
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by Members
- SAP Analytics Cloud: SSO to Live Universe Data Con...
Technology Blogs by Members
Explore a vibrant mix of technical expertise, industry insights, and tech buzz in member blogs covering SAP products, technology, and events. Get in the mix!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
former_member18
Explorer
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
09-11-2019
7:28 AM
Introduction
In my first blog post I mentioned that future blog posts could be SAP Analytics Cloud, SAC, or SAP BusinessObjects BI Platform 4.2, SAP BI 4.2. Good News! You get both in this blog post!
Most customers I tend to work with will be organisations who have already got deployments of SAP BI Platform and will have spent a lot of time developing Universes and building documents off of them.
A great feature of SAC is that you can base your stories on data imported from Universes or retrieve data live using CORS. The only annoying thing getting in your way of live data is that every time you open a story, you are blocked from getting to your Universe as you have to login to SAP BI 4.2 to retrieve data. This will be frustrating for users as they presented with the screen below:

In this blog post, we will go through the process of setting up SAML SSO to your SAP BI Platform using Azure AD.
Note: This is not same process as setting up SAML SSO to the BI Launchpad. For that, check out Francisco Almeida's guide available at:
https://blogs.sap.com/2018/08/17/setting-up-sap-businessintelligence-bi-platform-saml-single-sign-on...
Pre-Reqs
The following is needed in order to complete Azure AD integration:
- A SAC tenant which your organisation will have already have. If you are studying this yourself, I believe you will need to purchase a tenant rather than use the trial version. You can purchase a 1 user license for a year (minimum subscription term). This will give you a license for 1 admin account and 1 user in a single tenant. If you only want it for a year, remember to turn off auto-renew subscription. I paid around £240 for 1 year. Check out https://www.sap.com/uk/products/cloud-analytics.html if you want purchase a tenant.
- Microsoft Azure subscription which again your organisation should have. If not, you can get your own free subscription for 12 months access. Check out https://azure.microsoft.com/en-gb/free/ to setup an account. You do also need Premium AD which is not free but you get a 30 day trial initially.
- A PC with Google Chrome and Mozilla Firefox (I know its not supported but you may need it for troubleshooting.)
- SAML Tracer addon for Firefox. This is needed as the SAML SSO is performed in a pop up box. The SAML Tracer runs in a separate window and will capture all browser SAML activity. https://addons.mozilla.org/en-GB/firefox/addon/saml-tracer/
- SAP BI Platform 4.2 with SP04 or higher deployed. For this guide it assumed that the install has been placed in the default directory of C:\Program Files (x86)\SAP BusinessObjects and the default Tomcat has been used.
- To have performed steps 1-7 of the Live Universe connection guided playlist: https://www.sapanalytics.cloud/guided_playlists/connect-sap-universe-live (Not a fan of the security rights part though, Full Control access to Webi and using Advanced rights, hmmmm)
- SAML SSO in SAC has already been set up against Azure AD
Setup Process
Step 1: SAP BI - Update boe.properties
The first step is to update the boe.properties file to have SAML enabled. Following the Guided Playlist, the file should look something like:
# BOE Server info
boe.restUrl=http://<BOE_SERVER_NAME>:8080/biprws
boe.authenticationMode=secEnterpriseYou will note that I am not using WACS and just using the Restful web services now hosted on Tomcat. It seems faster. You could just use localhost if the BOE LIve Data connect WAR file has been deployed on that same Tomcat as standard BI Launchpad, etc.
The authentication mode needs to be changed to saml and additional lines need to be added so the file reads as:
# BOE Server info
boe.restUrl=http://<BOE_SERVER_NAME>:8080/biprws
boe.authenticationMode=saml
# SAML via trusted authentication
boe.trustedauth.method=HTTP_HEADER
boe.trustedauth.user.name.parameter=X-SAP-TRUSTED-USER
boe.httpTimeout=180000Step 2: SAP BI - Update web.xml
Using a text editor like Notepad++, open the web.xml located in:
C:\Program Files (x86)\SAP BusinessObjects\tomcat\webapps\sap#boc#ina\WEB-INFThere are 2 sections that need to be uncommented.
Section1 before:

Section 1 after:

Section 2 before:

Section 2 after:

Save and close the file, then restart Apache Tomcat.
Step 3: SAP BI - Enable Trusted Authentication
The next step is to enable Trusted Authentication and load TrustedPrincipal.conf into Tomcat.
It maybe the case that you have already enabled Trusted Authentication before, say if you have setup SAML SSO to the BI Launchpad. In which case you only need to place the previously generated TrustedPrincipal.conf file in the right location.
It is assumed that you are starting from scratch.
- Log in to the Central Management Console (CMC) as Administrator
- Go to Home > Authentication > Enterprise
- Ensure “Trusted Authentication is enabled” is checked
- Click "New Shared Secret"
- Click "Download Shared Secret" and save TrustedPrincipal.conf to on all web and app servers:
- C:\Program Files (x86)\SAP BusinessObjects\SAP BusinessObjects Enterprise XI 4.0\win32_x86
- C:\Program Files (x86)\SAP BusinessObjects\SAP BusinessObjects Enterprise XI 4.0\win64_x64

- Click Update Settings and then close the Enterprise Window
- On the server hosting Apache Tomcat and the biprws.war file deployed, place the TrustedPrincipal.conf in a folder. I put it in D:\trustauth
- Open Tomcat Configuration by going to Start > Tomcat > Tomcat Configuration
- Go to Java Tab
- In Java Options add:
-Dbobj.trustedauth.home=D:\trustauth
- Click OK
The properties window should have looked like this (yes I am using Tomcat 9 rather than bundled Tomcat):

- Restart Tomcat
Step 4: Azure - Create Live DC Enterprise Application
- Login to Azure Portal (https://portal.azure.com) and click “Azure Active Directory”

- Select “Enterprise applications”

- Click “New Application”

- Click "Non-gallery application"

- Give the application a name. e.g. SAP BOE Live DC. Then Click OK.

- You have now created the Application
Step 5: Azure – Download Metadata from Azure to BOE Live Data Connect
- In the SAP BOE Live DC Overview screen, click Single Sign-On
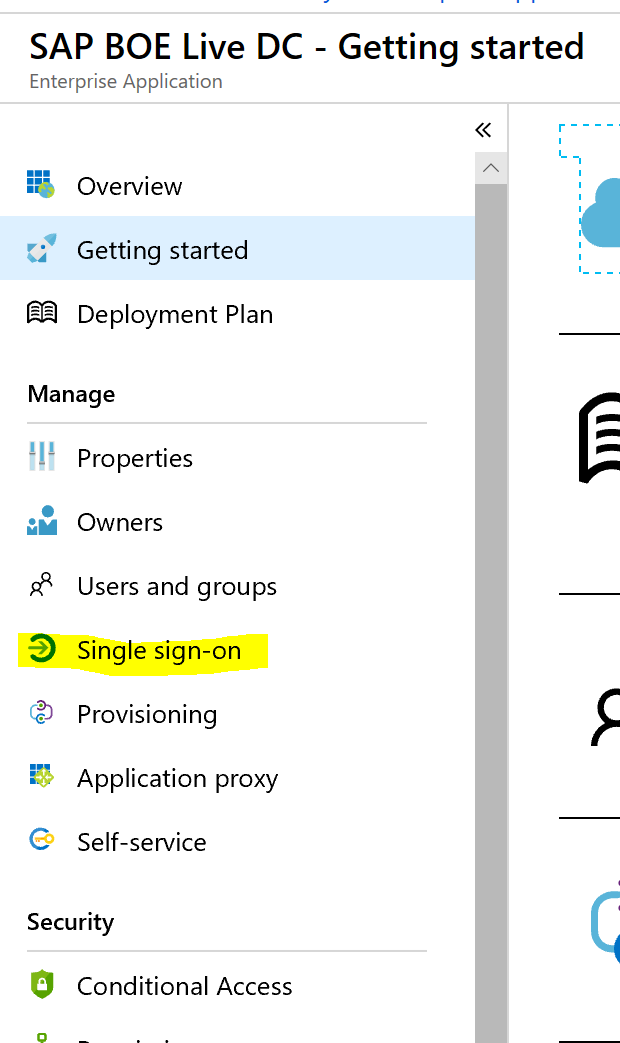
- Select “SAML”

- Under SAML Signing Certificate, download the Federation Metadata XML file. The file will have a default name of your application e.g. SAP BOE Live DC.xml.

- Change the name of the file to idp_metadata.xml and place in C:\Program Files (x86)\SAP BusinessObjects\tomcat\webapps\sap#boc#ina\WEB-INF\classes\metadata on the SAP BI server

Step 6: SAP BI - Create a Keystore
The next step is to create a certificate keystore like you would for enabling SSL. This is needed for SAML SSO. If you have set up SAML to SAP BI Launchpad, you will have noticed that SAP provided a keystore in the WEB-INF folder of the BOE war file and had configured the securitycontext.xml file to use it. This is not the case with the BOE Live Data Connect war file and defaults to have no keystore. SSO will not work without the keystore and securitycontext.xml file updated to use the file.
Here are the steps to create and place the keystore:
- On the SAP BI server, open the command prompt as administrator
- Navigate to:
C:\Program Files (x86)\SAP BusinessObjects\SAP BusinessObjects Enterprise XI 4.0\win64_x64\sapjvm\jre\bin- Run the following command:
keytool.exe -genkey -alias boe -keyalg RSA -keystore "samlKeystore.jks" -keysize 2048- You will be prompted with a number of questions to generate the keystore. The things like first name, country, etc are not important. What is important is setting the 2 passwords (make a note of what you set them to). I have highlighted what you type in Red, you won't see the passwords actually being typed:
Enter keystore password: Password1
Re-enter new password: Password1
What is your first and last name?
[Unknown]:
What is the name of your organizational unit?
[Unknown]: IT
What is the name of your organization?
[Unknown]: Itelligence
What is the name of your City or Locality?
[Unknown]: London
What is the name of your State or Province?
[Unknown]: London
What is the two-letter country code for this unit?
[Unknown]: GB
Is CN=Unknown, OU=IT, O=Itelligence, L=London, ST=London, C=GB correct?
[no]: yes
Enter key password for <boe>
(RETURN if same as keystore password): Password2
Re-enter new password: Password2- Copy the samlKeystore.jks file from:
C:\Program Files (x86)\SAP BusinessObjects\SAP BusinessObjects Enterprise XI 4.0\win64_x64\sapjvm\jre\bin- To
C:\Program Files (x86)\SAP BusinessObjects\tomcat\webapps\sap#boc#ina\WEB-INFStep 7: SAP BI - Update securityContext.xml
You now need to update securityContext.xml file to use the keystore created in the previous section and also set it to reflect URL that will be used to access the Live Universe connection. Doing this will mean that the metadata file that you upload into Azure will contain all the correct data without need for modification in Azure. By default the metadata file will contain a URL for localhost with no https.
The steps below go through the changes required for the securityContext.xml:
- Using a text editor, e.g. Notepad++, open the securityContext.xml file located in:
C:\Program Files (x86)\SAP BusinessObjects\tomcat\webapps\sap#boc#ina\WEB-INF- Locate the following lines of code:
<!-- Central storage of cryptographic keys -->
<bean id="keyManager" class="org.springframework.security.saml.key.EmptyKeyManager"/>- Update it to read as below:
<!-- Central storage of cryptographic keys -->
<!--<bean id="keyManager" class="org.springframework.security.saml.key.EmptyKeyManager"/>-->
<bean id="keyManager" class="org.springframework.security.saml.key.JKSKeyManager">
<constructor-arg value="/WEB-INF/samlKeystore.jks" />
<constructor-arg type="java.lang.String" value="Password1"/>
<constructor-arg>
<map>
<entry key="boe" value="Password2"/>
</map>
</constructor-arg>
<constructor-arg type="java.lang.String" value="boe"/>
</bean>- Locate the next section of code:
<!-- Filter automatically generates default SP metadata -->
<bean id="metadataGeneratorFilter"
class="org.springframework.security.saml.metadata.MetadataGeneratorFilter">
<constructor-arg>
<bean class="org.springframework.security.saml.metadata.MetadataGenerator">
<property name="extendedMetadata">
<bean class="org.springframework.security.saml.metadata.ExtendedMetadata">
<property name="idpDiscoveryEnabled" value="false" />
</bean>
</property>
</bean>
</constructor-arg>
</bean>- Add the "entityBaseURL" property:
<!-- Filter automatically generates default SP metadata -->
<bean id="metadataGeneratorFilter"
class="org.springframework.security.saml.metadata.MetadataGeneratorFilter">
<constructor-arg>
<bean class="org.springframework.security.saml.metadata.MetadataGenerator">
<property name="extendedMetadata">
<bean class="org.springframework.security.saml.metadata.ExtendedMetadata">
<property name="idpDiscoveryEnabled" value="false" />
</bean>
</property>
<property name="entityBaseURL" value="https://<BOE_SERVER_NAME>/sap/boc/ina"/>
</bean>
</constructor-arg>
</bean>- Locate the last section of code that needs updating:
<!-- Provider of default SAML Context -->
<bean id="contextProvider"
class="org.springframework.security.saml.context.SAMLContextProviderImpl" />- Update the code to explicitly state server name and path to BOE Live Data Connect URL:
<!-- Provider of default SAML Context -->
<!--<bean id="contextProvider"
class="org.springframework.security.saml.context.SAMLContextProviderImpl" /> -->
<bean id="contextProvider" class="org.springframework.security.saml.context.SAMLContextProviderLB">
<property name="scheme" value="https"/>
<property name="serverName" value="<BOE_SERVER_NAME"/>
<property name="serverPort" value="443"/>
<property name="includeServerPortInRequestURL" value="false"/>
<property name="contextPath" value="/sap/boc/ina"/>
</bean>- Save and Close the securityContext.xml file
- Restart Apache Tomcat
Step 8: Azure – Upload Metadata to Azure from BOE Live Data Connect
We are nearly there! The next step is to upload the metadata file from BOE Live Data Connect into Azure
- Open your web browser go to the URL: https://<BOE_SERVERNAME>/sap/boc/ina/saml/metadata
- You will be prompted to save a file called spring_saml_metadata.xml. Just save it to a local folder on your PC/Laptop
- Login to Azure Portal (https://portal.azure.com) and click “Azure Active Directory”

- Click "Enterprise Applications"

- Click "SAP BOE Live DC"

- Click "Single Sign-on"

- Click "Upload metadata file" and then locate the spring_saml_metadata.xml file you downloaded earlier. Then click "Add"

- You will now see the URLs for your BOE Live Data Connect application. Check that the URL has the right servername prefixed with https. It should look like this:

Step 9: Azure – Passing the correct User ID to SAP BI
In order for SSO to work you have get Azure to pass an ID which is matches the account name field in SAP BI 4.2. In my case I am going with email address but it is likely you will want to pass a standard Windows AD username. I would suggest working with your AD administrator on what ID to pass. Users using BOE Live Data Connect must have an Enterprise alias assigned to their account as well if they had been created from Windows AD.

The steps I will go through are setting up email address as the ID:
- Login to Azure Portal (https://portal.azure.com) and click “Azure Active Directory”

- Click "Enterprise Applications"

- Click "SAP BOE Live DC"

- Under User Attributes & Claims, click the edit icon

- Click "Unique User Identifier (Name ID)"

- Change Source attribtute to user.mail and then click save

Step 10: SAC - Update Connection to use SAML
For these steps, it is assumed that you already have a Live Universe connection that you are updating to work using SAML SSO. You can create brand new connections using SAML SSO as well.
- Login to SAP Analytics Cloud Tenant as the user with privileges to edit connections
- Click on Menu > Connections

- Select the connection you wish to edit, "UNX Live" in my example, and then click the edit icon.

- Change the Authentication Method to "SAML Single Sign On."

- Click Save. If successful, your connection will Save.
Following this step you have now completed all the technical aspects of setting up SSO to Universes from SAP Analytics Cloud.
User Management
Following the setup make sure you do the following:
- Make sure that in Azure AD that you have added users and groups to "SAP BOE Live DC" application. (The users have been added to SAP Analytics Cloud).
- Users have been setup in SAP BI 4.2 either as just Enterprise authenticated users or users have Enterprise aliases added. Enterprise is needed as Trusted Authentication is used.
- Users in SAP BI 4.2 have create query and data refresh access to relevant Universes and Connections.
- On user PCs, make sure pop ups are allowed from your SAC Tenant URL. A popup windows appears briefly to perform the authentication.
Troubleshooting
Troubleshooting was a bit more tricky compared to setting up SAML SSO into SAC. The Google Chrome SAML Panel I used before was of no use as BOE Live Data Connect performs SAML SSO in a popup window. So the way I view what was happening with SAML was to use Firefox and SAML Tracer addon. The SAML Tracer addon logs all activity in any Firefox Window. Below is a screenshot example of the tool in action.

SAP BI Sessions
One thing I have noticed with using BOE Live Data Connect is that when a user retrieves data for a story that 2 sessions are generated in SAP BI 4.2. So be careful if your users are using Concurrent Session Based Licesing, CSBLs, in SAP BI 4.2.

Conclusion
You should now have full SSO into SAP BI 4.2 Universes after following this guide. This will certainly make your users happy not having to logon twice to get their analytics.
I hope you find this guide useful. I really enjoyed researching and writing this guide and hope to write more technical blog posts in the future.
Andrew
3 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
"automatische backups"
1 -
"regelmäßige sicherung"
1 -
"TypeScript" "Development" "FeedBack"
1 -
505 Technology Updates 53
1 -
ABAP
14 -
ABAP API
1 -
ABAP CDS Views
2 -
ABAP CDS Views - BW Extraction
1 -
ABAP CDS Views - CDC (Change Data Capture)
1 -
ABAP class
2 -
ABAP Cloud
2 -
ABAP Development
5 -
ABAP in Eclipse
1 -
ABAP Platform Trial
1 -
ABAP Programming
2 -
abap technical
1 -
absl
2 -
access data from SAP Datasphere directly from Snowflake
1 -
Access data from SAP datasphere to Qliksense
1 -
Accrual
1 -
action
1 -
adapter modules
1 -
Addon
1 -
Adobe Document Services
1 -
ADS
1 -
ADS Config
1 -
ADS with ABAP
1 -
ADS with Java
1 -
ADT
2 -
Advance Shipping and Receiving
1 -
Advanced Event Mesh
3 -
AEM
1 -
AI
7 -
AI Launchpad
1 -
AI Projects
1 -
AIML
9 -
Alert in Sap analytical cloud
1 -
Amazon S3
1 -
Analytical Dataset
1 -
Analytical Model
1 -
Analytics
1 -
Analyze Workload Data
1 -
annotations
1 -
API
1 -
API and Integration
3 -
API Call
2 -
Application Architecture
1 -
Application Development
5 -
Application Development for SAP HANA Cloud
3 -
Applications and Business Processes (AP)
1 -
Artificial Intelligence
1 -
Artificial Intelligence (AI)
5 -
Artificial Intelligence (AI) 1 Business Trends 363 Business Trends 8 Digital Transformation with Cloud ERP (DT) 1 Event Information 462 Event Information 15 Expert Insights 114 Expert Insights 76 Life at SAP 418 Life at SAP 1 Product Updates 4
1 -
Artificial Intelligence (AI) blockchain Data & Analytics
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise Oil Gas IoT Exploration Production
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise sustainability responsibility esg social compliance cybersecurity risk
1 -
ASE
1 -
ASR
2 -
ASUG
1 -
Attachments
1 -
Authorisations
1 -
Automating Processes
1 -
Automation
2 -
aws
2 -
Azure
1 -
Azure AI Studio
1 -
B2B Integration
1 -
Backorder Processing
1 -
Backup
1 -
Backup and Recovery
1 -
Backup schedule
1 -
BADI_MATERIAL_CHECK error message
1 -
Bank
1 -
BAS
1 -
basis
2 -
Basis Monitoring & Tcodes with Key notes
2 -
Batch Management
1 -
BDC
1 -
Best Practice
1 -
bitcoin
1 -
Blockchain
3 -
bodl
1 -
BOP in aATP
1 -
BOP Segments
1 -
BOP Strategies
1 -
BOP Variant
1 -
BPC
1 -
BPC LIVE
1 -
BTP
12 -
BTP Destination
2 -
Business AI
1 -
Business and IT Integration
1 -
Business application stu
1 -
Business Application Studio
1 -
Business Architecture
1 -
Business Communication Services
1 -
Business Continuity
1 -
Business Data Fabric
3 -
Business Partner
12 -
Business Partner Master Data
10 -
Business Technology Platform
2 -
Business Trends
4 -
CA
1 -
calculation view
1 -
CAP
3 -
Capgemini
1 -
CAPM
1 -
Catalyst for Efficiency: Revolutionizing SAP Integration Suite with Artificial Intelligence (AI) and
1 -
CCMS
2 -
CDQ
12 -
CDS
2 -
Cental Finance
1 -
Certificates
1 -
CFL
1 -
Change Management
1 -
chatbot
1 -
chatgpt
3 -
CL_SALV_TABLE
2 -
Class Runner
1 -
Classrunner
1 -
Cloud ALM Monitoring
1 -
Cloud ALM Operations
1 -
cloud connector
1 -
Cloud Extensibility
1 -
Cloud Foundry
4 -
Cloud Integration
6 -
Cloud Platform Integration
2 -
cloudalm
1 -
communication
1 -
Compensation Information Management
1 -
Compensation Management
1 -
Compliance
1 -
Compound Employee API
1 -
Configuration
1 -
Connectors
1 -
Consolidation Extension for SAP Analytics Cloud
2 -
Control Indicators.
1 -
Controller-Service-Repository pattern
1 -
Conversion
1 -
Cosine similarity
1 -
cryptocurrency
1 -
CSI
1 -
ctms
1 -
Custom chatbot
3 -
Custom Destination Service
1 -
custom fields
1 -
Customer Experience
1 -
Customer Journey
1 -
Customizing
1 -
cyber security
3 -
Data
1 -
Data & Analytics
1 -
Data Aging
1 -
Data Analytics
2 -
Data and Analytics (DA)
1 -
Data Archiving
1 -
Data Back-up
1 -
Data Governance
5 -
Data Integration
2 -
Data Quality
12 -
Data Quality Management
12 -
Data Synchronization
1 -
data transfer
1 -
Data Unleashed
1 -
Data Value
8 -
database tables
1 -
Datasphere
2 -
datenbanksicherung
1 -
dba cockpit
1 -
dbacockpit
1 -
Debugging
2 -
Delimiting Pay Components
1 -
Delta Integrations
1 -
Destination
3 -
Destination Service
1 -
Developer extensibility
1 -
Developing with SAP Integration Suite
1 -
Devops
1 -
digital transformation
1 -
Documentation
1 -
Dot Product
1 -
DQM
1 -
dump database
1 -
dump transaction
1 -
e-Invoice
1 -
E4H Conversion
1 -
Eclipse ADT ABAP Development Tools
2 -
edoc
1 -
edocument
1 -
ELA
1 -
Embedded Consolidation
1 -
Embedding
1 -
Embeddings
1 -
Employee Central
1 -
Employee Central Payroll
1 -
Employee Central Time Off
1 -
Employee Information
1 -
Employee Rehires
1 -
Enable Now
1 -
Enable now manager
1 -
endpoint
1 -
Enhancement Request
1 -
Enterprise Architecture
1 -
ETL Business Analytics with SAP Signavio
1 -
Euclidean distance
1 -
Event Dates
1 -
Event Driven Architecture
1 -
Event Mesh
2 -
Event Reason
1 -
EventBasedIntegration
1 -
EWM
1 -
EWM Outbound configuration
1 -
EWM-TM-Integration
1 -
Existing Event Changes
1 -
Expand
1 -
Expert
2 -
Expert Insights
2 -
Fiori
14 -
Fiori Elements
2 -
Fiori SAPUI5
12 -
Flask
1 -
Full Stack
8 -
Funds Management
1 -
General
1 -
Generative AI
1 -
Getting Started
1 -
GitHub
8 -
Grants Management
1 -
groovy
1 -
GTP
1 -
HANA
6 -
HANA Cloud
2 -
Hana Cloud Database Integration
2 -
HANA DB
2 -
HANA XS Advanced
1 -
Historical Events
1 -
home labs
1 -
HowTo
1 -
HR Data Management
1 -
html5
8 -
HTML5 Application
1 -
Identity cards validation
1 -
idm
1 -
Implementation
1 -
input parameter
1 -
instant payments
1 -
Integration
3 -
Integration Advisor
1 -
Integration Architecture
1 -
Integration Center
1 -
Integration Suite
1 -
intelligent enterprise
1 -
iot
1 -
Java
1 -
job
1 -
Job Information Changes
1 -
Job-Related Events
1 -
Job_Event_Information
1 -
joule
4 -
Journal Entries
1 -
Just Ask
1 -
Kerberos for ABAP
8 -
Kerberos for JAVA
8 -
KNN
1 -
Launch Wizard
1 -
learning content
2 -
Life at SAP
4 -
lightning
1 -
Linear Regression SAP HANA Cloud
1 -
local tax regulations
1 -
LP
1 -
Machine Learning
2 -
Marketing
1 -
Master Data
3 -
Master Data Management
14 -
Maxdb
2 -
MDG
1 -
MDGM
1 -
MDM
1 -
Message box.
1 -
Messages on RF Device
1 -
Microservices Architecture
1 -
Microsoft Universal Print
1 -
Middleware Solutions
1 -
Migration
5 -
ML Model Development
1 -
Modeling in SAP HANA Cloud
8 -
Monitoring
3 -
MTA
1 -
Multi-Record Scenarios
1 -
Multiple Event Triggers
1 -
Neo
1 -
New Event Creation
1 -
New Feature
1 -
Newcomer
1 -
NodeJS
2 -
ODATA
2 -
OData APIs
1 -
odatav2
1 -
ODATAV4
1 -
ODBC
1 -
ODBC Connection
1 -
Onpremise
1 -
open source
2 -
OpenAI API
1 -
Oracle
1 -
PaPM
1 -
PaPM Dynamic Data Copy through Writer function
1 -
PaPM Remote Call
1 -
PAS-C01
1 -
Pay Component Management
1 -
PGP
1 -
Pickle
1 -
PLANNING ARCHITECTURE
1 -
Popup in Sap analytical cloud
1 -
PostgrSQL
1 -
POSTMAN
1 -
Process Automation
2 -
Product Updates
4 -
PSM
1 -
Public Cloud
1 -
Python
4 -
Qlik
1 -
Qualtrics
1 -
RAP
3 -
RAP BO
2 -
Record Deletion
1 -
Recovery
1 -
recurring payments
1 -
redeply
1 -
Release
1 -
Remote Consumption Model
1 -
Replication Flows
1 -
research
1 -
Resilience
1 -
REST
1 -
REST API
1 -
Retagging Required
1 -
Risk
1 -
Rolling Kernel Switch
1 -
route
1 -
rules
1 -
S4 HANA
1 -
S4 HANA Cloud
1 -
S4 HANA On-Premise
1 -
S4HANA
3 -
S4HANA_OP_2023
2 -
SAC
10 -
SAC PLANNING
9 -
SAP
4 -
SAP ABAP
1 -
SAP Advanced Event Mesh
1 -
SAP AI Core
8 -
SAP AI Launchpad
8 -
SAP Analytic Cloud Compass
1 -
Sap Analytical Cloud
1 -
SAP Analytics Cloud
4 -
SAP Analytics Cloud for Consolidation
3 -
SAP Analytics Cloud Story
1 -
SAP analytics clouds
1 -
SAP BAS
1 -
SAP Basis
6 -
SAP BODS
1 -
SAP BODS certification.
1 -
SAP BTP
21 -
SAP BTP Build Work Zone
2 -
SAP BTP Cloud Foundry
6 -
SAP BTP Costing
1 -
SAP BTP CTMS
1 -
SAP BTP Innovation
1 -
SAP BTP Migration Tool
1 -
SAP BTP SDK IOS
1 -
SAP Build
11 -
SAP Build App
1 -
SAP Build apps
1 -
SAP Build CodeJam
1 -
SAP Build Process Automation
3 -
SAP Build work zone
10 -
SAP Business Objects Platform
1 -
SAP Business Technology
2 -
SAP Business Technology Platform (XP)
1 -
sap bw
1 -
SAP CAP
2 -
SAP CDC
1 -
SAP CDP
1 -
SAP CDS VIEW
1 -
SAP Certification
1 -
SAP Cloud ALM
4 -
SAP Cloud Application Programming Model
1 -
SAP Cloud Integration for Data Services
1 -
SAP cloud platform
8 -
SAP Companion
1 -
SAP CPI
3 -
SAP CPI (Cloud Platform Integration)
2 -
SAP CPI Discover tab
1 -
sap credential store
1 -
SAP Customer Data Cloud
1 -
SAP Customer Data Platform
1 -
SAP Data Intelligence
1 -
SAP Data Migration in Retail Industry
1 -
SAP Data Services
1 -
SAP DATABASE
1 -
SAP Dataspher to Non SAP BI tools
1 -
SAP Datasphere
10 -
SAP DRC
1 -
SAP EWM
1 -
SAP Fiori
2 -
SAP Fiori App Embedding
1 -
Sap Fiori Extension Project Using BAS
1 -
SAP GRC
1 -
SAP HANA
1 -
SAP HCM (Human Capital Management)
1 -
SAP HR Solutions
1 -
SAP IDM
1 -
SAP Integration Suite
9 -
SAP Integrations
4 -
SAP iRPA
2 -
SAP Learning Class
1 -
SAP Learning Hub
1 -
SAP Odata
2 -
SAP on Azure
1 -
SAP PartnerEdge
1 -
sap partners
1 -
SAP Password Reset
1 -
SAP PO Migration
1 -
SAP Prepackaged Content
1 -
SAP Process Automation
2 -
SAP Process Integration
2 -
SAP Process Orchestration
1 -
SAP S4HANA
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Cloud for Finance
1 -
SAP S4HANA Cloud private edition
1 -
SAP Sandbox
1 -
SAP STMS
1 -
SAP successfactors
3 -
SAP SuccessFactors HXM Core
1 -
SAP Time
1 -
SAP TM
2 -
SAP Trading Partner Management
1 -
SAP UI5
1 -
SAP Upgrade
1 -
SAP Utilities
1 -
SAP-GUI
8 -
SAP_COM_0276
1 -
SAPBTP
1 -
SAPCPI
1 -
SAPEWM
1 -
sapmentors
1 -
saponaws
2 -
SAPS4HANA
1 -
SAPUI5
4 -
schedule
1 -
Secure Login Client Setup
8 -
security
9 -
Selenium Testing
1 -
SEN
1 -
SEN Manager
1 -
service
1 -
SET_CELL_TYPE
1 -
SET_CELL_TYPE_COLUMN
1 -
SFTP scenario
2 -
Simplex
1 -
Single Sign On
8 -
Singlesource
1 -
SKLearn
1 -
soap
1 -
Software Development
1 -
SOLMAN
1 -
solman 7.2
2 -
Solution Manager
3 -
sp_dumpdb
1 -
sp_dumptrans
1 -
SQL
1 -
sql script
1 -
SSL
8 -
SSO
8 -
Substring function
1 -
SuccessFactors
1 -
SuccessFactors Platform
1 -
SuccessFactors Time Tracking
1 -
Sybase
1 -
system copy method
1 -
System owner
1 -
Table splitting
1 -
Tax Integration
1 -
Technical article
1 -
Technical articles
1 -
Technology Updates
14 -
Technology Updates
1 -
Technology_Updates
1 -
terraform
1 -
Threats
1 -
Time Collectors
1 -
Time Off
2 -
Time Sheet
1 -
Time Sheet SAP SuccessFactors Time Tracking
1 -
Tips and tricks
2 -
toggle button
1 -
Tools
1 -
Trainings & Certifications
1 -
Transport in SAP BODS
1 -
Transport Management
1 -
TypeScript
2 -
ui designer
1 -
unbind
1 -
Unified Customer Profile
1 -
UPB
1 -
Use of Parameters for Data Copy in PaPM
1 -
User Unlock
1 -
VA02
1 -
Validations
1 -
Vector Database
2 -
Vector Engine
1 -
Visual Studio Code
1 -
VSCode
1 -
Web SDK
1 -
work zone
1 -
workload
1 -
xsa
1 -
XSA Refresh
1
- « Previous
- Next »
Related Content
- SAP Analytics Cloud, add-in for Microsoft Excel and SAP Datasphere connection in Technology Blogs by SAP
- 体验更丝滑!SAP 分析云 2024.07 版功能更新 in Technology Blogs by SAP
- I cannot cancel an import in SAP Analytics Cloud from SAP Hana. in Technology Q&A
- What’s New in SAP Analytics Cloud Release 2024.08 in Technology Blogs by SAP
- CDS View: Hierarchy node sign reversal in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 13 | |
| 11 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 3 |
