
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Cloud Integration (CPI) - Authorization Management...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Employee
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
02-27-2019
5:30 PM
SAP Cloud Platform Integration (CPI) is one of the SAP Cloud Platform (SCP) Services. SCP administrators ideally manage CPI - Authorization groups, roles and their assignments to users through SCP Cockpit over web browser.
There is another smart way of performing Authorization Management using SAP Cloud Platform API's.
Usage of SCP - Authorization Management REST API's are not limited to CPI Service but can be extended to other Subscriptions/Services under SCP Sub-accounts. These API's can be used in cases where User Assignment needs to happen in a controlled manner to enforce security policies, audit and compliance from SAP GRC or other User Management & governance products. User Management REST API's are available in SAP Cloud Platform API Documentation but not listed (as of now) on SAP API Business Hub.
Let's get into action and perform authorization management on CPI using REST API's.
Manage Authorizations from SCP Cockpit - Web UI:
SCP > Sub-account > 'Security' > 'Authorizations' > 'Groups' > 'New Group' + Assign 'Roles'/'Users'
Access to SCP Cockpit with Developer/Administrator role to create OAuth - Platform API Client.
SCP > Sub-account > 'Members' > 'Add Members'
Step 1: Create OAuth Platform API Client Credentials - To invoke API's on SCP, OAuth client credentials are required. Client Credentials are specific to SCP Sub-account.
Step 2: Invoke Authorization Management REST API's - Use the Bearer token retrieved from step 1 response and execute the REST method (GET/PUT/POST/DELETE) with respective API operation.
SAP Cloud Platform API's are protected by OAuth 2.0 with grant type - Client Credentials. Follow the below steps to create Platform API Client on SAP Cloud Platform.
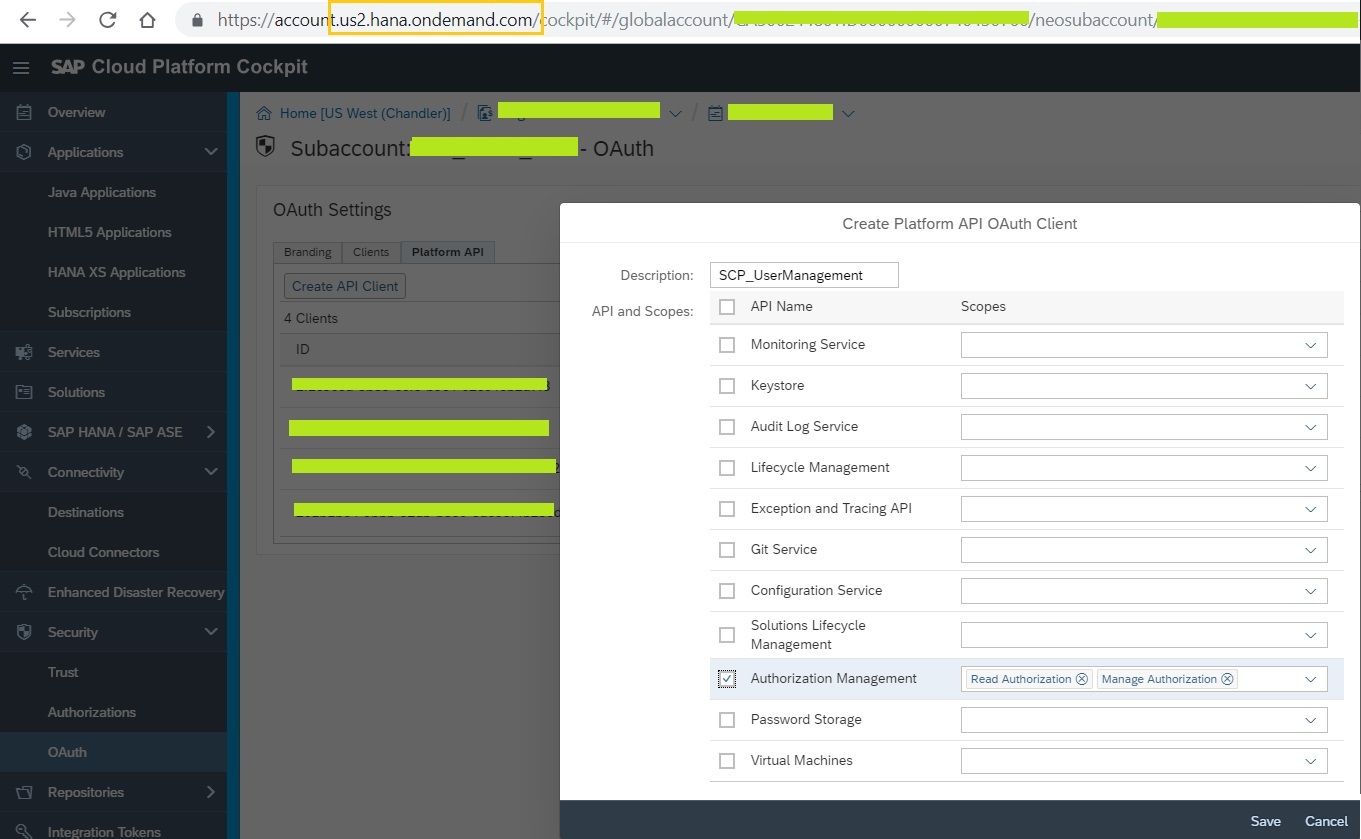
SCP > Sub-account > 'Security' > 'OAuth' > 'Platform API' tab > 'Create API Client'
Give meaningful description to the API Client and select the scope of API's for which this the OAuth Client credentials to be used. For this exercise, let's select the checkbox 'Authorization Management' and click on save. This generates OAuth Client Credentials for consuming Platform API's as in the below snapshot. Note the Client ID & Client Secret. These will serve like User ID & Password to get OAuth token.

Now it's time to call the OAuth endpoint for platform API's and get the token which is valid only for 25 minutes. Let's use postman tool to explore the OAuth Token.
SCP Token Endpoint: https://api.{landscapeHost}/oauth2/apitoken/v1
{landscapeHost} - this is tagged to the region on which SCP is hosted for your account.
For this example, the CPI tenant is running on us2 region (https://lxxxx-tmn.hci.us2.hana.ondemand.com/itspaces/). Accordingly built the below OAuth Token endpoint URL.
Token endpoint URL: https://api.us2.hana.ondemand.com/oauth2/apitoken/v1?grant_type=client_credentials
Select 'Basic Auth' as the Authorization type and pass the OAuth Client Credentials generated earlier as below and execute the OAuth Endpoint URL with POST method.
The response has the Bearer token. We will use this token to execute the Authorization management API's.
API URL extensions vary for each API operation. Refer to detailed API documentation on Authorization Management API's. In this exercise, let's execute some of the operations and know how to interpret API Documentation & execute REST API calls.
API Endpoint URL : https://api.{landscapeHost}/authorization/v1
Examples:
# Get Groups - To retrieve all the existing groups created, use the below API endpoint extension '/accounts/{accountName}/groups'.
Get the accountName of the respective SCP Sub-account under which the CPI tenant linked to & the OAuth client credentials created under.

Resolves into: https://api.us2.hana.ondemand.com/authorization/v1/accounts/test00500/groups
Pass the Bearer token generated in step 1 and execute GET method as below.
# Get Users - To retrieve users under each group, use the below API endpoint extension '/accounts/{accountName}/groups/users'.
Resolves into: https://api.us2.hana.ondemand.com/authorization/v1/accounts/test00500/groups/users?groupName=ZGRP_ServiceAccounts
Pass the Bearer token generated in step 1 and execute GET method as below.
# Get Roles - To retrieve Roles assigned to each group, use the below API endpoint extension '/accounts/{accountName}/groups/roles'.
Resolves into: https://api.us2.hana.ondemand.com/authorization/v1/accounts/test00500/groups/roles?groupName=ZGRP_Administrators
Pass the Bearer token generated in step 1 and execute GET method as below.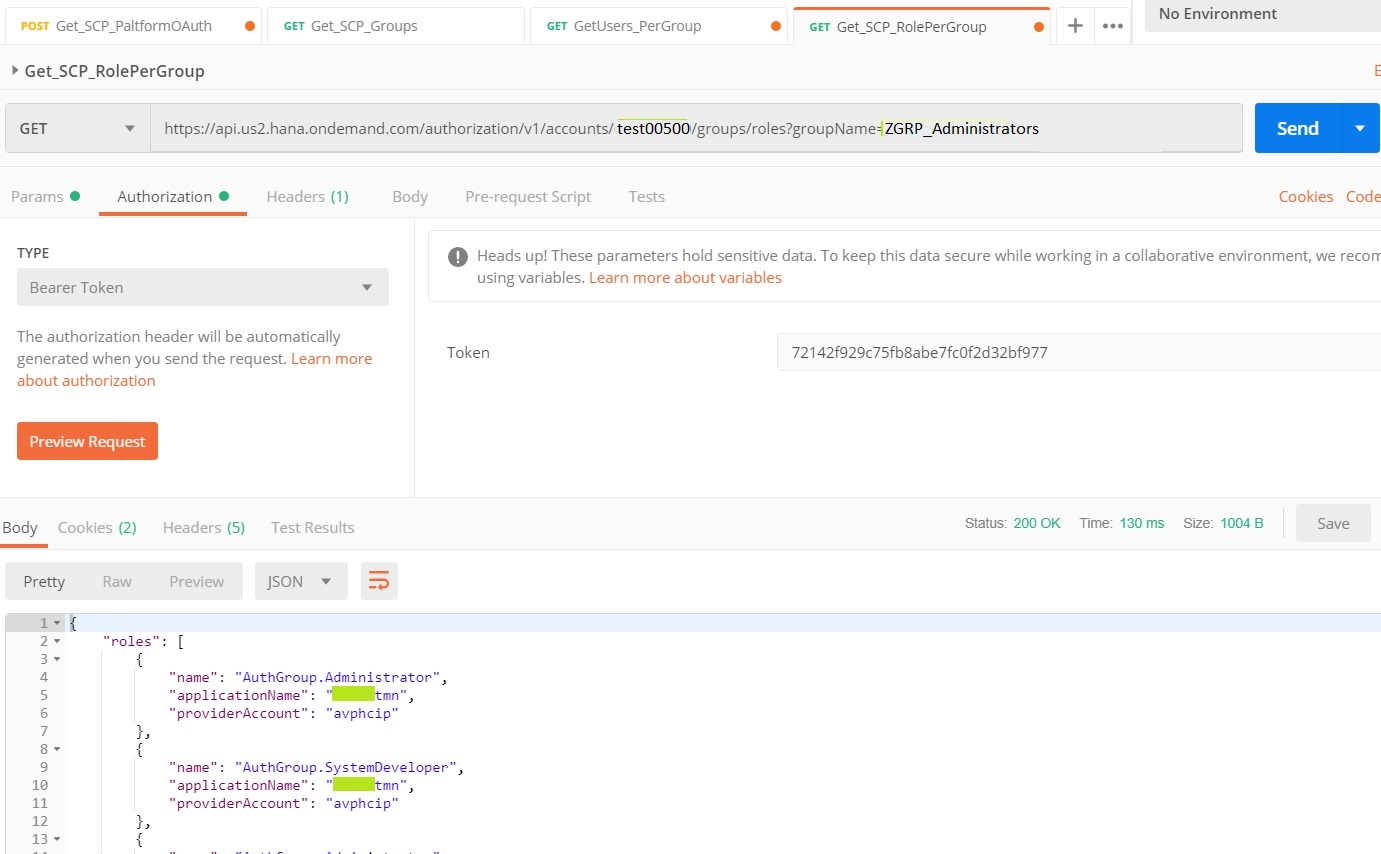
# Add Users - Add users to a particular existing group, use the below API endpoint extension '/accounts/{accountName}/groups/users'.
Resolves into: https://api.us2.hana.ondemand.com/authorization/v1/accounts/test00500/groups/users?groupName=ZGRP_ServiceAccounts
Pass the Bearer token generated in step 1 and execute PUT method as below.
This REST operation added the S-User and can be validated from SCP Cockpit Web UI (shown under the section - 'Manage Authorizations from SCP Cockpit - Web UI').
With this, we know how to interpret the API documentation and execute Authorization Management REST API calls - PUT/GET.
In similar way, other API Operations and the respective methods can be executed by following the Authorization Management API documentation.
With this understanding, we can create integration flows in CPI to manage Authorization groups, roles and users using HTTP adapter to work with these REST Operations. Such i-flows can be consumed by SAP GRC/User Management tools in a controlled manner.
Enjoy exploring API's!
There is another smart way of performing Authorization Management using SAP Cloud Platform API's.
Usage of SCP - Authorization Management REST API's are not limited to CPI Service but can be extended to other Subscriptions/Services under SCP Sub-accounts. These API's can be used in cases where User Assignment needs to happen in a controlled manner to enforce security policies, audit and compliance from SAP GRC or other User Management & governance products. User Management REST API's are available in SAP Cloud Platform API Documentation but not listed (as of now) on SAP API Business Hub.
Let's get into action and perform authorization management on CPI using REST API's.
Manage Authorizations from SCP Cockpit - Web UI:
SCP > Sub-account > 'Security' > 'Authorizations' > 'Groups' > 'New Group' + Assign 'Roles'/'Users'

Manage Authorizations from SCP - Authorization Management API's:
Prerequisites:
Access to SCP Cockpit with Developer/Administrator role to create OAuth - Platform API Client.
SCP > Sub-account > 'Members' > 'Add Members'

Authorization Management API - Operations:
- Groups - Manage groups and their assignments to users and roles within the specified account.
- Roles - Manage roles and their assignments to users and groups in the specified account and application
- Users - Manage role and group assignments to the specified user.
Procedure:
Step 1: Create OAuth Platform API Client Credentials - To invoke API's on SCP, OAuth client credentials are required. Client Credentials are specific to SCP Sub-account.
Step 2: Invoke Authorization Management REST API's - Use the Bearer token retrieved from step 1 response and execute the REST method (GET/PUT/POST/DELETE) with respective API operation.
Execute the scenario:
Step 1: Create OAuth Platform API Client Credentials
SAP Cloud Platform API's are protected by OAuth 2.0 with grant type - Client Credentials. Follow the below steps to create Platform API Client on SAP Cloud Platform.
SCP > Sub-account > 'Security' > 'OAuth' > 'Platform API' tab > 'Create API Client'
Give meaningful description to the API Client and select the scope of API's for which this the OAuth Client credentials to be used. For this exercise, let's select the checkbox 'Authorization Management' and click on save. This generates OAuth Client Credentials for consuming Platform API's as in the below snapshot. Note the Client ID & Client Secret. These will serve like User ID & Password to get OAuth token.


Now it's time to call the OAuth endpoint for platform API's and get the token which is valid only for 25 minutes. Let's use postman tool to explore the OAuth Token.
SCP Token Endpoint: https://api.{landscapeHost}/oauth2/apitoken/v1
{landscapeHost} - this is tagged to the region on which SCP is hosted for your account.
For this example, the CPI tenant is running on us2 region (https://lxxxx-tmn.hci.us2.hana.ondemand.com/itspaces/). Accordingly built the below OAuth Token endpoint URL.
Token endpoint URL: https://api.us2.hana.ondemand.com/oauth2/apitoken/v1?grant_type=client_credentials
Select 'Basic Auth' as the Authorization type and pass the OAuth Client Credentials generated earlier as below and execute the OAuth Endpoint URL with POST method.

The response has the Bearer token. We will use this token to execute the Authorization management API's.
Step 2: Invoke Authorization Management REST API's
API URL extensions vary for each API operation. Refer to detailed API documentation on Authorization Management API's. In this exercise, let's execute some of the operations and know how to interpret API Documentation & execute REST API calls.
API Endpoint URL : https://api.{landscapeHost}/authorization/v1
Examples:
# Get Groups - To retrieve all the existing groups created, use the below API endpoint extension '/accounts/{accountName}/groups'.
Get the accountName of the respective SCP Sub-account under which the CPI tenant linked to & the OAuth client credentials created under.

Resolves into: https://api.us2.hana.ondemand.com/authorization/v1/accounts/test00500/groups
Pass the Bearer token generated in step 1 and execute GET method as below.

# Get Users - To retrieve users under each group, use the below API endpoint extension '/accounts/{accountName}/groups/users'.
Resolves into: https://api.us2.hana.ondemand.com/authorization/v1/accounts/test00500/groups/users?groupName=ZGRP_ServiceAccounts
Pass the Bearer token generated in step 1 and execute GET method as below.

# Get Roles - To retrieve Roles assigned to each group, use the below API endpoint extension '/accounts/{accountName}/groups/roles'.
Resolves into: https://api.us2.hana.ondemand.com/authorization/v1/accounts/test00500/groups/roles?groupName=ZGRP_Administrators
Pass the Bearer token generated in step 1 and execute GET method as below.

# Add Users - Add users to a particular existing group, use the below API endpoint extension '/accounts/{accountName}/groups/users'.
Resolves into: https://api.us2.hana.ondemand.com/authorization/v1/accounts/test00500/groups/users?groupName=ZGRP_ServiceAccounts
Pass the Bearer token generated in step 1 and execute PUT method as below.

This REST operation added the S-User and can be validated from SCP Cockpit Web UI (shown under the section - 'Manage Authorizations from SCP Cockpit - Web UI').
With this, we know how to interpret the API documentation and execute Authorization Management REST API calls - PUT/GET.
In similar way, other API Operations and the respective methods can be executed by following the Authorization Management API documentation.
With this understanding, we can create integration flows in CPI to manage Authorization groups, roles and users using HTTP adapter to work with these REST Operations. Such i-flows can be consumed by SAP GRC/User Management tools in a controlled manner.
Enjoy exploring API's!
Labels:
1 Comment
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
93 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
66 -
Expert
1 -
Expert Insights
177 -
Expert Insights
299 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
344 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
422 -
Workload Fluctuations
1
Related Content
- SAP Build Process Automation Pre-built content for Finance Use cases in Technology Blogs by SAP
- Consuming SAP with SAP Build Apps - Mobile Apps for iOS and Android in Technology Blogs by SAP
- Onboarding Users in SAP Quality Issue Resolution in Technology Blogs by SAP
- How to host static webpages through SAP CPI-Iflow in Technology Blogs by Members
- IoT - Ultimate Data Cyber Security - with Enterprise Blockchain and SAP BTP 🚀 in Technology Blogs by Members
Top kudoed authors
| User | Count |
|---|---|
| 40 | |
| 25 | |
| 17 | |
| 13 | |
| 7 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 6 |