
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Understanding Security & Authentication within Mob...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
former_member18
Explorer
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
03-01-2018
12:57 PM
A Brief Overview
This blogpost discuss how one authenticates into the Development and Operations service provisioned within the SAP Cloud Platform and the various authentication and Single SignOn mechanisms available.
Gaining access to apps and related data via Mobile Services for Development and Operations (SAP CPms) is a two fold process. First one must authenticate into the platform and then to the datasource.

The SAP Cloud Platform which is the provider for core services to all the other services running within its scope is responsible for handling all the authentication into the platform and the services themselves are responsible for the second part of the flow where one implements what we call SSO (single sign-on) to the respective backend systems or data sources. Thus, one may see this setup as two distinct entities that need to work symbiotically to produce the desired end result.
Let us have a more in depth look at how this is set up.
The Identity Provider
The SAP Cloud Platform cockpit contains a Trust center (I actually have no idea what it is officially called but Trust center does sound nice Upon further inspection !! I can see it is actually called Trust Management 🙂 ) where one configures the various Identity providers. Normally this federation is done using SAML. By default the sap identity provider (accounts.sap.com) is available, meaning all users within your current scope will reside in this identity provider. Typically they will follow the S, P, D or I user naming nomenclature. It is also here in the trust center that one may configure 3rd party Identity Providers like AD(FS) or indeed a tenant of SAP’s own Identity and Authentication Service.


The Configuration Nodes
But hold on, this is only about setting up where to look for the users when authenticating a call to a resource. Not how this is done. Well, the SAP Cloud Platform is also responsible for the “how” part of things (meaning various authentication mechanisms are provided which can either be called programmatically or set up as a part of the configuration tasks).
In the case of our service (SAP CPms), when an application is built, there are typically two configuration nodes that need addressing, namely Connectivity and Security.

While the connectivity node is left incomplete because there is no possibility to pre-populate the information required here, the Security node is provided with default settings which is SAML.

While the default security option for authenticating into the service is SAML, one also has other options available like
- OAuth
- Basic Authentication
- Certificate (X.509)
- And even NONE (so no authentication, can you guess why this may be relevant?)
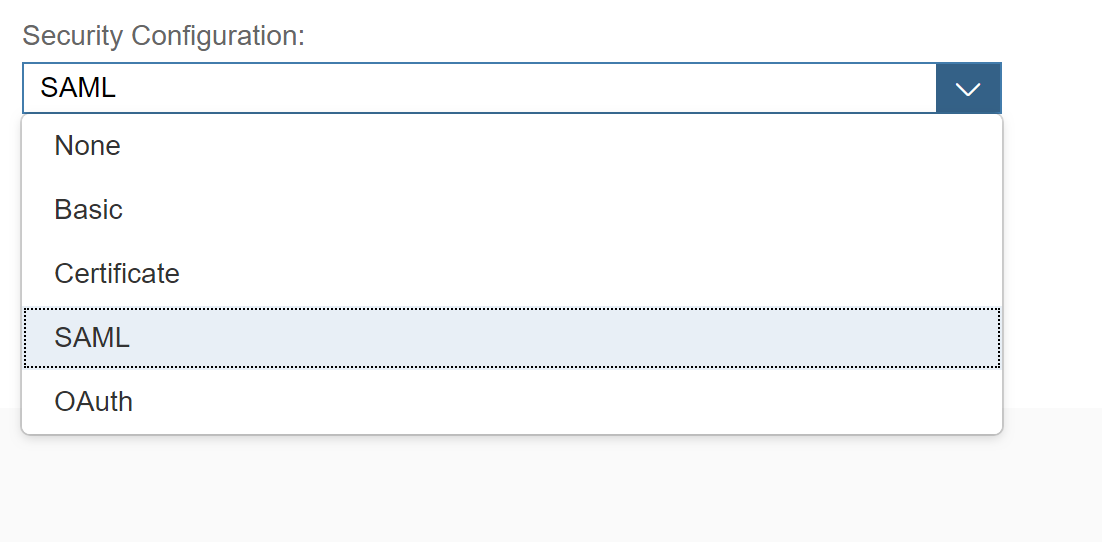
While we are here, let us take a moment to crystalize the message.
“When creating an application in the Development & Operations Service, one can use Basic, Certificates, OAuth or SAML (default) to identify the user behind the request. In some cases it may be viable to allow anonymous access (B2C scenarios for e.g. a webshop ) using the None option.”
Once we have decided on our Security mechanism, we are left with the simple (sic!) task of setting up SSO to the backend (or DataSource). This as you may have guessed is done in the Connectivity node.

As with the Security mechanisms we again have a few options to choose from.

- Application-to-Application SSO
- This is an option typically used to pass the identity of the requester between services deployed within the cloud platform.
- SAPAssertion SSO
- Use the assertion token option if the backend is configured accordingly. This option is typically used when working in a System-to-system scenario (user is identified with a logon ticket) where the recipient is singled out.
- OAuth2 SAML Bearer Assertion
- As the name suggest, here one uses the SAML assertion to gain access to resources that are protected using OAuth.
- Basic Authentication
- This option allows either using a preconfigured user (for e.g. technical user) or if the fields are left blank, then to respond to a challenge from the backend with an appropriate user & password combination.
- Client Certificate Authentication
- Using certificates is viable when the backend is configured to accept trusted certificates (from a well known CA or one that is specifically trusted, typically enterprise internal CA’s).
- No Authentication
- If the backend in question allows access to the requested resource without any form of authentication required, then one would use the NoAuth option.
One Last Thing
Did you pickup on the fact that the list above is missing one of the major topics we (Michael van Cutsem did sterling work on it while seconded to my team) worked on last year? Yes, Principal Propagation is missing in this list. That is because the list is dynamic and will change based on what is a valid combination. See the matrix table in the appendix below for more insights into valid combinations. The screenshots below show you the difference in the options present when having chosen the Internet Proxy (for the destination / Connectivity) versus having chosen the On-Premise proxy and in the case of the latter, we can see the Principal Propagation option.


You're Done
This done, one can safely say that the two components of the trinity that supports an authenticated and safe usage of applications via the SAP CPms have been configured and you have successfully joined the ranks of those who understand the basic tenants of Security and Authentication within the Development and Operations service on SAP Cloud Platform.
Appendix
The matrix below visualizes the various combinations and permutations between the Security configuration and the SSO options.

Find the official help documentation for Security Administration at this link.
- SAP Managed Tags:
- SAP Mobile Services,
- SAP Business Technology Platform
12 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,661 -
Business Trends
87 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
64 -
Expert
1 -
Expert Insights
178 -
Expert Insights
273 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
Kafka
1 -
Life at SAP
784 -
Life at SAP
11 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,577 -
Product Updates
326 -
Replication Flow
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,886 -
Technology Updates
403 -
Workload Fluctuations
1
Related Content
- SAP HANA Cloud Vector Engine: Quick FAQ Reference in Technology Blogs by SAP
- Top Picks: Innovations Highlights from SAP Business Technology Platform (Q1/2024) in Technology Blogs by SAP
- Unable to log in to SAP BusinessObjects CMC in Technology Blogs by Members
- Partner-2-Partner Collaboration in Manufacturing in Technology Blogs by SAP
- Pilot: SAP Datasphere Fundamentals in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 12 | |
| 10 | |
| 10 | |
| 7 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 4 |