in Technology Blogs by SAP
- What’s new in Mobile development kit client 24.4 in Technology Blogs by SAP
- IoT - Ultimate Data Cyber Security - with Enterprise Blockchain and SAP BTP 🚀 in Technology Blogs by Members
Top kudoed authors
| User | Count |
|---|---|
| 35 | |
| 25 | |
| 14 | |
| 13 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 5 |