
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Part 5: Configuring JWT token verification flows f...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
divyamary
Contributor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
09-05-2019
1:05 AM
The JWT policies of SAP Cloud Platform API Management enables you to generate, verify and decode the JWT token. In the Blog Series : JSON Web Tokens (JWT) verification using SAP Cloud Platform API Management we have covered the modeling and configuration of JWT verification policies for various Identity providers like SAP Cloud Platform XS UAA, Okta , Azure Active Directory .
SAP Customer Data Cloud (Gigya) securely identifies consumers across devices and channels, manages permissions and consent across entire lifecycles and transforms data into unified customer profiles. SAP Customer Data Data Cloud supports JWT token based authentication. In this part of the blog series, we have covered the steps for Configuring the JWT token verification policy for SAP Customer Data Cloud ( Gigya).
https://{datacenter_of_your_registered_site}/accounts.getJWTPublicKey?apiKey={your_site_api_key}&V2=true









Refer Blog Series : JSON Web Tokens (JWT) verification using SAP Cloud Platform API Management for more blogs on JWT verification policies.
SAP Customer Data Cloud (Gigya) securely identifies consumers across devices and channels, manages permissions and consent across entire lifecycles and transforms data into unified customer profiles. SAP Customer Data Data Cloud supports JWT token based authentication. In this part of the blog series, we have covered the steps for Configuring the JWT token verification policy for SAP Customer Data Cloud ( Gigya).
Pre-requisite
- Part 1: Modeling the JWT token verification flows in SAP Cloud Platform API Management
- Setup completed in your SAP Customer Data Cloud account as covered in Registration as a Service ( RaaS) guide and Site Setup guide.
Configuration on your SAP Customer Data Cloud account
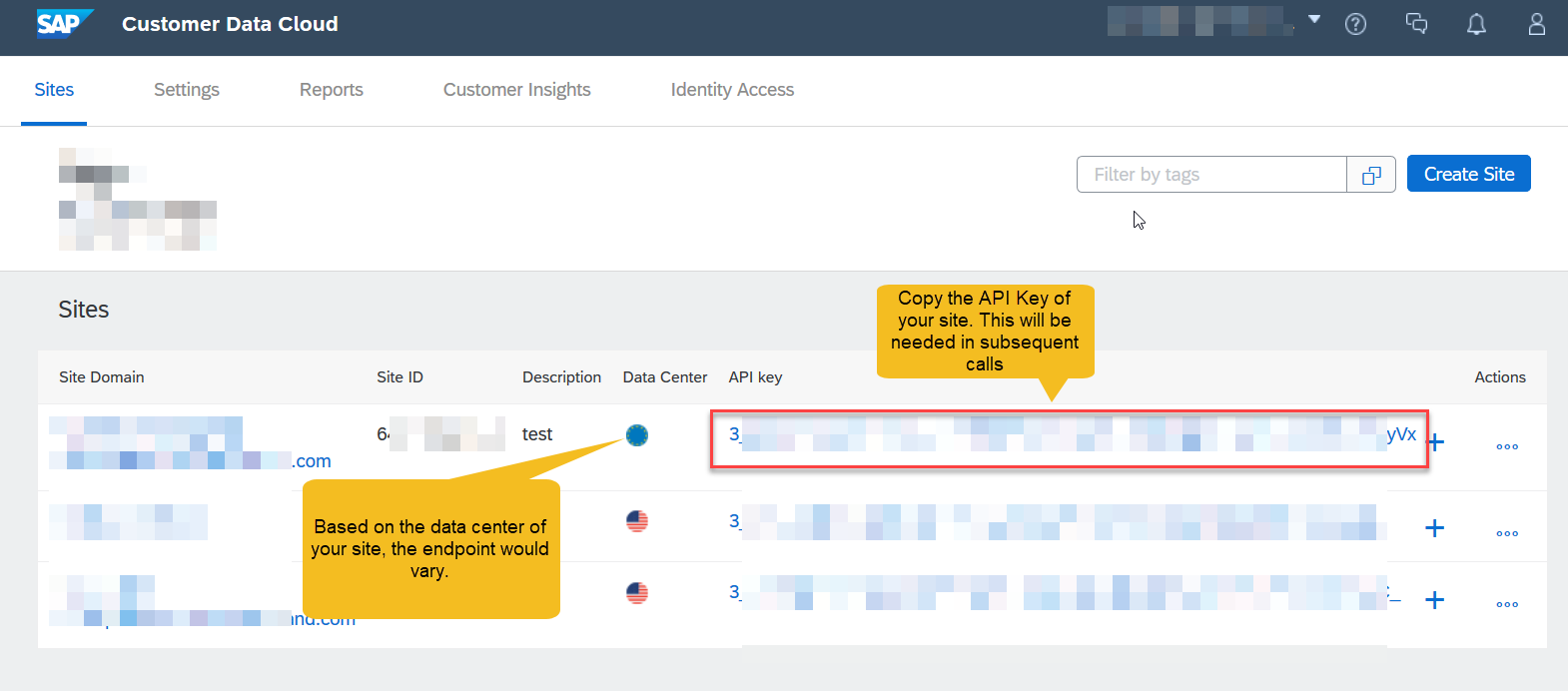
- Logon to your SAP Customer Data Cloud account and navigate to the sites page.
- Note down your API key of the site configured on your SAP Customer Data Cloud account. Take a note of the data center of your site. The endpoint of the SAP Customer Data Cloud APIs would vary based on the data center. Refer the guide on finding your data center for more details.

- accounts.getJWTPublicKey REST API returns the JWKS keys information that is used in signing of the id_token returned from accounts.getJWT API endpoint. As a public endpoint, this API requires no parameters, including a secret or userKey/secret pair, and only the API key of the site is required. accounts.getJWTPublicKey REST API endpoint would be the JWKS_URL that can be used in the SAP Cloud Platform API Management policies.
- Construct your accounts.getJWTPublicKey endpoint based on your site data centers and the API Key of your site by replacing the placeholder {datacenter_of_your_registered_site} and {your_site_api_key}
https://{datacenter_of_your_registered_site}/accounts.getJWTPublicKey?apiKey={your_site_api_key}&V2=true
- Construct your JWT issuer by replacing {your_site_api_key} with API Key value of the site copied in the previous steps https://fidm.gigya.com/jwt/{your_site_api_key}/
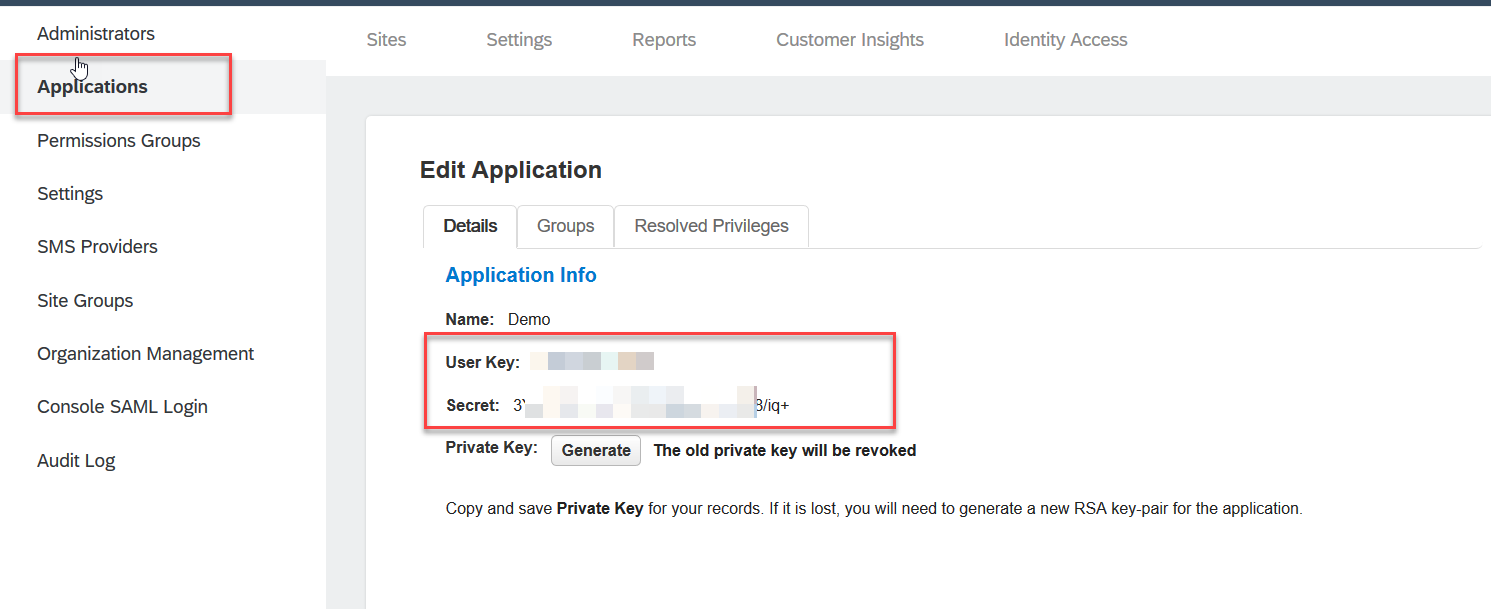
- For getting the JWT token from SAP Customer Data Cloud account, you will also need to create an application for your site and get your own user key and secret. Navigate to Admin center and select your application and copy your User key and Secret of your applications.

Configure OAuth Issuer and JWKS URI in SAP Cloud Platform API Management
- Navigate to API Portal service of your SAP Cloud Platform API Management.
- Navigate to Develop tab and select the API Proxy to you have modeled the JWT token verification policies. Refer part 1 of this blog series to model the JWT verification policies for your API Proxy.

- From the selected API Proxy details view, click Policies to open Policy Designer.

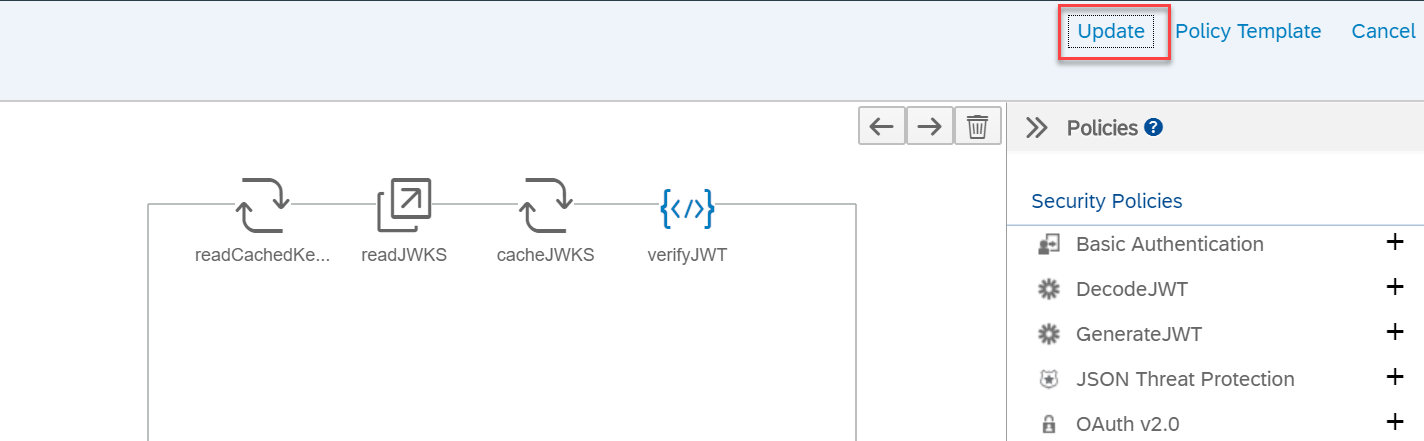
- Click Edit on the policy designer, to enter edit mode.

- Select the policy readJWKS policy and replace the URL element with the JWKS_URL constructed in the previous section.

- Select the policy verifyJWT policy and replace the URL element with the issuer constructed in the previous section.

- Select Update to persist all the policy changes.

- Click Save to persist all the API Proxy changes.

Finally testing the JWT token verification flows
- accounts.getJWT REST API can be used to obtain the id_token containing the users's data in JWT format. For the getJWT REST call, API Key of your site, your user key and secret that you had copied from your SAP Customer Data Cloud account is required. You will also need the UID of the users's who are registered for your site. Steps to register users to your SAP Customer Data Cloud site is covered in this help documentation.
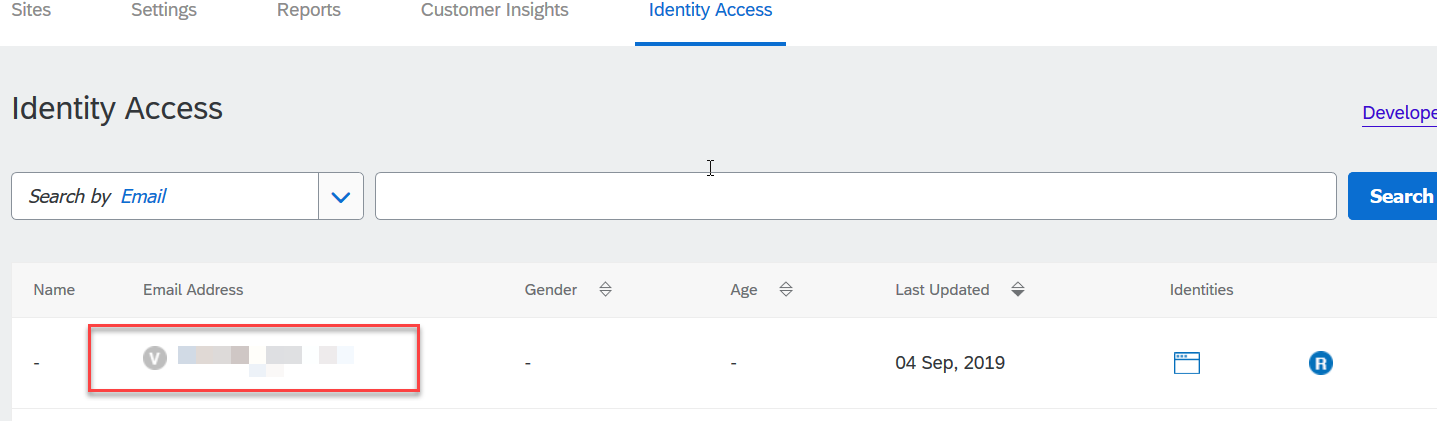
- To get the UID of registered user, select your registered site in SAP Customer Data Cloud account and navigate to the Identity Access tab.

- Select the users, which you would like to use for your testing.

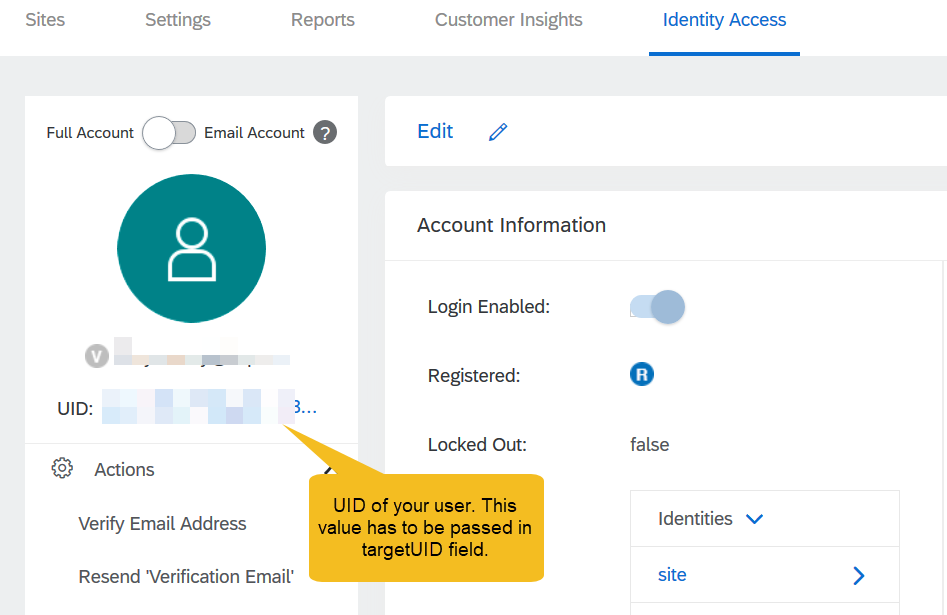
- From the details view of registered user, you would be able copy the UID value.

- Use the API Key of your site, user key, secret and UID of your registered user to get a JWT access token by calling accounts.getJWT REST API. Details is covered in this documentation.
- Call your API Proxy endpoint passing in your OAuth access token, received in id_token field of the accounts.getJWT REST API response, in a HTTP header named authorization in the format Bearer {oauth_access_token}.
- In case of successful JWT token validation, the response from your target server would be returned.

- Passing invalid access token or an empty access token will result in error with HTTP status code set to 401.

Refer Blog Series : JSON Web Tokens (JWT) verification using SAP Cloud Platform API Management for more blogs on JWT verification policies.
- SAP Managed Tags:
- SAP BTP Security,
- API Management,
- SAP Customer Data Cloud,
- Security,
- SAP Business Technology Platform
Labels:
1 Comment
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
87 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
64 -
Expert
1 -
Expert Insights
178 -
Expert Insights
270 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
11 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,578 -
Product Updates
323 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
396 -
Workload Fluctuations
1
Related Content
- SAP Document and Reporting Compliance - 'Colombia' - Contingency Process in Technology Blogs by SAP
- explore the business continuity recovery sap solutions on AWS DRS in Technology Blogs by Members
- SAP SABRIX UPGRADE in Technology Blogs by Members
- Cloud Integration: Manually Sign / Verify XML payload based on XML Signature Standard in Technology Blogs by SAP
- SAP Cloud Integration: Understanding the XML Digital Signature Standard in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 11 | |
| 10 | |
| 10 | |
| 9 | |
| 8 | |
| 7 | |
| 7 | |
| 7 | |
| 7 | |
| 6 |