
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- SAML Integration between SAP Netweaver AS ABAP and...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
former_member45
Contributor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
08-05-2019
10:05 AM
This blog describes implementing a single sign on mechanism with SAML between Active Directory Federation Services and SAP Netweaver AS ABAP
In summary, the configuration provided in this document have been executed on the below mentioned platform versions.
Before we run into the configuration make sure you have HTTPS enabled for your gateway system and certificates are signed

Activate secure session management to enable SAML 2.0 on the client server
To activate the security session management, perform the following steps.
Ensure to activate the following services in the transaction SICF
/default_host/sap/bc/webdynpro/sap/saml2
From the ADFS, you can export the metadata file to build a secure trust with the relying party.
Download metadata file from your ADFS server using the following URL
https://<hostname FQDN>/FederationMetadata/2007-06/FederationMetadata.xml
To configure SAML 2.0 for specific client, perform the following steps
Goto transaction SAML2 and select Enable SAML 2.0 support

Add provider name and click next
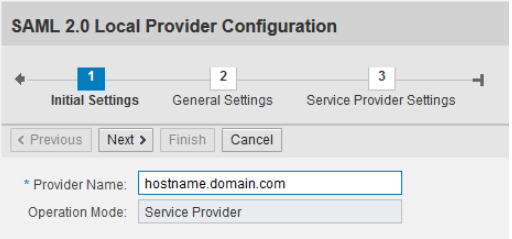
Continue with default option in General settings screen
In Service Provider settings choose Automatic for Selection Mode

Select Finish
Select Edit ---> Include Certificate in Signature to establish connection between SAP Netweaver AS ABAP and Microsoft ADFS

Select Metadata to export metadata

Save a copy of metadata to share this information with the identity provider
In the Service Provider settings tab, you can view the configuration details
To import the metadata file of identity provider, perform the following steps
This section provides information on how to configure SAML on Microsoft Active Directory Federation Services (ADFS).
Prerequisite - ADFS is successfully installed and configured
Add a Relying Party Trust
Open ADFS Management Tool, navigate to Trusted Relationship ---> Relying Party Trusts ---> Add Relying Party Trust

Click Start
Select Import Data about the relying party from a file and select Browse to navigate to ABAP metadata file

Click on Next
Click Ok
Provide Name
Select Next
Select Permit all users to access the relying party and select Next

Select Next and go with the default screen
Select Close
Select Add Rule
Click Next

On the Configure Rule screen, perform the following steps
Under LDAP Attribute, select SAM-Account-Name
Under Outgoing Claim Types, select Name ID

Select Relying Party Trust ---> Properties
Goto Advanced tab and change Secure Hash Algorithm to SHA-1
Note – Match this with what you selected on your ABAP system

Exporting ADFS Token Signing Certificate
Open ADFS Management tool
Navigate to Service ---> Certificates
On the right-hand panel, under the Token-signing, double click on the Certificate.

On the Certificate window, select Details tab.
Select Copy to File and Select Next
Select Base-64 encoded X.509 (.CER).
Subsequently select Next to export the certificate.
This section provides information on how to enable SAML on of the services.
To enable SAP Netweaver server to perform user authentication using SAML, perform the following steps
On executing Gateway service, the client will be redirected to the logon screen of the external SAML 2.0 IdP server.
Note: To test the service, edit the following link with server details –
https://<FQDN>:<port>/sap/opu/odata/iwfnd/catalogservice/?sap-client=<client no>&$format=xml
https://blogs.sap.com/2018/02/28/saml-integration-between-microsoft-azure-portal-and-sap-analytics-c...
https://blogs.sap.com/2017/12/19/sap-analytics-cloud-saml-sso-using-adfs-active-directory-federation...
https://blogs.sap.com/2018/02/22/adfs-with-sap-business-intelligence-platform/
https://blogs.sap.com/2018/03/01/saml-integration-between-microsoft-azure-portal-and-sap-business-in...
In summary, the configuration provided in this document have been executed on the below mentioned platform versions.
- Microsoft ADFS (Windows Server 2012 R2) as Identity Provider
- SAP Netweaver AS ABAP 7.50 SP10 as Service Provider
1. HTTPS configuration on ABAP system
Before we run into the configuration make sure you have HTTPS enabled for your gateway system and certificates are signed

2. Activation of SICF
Activate secure session management to enable SAML 2.0 on the client server
To activate the security session management, perform the following steps.
- Goto transaction SICF_SESSIONS
- Choose corresponding client
- Select Activate
Ensure to activate the following services in the transaction SICF
/default_host/sap/bc/webdynpro/sap/saml2
3. Download ADFS server metadata
From the ADFS, you can export the metadata file to build a secure trust with the relying party.
Download metadata file from your ADFS server using the following URL
https://<hostname FQDN>/FederationMetadata/2007-06/FederationMetadata.xml
4. Configuring SAP Netweaver AS ABAP
To configure SAML 2.0 for specific client, perform the following steps
Goto transaction SAML2 and select Enable SAML 2.0 support

Add provider name and click next

Continue with default option in General settings screen
In Service Provider settings choose Automatic for Selection Mode

Select Finish
Select Edit ---> Include Certificate in Signature to establish connection between SAP Netweaver AS ABAP and Microsoft ADFS

Select Metadata to export metadata

Save a copy of metadata to share this information with the identity provider
In the Service Provider settings tab, you can view the configuration details
5. Importing metadata file of identity provider
To import the metadata file of identity provider, perform the following steps
- Select Trusted Providers tab and select Identity Providers in show
- Select Add ---> Upload Metadata File

- On Metadata verification screen, select upload from file

- Select Next
- On Provider name screen, Name field is pre-filled and select Next
- On Signature and Encryption screen, under Artifact profile, select Require Signature Never

- Select Next
- On Single Sign-On Endpoints screen, select Next
- On Single Logout Endpoints screen, select Next
- On Artifact Endpoints screen, select Next
- Select Binding as HTTP Post and select Finish
- Under List of Trusted Providers, select Edit
- Select Identity Federation tab and select Add to Name ID
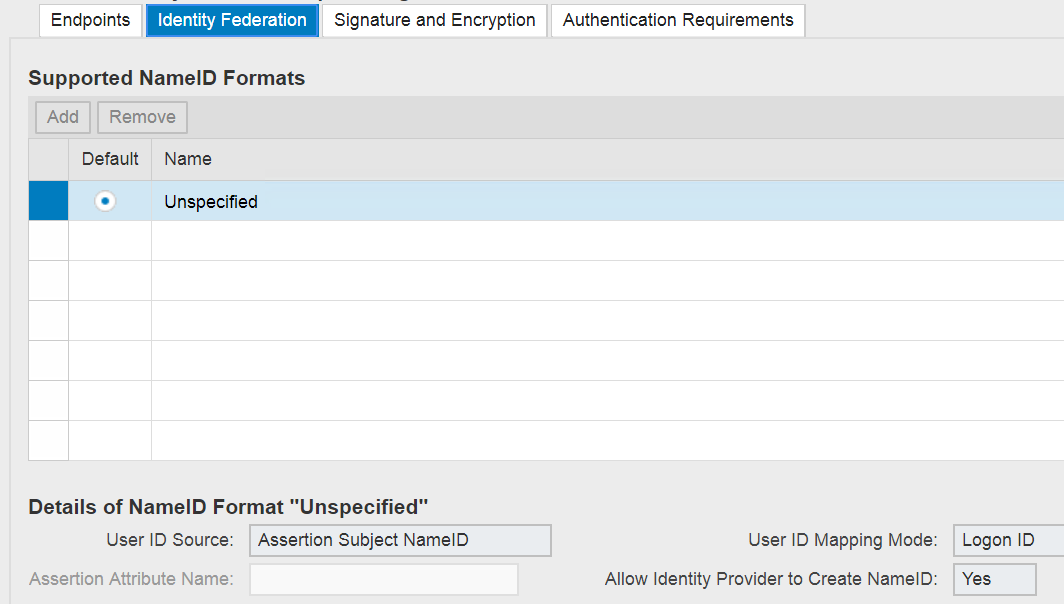
- Select Save
- To enable the Trusted provider, select Enable
6. Configuring ADFS
This section provides information on how to configure SAML on Microsoft Active Directory Federation Services (ADFS).
Prerequisite - ADFS is successfully installed and configured
Add a Relying Party Trust
Open ADFS Management Tool, navigate to Trusted Relationship ---> Relying Party Trusts ---> Add Relying Party Trust

Click Start
Select Import Data about the relying party from a file and select Browse to navigate to ABAP metadata file

Click on Next
Click Ok
Provide Name
Select Next
Select Permit all users to access the relying party and select Next

Select Next and go with the default screen
Select Close
Select Add Rule
Click Next

On the Configure Rule screen, perform the following steps
- In the Claim rule name field, enter Claim Rule name
- Under Attribute store, select Active Directory
- In Mapping of LDAP attribute to outgoing claim types
Under LDAP Attribute, select SAM-Account-Name
Under Outgoing Claim Types, select Name ID
- Select Finish
- Click Apply and Ok

Select Relying Party Trust ---> Properties
Goto Advanced tab and change Secure Hash Algorithm to SHA-1
Note – Match this with what you selected on your ABAP system

Exporting ADFS Token Signing Certificate
Open ADFS Management tool
Navigate to Service ---> Certificates
On the right-hand panel, under the Token-signing, double click on the Certificate.

On the Certificate window, select Details tab.
Select Copy to File and Select Next
Select Base-64 encoded X.509 (.CER).
Subsequently select Next to export the certificate.
7. Enabling SAP Netweaver AS ABAP server to perform User Authentication using SAML
This section provides information on how to enable SAML on of the services.
To enable SAP Netweaver server to perform user authentication using SAML, perform the following steps
- Go to Transaction SICF
- Navigate to sap/opu/odata/iwfnd/catalogservice service and Edit
- Select Logon Data tab and perform the following sub-steps
a. Set Procedure field to Alternate Logon Procedure.
b. Set Security Requirement to SSL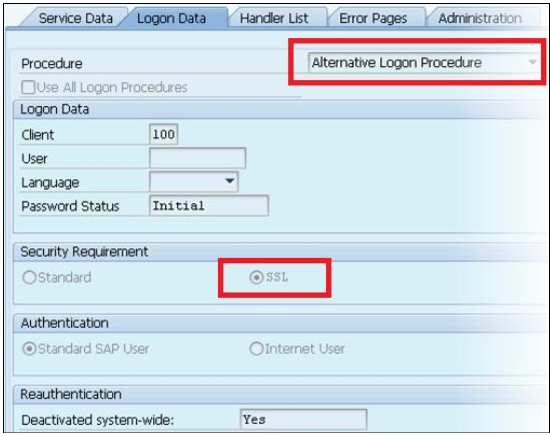 Once the “Alternative Logon Procedure” has been changed, you can scroll down within the Logon Data tab area and you will see a list of Logon Procedures. By default, SAML Logon is item 7 in the list.To change this order, simply overtype the number in the left-hand column with 1 (or 2).
Once the “Alternative Logon Procedure” has been changed, you can scroll down within the Logon Data tab area and you will see a list of Logon Procedures. By default, SAML Logon is item 7 in the list.To change this order, simply overtype the number in the left-hand column with 1 (or 2). - To change this order, in the left-hand No column, overwrite the number. The list is automatically sorted according to the new order, but Logon Through HTTP Fields will always be item one.

- Save your changes.
- Go to Transaction SAML2, on the Trusted Provider tab, select Disable and Enable it again.
8. Verification
On executing Gateway service, the client will be redirected to the logon screen of the external SAML 2.0 IdP server.
Note: To test the service, edit the following link with server details –
https://<FQDN>:<port>/sap/opu/odata/iwfnd/catalogservice/?sap-client=<client no>&$format=xml
Learn More:
https://blogs.sap.com/2018/02/28/saml-integration-between-microsoft-azure-portal-and-sap-analytics-c...
https://blogs.sap.com/2017/12/19/sap-analytics-cloud-saml-sso-using-adfs-active-directory-federation...
https://blogs.sap.com/2018/02/22/adfs-with-sap-business-intelligence-platform/
https://blogs.sap.com/2018/03/01/saml-integration-between-microsoft-azure-portal-and-sap-business-in...
- SAP Managed Tags:
- SAP NetWeaver,
- SAP NetWeaver Application Server for ABAP,
- NW ABAP User Authentication
Labels:
8 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
87 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
64 -
Expert
1 -
Expert Insights
178 -
Expert Insights
273 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
11 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
326 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
403 -
Workload Fluctuations
1
Related Content
- Top Picks: Innovations Highlights from SAP Business Technology Platform (Q1/2024) in Technology Blogs by SAP
- Harnessing the Power of SAP HANA Cloud Vector Engine for Context-Aware LLM Architecture in Technology Blogs by SAP
- Identity Provisioning Documentation Joined the Family of SAP Cloud Identity Services in Technology Blogs by SAP
- Single Sign On to SAP Cloud Integration (CPI runtime) from an external Identity Provider in Technology Blogs by SAP
- Exploring Integration Options in SAP Datasphere with the focus on using SAP extractors in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 12 | |
| 10 | |
| 10 | |
| 7 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 4 |