
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- SAML between ADFS and SAP Business Intelligence de...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
former_member45
Contributor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
11-24-2018
7:24 AM
In order to enable SAML between ADFS and SAP Business Intelligence platform content deployed on SAP NW AS Java through Single Sign On (SSO)
This document describes how to establish trust between ADFS and SAP Business Intelligence deployed on SAP Netweaver AS Java
The configuration is divided into following
SAP BI Configuration
Setting up SAML authentication for BIP on NW AS Java
Open command and navigate to wdeploy directory. By default directory is
C:\Program Files (x86)\SAP BusinessObjects\SAP BusinessObjects Enterprise XI 4.0\wdeploy
wdeploy.bat sapappsvr73 -DAPP=BOE predeploy
C:\Program Files (x86)\SAP BusinessObjects\SAP BusinessObjects Enterprise XI 4.0\wdeploy\workdir\sapappsvr73\application
Enabling saml authentication
You now have to enable the authentication by editing the above generated BOE.sca file using wdeploy.
Use third party tool ex – WinRAR and extract the BOE.sca file
Open the BOE.sca file
Note – Before making any changes make a copy of it.
Navigate to the DEPLOYARCHIVES directory and open the BOE.ear archive.

From within the BOE.ear archive, open the BOE war archive.

Go to WEB-INF

Goto lib

Adding Service Provider Jars

Configure NW AS Java for HTTPS SSL
Follow steps from below blog to configure HTTPS SSL for NW AS Java
https://blogs.sap.com/2012/03/19/how-to-configure-ssl-by-using-configuration-tool-in-sap-netweaver-a...
Enabling SAML for required Web Applications Properties
SAML authentication has to be enabled for the different web applications. This can be done by uncommenting the respective endpoint in securityContext.xml and also by editing saml.enabled in customproperties files of the respective applications.
In this we will be enabling SAML for Old BI Launchpad BOE/BI
In the securityContext.xml under above generated BOE.sca file BOE.war\WEB-INF , there is a section for the SAML entry endpoints.
By default, only the SAML entry endpoint for Classic BI Launchpad is enabled.
Changes in BILaunchpad.properties
Create BILaunchpad.properties file in the BOE.war\WEB-INF \config\custom assuming custom properties file does not exist. If it is already does, only need to add the property saml.enabled=true
Configurations in the deployment descriptor – web.xml
Enabling SAML in the SP configuration
Activate the SAML context configuration


A new filter has been introduced for SAML, the relevant section in the web.xml will be kept commented by default.
Enabling filters in web.xml of BOE webapps by uncommenting the SAML sections.
Web.xml file path – BOE.war\WEB-INF \web.xml
Note: SAML authentication enablement is done the web application level, that is in BOE itself and not in individual webpath bundles.
Update IDP metadata in SP
The IDP metadata has to be downloaded from the respective IDP. Run the below URL in browser and download the IDP metadata file.
https://adfsdomainname/federationmetadata/2007-06/federationmetedata.xml
Rename the file to idp-meta-downloaded.xml
Copy the ADFS IDP idp-meta-downloaded.xml file to
BOE.war\WEB-INF
SAML keystore generation
SAML exchanges involve usage of cryptography for signing and encryption of data.
You can generate your own self-signed key using the Java utility keytool by following steps
Navigate to <BOE Install Dir>\SAP BusinessObjects Enterprise XI 4.0\win64_x64\sapjvm\bin and run the following command to generate certificate.
keytool -genkeypair -alias <aliasname> -keypass <Password> -keystore <sampleKeystore.jks> -keyalg RSA -validity <numberofdays>
aliasname – certificate alias name, Password -password of your choice, numberofdays – number of the days during which the self-signed certificate is valid, sampletestKeystore.jks is name of the keystore file.
Example – keytool -genkeypair -alias Testkey -keypass Password1 -keystore sampletestKeystore.jks -keyalg RSA -validity 735
The generated keystore file has to be copied from bin folder and pasted under BOE.war\WEB-INF and the references of the new aliasname, Password, keyStore file name has to be changed in securityContext.xml file

The first argument (sampleKeystore.jks) points to the used key store file,
second line contains password (Password1) for the keystore which you enter in command prompt after entering the keystore generation command,
third line then maps with passwords for private keys with alias-password value pairs(Password1). Fourth line Alias of the default certificate is the last parameter.(Testkey).
Note: SP metadata has to be generated everytime this keystore file is changed.
After making all the above changes, Deploy BOE.sca file, now deploy on Netweaver but we also need to enable trusted authentication, will make those changes in BOE.sca and deploy.
Configure Trusted Authentication for Netwevaer AS Java with Web session
We enable SSO by using WEB_SESSION method to pass the IDP username and TrustedPrincipal.conf file to pass shared secret.
Generating shared secret
Enabling Trusted Authentication and Generating Shared Secret
In the BOE.war/web-inf/config/default/folder, extract the following files to the
BOE.war/web-inf/config/custom/folder
- global.properties
Add the following in global.properties
sso.enabled=true
trusted.auth.shared.secret=MySecret
trusted.auth.user.param=MyUser
trusted.auth.user.retrieval=WEB_SESSION
Click Save and save the TrustedPrincipal.conf file to the following directories:
<INSTALLDIR>\SAP BusinessObjects Enterprise XI 4.0\win64_x64\
<INSTALLDIR>\SAP BusinessObjects Enterprise XI 4.0\win32_x86\
Create the IDP user in BOE
The IDP user has to be created in BOE or imported through some SDK script or export using CSV option in CMC.
The SAML based authentication relies on TrustedAuth from the web-server to the CMS. For this, the IDP users will have to be created in BOE as Enterprise users.
Import the bulk users into BIPlatform:
https://blogs.sap.com/2013/05/16/bi-40-sp6-how-to-import-users-in-bulk-from-central-management-conso...
Locate the custom.jsp file inside the web folder at C:\Program Files (x86)\SAP BusinessObjects\tomcat\webapps\BOE\WEB-INF\eclipse\plugins\webpath.InfoView\web\custom.jsp
Make the following changes to the custom.jsp file in the location mentioned above

Update and close the archive file.
After doing the above steps in BOE.sca file, now deploy on Netweaver.
ADFS Configuration
For ADFS IDP related configuration, follow the steps from section ADFS Configuration from below blog.
https://blogs.sap.com/2018/02/22/adfs-with-sap-business-intelligence-platform/
Learn More:
https://blogs.sap.com/2018/02/28/saml-integration-between-microsoft-azure-portal-and-sap-analytics-c...
https://blogs.sap.com/2017/12/19/sap-analytics-cloud-saml-sso-using-adfs-active-directory-federation...
https://blogs.sap.com/2018/02/22/adfs-with-sap-business-intelligence-platform/
https://blogs.sap.com/2018/03/01/saml-integration-between-microsoft-azure-portal-and-sap-business-in...
This document describes how to establish trust between ADFS and SAP Business Intelligence deployed on SAP Netweaver AS Java
The configuration is divided into following
- Configure SAML authentication for SAP Business Intelligence deployed on SAP NW AS Java
- Setting up trusted authentication for BIP
SAP BI Configuration
Setting up SAML authentication for BIP on NW AS Java
- Generating BI Web application using Wdeploy for NW AS Java
Open command and navigate to wdeploy directory. By default directory is
C:\Program Files (x86)\SAP BusinessObjects\SAP BusinessObjects Enterprise XI 4.0\wdeploy
- Run the following command to generate BOE.sca (in this doc we will generate only BOE.sca)
wdeploy.bat sapappsvr73 -DAPP=BOE predeploy
- Generated BOE.sca default output location is
C:\Program Files (x86)\SAP BusinessObjects\SAP BusinessObjects Enterprise XI 4.0\wdeploy\workdir\sapappsvr73\application
Enabling saml authentication
You now have to enable the authentication by editing the above generated BOE.sca file using wdeploy.
Use third party tool ex – WinRAR and extract the BOE.sca file
Open the BOE.sca file
Note – Before making any changes make a copy of it.
Navigate to the DEPLOYARCHIVES directory and open the BOE.ear archive.

From within the BOE.ear archive, open the BOE war archive.

Go to WEB-INF

Goto lib

Adding Service Provider Jars
- The Spring SAML Service Provider Jars are available inside <BOE Install Dir> \SAP BusinessObjects Enterprise XI 4.0\SAMLJARS,
- Copy these jars to above navigated lib folder \WEB-INF\lib

Configure NW AS Java for HTTPS SSL
Follow steps from below blog to configure HTTPS SSL for NW AS Java
https://blogs.sap.com/2012/03/19/how-to-configure-ssl-by-using-configuration-tool-in-sap-netweaver-a...
Enabling SAML for required Web Applications Properties
SAML authentication has to be enabled for the different web applications. This can be done by uncommenting the respective endpoint in securityContext.xml and also by editing saml.enabled in customproperties files of the respective applications.
In this we will be enabling SAML for Old BI Launchpad BOE/BI
- Changes in securityContext.xml file
In the securityContext.xml under above generated BOE.sca file BOE.war\WEB-INF , there is a section for the SAML entry endpoints.
By default, only the SAML entry endpoint for Classic BI Launchpad is enabled.

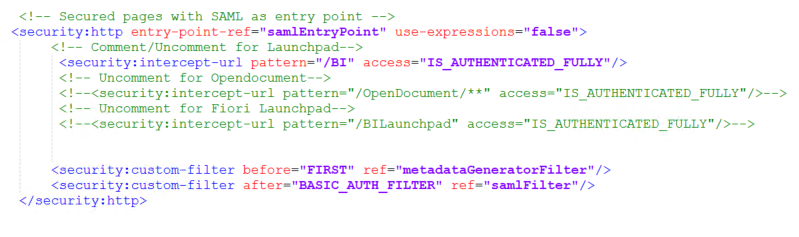
- SAML Authentication can also be enabled for other applications Opendocument, Fiori Launchpad by uncommenting <security:intercept line of that particular application.
- Also in case SAML authentication has to be enabled only for one application ex : BI Launchpad alone, the <security:intercept-url pattern=”/BI” access=”IS_AUTHENTICATED_FULLY”/> has to been uncommented, comment the entry points for Opendocument, Fiori Launchpad.
Changes in BILaunchpad.properties
Create BILaunchpad.properties file in the BOE.war\WEB-INF \config\custom assuming custom properties file does not exist. If it is already does, only need to add the property saml.enabled=true
Configurations in the deployment descriptor – web.xml
Enabling SAML in the SP configuration
Activate the SAML context configuration
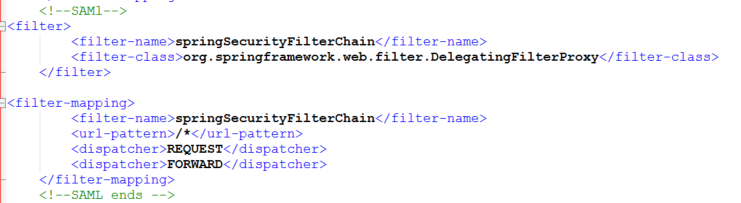
- Open the BOE.war\WEB-INF \web.xml file in a text editor.
- Remove the lines (<! —and –>) that comment out the contents of the START SAML / END SAML comments wherever you find in the web.xml file. Below snapshots show the uncommented part



A new filter has been introduced for SAML, the relevant section in the web.xml will be kept commented by default.
Enabling filters in web.xml of BOE webapps by uncommenting the SAML sections.
Web.xml file path – BOE.war\WEB-INF \web.xml
Note: SAML authentication enablement is done the web application level, that is in BOE itself and not in individual webpath bundles.
Update IDP metadata in SP
The IDP metadata has to be downloaded from the respective IDP. Run the below URL in browser and download the IDP metadata file.
https://adfsdomainname/federationmetadata/2007-06/federationmetedata.xml
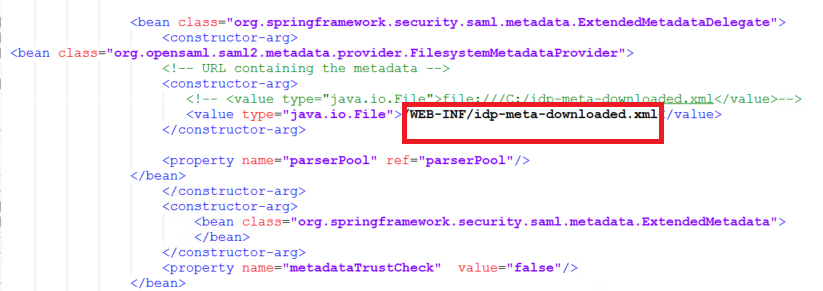
Rename the file to idp-meta-downloaded.xml
Copy the ADFS IDP idp-meta-downloaded.xml file to
BOE.war\WEB-INF

SAML keystore generation
SAML exchanges involve usage of cryptography for signing and encryption of data.
You can generate your own self-signed key using the Java utility keytool by following steps
Navigate to <BOE Install Dir>\SAP BusinessObjects Enterprise XI 4.0\win64_x64\sapjvm\bin and run the following command to generate certificate.
keytool -genkeypair -alias <aliasname> -keypass <Password> -keystore <sampleKeystore.jks> -keyalg RSA -validity <numberofdays>
aliasname – certificate alias name, Password -password of your choice, numberofdays – number of the days during which the self-signed certificate is valid, sampletestKeystore.jks is name of the keystore file.
Example – keytool -genkeypair -alias Testkey -keypass Password1 -keystore sampletestKeystore.jks -keyalg RSA -validity 735
The generated keystore file has to be copied from bin folder and pasted under BOE.war\WEB-INF and the references of the new aliasname, Password, keyStore file name has to be changed in securityContext.xml file

The first argument (sampleKeystore.jks) points to the used key store file,
second line contains password (Password1) for the keystore which you enter in command prompt after entering the keystore generation command,
third line then maps with passwords for private keys with alias-password value pairs(Password1). Fourth line Alias of the default certificate is the last parameter.(Testkey).
Note: SP metadata has to be generated everytime this keystore file is changed.
After making all the above changes, Deploy BOE.sca file, now deploy on Netweaver but we also need to enable trusted authentication, will make those changes in BOE.sca and deploy.
Configure Trusted Authentication for Netwevaer AS Java with Web session
We enable SSO by using WEB_SESSION method to pass the IDP username and TrustedPrincipal.conf file to pass shared secret.
Generating shared secret
Enabling Trusted Authentication and Generating Shared Secret
- Go to CMC > Authentication > Enterprise
- Enable Trusted Authentication
- Click "Create new shared secret"
- Click "Download shared secret" - save it in your BOE machine
- Click "Update"
In the BOE.war/web-inf/config/default/folder, extract the following files to the
BOE.war/web-inf/config/custom/folder
- global.properties
Add the following in global.properties
sso.enabled=true
trusted.auth.shared.secret=MySecret
trusted.auth.user.param=MyUser
trusted.auth.user.retrieval=WEB_SESSION
Click Save and save the TrustedPrincipal.conf file to the following directories:
<INSTALLDIR>\SAP BusinessObjects Enterprise XI 4.0\win64_x64\
<INSTALLDIR>\SAP BusinessObjects Enterprise XI 4.0\win32_x86\
Create the IDP user in BOE
The IDP user has to be created in BOE or imported through some SDK script or export using CSV option in CMC.
The SAML based authentication relies on TrustedAuth from the web-server to the CMS. For this, the IDP users will have to be created in BOE as Enterprise users.
Import the bulk users into BIPlatform:
https://blogs.sap.com/2013/05/16/bi-40-sp6-how-to-import-users-in-bulk-from-central-management-conso...
Locate the custom.jsp file inside the web folder at C:\Program Files (x86)\SAP BusinessObjects\tomcat\webapps\BOE\WEB-INF\eclipse\plugins\webpath.InfoView\web\custom.jsp
Make the following changes to the custom.jsp file in the location mentioned above
<\!DOCTYPE HTML PUBLIC “-//W3C//DTD HTML 4.01 Transitional//EN” “http://www.w3.org/TR/html4/loose.dtd”>
<%@ page language=”java” contentType=”text/html;charset=utf-8″ %>
<% //custom Java code

Update and close the archive file.
After doing the above steps in BOE.sca file, now deploy on Netweaver.
ADFS Configuration
For ADFS IDP related configuration, follow the steps from section ADFS Configuration from below blog.
https://blogs.sap.com/2018/02/22/adfs-with-sap-business-intelligence-platform/
Learn More:
https://blogs.sap.com/2018/02/28/saml-integration-between-microsoft-azure-portal-and-sap-analytics-c...
https://blogs.sap.com/2017/12/19/sap-analytics-cloud-saml-sso-using-adfs-active-directory-federation...
https://blogs.sap.com/2018/02/22/adfs-with-sap-business-intelligence-platform/
https://blogs.sap.com/2018/03/01/saml-integration-between-microsoft-azure-portal-and-sap-business-in...
Labels:
3 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
91 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
66 -
Expert
1 -
Expert Insights
177 -
Expert Insights
293 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
340 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
419 -
Workload Fluctuations
1
Related Content
- How to use AI services to translate Picklists in SAP SuccessFactors - An example in Technology Blogs by SAP
- Up Net Working Capital, Up Inventory and Down Efficiency. What to do? in Technology Blogs by SAP
- IoT - Ultimate Data Cyber Security - with Enterprise Blockchain and SAP BTP 🚀 in Technology Blogs by Members
- Developing & Deploying the UI5 App to Cloud Foundry and Accessing from App-router End-to-End Steps in Technology Blogs by Members
- New Machine Learning features in SAP HANA Cloud in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 35 | |
| 25 | |
| 13 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 6 | |
| 5 | |
| 4 |