
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Understanding & Implementing ILM Part 1
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
a343855
Explorer
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
08-24-2018
10:10 AM
Recently I was assigned to a prototype development which needs to consume ILM framework in ABAP on-Premise system. I have summarized the whole ILM topic into two separate blogs. The first one which we are going to discuss in this blog is to demonstrae the ability to automatically detect and destruct destroyable data (and its related component). Destroyable data could be defined as per customer or business scenario, its customizable. one such business scenario is data that are expired for more than one year could be defined as destroyable .
ILM stands for "Information Lifecycle Management". ILM framework helps to manage data life cycle through a very simple configurable steps and minimal amount of coding and highly flexible for customer. This is very useful as well for GDPR where the purpose could be to delete personal data/information after the user has left the organisation.
one simple answer would be to remove the unnecessary data and lessen the load on our application and DB.
It’s important to mention it could be achieved without ILM framework, however advantage of using ILM framework can’t be ignored more so where time and less complexity is directly related to Total cost of Development.
Advantages:
Pre-requisite

Following are the main points that we will be covering in detail

ILM Configuation is to be done at two ends as shown in above figure, one being IRM_CUST which a developer has to do in order to enable the ILM framework, and second being IRMPOL and ILMARA which is at customer end. For latter developer has to provide consulting note to their respective customer where they can customize the destroyable data definition, this will be explained in part 2 of this blog. we have here explained customization that is to be done by developer for ILM to be operational.
Customization at Developer end:
1 Create a destruction program in SE38 namely SAM_ILM_DES. no coding yet just we need to create a program. you can name anything starting with z or y or your namespace.
2. Configuration for Destruction Object:
DOBJ configuration: Enter transaction DOBJ in command box. Create a new entry. Give any destruction object name associate your destruction program name (created above) with this destruction object.

3. Configuration for ILM Object
Transaction: IRM_CUST Here we create one ILM object and link the above created destruction object to this ILM object.

Double click on ILM Objects
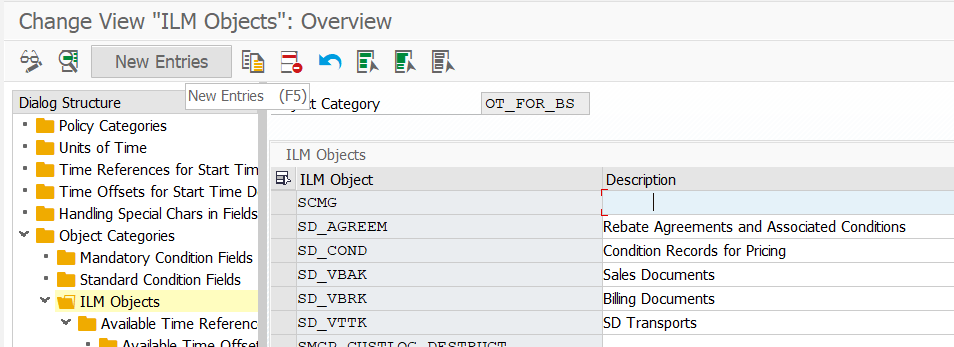
press "NEW ENTRIES" and here enter you ILM Object Name

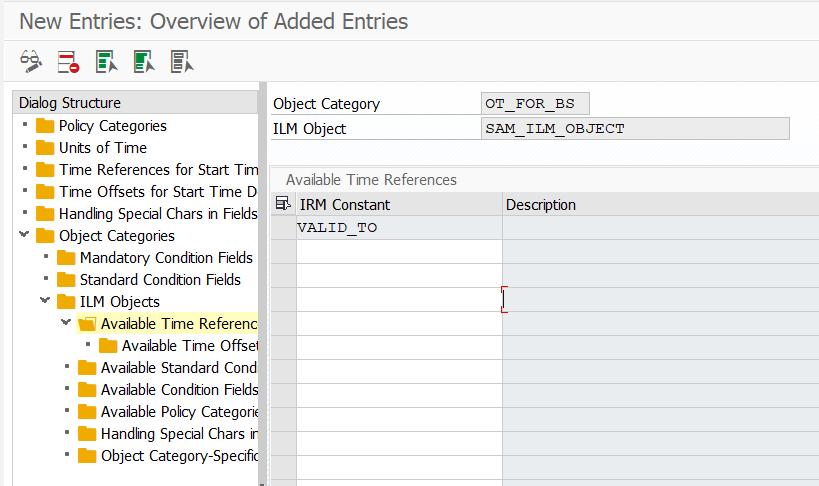
Define Available Time Reference fields which can be mapped to any time reference fields of your application table to be used for calculation of retention logic.







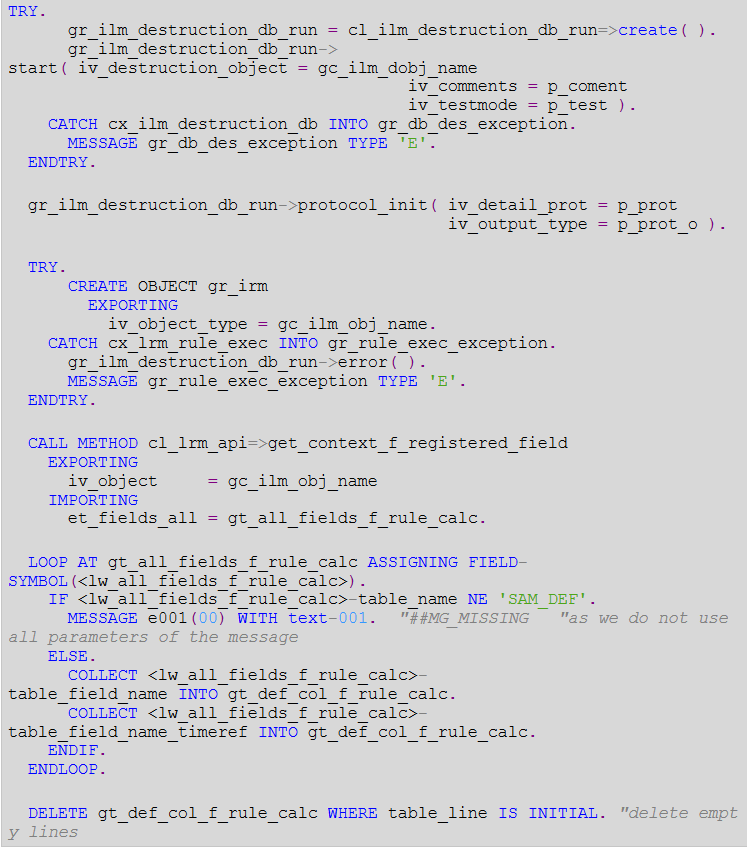
Inside routine “main”, we will have following sub routines.




What?
ILM stands for "Information Lifecycle Management". ILM framework helps to manage data life cycle through a very simple configurable steps and minimal amount of coding and highly flexible for customer. This is very useful as well for GDPR where the purpose could be to delete personal data/information after the user has left the organisation.
Why?
one simple answer would be to remove the unnecessary data and lessen the load on our application and DB.
It’s important to mention it could be achieved without ILM framework, however advantage of using ILM framework can’t be ignored more so where time and less complexity is directly related to Total cost of Development.
Advantages:
- Auto-enabled Application logging
- Least amount of coding
- Customizable business scenarios for deciding the destroyable data
How?
Pre-requisite
- ILM business function must be switched on : First thing first, you need to ensure ILM business function is switched on. For various reason is some organization it is not switched on. Check with system administrator first.
- Check ILM Business Function : To check if ILM is switched on or off. Go to transaction SFW5. Find ILM and you can see if its witched on or off.

Implementation Steps
Following are the main points that we will be covering in detail
- ILM Configuration
- Create a custom delete API that perform data and its component
- Embed the API into ILM based destruction program

Implementation Details
ILM Configuation is to be done at two ends as shown in above figure, one being IRM_CUST which a developer has to do in order to enable the ILM framework, and second being IRMPOL and ILMARA which is at customer end. For latter developer has to provide consulting note to their respective customer where they can customize the destroyable data definition, this will be explained in part 2 of this blog. we have here explained customization that is to be done by developer for ILM to be operational.
Customization at Developer end:
1 Create a destruction program in SE38 namely SAM_ILM_DES. no coding yet just we need to create a program. you can name anything starting with z or y or your namespace.
2. Configuration for Destruction Object:
DOBJ configuration: Enter transaction DOBJ in command box. Create a new entry. Give any destruction object name associate your destruction program name (created above) with this destruction object.

3. Configuration for ILM Object
Transaction: IRM_CUST Here we create one ILM object and link the above created destruction object to this ILM object.

Double click on ILM Objects

press "NEW ENTRIES" and here enter you ILM Object Name

Define Available Time Reference fields which can be mapped to any time reference fields of your application table to be used for calculation of retention logic.







- ILM Program: Coding Embedding delete API into ILM framework backed program as shown below

- Add INCLUDE destroy_prg_standard before INITIALIZATION
- Under INTIALIZATION add PERFORM standard_texts_init.
- In START OF SELECTION event, a subroutine PERFORM main.
- Inside main, we need to add four subroutines that are mentioned below.
- All above steps can be seen in above screenshot of the program
Inside routine “main”, we will have following sub routines.
- PREPROCESSING

- FILL_WORKLIST - Here we can retrieve the data from main table from which is to be scope of data destruction. Let's say GT_WORK_LIST

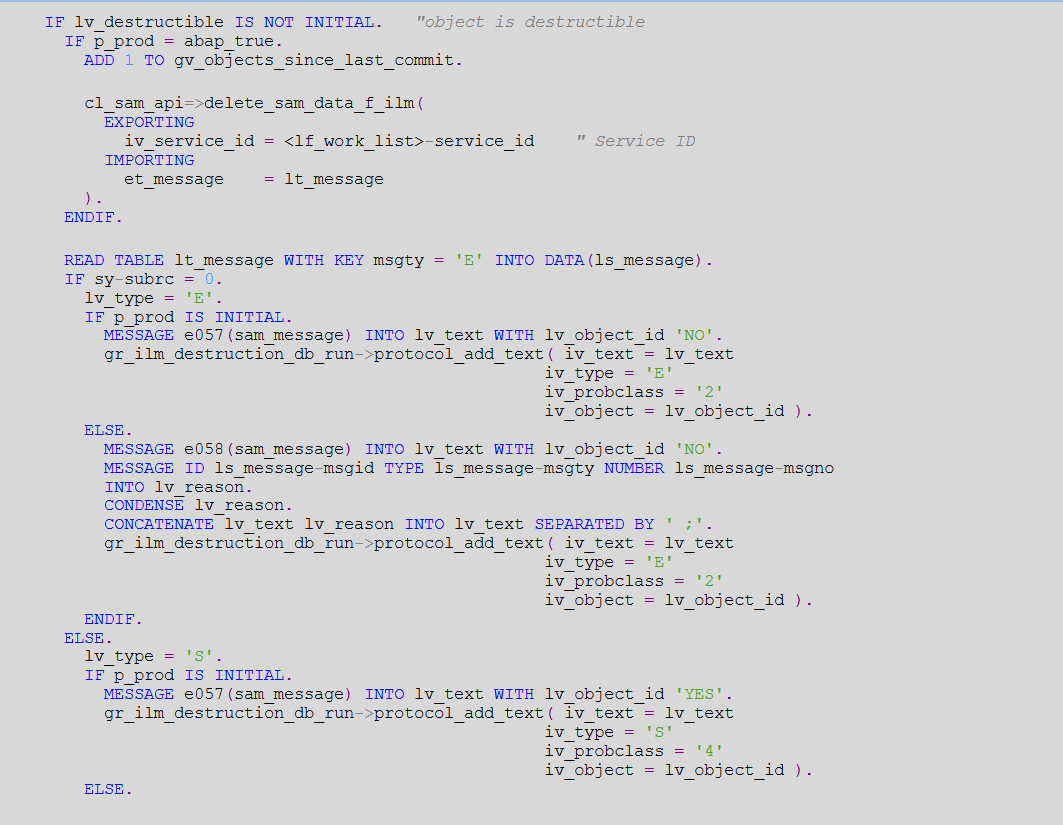
- PROCESSING




- You can now run this program in foreground
- Or you can schedule this program in background and it will check the data everyday which all data has expired and will delete it
- SAP Managed Tags:
- ABAP Development,
- SAP Information Lifecycle Management,
- SAP R/3
15 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
88 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
65 -
Expert
1 -
Expert Insights
178 -
Expert Insights
282 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
11 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
330 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
408 -
Workload Fluctuations
1
Related Content
- Analyze Expensive ABAP Workload in the Cloud with Work Process Sampling in Technology Blogs by SAP
- Introducing Blog Series of SAP Signavio Process Insights, discovery edition – An in-depth exploratio in Technology Blogs by SAP
- Kyma Integration with SAP Cloud Logging. Part 2: Let's ship some traces in Technology Blogs by SAP
- SAP HANA Cloud Vector Engine: Quick FAQ Reference in Technology Blogs by SAP
- Empowering Retail Business with a Seamless Data Migration to SAP S/4HANA in Technology Blogs by Members
Top kudoed authors
| User | Count |
|---|---|
| 11 | |
| 11 | |
| 11 | |
| 10 | |
| 9 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 5 |