
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Part 1: SAP Cloud Platform Authentication setup us...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Employee
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
11-06-2018
5:51 AM
--------------Begin Update - 05/02/2019: Following updates are made---------------
---------------End update------------------------------------------------------------------------------
In this blog series, I would like to share my experience in enablement of SAP Cloud Platform in 3 part series and share some of the tips and tricks for rapid cloud adoption. When customer decided to adopt SAP Cloud Portal or Fiori Cloud in Cloud Platform (SCP), following set of activities are required.
SAP Cloud Platform Identity Authentication service is a cloud service for secure authentication and user management in SAP cloud and on-premise applications. It provides services for authentication, single sign-on, and user management.
One of the use cases is to allow users to authenticate on SCP from Microsoft Active Directory and ADFS. The scenario is depicted in the picture below.

IAS connect to the Corporate AD via Cloud Connector where IAS is acting like a proxy. Once the user is authenticated, a user is created in IAS tenant, subsequent logins always get authenticated against the corporate Active Directory. Perform the following steps to establish the authentication setup
Connection to Corporate Active Directory
Prerequisite: Cloud connector is installed and connected to SCP subaccount
Change default trust management to custom

3. Select Application Identity Provider, click on Add Identity Authentication tenant and select tenant

4. Click on the tenant to map the assertion attributes to AD attribute as shown below

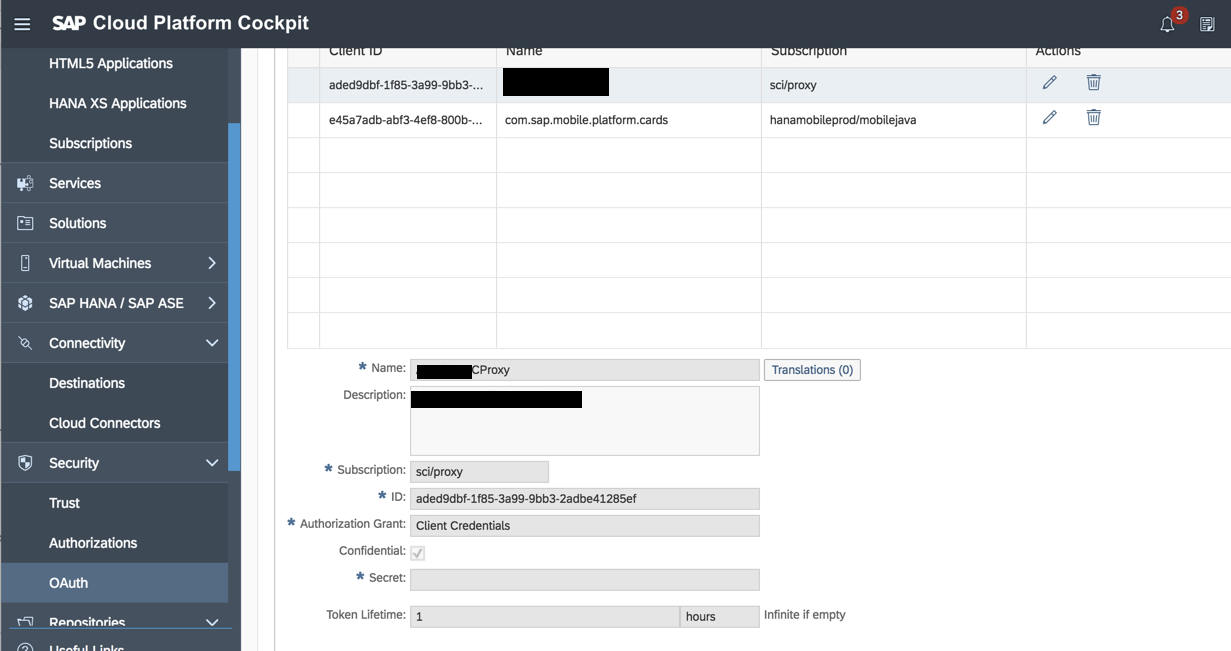
Create OAuth Client of type sci/proxy in SAP Cloud Platform
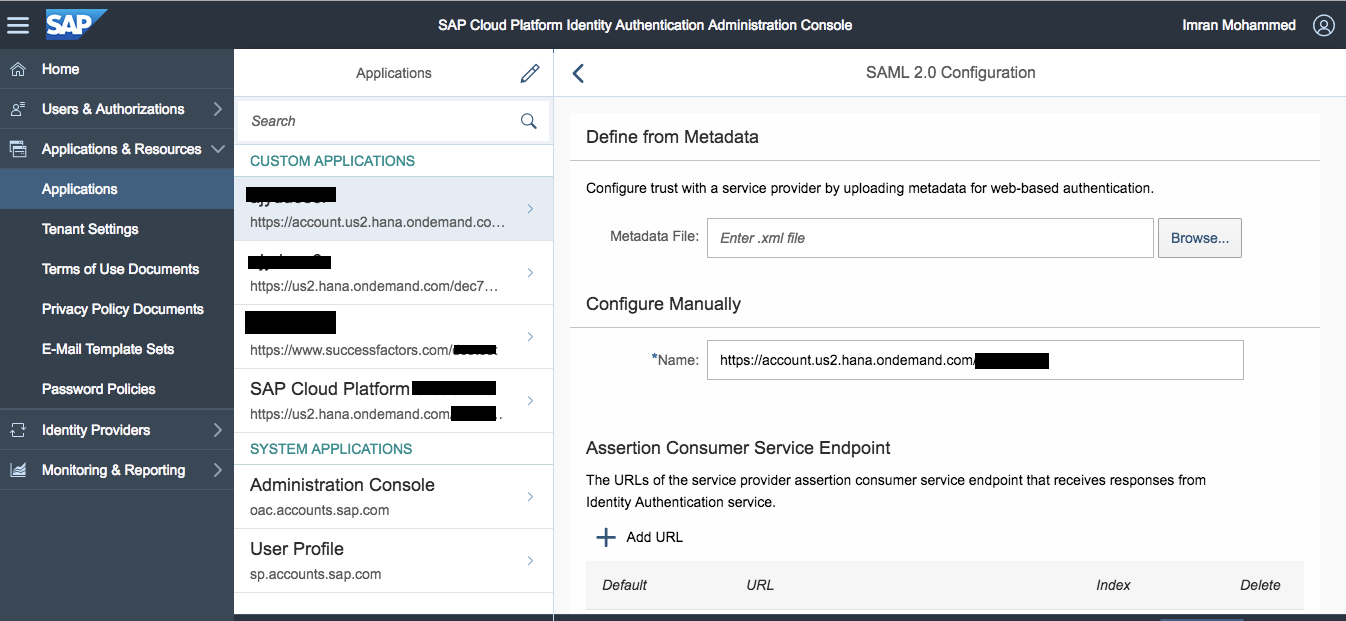
Upload Metadata file into IAS applications
4. You can also change Name ID Attribute and add additional assertion attributes if required

Configure the connection to corporate user store in IAS tenant settings

Maintain LDAP connection details in Cloud Connector


Test authentication

Enter Active directory domain username (no email) for the first time and in subsequent logins, you enter an email address or username.
Connection to Microsoft ADFS using Conditional Authentication
Conditional authentication is one of the features of IAS. Tenant administrator can define rules for authenticating identity provider according to the e-mail domain, user type, user group, and IP range (specified in CIDR notation). Based on the configured rules, IAS forward the request to the respective identity provider. For more information about Conditional Authentication refer to sap help.
Follow the steps below to configure the conditional authentication rule to redirect a user to Microsoft ADFS login page based on email.
Prerequisite:
Follow the steps mentioned in the blog to configure MS ADFS as an Identity provider

2. . Select SAML 2.0 Configuration and upload the MS ADFS metadata file and save the changes

3. Select Identity Provider Type as Microsoft ADFS / Azure AD


4. Navigate back to Applications & Resources menu and select Applications. Select Conditional Authentication link and add the rule as shown in the screenshots below
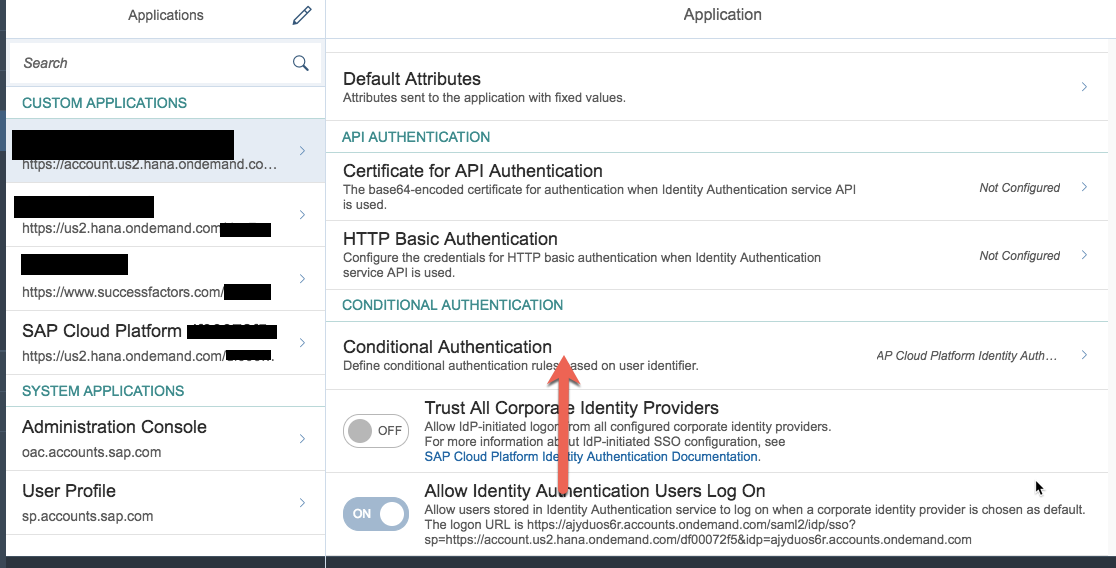


5. Select Default Identity Provider as IAS

6. Test the cloud portal URL, you will notice that IAS login page is displayed asking for email, based on the email provides, IAS forward the request to ADFS or used AD to authenticate the user


This concludes the part 1. In part 2, we will see how to do Principal Propagation between Cloud application and backend system.
If you want to Integrate IAS with Azure AD, please refer to my colleague Murali Shanmughan 5- part series of Integrating Identity Authenticationservice & Azure Active Directory in SAP Cloud Platform.
- Removed trusted identity provider between Cloud Platform and MS ADFS. This step is not required because Corporate Identity Provider is added in IAS and the trust is established between IAS & MSADFS.
- Added link to Murali Shanmugham blog for his 5- part series of Integrating Identity Authenticationservice & Azure Active Directory in SAP Cloud Platform
---------------End update------------------------------------------------------------------------------
In this blog series, I would like to share my experience in enablement of SAP Cloud Platform in 3 part series and share some of the tips and tricks for rapid cloud adoption. When customer decided to adopt SAP Cloud Portal or Fiori Cloud in Cloud Platform (SCP), following set of activities are required.
SAP Cloud Platform Identity Authentication service is a cloud service for secure authentication and user management in SAP cloud and on-premise applications. It provides services for authentication, single sign-on, and user management.
One of the use cases is to allow users to authenticate on SCP from Microsoft Active Directory and ADFS. The scenario is depicted in the picture below.

IAS connect to the Corporate AD via Cloud Connector where IAS is acting like a proxy. Once the user is authenticated, a user is created in IAS tenant, subsequent logins always get authenticated against the corporate Active Directory. Perform the following steps to establish the authentication setup
Connection to Corporate Active Directory
Prerequisite: Cloud connector is installed and connected to SCP subaccount
Change default trust management to custom
- Login to SAP Cloud Platform with S or I account, make sure your ID has admin access to perform this operation
- Navigate to Security > Trust > Local Service Provider: select Edit and change configuration type from default to custom and download the metadata file

3. Select Application Identity Provider, click on Add Identity Authentication tenant and select tenant

4. Click on the tenant to map the assertion attributes to AD attribute as shown below

Create OAuth Client of type sci/proxy in SAP Cloud Platform
- Create OAuth client of a type of sci/proxy as shown below
- Remember the client id and secret key this will be used in connection to the corporate user store in IAS tenant settings

Upload Metadata file into IAS applications
- Login to IAS tenant, launch tenant from Trust under Application Identity Provider or frame the URL using Http://<tenant>/accounts.ondemand.com/admin
- Under Applications & Resources, select the application same as tenant name. A custom application gets created upon selecting the custom under Trust done in step #1 above. Note, if you don’t find application, you can create one by selecting plus (+) icon at the bottom of the page
- Select SAML 2.0 Configuration and upload the metadata file downloaded in step #1 above


4. You can also change Name ID Attribute and add additional assertion attributes if required

Configure the connection to corporate user store in IAS tenant settings
- Under Applications & Resources, select Tenant Settings > Corporate User Store, enter the following details
- Select data center for subaccount, technical name= account name, paste client id and secret key from step#2 above

Maintain LDAP connection details in Cloud Connector
- Make sure cloud connector is connected and resource status is set to available
- Log in to Cloud Connector, select Configuration > Cloud, enter Active Directory details under Cloud User Store section
- Make sure secure checkbox is checked and SSL port is opened in the firewall


Test authentication
- Launch Cloud portal for testing, enter Active directory credential to log in the application
- A request will be redirected to IAS

Enter Active directory domain username (no email) for the first time and in subsequent logins, you enter an email address or username.
Connection to Microsoft ADFS using Conditional Authentication
Conditional authentication is one of the features of IAS. Tenant administrator can define rules for authenticating identity provider according to the e-mail domain, user type, user group, and IP range (specified in CIDR notation). Based on the configured rules, IAS forward the request to the respective identity provider. For more information about Conditional Authentication refer to sap help.
Follow the steps below to configure the conditional authentication rule to redirect a user to Microsoft ADFS login page based on email.
Prerequisite:
Follow the steps mentioned in the blog to configure MS ADFS as an Identity provider
- Login to IAS tenant, under Identity Providers, select Corporate Identity Providers and click on Add link to add the identity provider. Enter Corporate IdP name, click Save

2. . Select SAML 2.0 Configuration and upload the MS ADFS metadata file and save the changes


3. Select Identity Provider Type as Microsoft ADFS / Azure AD


4. Navigate back to Applications & Resources menu and select Applications. Select Conditional Authentication link and add the rule as shown in the screenshots below



5. Select Default Identity Provider as IAS

6. Test the cloud portal URL, you will notice that IAS login page is displayed asking for email, based on the email provides, IAS forward the request to ADFS or used AD to authenticate the user


This concludes the part 1. In part 2, we will see how to do Principal Propagation between Cloud application and backend system.
If you want to Integrate IAS with Azure AD, please refer to my colleague Murali Shanmughan 5- part series of Integrating Identity Authenticationservice & Azure Active Directory in SAP Cloud Platform.
Labels:
9 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
93 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
66 -
Expert
1 -
Expert Insights
177 -
Expert Insights
299 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
345 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
427 -
Workload Fluctuations
1
Related Content
- SAP Cloud ALM and Identity Authentication Service (IAS) in Technology Blogs by SAP
- SAP LICENSE RENEWAL FROM BASIS END #ATR in Technology Blogs by Members
- How to use AI services to translate Picklists in SAP SuccessFactors - An example in Technology Blogs by SAP
- Activation of IAS in Technology Q&A
- Top Picks: Innovations Highlights from SAP Business Technology Platform (Q1/2024) in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 40 | |
| 25 | |
| 17 | |
| 14 | |
| 8 | |
| 7 | |
| 7 | |
| 7 | |
| 6 | |
| 6 |