
- SAP Community
- Groups
- Interest Groups
- Application Development
- Blog Posts
- ABAP Code Vulnerabilities, a call for real-time se...
Application Development Blog Posts
Learn and share on deeper, cross technology development topics such as integration and connectivity, automation, cloud extensibility, developing at scale, and security.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
ivan-ae
Explorer
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
11-17-2017
12:10 PM
ABAP code vulnerabilities
SAP security is a great challenge and will be a challenge for many years to come. In order to thoroughly secure an application, all of its components and potential threats need to be understood. SAP security is multi-layered, its building blocks range from infrastructure to application security. In order to break an application, only one flaw may be sufficient to compromise an entire environment.
Below an overview of SAP security notes released between June and November 2017, categorized by their priority.

A good number of vulnerabilities find their origin within insecure ABAP coding. Within this blog article we will in particular zoom in on SQL-injection, one of just many ABAP code vulnerabilities.
By reading this blog post, the first one in a series, I want to trigger the awareness for the need of real-time security monitoring.
What is SQL-injection?
In ABAP we have various ways of reading and updating database values. By modifying specific variables or SQL-access clauses one can gain unauthorized access to secured data, or one can even alter data directly on the database.
Let’s look at the most basic form of SQL-injection through the use of commonly used open-SQL statements and a selection-screen parameter.
Following program reads user master data for a specific user-ID:

When we run the report “as designed” we get the output for one particular user.
When we however fiddle around with the input entered at the selection-screen, perfectly bypassing typical validation rules, we are able to extract the entire user master!
The code above may be a textbook example, you may be surprised how often we see such code snippets passing through established QA processes. And to be truly honest, being an ABAP developer myself for more then 20 years, also I have to plead guilty when it comes to introducing certain unwanted vulnerabilities.
Besides relatively basic SQL-injection scenarios, using Open-SQL, new technologies also introduce new vulnerabilities. An example here being ABAP managed database procedures, the SQL-scripting functions available within HANA databases. EXEC-statements using variables parts impose a very similar risk as seen with Open-SQL.
How to identify SQL-injection vulnerabilities?
Nowadays every self-respecting SAP developer should be aware of commonly known vulnerabilities. “Awareness” may already remediate a lot of risks introduced through insecure code, it surely does not close the gates for vulnerabilities getting introduced into your business critical environment.
SAP standard offers a range of tools in order to ensure code violations can be identified. The ABAP Test Cockpit (ATC) is an ABAP check framework which allow static checks and unit tests for ABAP programs. ATC is also the umbrella above SAP Code Inspector (SCI), the extended syntax check (SLIN) and the SAP Code Vulnerability Analyzer (CVA).
Especially this last one, the SAP code vulnerability analyzer, serves a great purpose when it comes to code security. Although SAP ships CVA as standard with recent NetWeaver releases its use unfortunately is far from free.
Code security should not be optional
Especially within large enterprises we see the awareness of risks and vulnerabilities translate into very concrete measures to mitigate the ever growing risks of hacking, data theft, data loss, ...
Next to the SAP standard portfolio of tools like code inspector and CVA there are a number of –excellent– 3rd party tools on the market which perform static code scans, even offering instant remediation options. Still such tools highlight vulnerabilities at a relatively late stage.
Code verification might be executed by the developer, or during a peer or QA review at transport release. At best, a static and overall analysis is executed once sources are released or even productively deployed.
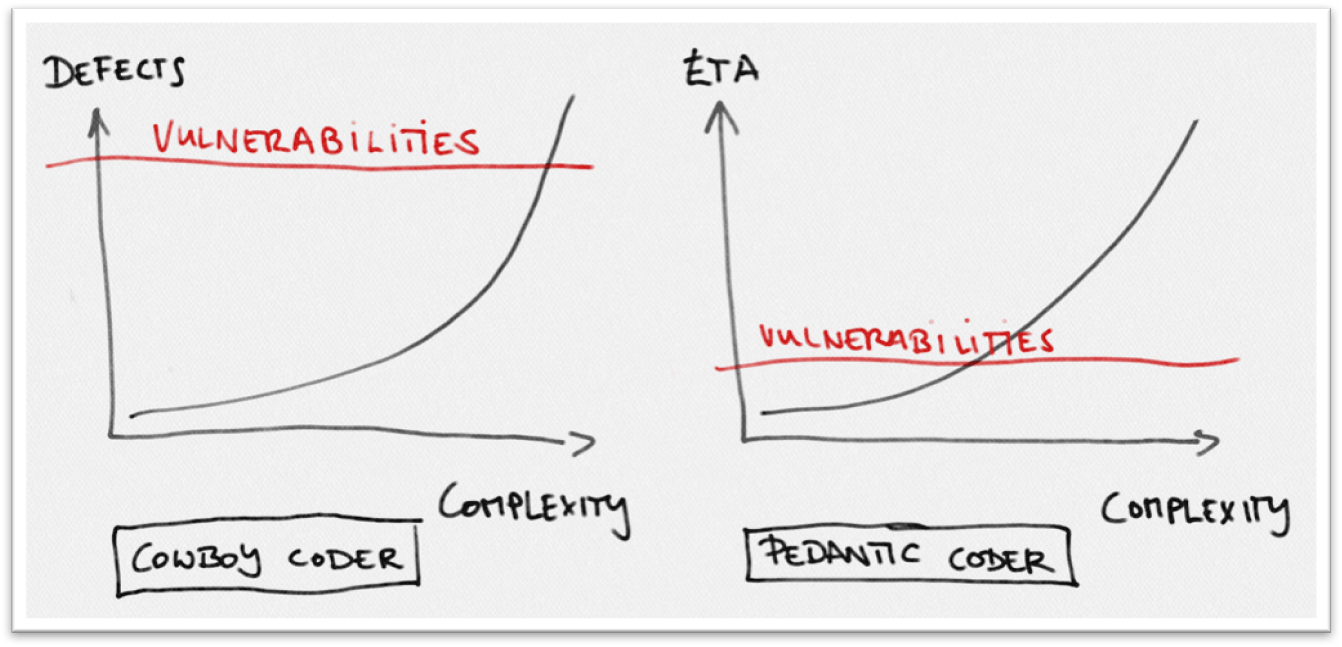
Security often starts with code, without code there would be no vulnerabilities.
Quality of the code base has a direct relation to vulnerabilities
Real-time code vulnerability checks
Whenever a developer introduces a fresh vulnerability within a development environment this may be of no relevance (yet) for your security operations center, they may mainly monitor your productive and critical business operations. However, when a developer gets an instant alert while still coding no unnoticed vulnerabilities will be released into subsequent environments.
In a next post we will talk about ABAP code injection. Can't wait? Join me at the Cybersecurity conference for SAP customers 2017.
Now, are you continuously checking your code base for vulnerabilities?
- SAP Managed Tags:
- ABAP Development,
- Security
2 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
A Dynamic Memory Allocation Tool
1 -
ABAP
8 -
abap cds
1 -
ABAP CDS Views
14 -
ABAP class
1 -
ABAP Cloud
1 -
ABAP Development
4 -
ABAP in Eclipse
1 -
ABAP Keyword Documentation
2 -
ABAP OOABAP
2 -
ABAP Programming
1 -
abap technical
1 -
ABAP test cockpit
7 -
ABAP test cokpit
1 -
ADT
1 -
Advanced Event Mesh
1 -
AEM
1 -
AI
1 -
API and Integration
1 -
APIs
8 -
APIs ABAP
1 -
App Dev and Integration
1 -
Application Development
2 -
application job
1 -
archivelinks
1 -
Automation
4 -
BTP
1 -
CAP
1 -
CAPM
1 -
Career Development
3 -
CL_GUI_FRONTEND_SERVICES
1 -
CL_SALV_TABLE
1 -
Cloud Extensibility
8 -
Cloud Native
7 -
Cloud Platform Integration
1 -
CloudEvents
2 -
CMIS
1 -
Connection
1 -
container
1 -
Debugging
2 -
Developer extensibility
1 -
Developing at Scale
4 -
DMS
1 -
dynamic logpoints
1 -
Eclipse ADT ABAP Development Tools
1 -
EDA
1 -
Event Mesh
1 -
Expert
1 -
Field Symbols in ABAP
1 -
Fiori
1 -
Fiori App Extension
1 -
Forms & Templates
1 -
General
1 -
Getting Started
1 -
IBM watsonx
1 -
Integration & Connectivity
10 -
Introduction
1 -
JavaScripts used by Adobe Forms
1 -
joule
1 -
NodeJS
1 -
ODATA
3 -
OOABAP
3 -
Outbound queue
1 -
Product Updates
1 -
Programming Models
13 -
Restful webservices Using POST MAN
1 -
RFC
1 -
RFFOEDI1
1 -
SAP BAS
1 -
SAP BTP
1 -
SAP Build
1 -
SAP Build apps
1 -
SAP Build CodeJam
1 -
SAP CodeTalk
1 -
SAP Odata
1 -
SAP UI5
1 -
SAP UI5 Custom Library
1 -
SAPEnhancements
1 -
SapMachine
1 -
security
3 -
text editor
1 -
Tools
17 -
User Experience
5
Top kudoed authors
| User | Count |
|---|---|
| 3 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |