
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by Members
- Terminal Access to CPI Runtime: Execution of Shell...
Technology Blogs by Members
Explore a vibrant mix of technical expertise, industry insights, and tech buzz in member blogs covering SAP products, technology, and events. Get in the mix!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
vadimklimov
Active Contributor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
07-01-2020
11:35 AM
Disclaimer
Material in this blog post is provided for information and technical features demonstration purposes only. The described technique might introduce CPI runtime node stability and security risks, if applied carelessly or if used to execute imprudent or unsafe shell commands.
Intro and overview
Undoubtedly, a shell is one of essential tools in administrators' toolbox – shell commands are used in day-to-day administration and monitoring activities, and they play an important role in automations of various processes. When working with CPI, normally customers don't need to be concerned about underlying components of the infrastructure where the CPI tenant is hosted, and operating system level access isn't exposed to customers. On the other hand, putting responsibility segregation aspect of cloud service provisioning models aside for a moment, is it possible to retrieve information from lower levels of the CPI runtime and utilize the power of the shell? Can we have a terminal-like access to the CPI runtime node and execute shell commands on it using a command line interface similarly to a local shell? The answer is – YES. It shall be noted that this technique isn't what customers are encouraged to use – nevertheless, let us have a look at it from perspective of technical feasibility and see few examples of its usage.
The overall overview of components that are going to be involved in the end-to-end demonstrations in this blog post, is depicted on the illustration below:

Note: the proof of concept has been performed in the CPI trial tenant that was provisioned in the Cloud Foundry environment. Due to fundamental differences in the overall architecture and the securiy model of Neo and Cloud Foundry environments, installed packages, permissions and access rights of running processes may vary between those two types of tenants. As a result, some system commands that will be demonsrated in this blog post, might not be accessible with the described technique due to differences in installed packages and permission restrictions that are in place in corresponding provisioned tenants.
Background in Java: baseline versions
Java Virtual Machine (JVM) of a CPI runtime node comes with a plethora of techniques that allow it to interact with components of the runtime environment where the JVM is executed. A lot of such capabilities are abstracted by means of Java APIs, and some others are accessible using native interfaces.
In Java, it is possible to create a native child process of the operating system and execute a system command programmatically in the context of that newly created process. This functionality is a part of the Process API, which provides a relevant reflection of a native operating system process –
java.lang.Process.There are two most commonly used approaches to control a Process instance:
- Using
java.lang.ProcessBuilder. A ProcessBuilder helps customize process attributes – for example, environment variables, a working directory, a source of standard input, destinations for standard output and standard error – and finally the command that will be executed in the context of processes that will be created using this ProcessBuilder instance. After the ProcessBuilder instance is configured, we can callProcessBuilder.start()to create one or several Process instances and trigger execution of a required command. This method is preferred when a process needs to be started with a modified environment. - Using
java.lang.Runtime. A Runtime instance is a reflection of the runtime environment where the Java application is running. The application cannot create a new runtime, but it can access its runtime by callingRuntime.getRuntime(). We can then callRuntime.exec()to create a Process instance and trigger execution of a required command – the command and optional process attributes are passed as parameters in this method call. In fact, whenRuntime.exec()is called, it creates a ProcessBuilder instance and uses it to start a single Process instance.
The Process API can be used to execute commands that are recognized by a corresponding operating system where the JVM is executed. Since the CPI runtime node runs on a Linux-based operating system, examples of commands that will be illustrated in this blog post, are going to be Linux shell commands.
For example, if we want to retrieve and print information about the used operating system and its version (I will use a Linux shell command
lsb_release for this in the demo), we can achieve that using the following Java code snippet that illustrates the former approach based on usage of a ProcessBuilder (class and method declarations, as well as import statements are omitted to keep the code snippet more compact; conversion of an InputStream to a String is significantly simplified):ProcessBuilder builder = new ProcessBuilder();
builder.command("lsb_release", "-a");
Process process = builder.start();
InputStream input = process.getInputStream();
BufferedReader reader = new BufferedReader(new InputStreamReader(input));
String output = reader.lines().collect(Collectors.joining("\n"));
System.out.println(output);A sample implementation for the same example, but using the latter approach based on usage of a Runtime, is provided below (class and method declarations, as well as import statements are omitted to keep the code snippet more compact; conversion of an InputStream to a String is significantly simplified):
Runtime runtime = Runtime.getRuntime();
Process process = runtime.exec("lsb_release -a");
InputStream input = process.getInputStream();
BufferedReader reader = new BufferedReader(new InputStreamReader(input));
String output = reader.lines().collect(Collectors.joining("\n"));
System.out.println(output);From Java to Groovy: a one-liner version
Can we make above presented implementations more concise when migrating from Java to Groovy? Yes! The Groovy Development Kit provides enhancements for some classes that are a part of the Java Development Kit – for example, it allows execution of a command specified in a String, by calling
String.execute(). In fact, the runtime will execute the command using a Runtime instance that was described earlier, but using Groovy, we have an option to use a handy shortcut for it. Being combined with additional capabilities that Groovy offers for handling input and output streams, it leads us to a very compact implementation that can be expressed in just a single line of Groovy code:println('lsb_release -a'.execute().text)We can execute this locally using a Groovy shell and verify that the result will be exactly the same as if we would have executed the command more traditionally, in the shell. I’m going to use an Ubuntu distribution that runs in the Windows Subsystem for Linux (WSL) in the remaining part of the demo that involves a Linux shell, but the demonstrated realization can be adapted for use with other Linux distributions or the concept can be applied and implemented for other platforms – for example, it can take the shape of a PowerShell script for a Windows platform.
Command execution using a Linux shell:

Command execution using a Groovy shell:

Groovy meets CPI: a basic iFlow version
We got to know how we can create new native child processes and execute commands in Java/Groovy – we can even run those examples locally and use results of local commands execution in our Java and Groovy applications. But that alone isn't the immediate purpose of this blog post – we are here to make the CPI runtime node execute shell commands for us.
For that, let's embed the described sample implementation into the iFlow in CPI. In sake of simplicity, the iFlow consists of only one Groovy script step that holds the described implementation:

The script function that is used in the Groovy script step, is provided below:
import com.sap.gateway.ip.core.customdev.util.Message
Message processData(Message message) {
message.body = message.getBody(String).execute().text
return message
}In this first demo, commands are going to be submitted in a request message body (hence, we will be sending HTTP POST requests to the iFlow endpoint). The iFlow doesn't check if the message body exists at all – it is assumed that a shell command is provided in the body of the submitted request, otherwise the iFlow shall not be called.
After the iFlow is deployed to runtime, when the iFlow will be triggered and our sample implementation will be invoked, it will create a new native child process and make it execute the specified command – and given it will be a JVM of the CPI runtime that will process the call, a new native child process will be created in the runtime environment of the CPI runtime node, and the command will get executed on the CPI runtime node, and not on the local machine.
Let's use Postman and test the iFlow – clearly, you can also use any relevant HTTP client tool of your choice instead. I use the same shell command as earlier – but this time, it will get executed on the CPI runtime node:
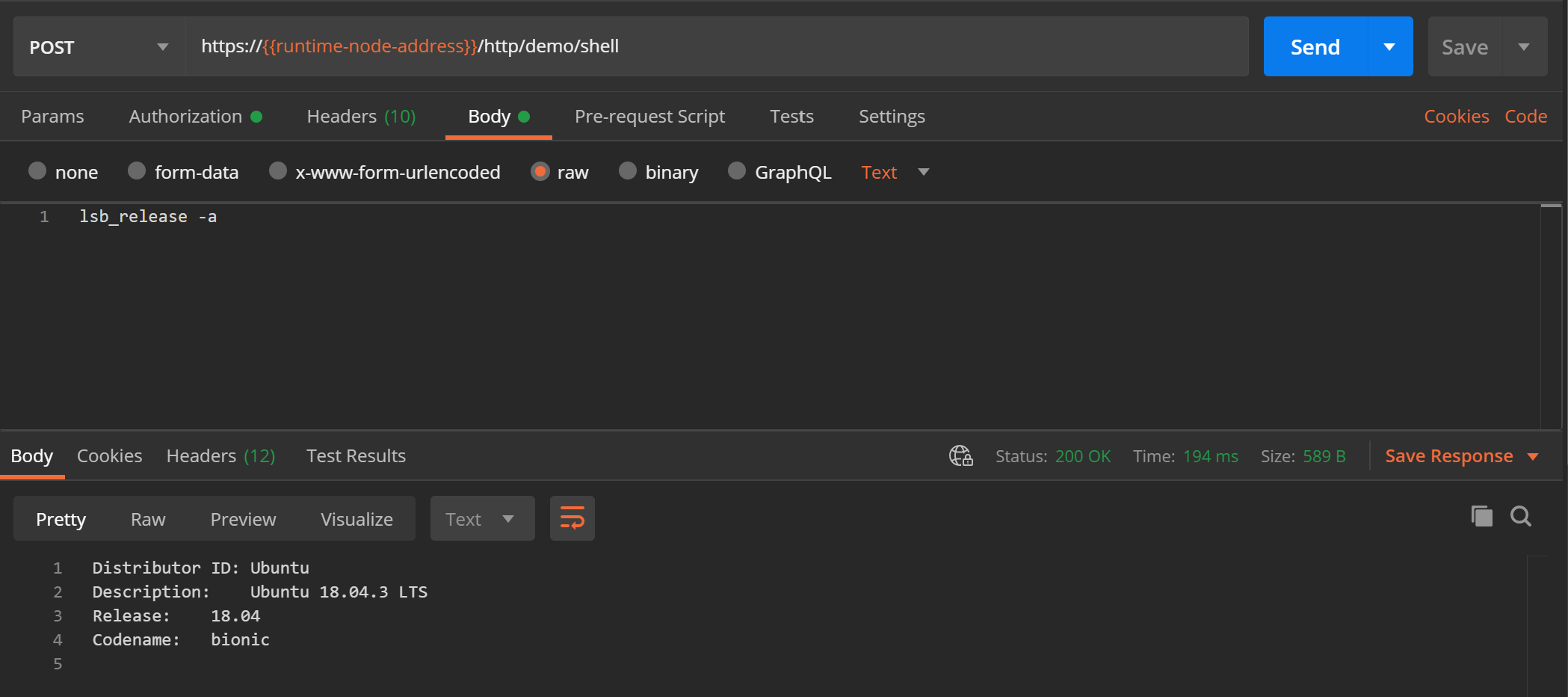
Final notes on the server-side: an enhanced iFlow version
The provided one-liner implementation is indeed an extremely simplified version, as it doesn't customize process attributes, only processes standard output stream of command execution (doesn't handle standard error stream in case the child process ends with an error), doesn't implement error handling and so on. Moreover, the implementation above expects a command to be contained in the message body.
With the introduced enhancement, we make the iFlow a bit more fault-tolerant and safe. We also ensure that we don't leave the created child process unattended and that we kill the child process after some timeout, not to cause long-running child processes (in the demo, I use a timeout of 1 minute). Here, to keep the demo simple, a timeout value is fixed and settled in the script function, but that can get transformed into an externalized configurable parameter of the iFlow or even get submitted by the caller as an additional parameter to allow the caller adjust timeout depending on the command they submit for execution.
To extend an area of application of the iFlow, let's adjust it in such a way that the shell command is submitted in the URL query string, in the query parameter (I will use the query parameter
command for this). A reason behind using a query parameter instead of a message body is because it enables us to use HTTP GET requests to trigger the iFlow – which means, the setup on a client side will not require any additional API testing tools such as Postman, and we will be able to use a web browser to trigger the iFlow. In other words, we get a browser-based method to execute shell commands on the CPI runtime node.A corresponding Groovy function that implements described adjustments and enhancements and that replaces the previously used implementation in the Groovy script step of the iFlow, is provided below:
import com.sap.gateway.ip.core.customdev.util.Message
import java.nio.charset.StandardCharsets
Message processData(Message message) {
final String QUERY_PARAM_COMMAND = 'command'
final long COMMAND_EXEC_TIMEOUT_MS = 60000
String httpQuery = message.headers['CamelHttpQuery'] as String
if (httpQuery) {
httpQuery = URLDecoder.decode(httpQuery, StandardCharsets.UTF_8.name())
String command = httpQuery.tokenize('&').find { it.tokenize('=')[0] == QUERY_PARAM_COMMAND }?.minus("$QUERY_PARAM_COMMAND=")
if (command) {
try {
Process process = command.execute()
process.waitForOrKill(COMMAND_EXEC_TIMEOUT_MS)
message.body = (process.exitValue()) ? process.err.text : process.in.text
} catch (IOException | IllegalThreadStateException e) {
message.body = "Error while executing command\nCommand: ${command}\nError: ${e.message}\n"
}
} else {
message.body = "Error: Command has not been provided, check query parameter '${QUERY_PARAM_COMMAND}'\n"
}
} else {
message.body = "Error: Command has not been provided, check query parameter '${QUERY_PARAM_COMMAND}'\n"
}
return message
}We can still test the iFlow using Postman – or we can use a web browser for testing purposes:


With this, we conclude iFlow enhancements and leave it for now. We were successful to trigger it and execute shell commands on the CPI runtime node and receive results of commands execution back using HTTP clients with a graphical user interface – Postman and a web browser. But we aren't done yet with the client side of the demo: in the introduction, I mentioned we were aiming terminal-like experience when executing shell commands on the CPI runtime node. Using a Linux shell on a local machine to trigger execution of familiar shell commands on a remote Linux server (the CPI runtime node) – that might happen to be convenient. Let's get to the final element of the demo to settle that.
From GUI to CLI on the client-side: adding terminal to the mix
The developed iFlow exposes an HTTP endpoint, so we can send requests to it using some command line tool – here, I’m going to use cURL. For example, one of shell commands that we already observed earlier, can be triggered using cURL in the following way:
To improve usability of this approach and make it more user-friendly, let's create a Bash script and use it instead – the script addresses following aspects:
- Environment specific parameters are externalized and maintained in a configuration file that is used by the script. The file contains a list of key-value pairs for corresponding required parameters that are used to access the CPI runtime node and trigger the iFlow – in particular, a CPI runtime node address, a path to the iFlow endpoint, credentials.
- The shell command is passed as an argument to the script.
- After some basic input validations, the script uses environment specific parameters retrieved from the configuration file and the shell command submitted in the argument, to compose a request that is sent to the CPI runtime node using cURL.
- Outcome of cURL execution is issued to the standard output – this will contain a response produced by the iFlow and any errors that cURL might encounter or receive while calling the iFlow endpoint.
The script implements some basic input validations, but those checks are only to ensure that mandatory parameters aren't missing. The script provides no additional configuration (for example, usage of environment variables to specify location of the configuration file, verbose/silent modes) and doesn't implement any sophisticated input checks (for example, handling of additional arguments, parsing of the configuration file content and protection against malicious commands that can be contained in it) or advanced error handling, so please consider it as a simplified proof of concept used for demonstration purposes, and not as a production-ready reference example.
The script is provided below:
#!/bin/bash
config_file=~/.config/sap-cpi-env.conf
mandatory_params=("runtime_node" "api_path" "username" "password")
command=$1
[[ -z "$command" ]] && echo "Command is missing, check command line arguments" && exit 1
[[ ! -f $config_file ]] && echo "Configuration file $config_file does not exist" && exit 1
echo "Configuration file: $(realpath $config_file)"
. $config_file
missing_params_count=0
for param in "${mandatory_params[@]}"
do
[[ -z "${!param}" ]] && echo "Parameter $param is missing" && (( missing_params_count++ ))
done
[[ "$missing_params_count" -gt 0 ]] && echo "$missing_params_count mandatory parameter(s) is(are) missing, check configuration file" && exit 1
endpoint="https://$runtime_node/http$api_path"
echo "API endpoint: $endpoint"
echo "Command: $command"
echo -e "\n--------------------------------------------------"
curl --user $username:$password \
--get --data-urlencode "command=$command" \
$endpoint
echo -e "\n--------------------------------------------------"I placed the configuration file
sap-cpi-env.conf in the .config directory that can be found in the user's home directory. Location of the configuration file is maintained in the script (it can be replaced in the script or it can be alternatively externalized and stored in the environment variable), and sample content of the configuration file is provided below (username and password were replaced with placeholders here - in the configuration file, these parameters shall refer to valid credentials):runtime_node="22f65e1ftrial.it-cpitrial-rt.cfapps.us10.hana.ondemand.com"
api_path="/demo/shell-cmd"
username="{username}"
password="{password}"Next, to provide a simpler way of executing the script, I enabled a Linux shell to find this script when searching for executables (ensure that the directory where the script is located, is listed in the environment variable
$PATH) and made the script executable (for example, using chmod +x {script file name}).We are all set to go now. Let's now see the entire end-to-end demo in action and run a final series of tests – this time, with some more shell commands.
As it was in previous examples, let's start the final part of the demo from executing the already used command to get information about the operating system and its version using the command
lsb_release:
Some more examples
More details about the system using the command
uname:
Next, let's list available file systems using the command
df: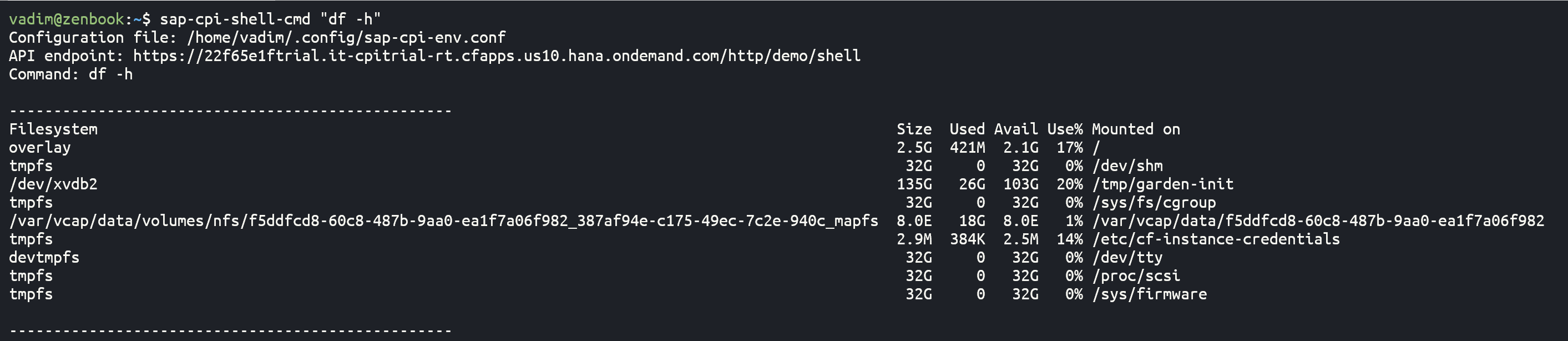
We can also get familiar with information about the CPU using the command
lscpu:
Let's check free and used memory using the command
free:
Next, we take a glance at current processes using the command
ps:
We can also browse content of directories using the command
ls:


And as a final example for now, let's browse content of some files using commands
cat and tail: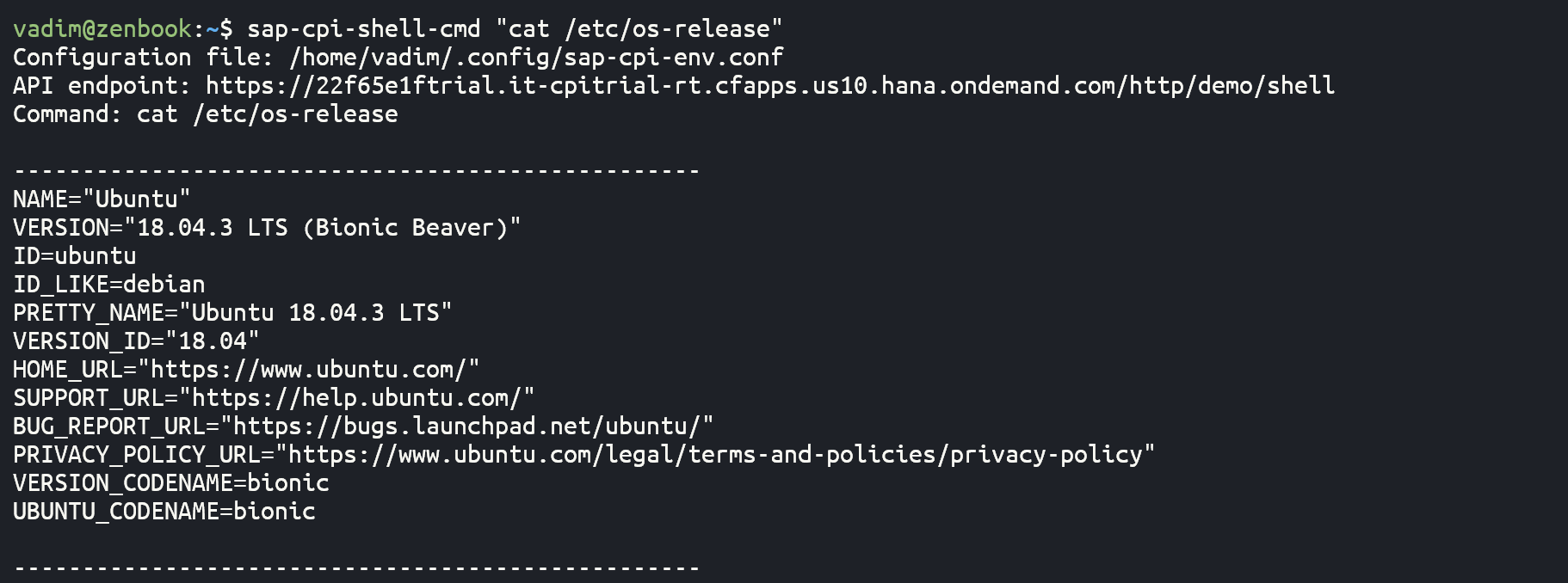


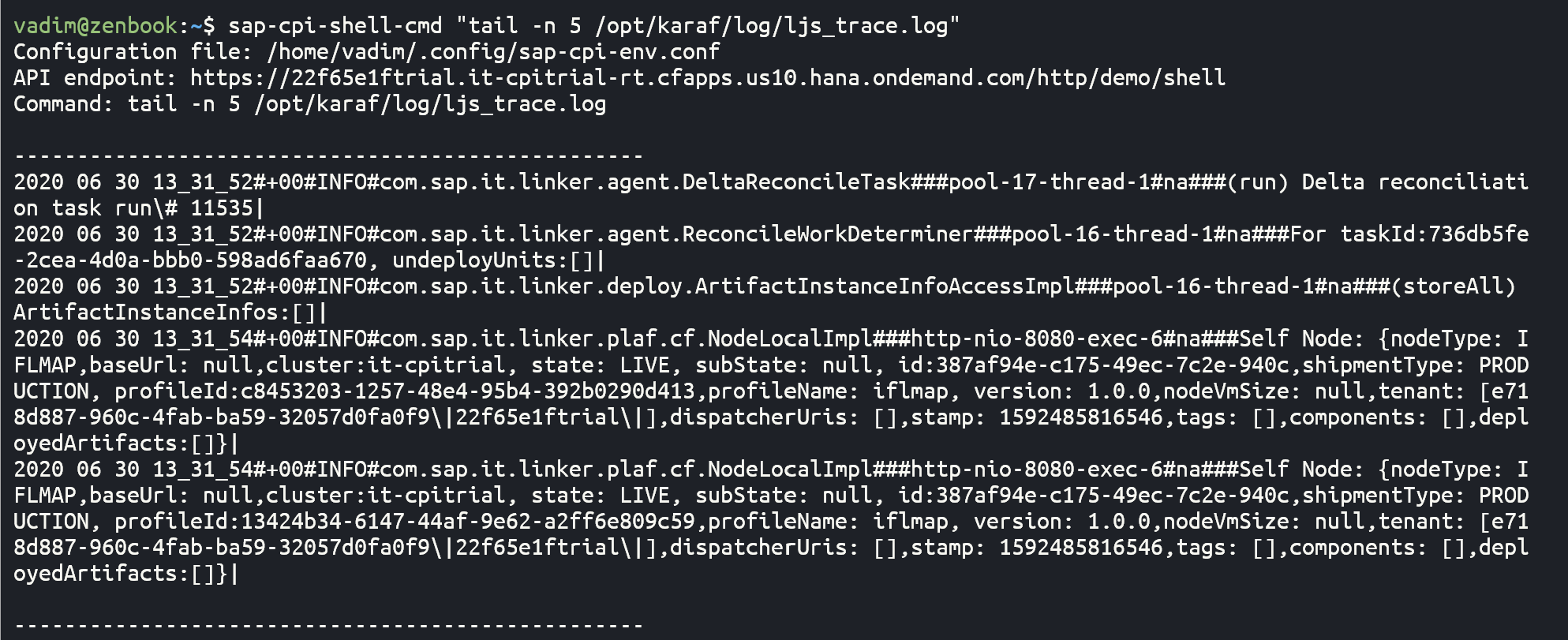
Outro
Above I executed and demonstrated very few examples of commands that help us become more familiar with the runtime environment where the CPI runtime node runs – obviously, there is a lot more to explore as we have just scratched the surface with these very few commands. I hope this already provides a glimpse of the technique and its usage.
The technique that was described in this blog post, is very powerful and allows to access and execute a lot of shell commands on the CPI runtime that can help browse directories, access content of files, get information about running processes, runtime environment workload and configuration, just to name a few. It shall be noted that since the user context which is used when creating and running such child processes in CPI is privileged, the technique shall be used mindfully and responsibly. Let me remind you here that if you get excited about applying this knowledge to practice in CPI tenants, please assess risks associated with executed commands carefully and do it at your own risk.
- SAP Managed Tags:
- SAP Integration Suite,
- Cloud Integration
5 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
"automatische backups"
1 -
"regelmäßige sicherung"
1 -
"TypeScript" "Development" "FeedBack"
1 -
505 Technology Updates 53
1 -
ABAP
14 -
ABAP API
1 -
ABAP CDS Views
2 -
ABAP CDS Views - BW Extraction
1 -
ABAP CDS Views - CDC (Change Data Capture)
1 -
ABAP class
2 -
ABAP Cloud
2 -
ABAP Development
5 -
ABAP in Eclipse
1 -
ABAP Platform Trial
1 -
ABAP Programming
2 -
abap technical
1 -
absl
2 -
access data from SAP Datasphere directly from Snowflake
1 -
Access data from SAP datasphere to Qliksense
1 -
Accrual
1 -
action
1 -
adapter modules
1 -
Addon
1 -
Adobe Document Services
1 -
ADS
1 -
ADS Config
1 -
ADS with ABAP
1 -
ADS with Java
1 -
ADT
2 -
Advance Shipping and Receiving
1 -
Advanced Event Mesh
3 -
AEM
1 -
AI
7 -
AI Launchpad
1 -
AI Projects
1 -
AIML
9 -
Alert in Sap analytical cloud
1 -
Amazon S3
1 -
Analytical Dataset
1 -
Analytical Model
1 -
Analytics
1 -
Analyze Workload Data
1 -
annotations
1 -
API
1 -
API and Integration
3 -
API Call
2 -
Application Architecture
1 -
Application Development
5 -
Application Development for SAP HANA Cloud
3 -
Applications and Business Processes (AP)
1 -
Artificial Intelligence
1 -
Artificial Intelligence (AI)
5 -
Artificial Intelligence (AI) 1 Business Trends 363 Business Trends 8 Digital Transformation with Cloud ERP (DT) 1 Event Information 462 Event Information 15 Expert Insights 114 Expert Insights 76 Life at SAP 418 Life at SAP 1 Product Updates 4
1 -
Artificial Intelligence (AI) blockchain Data & Analytics
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise Oil Gas IoT Exploration Production
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise sustainability responsibility esg social compliance cybersecurity risk
1 -
ASE
1 -
ASR
2 -
ASUG
1 -
Attachments
1 -
Authorisations
1 -
Automating Processes
1 -
Automation
2 -
aws
2 -
Azure
1 -
Azure AI Studio
1 -
B2B Integration
1 -
Backorder Processing
1 -
Backup
1 -
Backup and Recovery
1 -
Backup schedule
1 -
BADI_MATERIAL_CHECK error message
1 -
Bank
1 -
BAS
1 -
basis
2 -
Basis Monitoring & Tcodes with Key notes
2 -
Batch Management
1 -
BDC
1 -
Best Practice
1 -
bitcoin
1 -
Blockchain
3 -
bodl
1 -
BOP in aATP
1 -
BOP Segments
1 -
BOP Strategies
1 -
BOP Variant
1 -
BPC
1 -
BPC LIVE
1 -
BTP
12 -
BTP Destination
2 -
Business AI
1 -
Business and IT Integration
1 -
Business application stu
1 -
Business Application Studio
1 -
Business Architecture
1 -
Business Communication Services
1 -
Business Continuity
1 -
Business Data Fabric
3 -
Business Partner
12 -
Business Partner Master Data
10 -
Business Technology Platform
2 -
Business Trends
4 -
CA
1 -
calculation view
1 -
CAP
3 -
Capgemini
1 -
CAPM
1 -
Catalyst for Efficiency: Revolutionizing SAP Integration Suite with Artificial Intelligence (AI) and
1 -
CCMS
2 -
CDQ
12 -
CDS
2 -
Cental Finance
1 -
Certificates
1 -
CFL
1 -
Change Management
1 -
chatbot
1 -
chatgpt
3 -
CL_SALV_TABLE
2 -
Class Runner
1 -
Classrunner
1 -
Cloud ALM Monitoring
1 -
Cloud ALM Operations
1 -
cloud connector
1 -
Cloud Extensibility
1 -
Cloud Foundry
4 -
Cloud Integration
6 -
Cloud Platform Integration
2 -
cloudalm
1 -
communication
1 -
Compensation Information Management
1 -
Compensation Management
1 -
Compliance
1 -
Compound Employee API
1 -
Configuration
1 -
Connectors
1 -
Consolidation Extension for SAP Analytics Cloud
2 -
Control Indicators.
1 -
Controller-Service-Repository pattern
1 -
Conversion
1 -
Cosine similarity
1 -
cryptocurrency
1 -
CSI
1 -
ctms
1 -
Custom chatbot
3 -
Custom Destination Service
1 -
custom fields
1 -
Customer Experience
1 -
Customer Journey
1 -
Customizing
1 -
cyber security
3 -
cybersecurity
1 -
Data
1 -
Data & Analytics
1 -
Data Aging
1 -
Data Analytics
2 -
Data and Analytics (DA)
1 -
Data Archiving
1 -
Data Back-up
1 -
Data Flow
1 -
Data Governance
5 -
Data Integration
2 -
Data Quality
12 -
Data Quality Management
12 -
Data Synchronization
1 -
data transfer
1 -
Data Unleashed
1 -
Data Value
8 -
database tables
1 -
Datasphere
3 -
datenbanksicherung
1 -
dba cockpit
1 -
dbacockpit
1 -
Debugging
2 -
Delimiting Pay Components
1 -
Delta Integrations
1 -
Destination
3 -
Destination Service
1 -
Developer extensibility
1 -
Developing with SAP Integration Suite
1 -
Devops
1 -
digital transformation
1 -
Documentation
1 -
Dot Product
1 -
DQM
1 -
dump database
1 -
dump transaction
1 -
e-Invoice
1 -
E4H Conversion
1 -
Eclipse ADT ABAP Development Tools
2 -
edoc
1 -
edocument
1 -
ELA
1 -
Embedded Consolidation
1 -
Embedding
1 -
Embeddings
1 -
Employee Central
1 -
Employee Central Payroll
1 -
Employee Central Time Off
1 -
Employee Information
1 -
Employee Rehires
1 -
Enable Now
1 -
Enable now manager
1 -
endpoint
1 -
Enhancement Request
1 -
Enterprise Architecture
1 -
ETL Business Analytics with SAP Signavio
1 -
Euclidean distance
1 -
Event Dates
1 -
Event Driven Architecture
1 -
Event Mesh
2 -
Event Reason
1 -
EventBasedIntegration
1 -
EWM
1 -
EWM Outbound configuration
1 -
EWM-TM-Integration
1 -
Existing Event Changes
1 -
Expand
1 -
Expert
2 -
Expert Insights
2 -
Exploits
1 -
Fiori
14 -
Fiori Elements
2 -
Fiori SAPUI5
12 -
Flask
1 -
Full Stack
8 -
Funds Management
1 -
General
1 -
General Splitter
1 -
Generative AI
1 -
Getting Started
1 -
GitHub
8 -
Grants Management
1 -
GraphQL
1 -
groovy
1 -
GTP
1 -
HANA
6 -
HANA Cloud
2 -
Hana Cloud Database Integration
2 -
HANA DB
2 -
HANA XS Advanced
1 -
Historical Events
1 -
home labs
1 -
HowTo
1 -
HR Data Management
1 -
html5
8 -
HTML5 Application
1 -
Identity cards validation
1 -
idm
1 -
Implementation
1 -
input parameter
1 -
instant payments
1 -
Integration
3 -
Integration Advisor
1 -
Integration Architecture
1 -
Integration Center
1 -
Integration Suite
1 -
intelligent enterprise
1 -
iot
1 -
Java
1 -
job
1 -
Job Information Changes
1 -
Job-Related Events
1 -
Job_Event_Information
1 -
joule
4 -
Journal Entries
1 -
Just Ask
1 -
Kerberos for ABAP
8 -
Kerberos for JAVA
8 -
KNN
1 -
Launch Wizard
1 -
Learning Content
2 -
Life at SAP
5 -
lightning
1 -
Linear Regression SAP HANA Cloud
1 -
Loading Indicator
1 -
local tax regulations
1 -
LP
1 -
Machine Learning
2 -
Marketing
1 -
Master Data
3 -
Master Data Management
14 -
Maxdb
2 -
MDG
1 -
MDGM
1 -
MDM
1 -
Message box.
1 -
Messages on RF Device
1 -
Microservices Architecture
1 -
Microsoft Universal Print
1 -
Middleware Solutions
1 -
Migration
5 -
ML Model Development
1 -
Modeling in SAP HANA Cloud
8 -
Monitoring
3 -
MTA
1 -
Multi-Record Scenarios
1 -
Multiple Event Triggers
1 -
Myself Transformation
1 -
Neo
1 -
New Event Creation
1 -
New Feature
1 -
Newcomer
1 -
NodeJS
2 -
ODATA
2 -
OData APIs
1 -
odatav2
1 -
ODATAV4
1 -
ODBC
1 -
ODBC Connection
1 -
Onpremise
1 -
open source
2 -
OpenAI API
1 -
Oracle
1 -
PaPM
1 -
PaPM Dynamic Data Copy through Writer function
1 -
PaPM Remote Call
1 -
PAS-C01
1 -
Pay Component Management
1 -
PGP
1 -
Pickle
1 -
PLANNING ARCHITECTURE
1 -
Popup in Sap analytical cloud
1 -
PostgrSQL
1 -
POSTMAN
1 -
Process Automation
2 -
Product Updates
4 -
PSM
1 -
Public Cloud
1 -
Python
4 -
Qlik
1 -
Qualtrics
1 -
RAP
3 -
RAP BO
2 -
Record Deletion
1 -
Recovery
1 -
recurring payments
1 -
redeply
1 -
Release
1 -
Remote Consumption Model
1 -
Replication Flows
1 -
research
1 -
Resilience
1 -
REST
1 -
REST API
2 -
Retagging Required
1 -
Risk
1 -
Rolling Kernel Switch
1 -
route
1 -
rules
1 -
S4 HANA
1 -
S4 HANA Cloud
1 -
S4 HANA On-Premise
1 -
S4HANA
3 -
S4HANA_OP_2023
2 -
SAC
10 -
SAC PLANNING
9 -
SAP
4 -
SAP ABAP
1 -
SAP Advanced Event Mesh
1 -
SAP AI Core
8 -
SAP AI Launchpad
8 -
SAP Analytic Cloud Compass
1 -
Sap Analytical Cloud
1 -
SAP Analytics Cloud
4 -
SAP Analytics Cloud for Consolidation
3 -
SAP Analytics Cloud Story
1 -
SAP analytics clouds
1 -
SAP BAS
1 -
SAP Basis
6 -
SAP BODS
1 -
SAP BODS certification.
1 -
SAP BTP
21 -
SAP BTP Build Work Zone
2 -
SAP BTP Cloud Foundry
6 -
SAP BTP Costing
1 -
SAP BTP CTMS
1 -
SAP BTP Innovation
1 -
SAP BTP Migration Tool
1 -
SAP BTP SDK IOS
1 -
SAP Build
11 -
SAP Build App
1 -
SAP Build apps
1 -
SAP Build CodeJam
1 -
SAP Build Process Automation
3 -
SAP Build work zone
10 -
SAP Business Objects Platform
1 -
SAP Business Technology
2 -
SAP Business Technology Platform (XP)
1 -
sap bw
1 -
SAP CAP
2 -
SAP CDC
1 -
SAP CDP
1 -
SAP CDS VIEW
1 -
SAP Certification
1 -
SAP Cloud ALM
4 -
SAP Cloud Application Programming Model
1 -
SAP Cloud Integration for Data Services
1 -
SAP cloud platform
8 -
SAP Companion
1 -
SAP CPI
3 -
SAP CPI (Cloud Platform Integration)
2 -
SAP CPI Discover tab
1 -
sap credential store
1 -
SAP Customer Data Cloud
1 -
SAP Customer Data Platform
1 -
SAP Data Intelligence
1 -
SAP Data Migration in Retail Industry
1 -
SAP Data Services
1 -
SAP DATABASE
1 -
SAP Dataspher to Non SAP BI tools
1 -
SAP Datasphere
9 -
SAP DRC
1 -
SAP EWM
1 -
SAP Fiori
3 -
SAP Fiori App Embedding
1 -
Sap Fiori Extension Project Using BAS
1 -
SAP GRC
1 -
SAP HANA
1 -
SAP HCM (Human Capital Management)
1 -
SAP HR Solutions
1 -
SAP IDM
1 -
SAP Integration Suite
9 -
SAP Integrations
4 -
SAP iRPA
2 -
SAP LAGGING AND SLOW
1 -
SAP Learning Class
1 -
SAP Learning Hub
1 -
SAP Odata
2 -
SAP on Azure
1 -
SAP PartnerEdge
1 -
sap partners
1 -
SAP Password Reset
1 -
SAP PO Migration
1 -
SAP Prepackaged Content
1 -
SAP Process Automation
2 -
SAP Process Integration
2 -
SAP Process Orchestration
1 -
SAP S4HANA
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Cloud for Finance
1 -
SAP S4HANA Cloud private edition
1 -
SAP Sandbox
1 -
SAP STMS
1 -
SAP successfactors
3 -
SAP SuccessFactors HXM Core
1 -
SAP Time
1 -
SAP TM
2 -
SAP Trading Partner Management
1 -
SAP UI5
1 -
SAP Upgrade
1 -
SAP Utilities
1 -
SAP-GUI
8 -
SAP_COM_0276
1 -
SAPBTP
1 -
SAPCPI
1 -
SAPEWM
1 -
sapmentors
1 -
saponaws
2 -
SAPS4HANA
1 -
SAPUI5
5 -
schedule
1 -
Script Operator
1 -
Secure Login Client Setup
8 -
security
9 -
Selenium Testing
1 -
Self Transformation
1 -
Self-Transformation
1 -
SEN
1 -
SEN Manager
1 -
service
1 -
SET_CELL_TYPE
1 -
SET_CELL_TYPE_COLUMN
1 -
SFTP scenario
2 -
Simplex
1 -
Single Sign On
8 -
Singlesource
1 -
SKLearn
1 -
Slow loading
1 -
soap
1 -
Software Development
1 -
SOLMAN
1 -
solman 7.2
2 -
Solution Manager
3 -
sp_dumpdb
1 -
sp_dumptrans
1 -
SQL
1 -
sql script
1 -
SSL
8 -
SSO
8 -
Substring function
1 -
SuccessFactors
1 -
SuccessFactors Platform
1 -
SuccessFactors Time Tracking
1 -
Sybase
1 -
system copy method
1 -
System owner
1 -
Table splitting
1 -
Tax Integration
1 -
Technical article
1 -
Technical articles
1 -
Technology Updates
14 -
Technology Updates
1 -
Technology_Updates
1 -
terraform
1 -
Threats
2 -
Time Collectors
1 -
Time Off
2 -
Time Sheet
1 -
Time Sheet SAP SuccessFactors Time Tracking
1 -
Tips and tricks
2 -
toggle button
1 -
Tools
1 -
Trainings & Certifications
1 -
Transformation Flow
1 -
Transport in SAP BODS
1 -
Transport Management
1 -
TypeScript
2 -
ui designer
1 -
unbind
1 -
Unified Customer Profile
1 -
UPB
1 -
Use of Parameters for Data Copy in PaPM
1 -
User Unlock
1 -
VA02
1 -
Validations
1 -
Vector Database
2 -
Vector Engine
1 -
Visual Studio Code
1 -
VSCode
1 -
Vulnerabilities
1 -
Web SDK
1 -
work zone
1 -
workload
1 -
xsa
1 -
XSA Refresh
1
- « Previous
- Next »
Related Content
- Developing & Deploying the UI5 App to Cloud Foundry and Accessing from App-router End-to-End Steps in Technology Blogs by Members
- Kerberos Error when task "deploy" from db-deployer in Technology Q&A
- SAP HANA HDBSQL to execute SQL commands at OS level in background in Technology Q&A
- Explore Business Continuity Options for SAP workload using AWS Elastic DisasterRecoveryService (DRS) in Technology Blogs by Members
- Part 2:- SAP Basis OS support on SUSE Linux for beginners in Technology Blogs by Members
Top kudoed authors
| User | Count |
|---|---|
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 3 | |
| 3 |