
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- How to Connect SAP Enterprise Threat Detection to ...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Advisor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
12-18-2019
12:59 AM
The announcement of the newest version Enterprise Threat Detection 2.1 was made on December 3, 2019 in a recent blog by Michael Schmitt, the Enterprise Threat Detection Product Manager.
Of interest to those customers currently using Splunk Enterprise Security, the recent announcement included a new feature in ETD 2.1 to issue alerts to Splunk Enterprise Security for real time collaboration between SAP Security teams using Enterprise Threat Detection and IT Security teams using Splunk Enterprise Security.
This out of the box connector can be easily set up in Enterprise Threat Detection and Splunk in order to facilitate collaboration between the SAP Security teams and the Splunk Enterprise Security teams as described in my earlier blog, dated November 21, 2019.
This announced connectivity is an added feature that provides two-way communication with the publishing of an alert to Splunk Enterprise Security for further investigation into the event at the infrastructure level. There is also an out of the box connector available to Enterprise Threat Detection from Splunk Enterprise Security when it finds suspicious behavior at the infrastructure layer.
Here is how an alert from Splunk looks in Enterprise Threat Detection:

Let’s break this down a bit further. First, let’s look at an alert published by Enterprise Threat Detection to Splunk.
When an attack detection pattern is triggered in Enterprise Threat Detection, an alert is issued with an alert identifier – it looks like this:
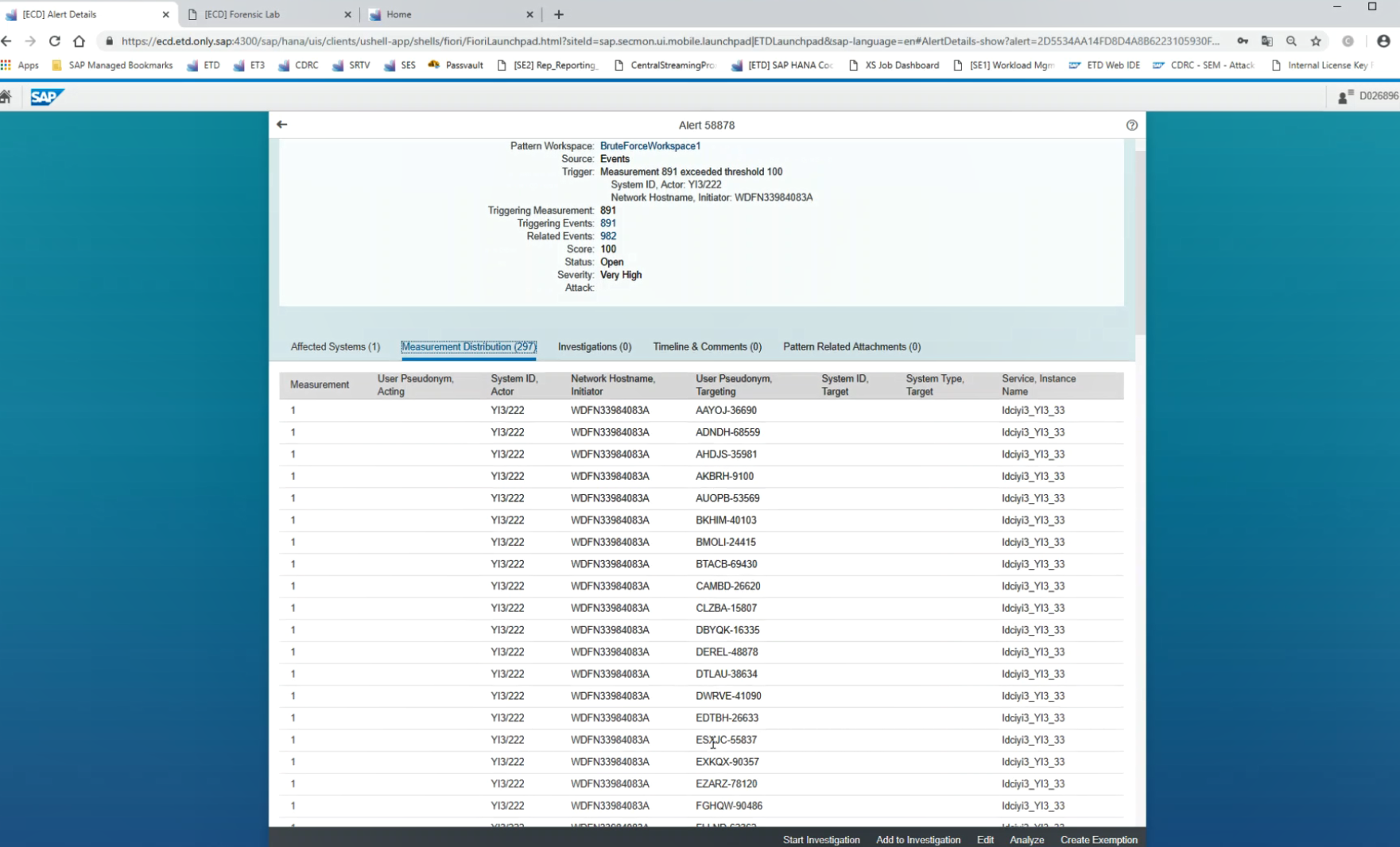
We can see here that the alert has a unique identifier and was triggered due to the Brute Force Attack Detection Pattern. We can also see the network host name initiator – WDFN33984083A who is the bad actor in this case. We also see the system that was acted upon identified as System ID, Actor and System ID Y13/222.
In Enterprise Threat Detection, we can see that the initiator, WDFN33984083A was able to access monitored data (sensitive data which turned out to be intellectual property – the pump architecture plans) and was able to download data as a result of the successful brute force attack:

These details will be published through the alert publishing feature to Splunk Enterprise Security. Enterprise Threat Detection supports JSON, CEF, or LEEF formats. In this case, a fully formed JSON record was published to Splunk Enterprise Security:

Here we can see that the information sent to Splunk Enterprise Security includes the Alert Identifier, the Attack Detection Pattern that was triggered that would be of interest to Splunk, the timestamps, severity level, terminal id and more.
Splunk Enterprise Security pulls in the information from the Alert and incorporates this information into the Splunk Enterprise Security in the Incident Review area:
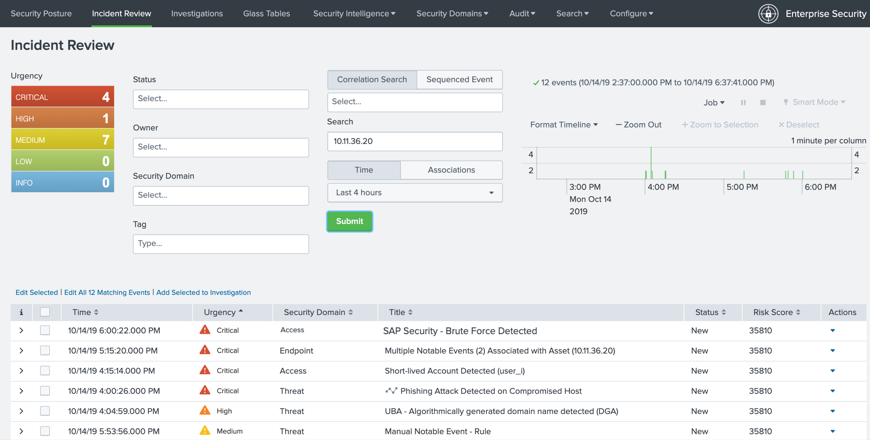
This information is now able to be correlated with Splunk Enterprise Security. Information is available related to activities regarding this endpoint, IP addresses and current threats or active compromise in the environment.
Additional information, including a risk score to prioritize the event, can be found in the Splunk Enterprise Security solution.
In Splunk, visibility into the SAP application and the reported attack is found along with additional information which is correlated in Splunk Enterprise Security. This supporting information includes the history related to this event and user, the phase of the Mitre Attack Kill Chain, tactics and techniques used along with a description to help the security analyst understand what needs to be done.

Splunk Enterprise Security can assist in threat hunting activities to further track down the issue:

How to enable SAP Enterprise Threat Detection to send alerts to Splunk?
The system can be set up through the Admin function of Enterprise Threat Detection using the Settings selection and then selecting Manage Alert Processing. The triggering events can then be sent to Splunk and this threat information can be consumed by Splunk Enterprise Security. To refine the alert, a pattern filter can be set up to only send critical alerts. More information is available in the Enterprise Threat Detection documentation. The SAP and Splunk security teams can work together to determine the correct solution set up options. Notice the JSON set up option in the screen below:
Once the set up is complete for Enterprise Threat Detection, alerts will be published to the Splunk HTTP Event Collector (HEC).
To ensure the events will be properly recognized in Splunk Enterprise Security, the Splunk HTTP Event Collector (HEC) must be enabled and the event collector token must be received. A user must be set up with the EtdSecExpert role for SAP Enterprise Threat Detection. More set up information is in the official Splunk documentation.
Other set up options in Enterprise Threat Detection, include starting the SAP HANA XS tool and creating an extension to define the host and port of the Splunk HTTP Event Collector tool. Choose the basic authentication options available and alerts will soon be sent to Splunk Event Collector every minute!
To view the alerts in Splunk, search on sapetd_alert.
Look out for more information soon on how to leverage Splunk Enterprise Security and SAP Enterprise Threat Detection together!
Of interest to those customers currently using Splunk Enterprise Security, the recent announcement included a new feature in ETD 2.1 to issue alerts to Splunk Enterprise Security for real time collaboration between SAP Security teams using Enterprise Threat Detection and IT Security teams using Splunk Enterprise Security.
This out of the box connector can be easily set up in Enterprise Threat Detection and Splunk in order to facilitate collaboration between the SAP Security teams and the Splunk Enterprise Security teams as described in my earlier blog, dated November 21, 2019.
This announced connectivity is an added feature that provides two-way communication with the publishing of an alert to Splunk Enterprise Security for further investigation into the event at the infrastructure level. There is also an out of the box connector available to Enterprise Threat Detection from Splunk Enterprise Security when it finds suspicious behavior at the infrastructure layer.
Here is how an alert from Splunk looks in Enterprise Threat Detection:

Let’s break this down a bit further. First, let’s look at an alert published by Enterprise Threat Detection to Splunk.
When an attack detection pattern is triggered in Enterprise Threat Detection, an alert is issued with an alert identifier – it looks like this:

We can see here that the alert has a unique identifier and was triggered due to the Brute Force Attack Detection Pattern. We can also see the network host name initiator – WDFN33984083A who is the bad actor in this case. We also see the system that was acted upon identified as System ID, Actor and System ID Y13/222.
In Enterprise Threat Detection, we can see that the initiator, WDFN33984083A was able to access monitored data (sensitive data which turned out to be intellectual property – the pump architecture plans) and was able to download data as a result of the successful brute force attack:

These details will be published through the alert publishing feature to Splunk Enterprise Security. Enterprise Threat Detection supports JSON, CEF, or LEEF formats. In this case, a fully formed JSON record was published to Splunk Enterprise Security:

Here we can see that the information sent to Splunk Enterprise Security includes the Alert Identifier, the Attack Detection Pattern that was triggered that would be of interest to Splunk, the timestamps, severity level, terminal id and more.
Splunk Enterprise Security pulls in the information from the Alert and incorporates this information into the Splunk Enterprise Security in the Incident Review area:

This information is now able to be correlated with Splunk Enterprise Security. Information is available related to activities regarding this endpoint, IP addresses and current threats or active compromise in the environment.
Additional information, including a risk score to prioritize the event, can be found in the Splunk Enterprise Security solution.
In Splunk, visibility into the SAP application and the reported attack is found along with additional information which is correlated in Splunk Enterprise Security. This supporting information includes the history related to this event and user, the phase of the Mitre Attack Kill Chain, tactics and techniques used along with a description to help the security analyst understand what needs to be done.

Splunk Enterprise Security can assist in threat hunting activities to further track down the issue:

How to enable SAP Enterprise Threat Detection to send alerts to Splunk?
The system can be set up through the Admin function of Enterprise Threat Detection using the Settings selection and then selecting Manage Alert Processing. The triggering events can then be sent to Splunk and this threat information can be consumed by Splunk Enterprise Security. To refine the alert, a pattern filter can be set up to only send critical alerts. More information is available in the Enterprise Threat Detection documentation. The SAP and Splunk security teams can work together to determine the correct solution set up options. Notice the JSON set up option in the screen below:
Once the set up is complete for Enterprise Threat Detection, alerts will be published to the Splunk HTTP Event Collector (HEC).
To ensure the events will be properly recognized in Splunk Enterprise Security, the Splunk HTTP Event Collector (HEC) must be enabled and the event collector token must be received. A user must be set up with the EtdSecExpert role for SAP Enterprise Threat Detection. More set up information is in the official Splunk documentation.
Other set up options in Enterprise Threat Detection, include starting the SAP HANA XS tool and creating an extension to define the host and port of the Splunk HTTP Event Collector tool. Choose the basic authentication options available and alerts will soon be sent to Splunk Event Collector every minute!
To view the alerts in Splunk, search on sapetd_alert.
Look out for more information soon on how to leverage Splunk Enterprise Security and SAP Enterprise Threat Detection together!
Labels:
1 Comment
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
91 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
66 -
Expert
1 -
Expert Insights
178 -
Expert Insights
293 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
12 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
337 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
415 -
Workload Fluctuations
1
Related Content
- IoT - Ultimate Data Cyber Security - with Enterprise Blockchain and SAP BTP 🚀 in Technology Blogs by Members
- SAP Signavio is the highest ranked Leader in the SPARK Matrix™ Digital Twin of an Organization (DTO) in Technology Blogs by SAP
- Accelerate Business Process Development with SAP Build Process Automation Pre-Built Content in Technology Blogs by SAP
- ABAP Cloud Developer Trial 2022 Available Now in Technology Blogs by SAP
- It’s Official - SAP BTP is Again a Leader in G2’s Reports in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 29 | |
| 21 | |
| 10 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 5 | |
| 5 |