
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Federated SAML SSO with Azure AD and SAP HANA [doc...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Product and Topic Expert
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
07-12-2020
8:32 PM
Abstract.
| Azure AD (Active Directory) has become an increasingly popular choice as a SAML SSO identity provider with SAP applications. Azure AD makes it a relatively simple task to set up SAML SSO with the likes of [SAP HANA], [SAP Analytics Cloud] etc. by providing easy to follow step by step guides. Good to know:Azure AD is offered either as a free trial or may be available as part of your other MSFT products/service subscription(s). SAP HANA, express edition [database and application services] is available as a ready-to-deploy docker image under the SAP free plan license terms. Please note a [docker hub account] may be required to get access to the image. |
First things first.
Prepare the SAP HANA database.
If you opted for the SAP HANA express docker image please follow the deployment [instructions].
Then, you may eventually run the image with the following docker run command:
docker run -d --restart=always -p 8090:8090 -p 4390:4390 -p 39013:39013 -p 39015:39015 -p 39041-39045:39041-39045 -p 1128-1129:1128-1129 -p 59013-59014:59013-59014 -p 39030-39033:39030-39033 -p 51000-51100:51000-51100 -p 53075:53075 -h hxehost -v /home/<linux user>/data:/hana/mounts --ulimit nofile=1048576:1048576 --sysctl kernel.shmmax=1073741824 --sysctl net.ipv4.ip_local_port_range='60000 65535' --sysctl kernel.shmmni=524288 --sysctl kernel.shmall=8388608 --name myhanaxsa store/saplabs/hanaexpressxsa:2.00.045.00.20200121.1 --agree-to-sap-license --passwords-url https://raw.githubusercontent.com/<githubRepo>/myjson/master/db.jsondocker exec -it myhanaxsa bash
hxeadm@hxehost:/usr/sap/HXE/HDB90>
hxeadm@hxehost:/usr/sap/HXE/HDB90> HDB version
HDB version info:
version: 2.00.045.00.1575639312
branch: fa/hana2sp04
machine config: linuxx86_64
git hash: af3aabc5a5cdb94ecbc7c07d0997d0bd4ae0046b
git merge time: 2019-12-06 14:35:12
weekstone: 0000.00.0
cloud edition: 0000.00.00
compile date: 2019-12-06 15:29:38
compile host: ld5144
compile type: relQuo vadis?
When configuring the SAML SSO it is important to bear in my mind SAP HANA is the application or service provider (SP) and Azure AD is the Identity Provider (IdP).
In order to set up the trust between the SP and the IDP we need to exchange their respective metadata descriptors.
In a nutshell, the SAP HANA service provider metadata will be used to create an application within the IDP, and vice versa the Azure AD IDP's metadata will be uploaded into SAP HANA.
XSC Admin Tool
For the sake of simplicity I shall demonstrate the SAML SSO setup using the SAP HANA XS classic administration GUI:
https://<FQDN>:43xx/sap/hana/xs/admin/index.html#/samlSPwhere `FQDN` stands for a fully qualified domain name of your SAP HANA database host and `xx` is the SAP HANA host instance number.
samlSP
1. You may want to edit or change the service provider name and organisation attributes.
This is what I chose to do. Or you can go head with the default settings.
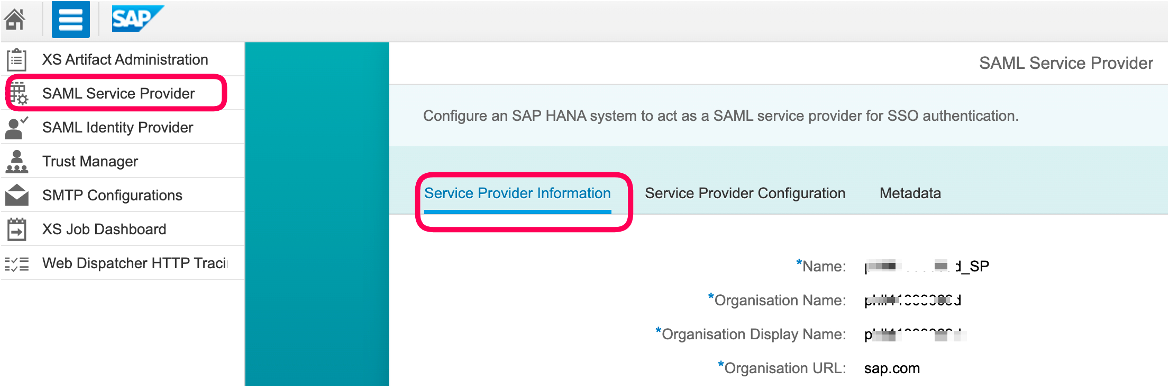
2. Copy and save the service provider metadata into a file with the .xml extension, for instance samlSP.xml.
You will need to upload this file when configuring the SAP HANA Azure AD enterprise application.

3. Now it is time to configure the Azure AD SAP HANA Application.
Azure portal access
You may have several Azure accounts. Pick the account that gives you access to Azure AD.
From the [main portal] menu select Azure Active Directory resource.

Azure AD landing page should open.
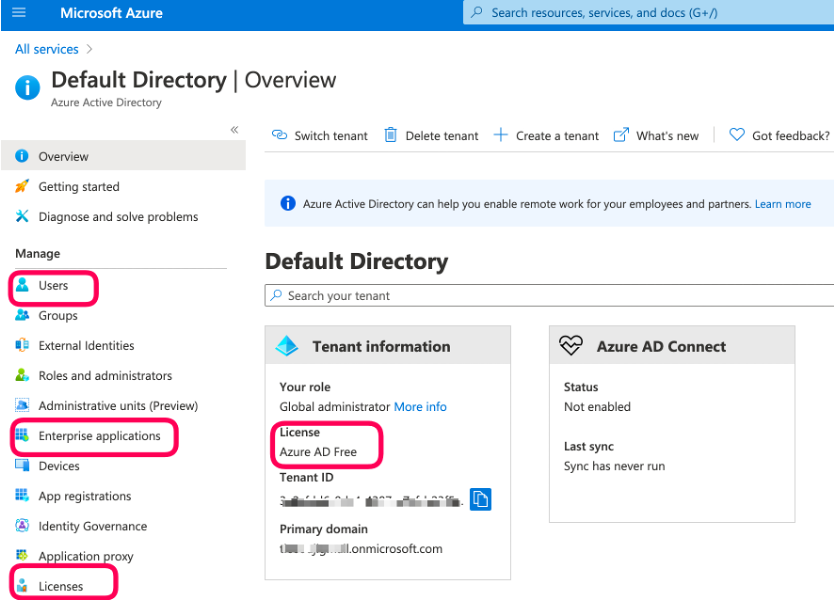
Choose to create an Enterprise application to establish trust between Azure AD and SAP HANA.

Azure AD makes is really simple with its *enterprise application gallery* as depicted below:

select the SAP applications gallery and make your application integration choice:

a. Create your SAP HANA application.
Please give it a distinguished name so you can easily refer to it afterwards. You may notice that the Create button is somehow at the very bottom of the page and may be initially difficult to spot.

b. Configure (steps 1-4 from the below screenshot) the SAP HANA application you have just created:
* Please follow the configuration [guide].
* Most likely you will be uploading the SAP HANA service provider metadata. However, you may also choose to configure all the values from (step 1) manually.

c. The most tricky part in the entire process is the claim management (step 2).
Indeed, Azure AD offers a variety of ways of mapping an external user into an identity claim.
For the sake of clarity, I have rather chosen to use the same claim management option as described in the [SAP HANA integration tutorial]
Please have a good understanding of the claim management options you may choose. Otherwise you may spend lots of time trying to troubleshoot not-so-obvious errors.

d. Download the Federated AzureAD SAML IDP metadata (step 3) and add the new SAML IDP metadata into SAP HANA

it is important to verify the SAML IDP certificate has been added to the SAML trust store

e. Configure a database user mapping (step 4)
I mapped an existing SAP HANA tenant database user to the Azure AD external identity (using SAP HANA Studio)
You may notice I used the SAP HANA SYSTEM user to perform this activity [on HXE - the tenant db].

Testing SAML SSO
In order to test whether the SAML SSO is working one would typically configure the SAP HANA HTTPS InA service
https://<FQDN>:43xx/sap/hana/xs/admin/index.html#/package/sap.bc.ina.service.v2
and would call the GetServerInfo verb:
https://<FQDN>43xx/sap/bc/ina/service/v2/GetServerInfoas to retrieve the SAP HANA EPM-MDS server side configuration...
{"ServerInfo":{"BuildTime":"2019-12-06 15:29:38","Client":"000000000000000000","ServerType":"SAP HANA","SystemId":"HXE","UserLanguageCode":"EN","Version":"2.00.045.00.1575639312"},"Services":[{"Capabilities":[{"Capability":"ResultSetState","MaxVersion":104,"MinVersion":100},{"Capability":"DynamicResultsetFacets","MaxVersion":104,"MinVersion":100},{"Capability":"InaSearchModel","MaxVersion":104,"MinVersion":100}],"CapabilitiesDev":[],"Service":"Search"},{"Capabilities":[],"CapabilitiesDev":[],"Service":"Suggestions"},{"Capabilities":[{"Capability":"CellsValueFormated","MaxVersion":104,"MinVersion":100},On a side note: if the SAML token is no longer valid and has to be renewed you would be prompted with the IDP login screen first

That's all folks:)
best wishes
Piotr Tesny
- SAP Managed Tags:
- SAP Cloud Identity Services,
- SAP HANA,
- SAP HANA Info Access,
- SAP HANA studio,
- SAP Single Sign-On
Labels:
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
93 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
66 -
Expert
1 -
Expert Insights
177 -
Expert Insights
299 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
344 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
422 -
Workload Fluctuations
1
Related Content
- ABAP Cloud Developer Trial 2022 Available Now in Technology Blogs by SAP
- Kyma Integration with SAP Cloud Logging. Part 2: Let's ship some traces in Technology Blogs by SAP
- ABAP Platform Trial 1909 ( error in license check) in Technology Q&A
- SAP Datasphere - Space, Data Integration, and Data Modeling Best Practices in Technology Blogs by SAP
- Develop CAP Project with Lazyvim in Docker in Technology Blogs by Members
Top kudoed authors
| User | Count |
|---|---|
| 40 | |
| 25 | |
| 17 | |
| 13 | |
| 7 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 6 |