
- SAP Community
- Products and Technology
- Financial Management
- Financial Management Blogs by SAP
- GRC Tuesdays: Digital Trust, The New Consumer Curr...
Financial Management Blogs by SAP
Get financial management insights from blog posts by SAP experts. Find and share tips on how to increase efficiency, reduce risk, and optimize working capital.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Product and Topic Expert
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
11-17-2020
6:07 AM
In these GRC Tuesdays blog, I often discuss the regulator’s expectations and how companies can roll-out compliance programs to address associated requirements.
Today, I’d like to take a different view: one from the consumer who will be making the purchasing decision. In all business models: B2B, B2C, C2C, etc. there is a “consumer”. It can be an individual or a group of people but ultimately, it will be a consumer’s – and human – decision to select or not your products or services.
Now, if you really need convincing that data – including the one of this “consumer”, is a really thought after asset, just have a look at the World's Biggest Data Breaches & Hacks graphical representation:
I believe there are 2 ways to look at it:
I would personally be in favour of option 2 and, according to an Australian Community Attitudes to Privacy Survey released by the Office of the Australian Information Commissioner in September 2020, I don’t seem to be the only one: 70% of respondents see the protection of personal information as an important issue and a major concern in their life.
And this then ties directly back to economics and the purchasing decision when 84% consider the privacy of their information to be extremely or very important when choosing a digital service - including 54% who say it is extremely important. Clearly, this becomes a key selection criteria from consumers.
As a matter of fact, it becomes the #1 reason when choosing which app or program to download:
Now, let’s see what behaviours respondents are most likely to consider to be a misuse with that regards:
So, going back to my original point: the way an organization manages data privacy will be an important decision factor for the “consumer” and previous misuses will significantly impact a consumer’s choice.
As a matter of fact, in its Top 10 Technology Trends for 2019, Gartner stated that “Companies that misuse personal data will lose the trust of their customers. Trustworthiness is a key factor in driving revenue and profitability… By 2020, we expect that companies that are digitally trustworthy will generate 20% more online profit than those that aren’t.”
Data is more valuable than oil even if there’s no stock exchange for this jewel. The sheer number of breaches illustrated in the graphic above clearly asserts this assumption. And failure to protect it will surely impact the organization. In addition to potential non-compliance fines, digital trust – defined by PwC as “the level of confidence in people, processes, and technology to build a secure digital world”, will be broken and reputation will therefore be damaged. Since it is a decision factor as we established just earlier, it also means that the company’s revenue will de facto be impacted as well.
Creating and safeguarding digital trust means that the company's stakeholders are confident in how it governs the use, monetization, and sharing of data – and that it does so without compromising on security, management, or compliance. As a result, they are more likely to continue coming back to the company and even refer it and its products or services to their peers.
Unfortunately, safeguarding the assets that are at the centre of the digital trust is no small task. Why is it so complicated might you ask? That’s a good question!
Let’s start with the fact that 91% of enterprise-wide digital transformation include security and/or privacy personnel as stakeholders… but only 53% include proactive management of cyber and privacy risks by design in the project plan and budget “fully from the start”. Already, that’s not a great starting point.
Progressing to the “attack surface”, there are many areas that are exposed to security risks such as:
* Applications: especially the ones that are mission critical for business operations. Compromised applications from breaches and attacks represent significant disruption and cost. A breached ERP system negates prior auditing and control assertions and typically must be retested and validated;
* Data: since companies are collecting and storing incredible amounts of data including personally identifiable data and intellectual property. This data is key for needed insights and strategies but must be safeguarded;
* People: an often forgotten aspect, the human element poses a significant security risk. Yet, it can also be an effective line of defense. A well-informed human firewall with greater awareness can help confront threats.
Finally, the “adversaries” themselves have evolved radically. Whereas previously script kiddies with a desire to show that they could defeat security of a major organization was one of the key threats, we are now seeing much more organized, funded and driven attacks with monetary or political objectives.
Reduced preparedness, increased attack surface and professionalization of the adversaries creates the perfect storm.
If there was a silver bullet – a single tool for instance, to answer this complex requirement, it would be the Grail. Unfortunately, unless you unplug all your systems and only trade in person and in physical money, there’s no silver bullet and the way you manage cybersecurity and data protection will really depend on your landscape and what other processes are already in place and can be leveraged.
At SAP, we have opted for a modular approach where customers can select the right tools that they need to achieve their objectives.
These modules are organized around 5 pillars:
* Application Security: one of the most critical pieces of the puzzle since it helps secure the core applications that run your business;
* Identity and Access Management: to optimize digital identities across the enterprise by providing the key capabilities to manage system accounts and ensure the correct authorization assignments;
* Data Protection and Privacy: that addresses more particularly the data protection and privacy concerns and regulations;
* Cloud Transparency and Control: to enforce public cloud data access, location, movement,
and processing policies but also monitor and report on this data access, storage, movement, processing, and location in the cloud;
* Cybersecurity Risk and Governance: focuses on the identification and management of risks, regulations and polices to minimize potential business impact.
Together, we believe that they provide the most adequate response to this topic. And, since a picture is worth 1,000 words, and that we are already at this point in this blog, I have added below a representation of the relevant modules for each pillar:
Should you be interested in reading more about it, I would suggest the following links:
* Cybersecurity, Data Protection, and Privacy on SAP.com/GRC portal
* Discover SAP offerings for GRC, cybersecurity, and privacy that consists in a series of on-demand webinars covering this topic in more detail.
What about you, how does your organization protect digital trust? I look forward to reading your thoughts and comments either on this blog or on Twitter @TFrenehard
Today, I’d like to take a different view: one from the consumer who will be making the purchasing decision. In all business models: B2B, B2C, C2C, etc. there is a “consumer”. It can be an individual or a group of people but ultimately, it will be a consumer’s – and human – decision to select or not your products or services.
Now, if you really need convincing that data – including the one of this “consumer”, is a really thought after asset, just have a look at the World's Biggest Data Breaches & Hacks graphical representation:

Note: World's Biggest Data Breaches and Hacks by David McCandless,Tom Evans, Paul Barton, Dr Stephanie Starling & Duncan Geere, May 2020
I believe there are 2 ways to look at it:
- Option 1: This is the new normal and there’s nothing we can do about it;
- Option 2: This is not the way it should be and the company that holds my data needs to protect it.
I would personally be in favour of option 2 and, according to an Australian Community Attitudes to Privacy Survey released by the Office of the Australian Information Commissioner in September 2020, I don’t seem to be the only one: 70% of respondents see the protection of personal information as an important issue and a major concern in their life.
And this then ties directly back to economics and the purchasing decision when 84% consider the privacy of their information to be extremely or very important when choosing a digital service - including 54% who say it is extremely important. Clearly, this becomes a key selection criteria from consumers.
As a matter of fact, it becomes the #1 reason when choosing which app or program to download:
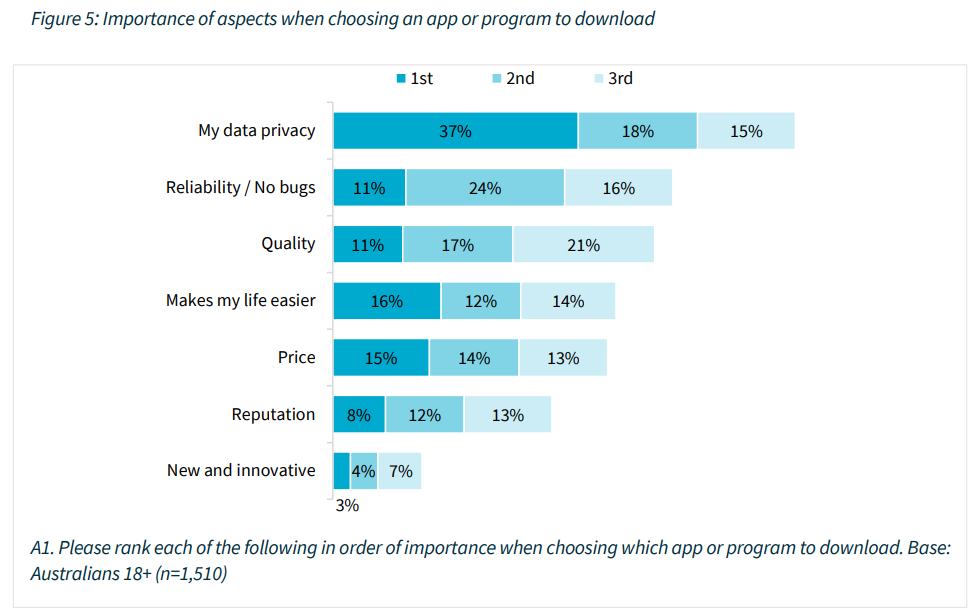
Note: Figure 5: Importance of aspects when choosing an app or program to download
Now, let’s see what behaviours respondents are most likely to consider to be a misuse with that regards:
- an organisation uses their personal information in ways that cause harm, loss or distress (84%)
- information supplied to an organisation for a specific purpose is used for another purpose (84%)
So, going back to my original point: the way an organization manages data privacy will be an important decision factor for the “consumer” and previous misuses will significantly impact a consumer’s choice.
As a matter of fact, in its Top 10 Technology Trends for 2019, Gartner stated that “Companies that misuse personal data will lose the trust of their customers. Trustworthiness is a key factor in driving revenue and profitability… By 2020, we expect that companies that are digitally trustworthy will generate 20% more online profit than those that aren’t.”
Digital Trust as the New Currency
Data is more valuable than oil even if there’s no stock exchange for this jewel. The sheer number of breaches illustrated in the graphic above clearly asserts this assumption. And failure to protect it will surely impact the organization. In addition to potential non-compliance fines, digital trust – defined by PwC as “the level of confidence in people, processes, and technology to build a secure digital world”, will be broken and reputation will therefore be damaged. Since it is a decision factor as we established just earlier, it also means that the company’s revenue will de facto be impacted as well.
Creating and safeguarding digital trust means that the company's stakeholders are confident in how it governs the use, monetization, and sharing of data – and that it does so without compromising on security, management, or compliance. As a result, they are more likely to continue coming back to the company and even refer it and its products or services to their peers.
What Makes Cybersecurity and Data Protection so Challenging?
Unfortunately, safeguarding the assets that are at the centre of the digital trust is no small task. Why is it so complicated might you ask? That’s a good question!
Let’s start with the fact that 91% of enterprise-wide digital transformation include security and/or privacy personnel as stakeholders… but only 53% include proactive management of cyber and privacy risks by design in the project plan and budget “fully from the start”. Already, that’s not a great starting point.
Progressing to the “attack surface”, there are many areas that are exposed to security risks such as:
* Applications: especially the ones that are mission critical for business operations. Compromised applications from breaches and attacks represent significant disruption and cost. A breached ERP system negates prior auditing and control assertions and typically must be retested and validated;
* Data: since companies are collecting and storing incredible amounts of data including personally identifiable data and intellectual property. This data is key for needed insights and strategies but must be safeguarded;
* People: an often forgotten aspect, the human element poses a significant security risk. Yet, it can also be an effective line of defense. A well-informed human firewall with greater awareness can help confront threats.
Finally, the “adversaries” themselves have evolved radically. Whereas previously script kiddies with a desire to show that they could defeat security of a major organization was one of the key threats, we are now seeing much more organized, funded and driven attacks with monetary or political objectives.
Reduced preparedness, increased attack surface and professionalization of the adversaries creates the perfect storm.
Managing Cybersecurity and Data Protection
If there was a silver bullet – a single tool for instance, to answer this complex requirement, it would be the Grail. Unfortunately, unless you unplug all your systems and only trade in person and in physical money, there’s no silver bullet and the way you manage cybersecurity and data protection will really depend on your landscape and what other processes are already in place and can be leveraged.
At SAP, we have opted for a modular approach where customers can select the right tools that they need to achieve their objectives.
These modules are organized around 5 pillars:
* Application Security: one of the most critical pieces of the puzzle since it helps secure the core applications that run your business;
* Identity and Access Management: to optimize digital identities across the enterprise by providing the key capabilities to manage system accounts and ensure the correct authorization assignments;
* Data Protection and Privacy: that addresses more particularly the data protection and privacy concerns and regulations;
* Cloud Transparency and Control: to enforce public cloud data access, location, movement,
and processing policies but also monitor and report on this data access, storage, movement, processing, and location in the cloud;
* Cybersecurity Risk and Governance: focuses on the identification and management of risks, regulations and polices to minimize potential business impact.
Together, we believe that they provide the most adequate response to this topic. And, since a picture is worth 1,000 words, and that we are already at this point in this blog, I have added below a representation of the relevant modules for each pillar:

Should you be interested in reading more about it, I would suggest the following links:
* Cybersecurity, Data Protection, and Privacy on SAP.com/GRC portal
* Discover SAP offerings for GRC, cybersecurity, and privacy that consists in a series of on-demand webinars covering this topic in more detail.
What about you, how does your organization protect digital trust? I look forward to reading your thoughts and comments either on this blog or on Twitter @TFrenehard
- SAP Managed Tags:
- Governance, Risk, Compliance (GRC), and Cybersecurity
Labels:
1 Comment
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
Business Trends
145 -
Business Trends
15 -
Event Information
35 -
Event Information
9 -
Expert Insights
8 -
Expert Insights
29 -
Life at SAP
48 -
Product Updates
521 -
Product Updates
63 -
Technology Updates
196 -
Technology Updates
10
Related Content
- SAP S/4HANA Cloud for group reporting - Release 2402 is generally available in Financial Management Blogs by SAP
- GRC Tuesdays: Announcing SAP’s plans for a next generation Governance, Risk, and Compliance Platform: SAP GRC edition for SAP HANA in Financial Management Blogs by SAP
- GRC Tuesdays: How To Calculate the ROI of an Integrated Risk and Control Platform to Justify Investment in Financial Management Blogs by SAP
- GRC Tuesdays: Governance, Risk and Compliance securing the Lead-to-Cash process in Financial Management Blogs by SAP
- GRC Tuesdays: What is Sensitive Information? in Financial Management Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |