
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Customer Controlled Key Management Services with S...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Advisor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
10-19-2020
5:00 AM
As a part of securing enterprise sensitive data, be it on-premise or cloud, data encryptions at rest and in transit has become mandatory requirement to meet security & regulatory compliance. In simple terms, encryption is a process of scrambling plaintext data using an algorithm and an encryption key to produce ciphertext. In this blog, we look at some of the key best practice principles of key management and understand how SAP supports encryption with customer controlled key management systems with SAP Data Custodian.
Introduction
Encryption can be applied at different layers in stack such as application layer, database layer, file system, storage layer. For example, encryption at the storage layer such as self-encrypting devices provides protection against theft of hard drive. However, to meet regulatory and other compliance such as GDPR, PCI-DSS, encryption at the higher layers of the stack such as database and application layer is necessary.
In the past, it was a common approach to define encryption key in the applications code or create encryption key in a database file. Using encryption key on the same server as the data brings greater risk of compromise of the sensitive data. Therefore, many organizations are looking for robust industry standard FIPS 140-2 compliant independent key management systems that store encryption keys on a separate server either via separate hardware or virtual server where customers have access to master keys that are stored and managed securely. Just as you would protect your bank locker key safely, there are some best practice approach that must be followed while rotating your encryption master keys:
Before we go into the details of customer controlled KMS in SAP Data Custodian, let us review some of the basic principles of symmetric, asymmetric and hybrid approaches to keys.
Symmetric Key:
In this approach, sender and receiver use the same key. This approach is used mainly for data at rest encryption such as encryption of data at HANA DB layer or storage layer. Typically, one can encrypt sensitive data into ciphertext while it is stored in a database and decrypt it to plaintext when it is accessed by an authorized application and user. This is depicted in a simple diagram:
Asymmetric Encryption
In Asymmetric encryption, a pair of keys (public and private keys) are used which are mathematically related to each other.
Public Key: This can be freely distributed and will be used to encrypt the data.
Private Key: This is kept secure and confidential. This will be used to decrypt the data that was previously encrypted with corresponding public key.
Hybrid Approach to Encryption:
Given that asymmetric methods are computationally intensive and not suitable for large data set, a hybrid approach is devised. As an initial step, public key is exchanged between communication entities:
Now we look at the definition of key elements, we will discuss on customer controlled KMS using SAP Data Custodian.
Customer Controlled KMS in S/4HANA with SAP Data Custodian
As SAP hosts S/4HANA applications in public cloud such as AWS, Azure and GCP as an option, our customers require an independent key management system to manage master keys and other components as a part of their compliance requirement. Having an independent FIPS140-2 Level 3 compliant hardware security module meets highest stringent security as the system provides tamper proof capability.
SAP Data Custodian delivers an independent KMS offered through Software as a Service model. SAP Data custodian also provides cloud data insight and protection, data governance, compliance and audit reporting, offers rapid identification and notification of data protection. SAP Data Custodian KMS can work with S/4HANA single tenanted deployments such as BYOL, HEC, S/4HANA hosted in public cloud.
Customer can create a cryptographic key “Master Key or Key Encryption Key (KEK)” with SAP Data Custodian Key Management Service. Customers manages life cycle management of cryptographic keys – creation, activation, backup, rotation, archival, deletion and other crypto operations. Customer gets clear segregation of keys per application and segregation of duties at the software and database levels and SAP does not have access to customer keys. Access to these can be provided strictly based on segregation of duties and key administrators can only manage the keys but do not have access to the encrypted data.
In a typical deployment, customer create data encryption keys (DEK) outside of the KMS. This key is used to encrypt and decrypt the actual payload data. The data encryption key (DEK) itself is encrypted with Key Encryption Key (KEK) which is managed by customer in KMS.
In the following section, we briefly look at enhancement in HANA2.0 SP 05 and native integration capability with SAP Data Custodian KMS. Part of the requirement is that Customer needs to subscribe to SAP Data Custodian KMS directly and customer have migrated to HANA 2.0 SP5 and HANA LSS. With HANA2.0 SP 05, SAP supports Local Secure Store.
Local Secure Store:
The local secure store (LSS) is a separate, lightweight utility for storing and securely managing encryption keys, encryption root keys, and other similarly sensitive data, such as security-relevant configuration settings. It helps protect sensitive server-side data from illegitimate or fraudulent usage. For a Single Tenanted SAP HANA system, we can install LSS.
The details on local secure store is in the link as follows:
https://help.sap.com/viewer/b3ee5778bc2e4a089d3299b82ec762a7/2.0.05/en-US/5a43dc48190f4543b0d840952d...
Segregation of Duties:
The advantage of LSS is a segregation of duties principle that can be applied. This security principle divides critical functions among different security personnel to ensure that no one individual has enough information or access privilege to perpetrate damaging fraud. Based on the above, two roles have been defined: <sid>crypt and <sid> adm
SAP Key Chain Hierarchy
The following key chain hierachy is used at the S/4HANA runtime:
When SAP Data Custodian KMS is used with the local secure store (LSS), the LSS payload database as well as the LSS backup of the payload database are encrypted with the public key of an asymmetric key pair whose private key is stored in the SAP Data Custodian KMS. Consequently, to read and decrypt the payload database, access to the private key of the key pair is required.
The LSS payload database contains the SAP HANA root keys used for encrypting the SAP HANA data volume, redo logs, and data and log backups. Therefore, if the private key is lost, damaged, or becomes unusable for some reason, the database data, logs, and backups can no longer be used.
More details on the SAP Data Custodian KMS with LSS can be found in this link:
https://help.sap.com/viewer/b3ee5778bc2e4a089d3299b82ec762a7/2.0.05/en-US/cf998f5a07af4c58bbb270659d...
Conclusion:
SAP Data Custodian KMS fulfils the compliance requirement of customer controlled key management services which are FIPS 140-2 Level 3 certified and provides assurance on data protection, privacy and that cloud service providers do not have a access visibility to customer data. Segregation of Duties, Master Key Managed outside of HANA environment, multiple hierarchy of key chain, role based access, authentication and authorization, configuration of masking through SAP Data Custodian with UI Masking S/4HANA add-on, audit logs of KMS access, provide transparency, stringent controls and protect critical data in HANA.
Introduction
Encryption can be applied at different layers in stack such as application layer, database layer, file system, storage layer. For example, encryption at the storage layer such as self-encrypting devices provides protection against theft of hard drive. However, to meet regulatory and other compliance such as GDPR, PCI-DSS, encryption at the higher layers of the stack such as database and application layer is necessary.
In the past, it was a common approach to define encryption key in the applications code or create encryption key in a database file. Using encryption key on the same server as the data brings greater risk of compromise of the sensitive data. Therefore, many organizations are looking for robust industry standard FIPS 140-2 compliant independent key management systems that store encryption keys on a separate server either via separate hardware or virtual server where customers have access to master keys that are stored and managed securely. Just as you would protect your bank locker key safely, there are some best practice approach that must be followed while rotating your encryption master keys:
- Customer should be able to manage key lifecycle such as key generation, pre-activation, expiration, post activation, archival and destruction.
- Control physical and logical access to key servers
- User/Role Access to encryption keys.
- Symmetric keys are to be securely transmitted through a tunnel established through secure TLS negotiation and mutual authentication.
Before we go into the details of customer controlled KMS in SAP Data Custodian, let us review some of the basic principles of symmetric, asymmetric and hybrid approaches to keys.
Symmetric Key:
In this approach, sender and receiver use the same key. This approach is used mainly for data at rest encryption such as encryption of data at HANA DB layer or storage layer. Typically, one can encrypt sensitive data into ciphertext while it is stored in a database and decrypt it to plaintext when it is accessed by an authorized application and user. This is depicted in a simple diagram:
 Symmetric Key
Symmetric Key
Asymmetric Encryption
In Asymmetric encryption, a pair of keys (public and private keys) are used which are mathematically related to each other.
Public Key: This can be freely distributed and will be used to encrypt the data.
Private Key: This is kept secure and confidential. This will be used to decrypt the data that was previously encrypted with corresponding public key.

Asymmetric Key
Hybrid Approach to Encryption:
Given that asymmetric methods are computationally intensive and not suitable for large data set, a hybrid approach is devised. As an initial step, public key is exchanged between communication entities:
- The sender encrypts the large volume of data using a generated ephemeral symmetric encryption key.
- Sender encrypts the symmetric encryption key with a public key of the receiver and sends the encrypted symmetric key, along with encrypted data to the receiver.
- Receiver decrypts symmetric key using receiver private key and obtains symmetric key.
- Using Symmetric key, receiver decrypts the data.

Hybrid Approach to Encryption
Now we look at the definition of key elements, we will discuss on customer controlled KMS using SAP Data Custodian.

Customer Controlled KMS in S/4HANA with SAP Data Custodian
As SAP hosts S/4HANA applications in public cloud such as AWS, Azure and GCP as an option, our customers require an independent key management system to manage master keys and other components as a part of their compliance requirement. Having an independent FIPS140-2 Level 3 compliant hardware security module meets highest stringent security as the system provides tamper proof capability.
SAP Data Custodian delivers an independent KMS offered through Software as a Service model. SAP Data custodian also provides cloud data insight and protection, data governance, compliance and audit reporting, offers rapid identification and notification of data protection. SAP Data Custodian KMS can work with S/4HANA single tenanted deployments such as BYOL, HEC, S/4HANA hosted in public cloud.
Customer can create a cryptographic key “Master Key or Key Encryption Key (KEK)” with SAP Data Custodian Key Management Service. Customers manages life cycle management of cryptographic keys – creation, activation, backup, rotation, archival, deletion and other crypto operations. Customer gets clear segregation of keys per application and segregation of duties at the software and database levels and SAP does not have access to customer keys. Access to these can be provided strictly based on segregation of duties and key administrators can only manage the keys but do not have access to the encrypted data.
In a typical deployment, customer create data encryption keys (DEK) outside of the KMS. This key is used to encrypt and decrypt the actual payload data. The data encryption key (DEK) itself is encrypted with Key Encryption Key (KEK) which is managed by customer in KMS.
In the following section, we briefly look at enhancement in HANA2.0 SP 05 and native integration capability with SAP Data Custodian KMS. Part of the requirement is that Customer needs to subscribe to SAP Data Custodian KMS directly and customer have migrated to HANA 2.0 SP5 and HANA LSS. With HANA2.0 SP 05, SAP supports Local Secure Store.
Local Secure Store:
The local secure store (LSS) is a separate, lightweight utility for storing and securely managing encryption keys, encryption root keys, and other similarly sensitive data, such as security-relevant configuration settings. It helps protect sensitive server-side data from illegitimate or fraudulent usage. For a Single Tenanted SAP HANA system, we can install LSS.
The details on local secure store is in the link as follows:
https://help.sap.com/viewer/b3ee5778bc2e4a089d3299b82ec762a7/2.0.05/en-US/5a43dc48190f4543b0d840952d...
Segregation of Duties:
The advantage of LSS is a segregation of duties principle that can be applied. This security principle divides critical functions among different security personnel to ensure that no one individual has enough information or access privilege to perpetrate damaging fraud. Based on the above, two roles have been defined: <sid>crypt and <sid> adm


Segregation of Duties
SAP Key Chain Hierarchy
The following key chain hierachy is used at the S/4HANA runtime:
When SAP Data Custodian KMS is used with the local secure store (LSS), the LSS payload database as well as the LSS backup of the payload database are encrypted with the public key of an asymmetric key pair whose private key is stored in the SAP Data Custodian KMS. Consequently, to read and decrypt the payload database, access to the private key of the key pair is required.

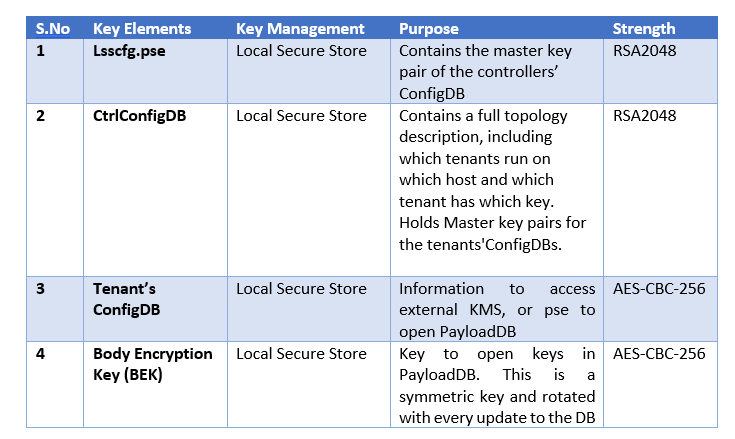
SAP Key Chain in HANA and LSS with External KMS

Key Chain
The LSS payload database contains the SAP HANA root keys used for encrypting the SAP HANA data volume, redo logs, and data and log backups. Therefore, if the private key is lost, damaged, or becomes unusable for some reason, the database data, logs, and backups can no longer be used.
More details on the SAP Data Custodian KMS with LSS can be found in this link:
https://help.sap.com/viewer/b3ee5778bc2e4a089d3299b82ec762a7/2.0.05/en-US/cf998f5a07af4c58bbb270659d...
Conclusion:
SAP Data Custodian KMS fulfils the compliance requirement of customer controlled key management services which are FIPS 140-2 Level 3 certified and provides assurance on data protection, privacy and that cloud service providers do not have a access visibility to customer data. Segregation of Duties, Master Key Managed outside of HANA environment, multiple hierarchy of key chain, role based access, authentication and authorization, configuration of masking through SAP Data Custodian with UI Masking S/4HANA add-on, audit logs of KMS access, provide transparency, stringent controls and protect critical data in HANA.
- SAP Managed Tags:
- SAP HANA Enterprise Cloud,
- SAP S/4HANA Public Cloud
Labels:
2 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
87 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
64 -
Expert
1 -
Expert Insights
178 -
Expert Insights
273 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
11 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
324 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
402 -
Workload Fluctuations
1
Related Content
- 10+ ways to reshape your SAP landscape with SAP Business Technology Platform – Blog 4 in Technology Blogs by SAP
- Consuming SAP with SAP Build Apps - Connectivity options for low-code development - part 2 in Technology Blogs by SAP
- New webcast series on “SAP BTP DevOps and Observability in Action” in Technology Blogs by SAP
- New features for Documents in SAP Cloud ALM in Technology Blogs by SAP
- What you need to know about Finance in SAP S/4HANA Cloud, Public Edition in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 12 | |
| 9 | |
| 7 | |
| 7 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 6 | |
| 4 |